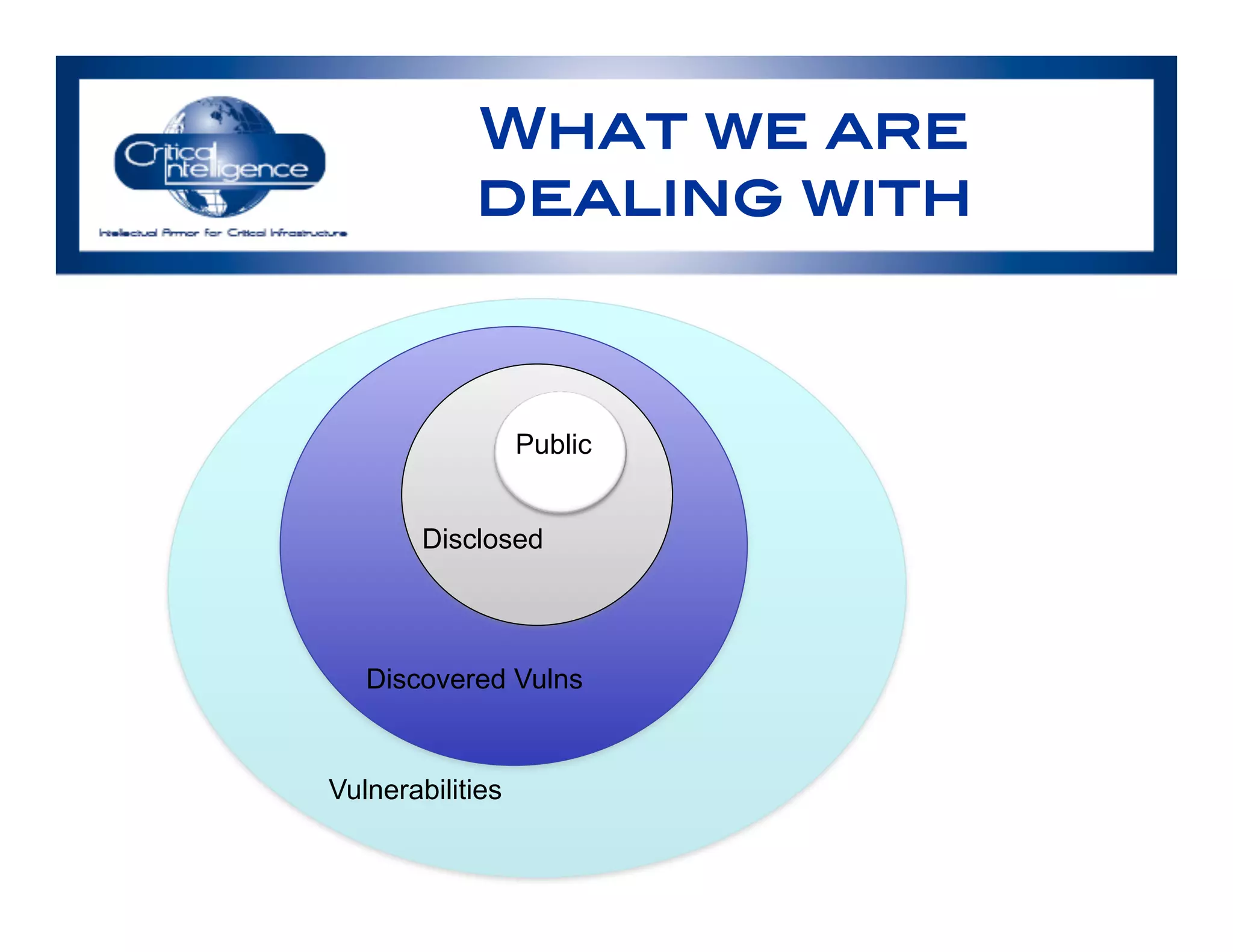
