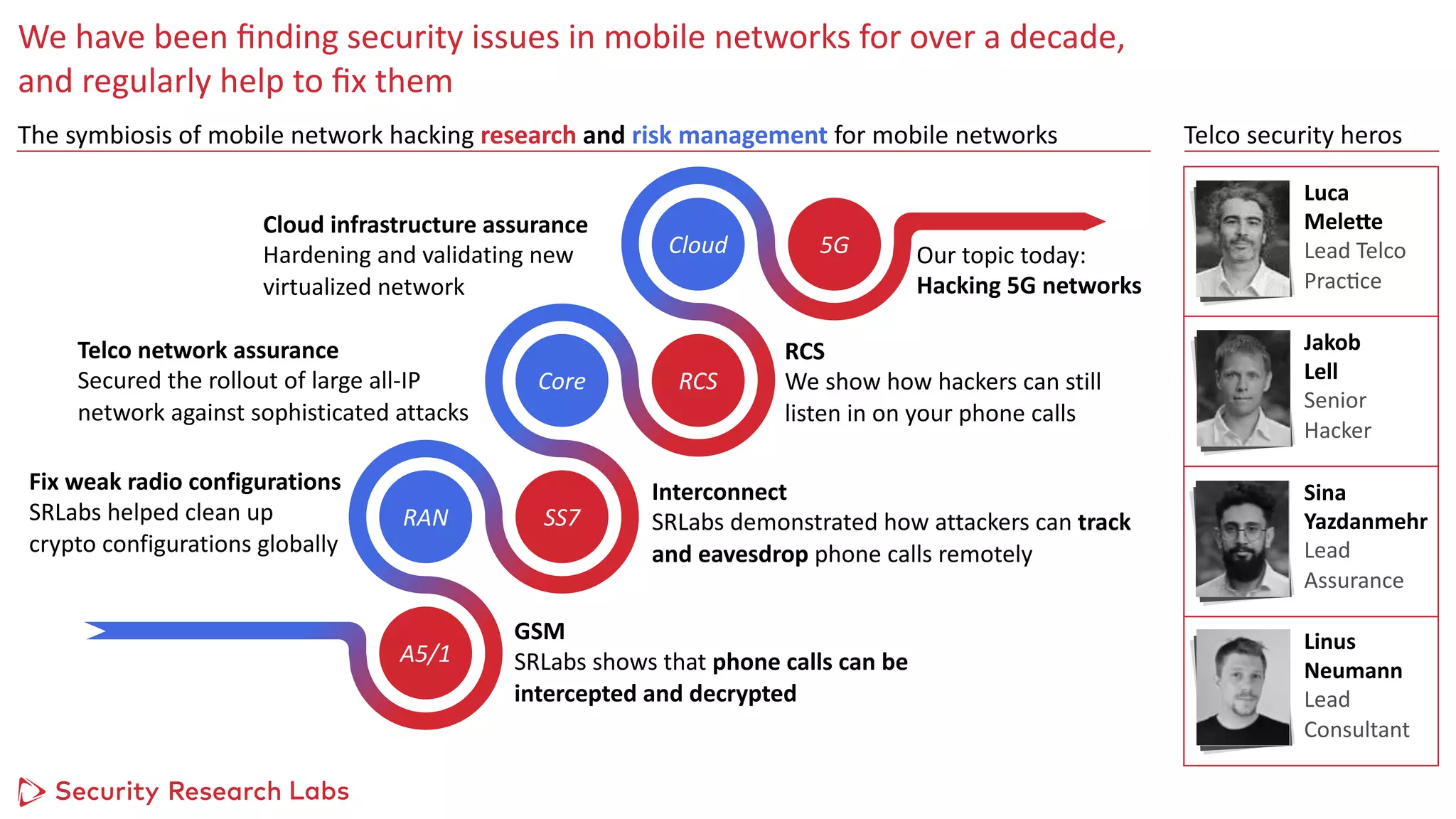
An expert in mobile network security provided a summary of hacking 5G networks. Some key points include:
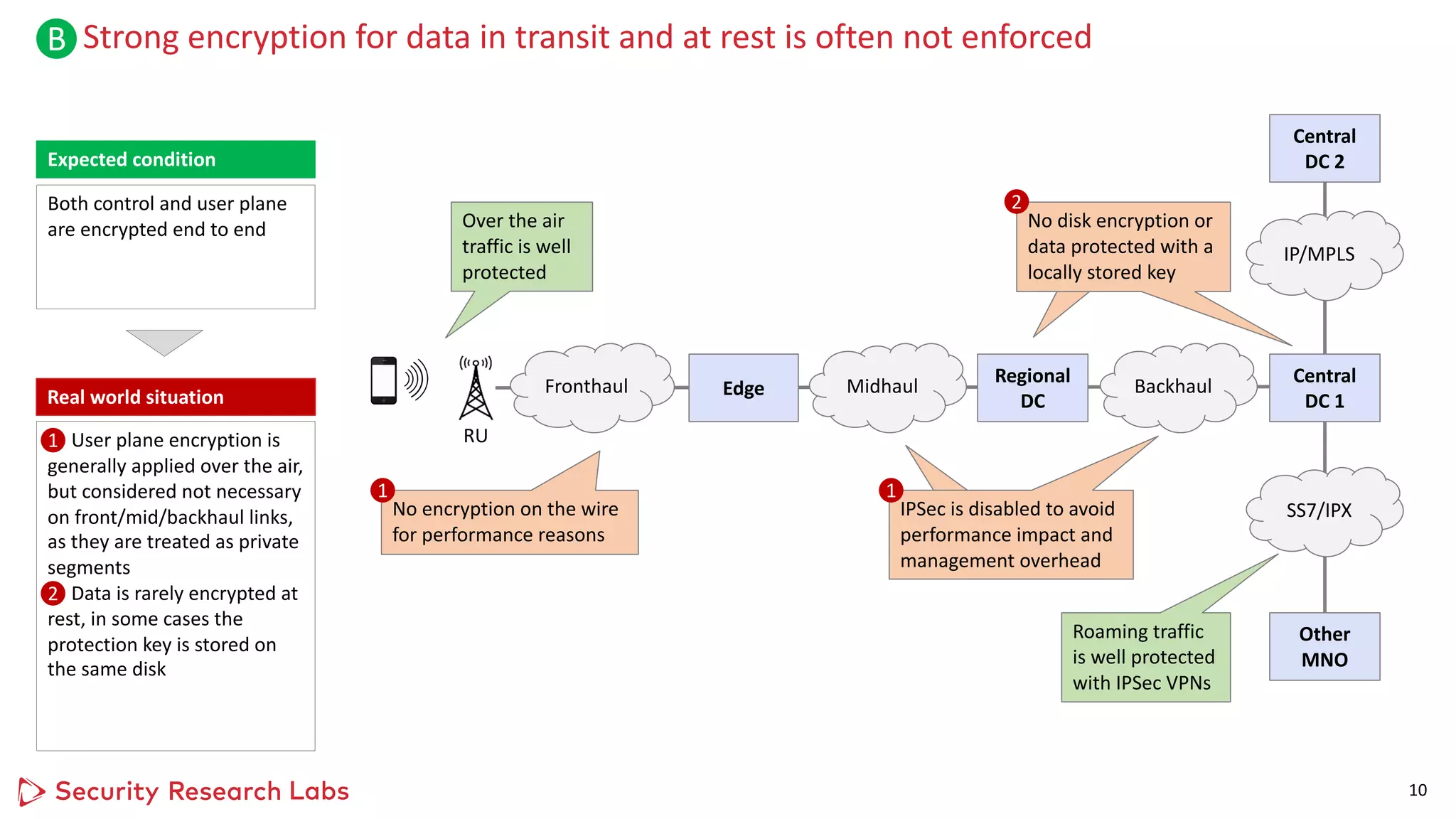
