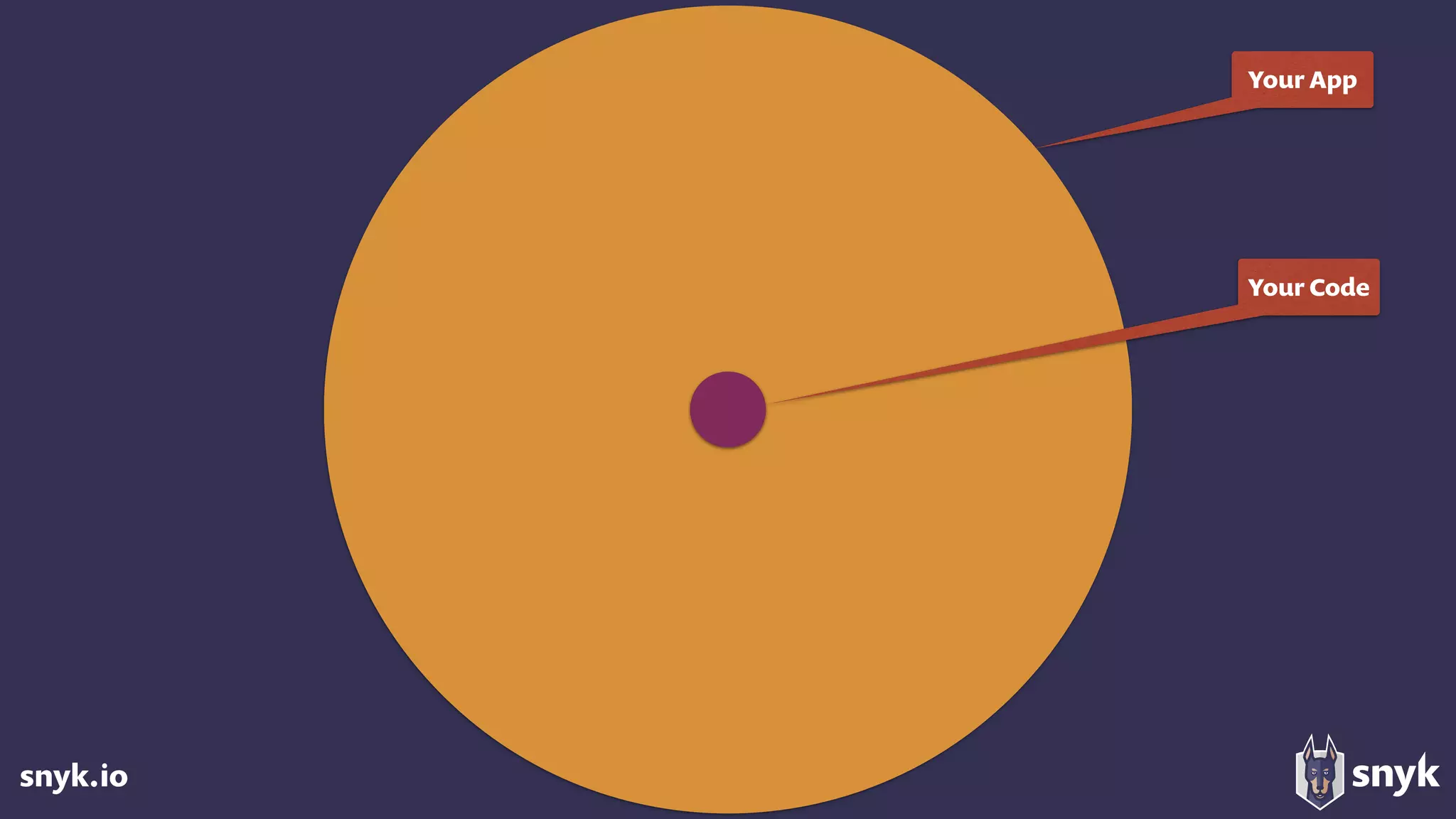
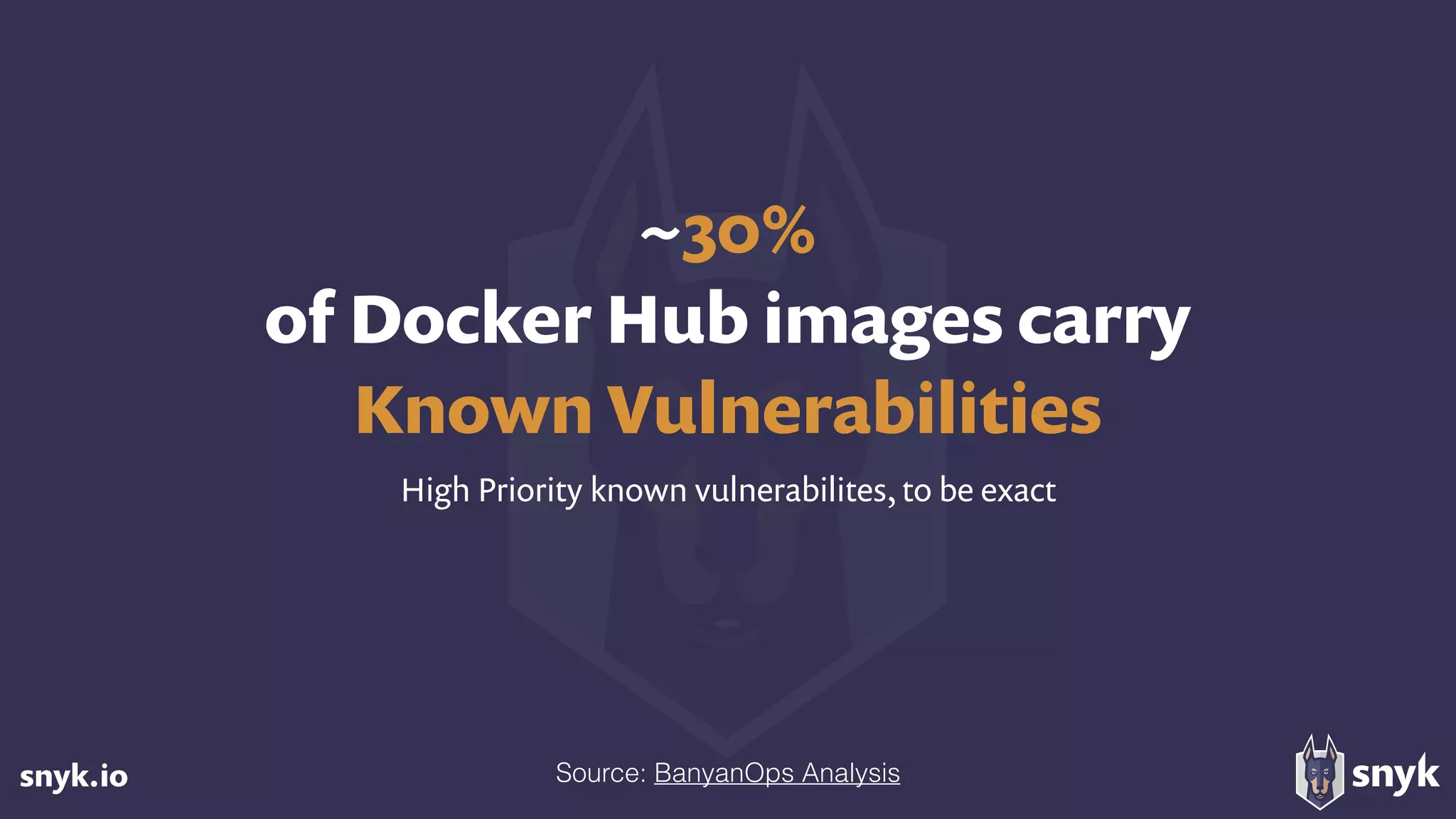
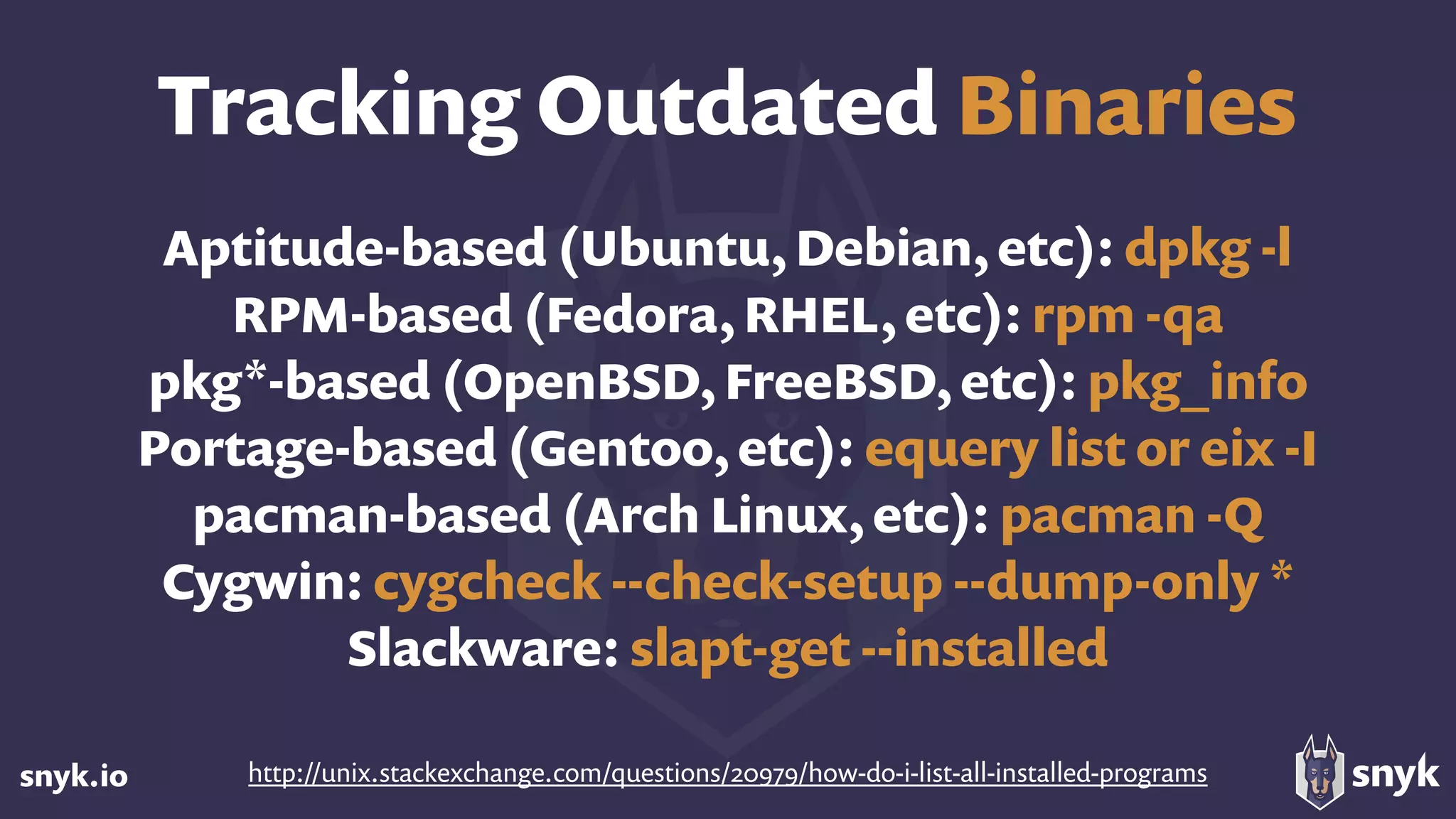