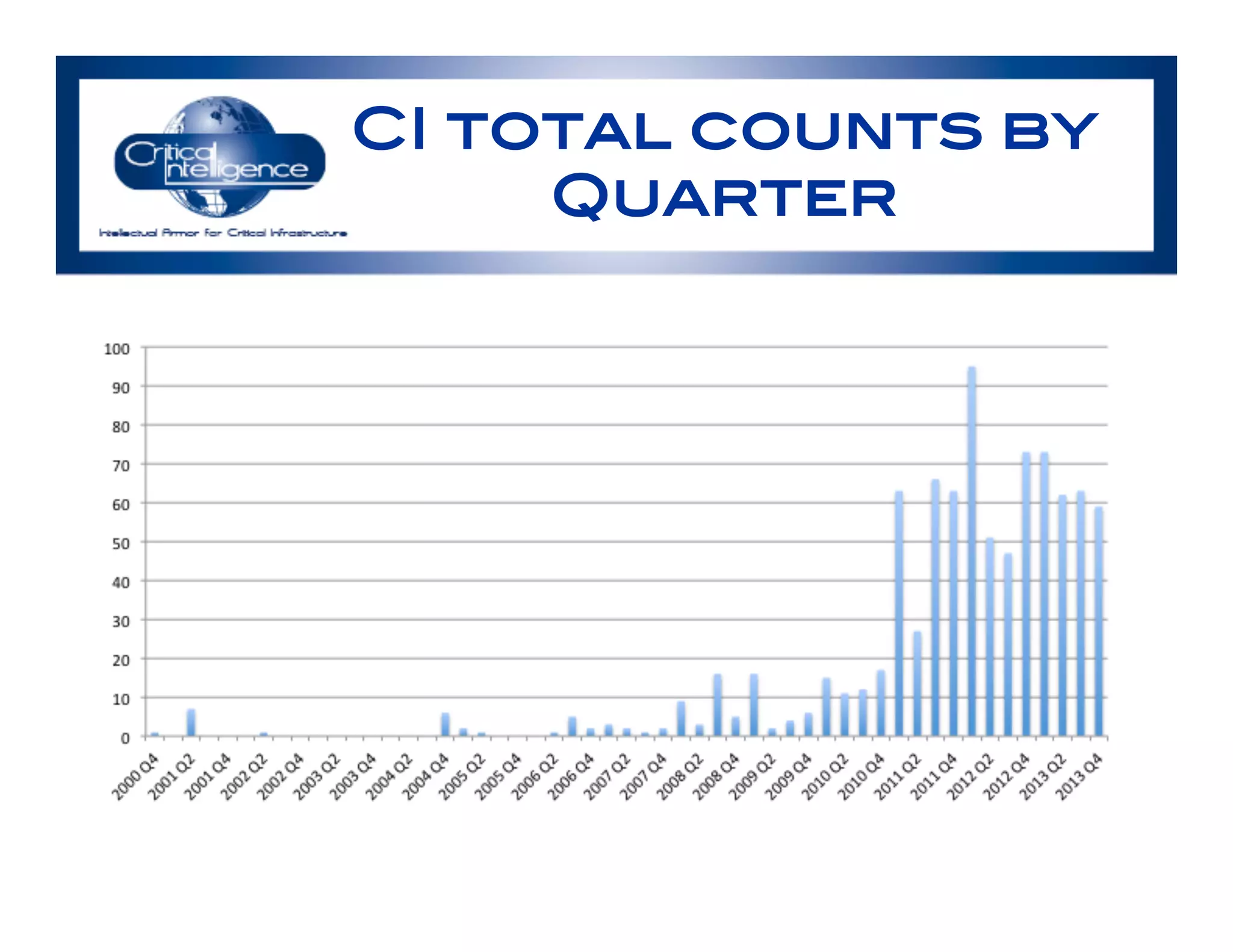
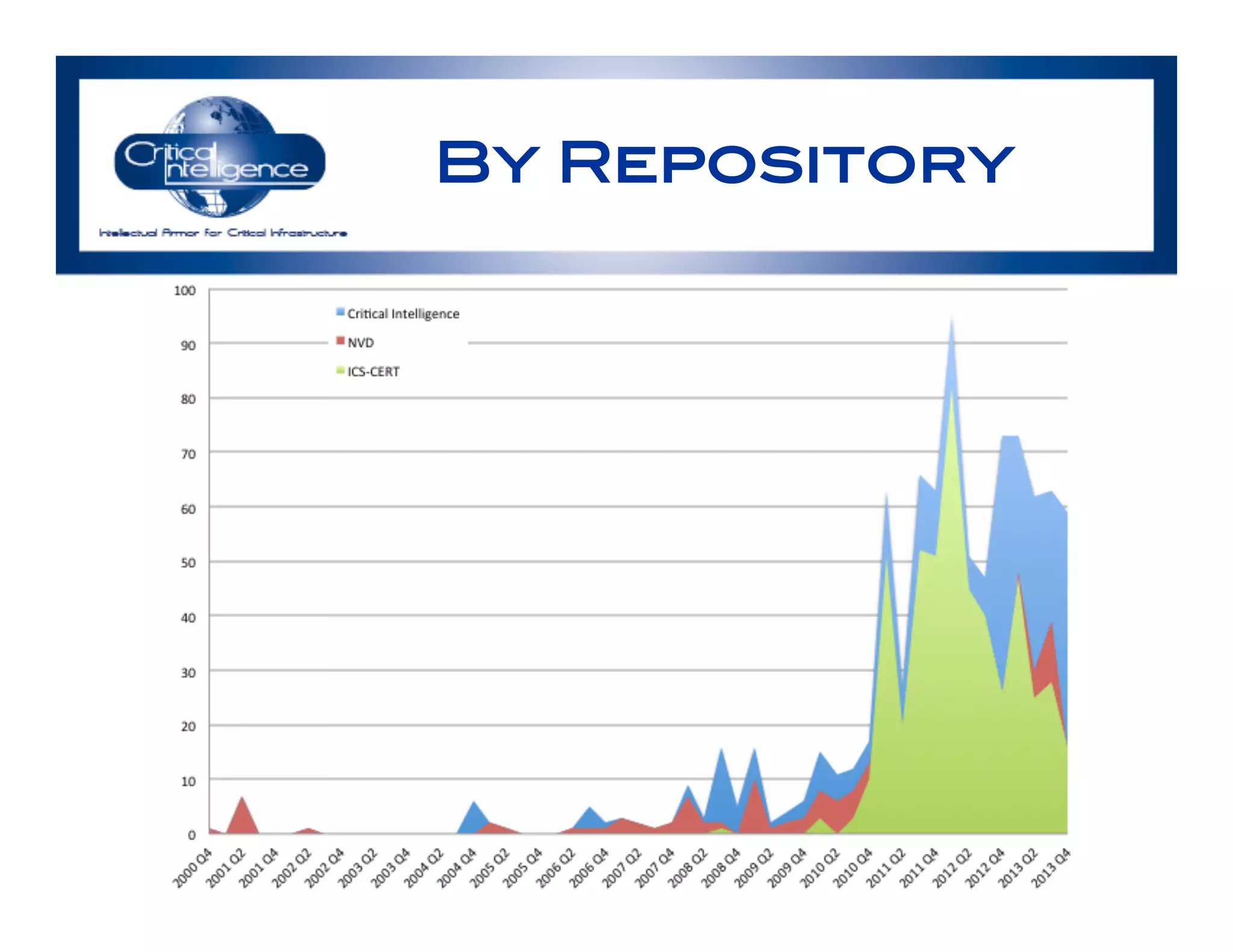