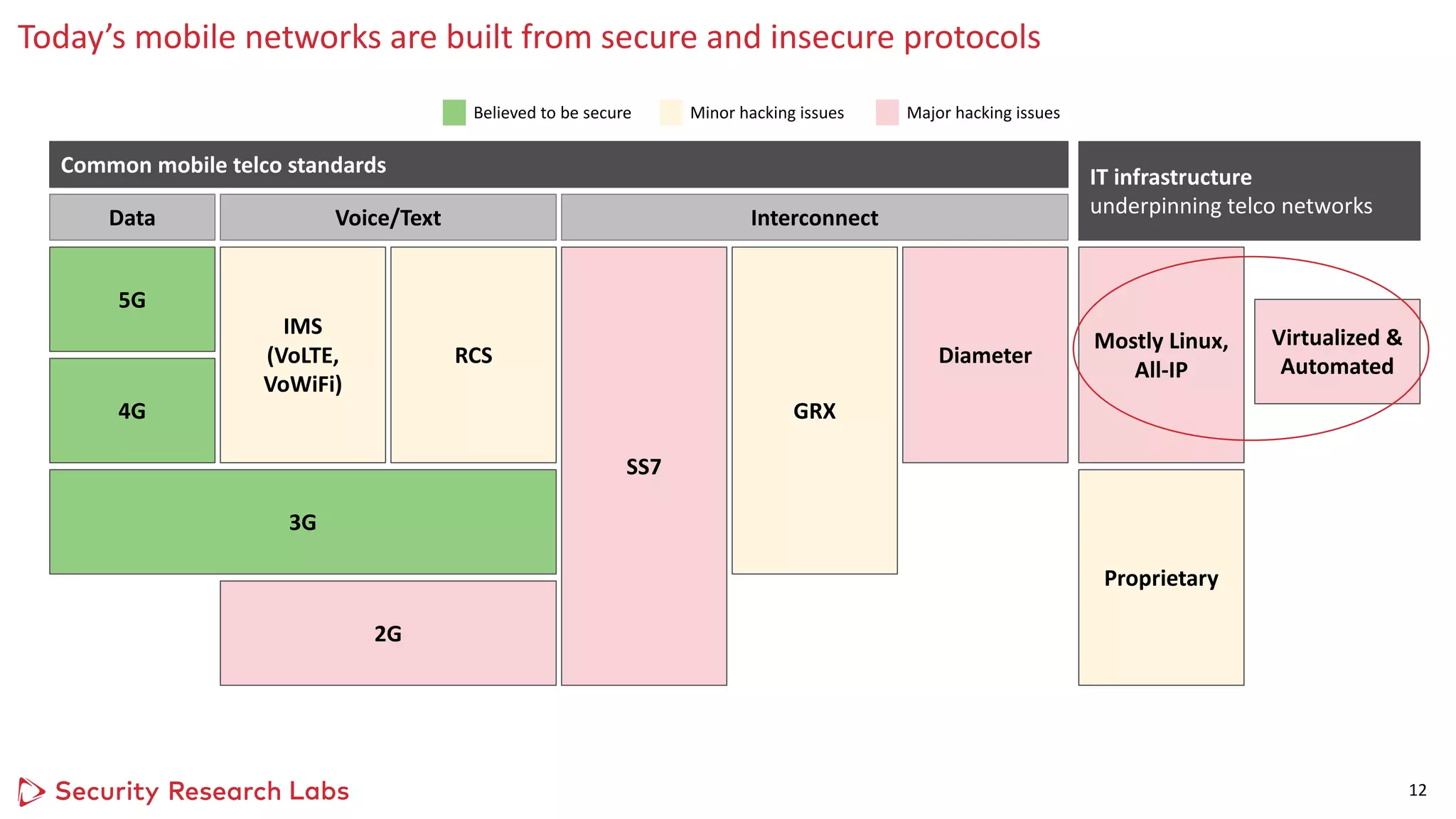
1) Standard IT security techniques uncovered issues when applied to upgraded legacy 4G networks, such as unpatched operating systems, weak configurations, and lack of encryption.
2) Future 5G networks introduce new security risks due to increased complexity from virtualization and automation layers, as well as a continuously evolving attack surface extending into cloud infrastructure.