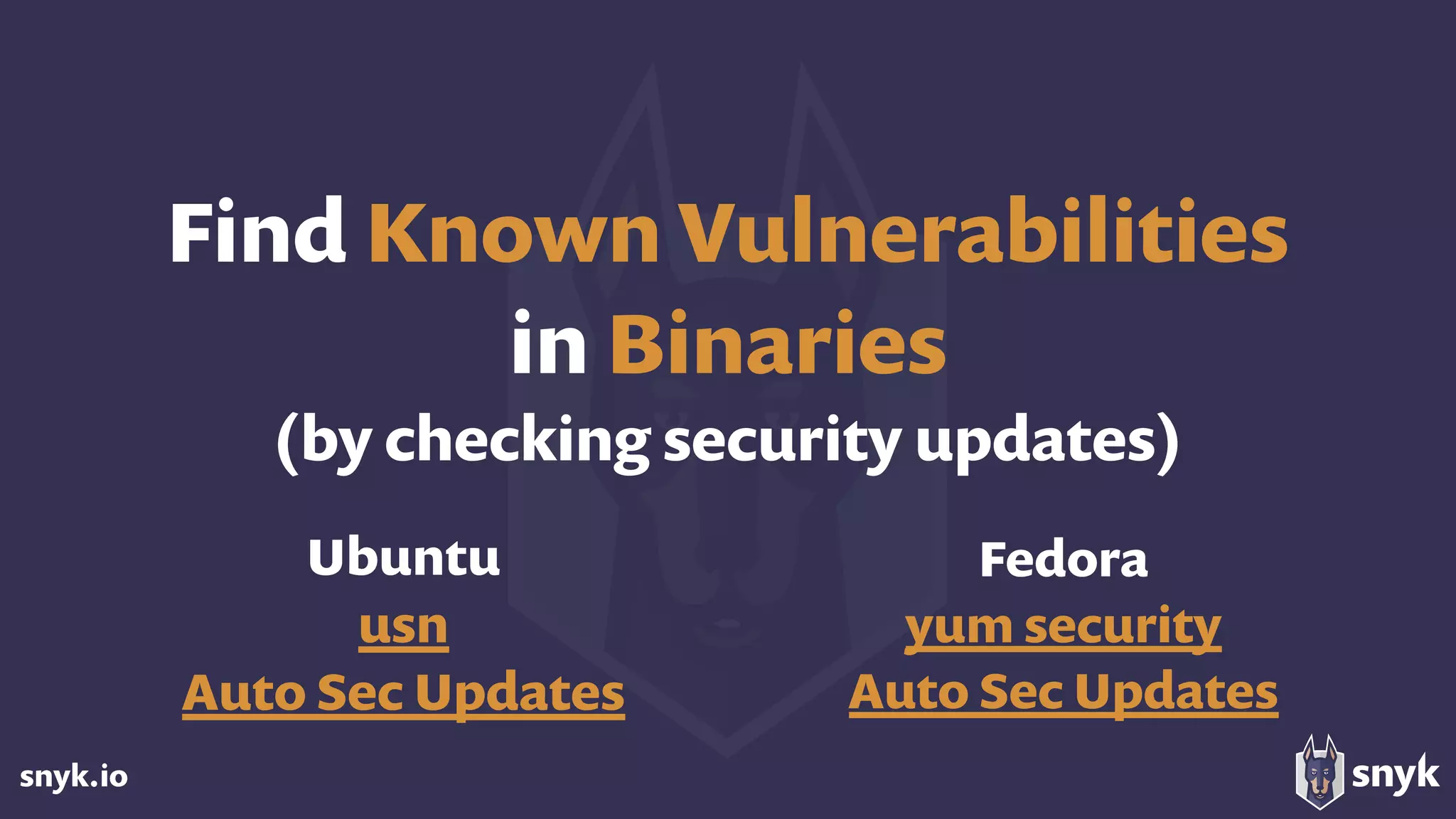
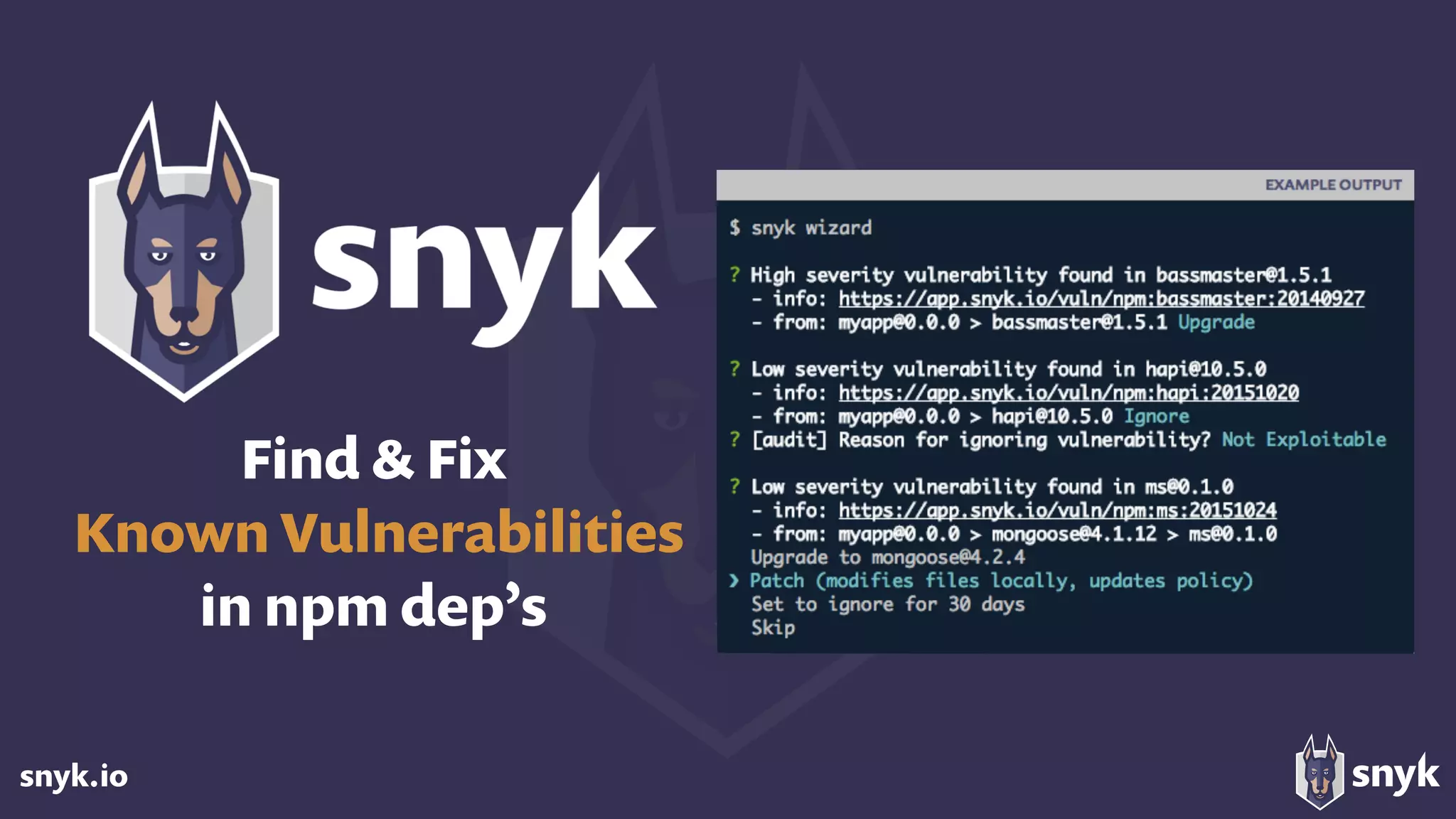