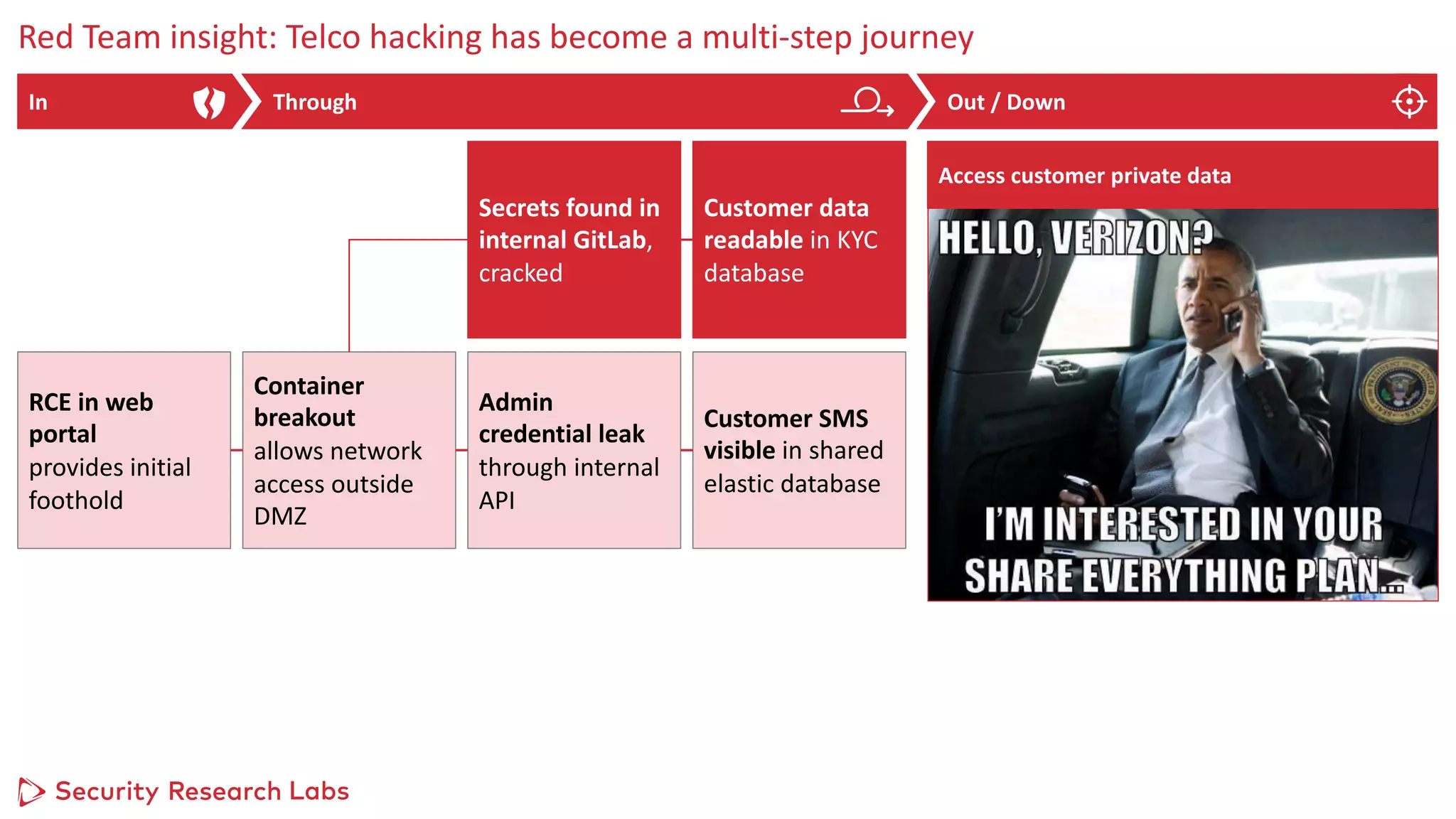
3) Red team exercises show that hacking mobile networks has become a multi-step process, where initial access through one vulnerability can enable lateral movement and privilege escalation to compromise critical systems or customer data.
