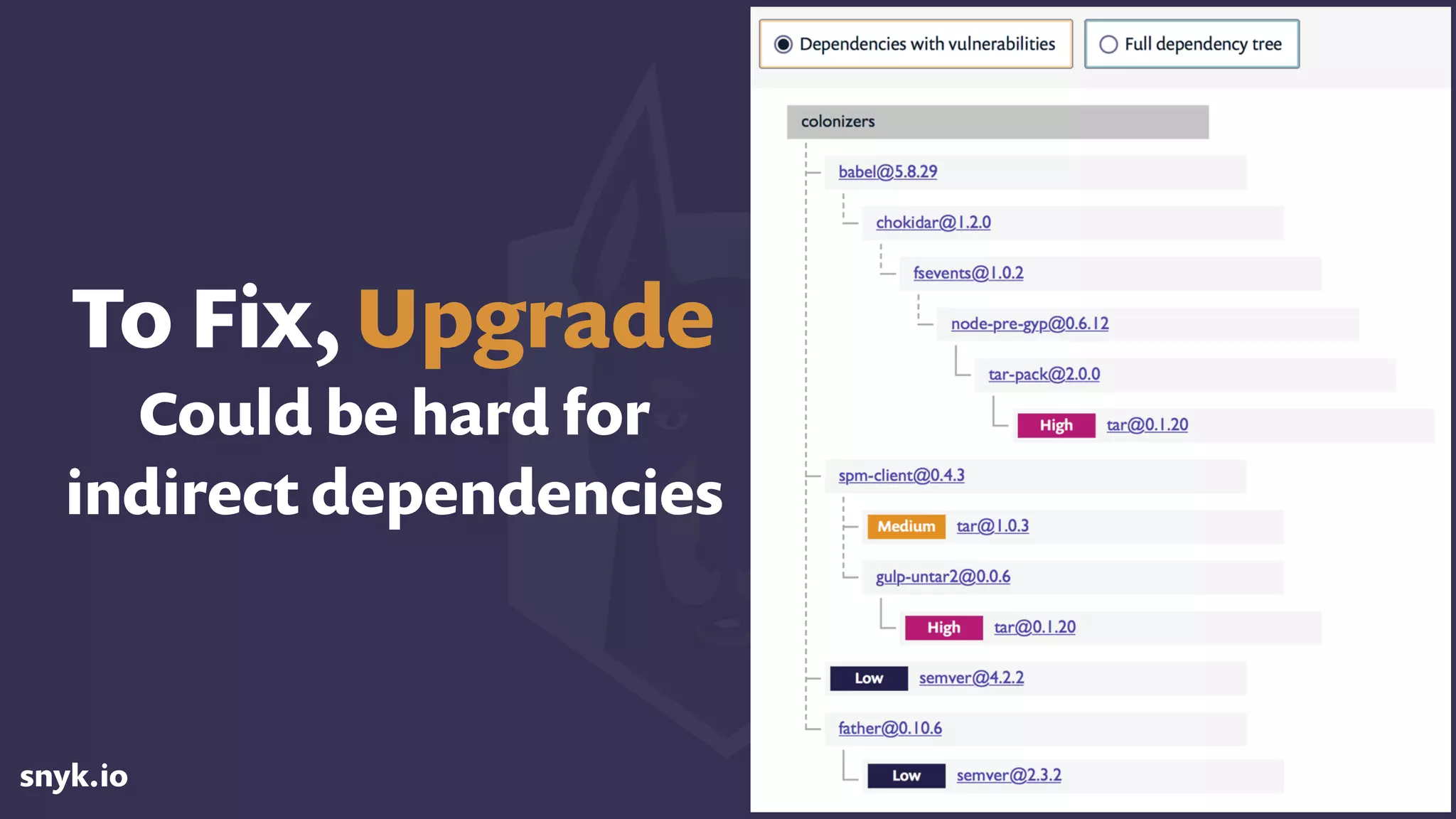
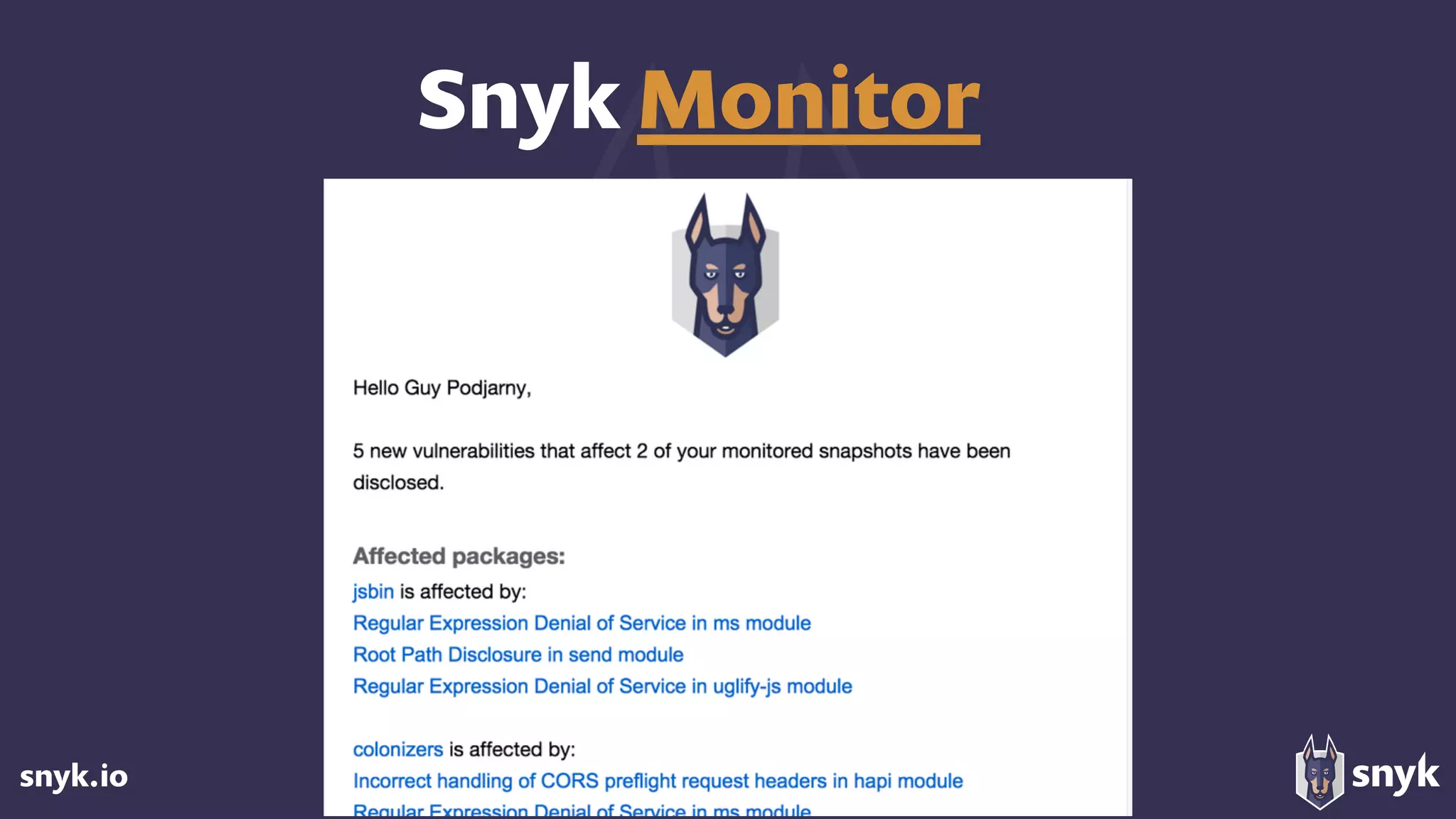
The document discusses the growing use of open-source software (OSS) and highlights security concerns associated with it, noting that 63% of enterprises express varying levels of worry over security issues. It emphasizes the importance of monitoring dependencies for vulnerabilities and implementing strategies such as tracking, updating, and fixing known security issues. Overall, it encourages a responsible approach to using OSS while remaining vigilant about potential risks.