![as Logo Horizontal
Pos / Neg
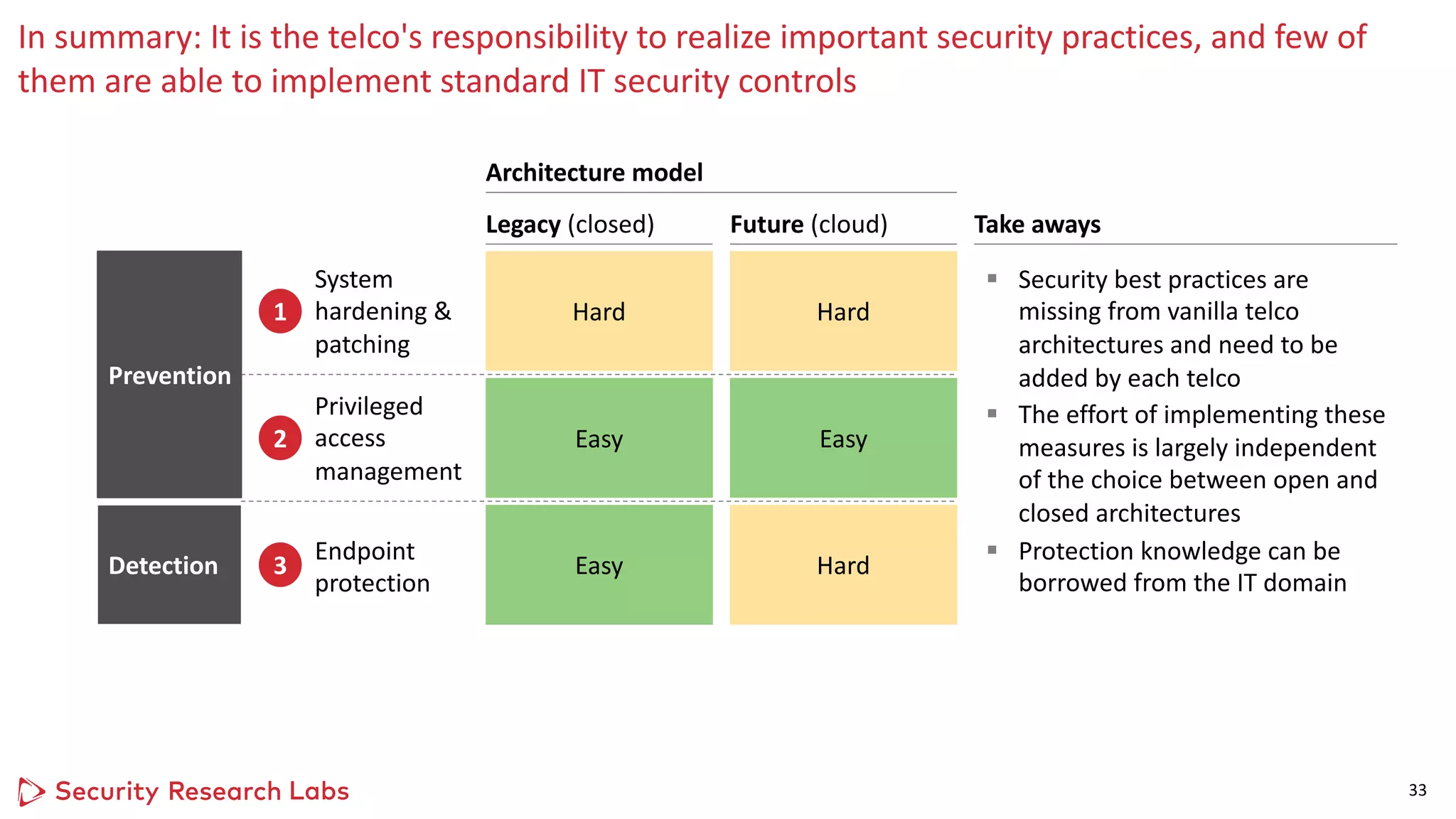
In practice, successful telco cyber defence is often hard as standard prevention and detection
controls are missing
Cyber risk areas Detection
Prevention
Defense best practices [examples]
System hacking
Abuse of insider
privileges
System hardening & patching
Privileged access management
1
2
Endpoint protection
3
Detailed on next slides
x
29](https://image.slidesharecdn.com/d2t1s09221127-230103071757-420d7b85/75/cb22-Tales-of-5G-hacking-by-Karsten-Nohl-29-2048.jpg)