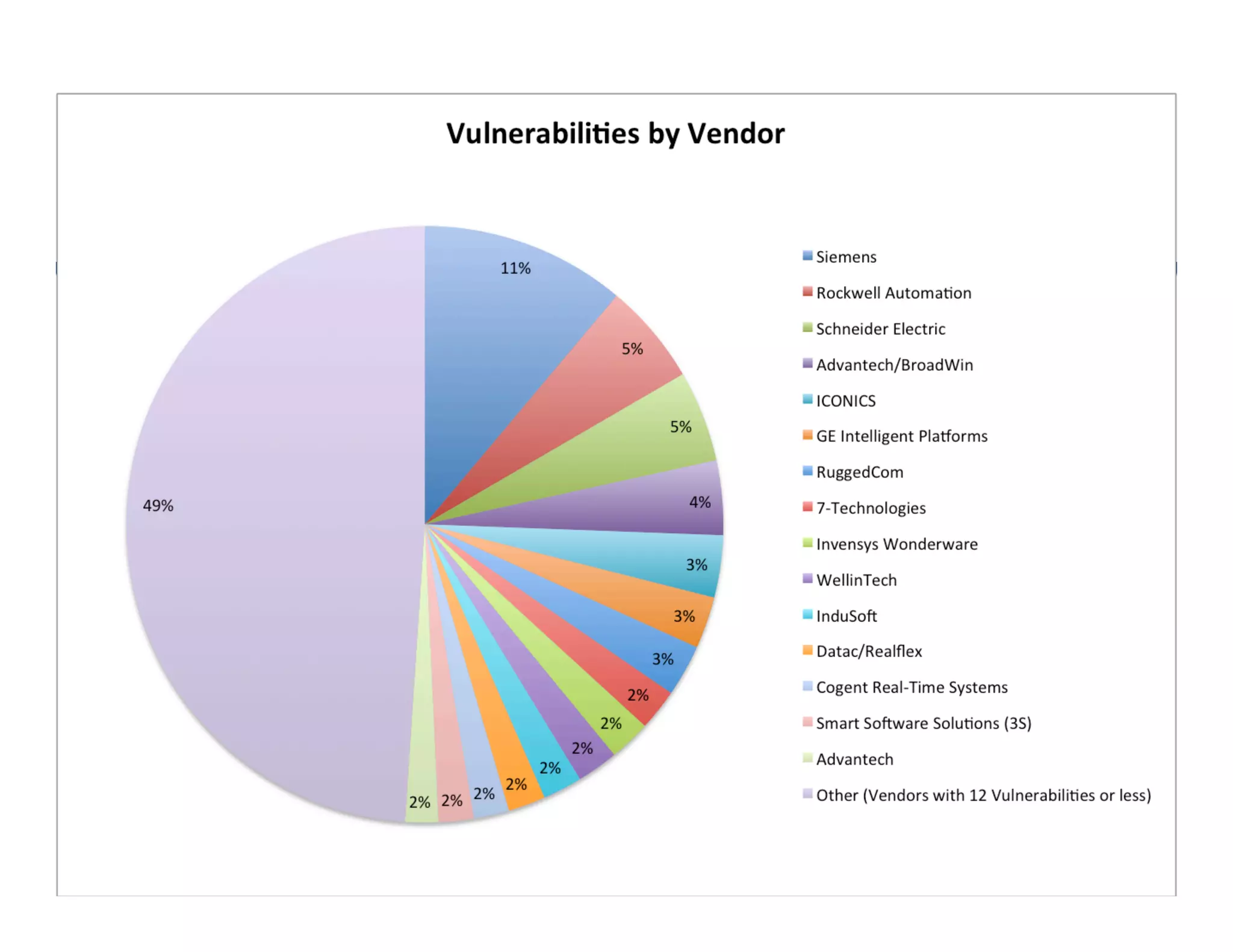
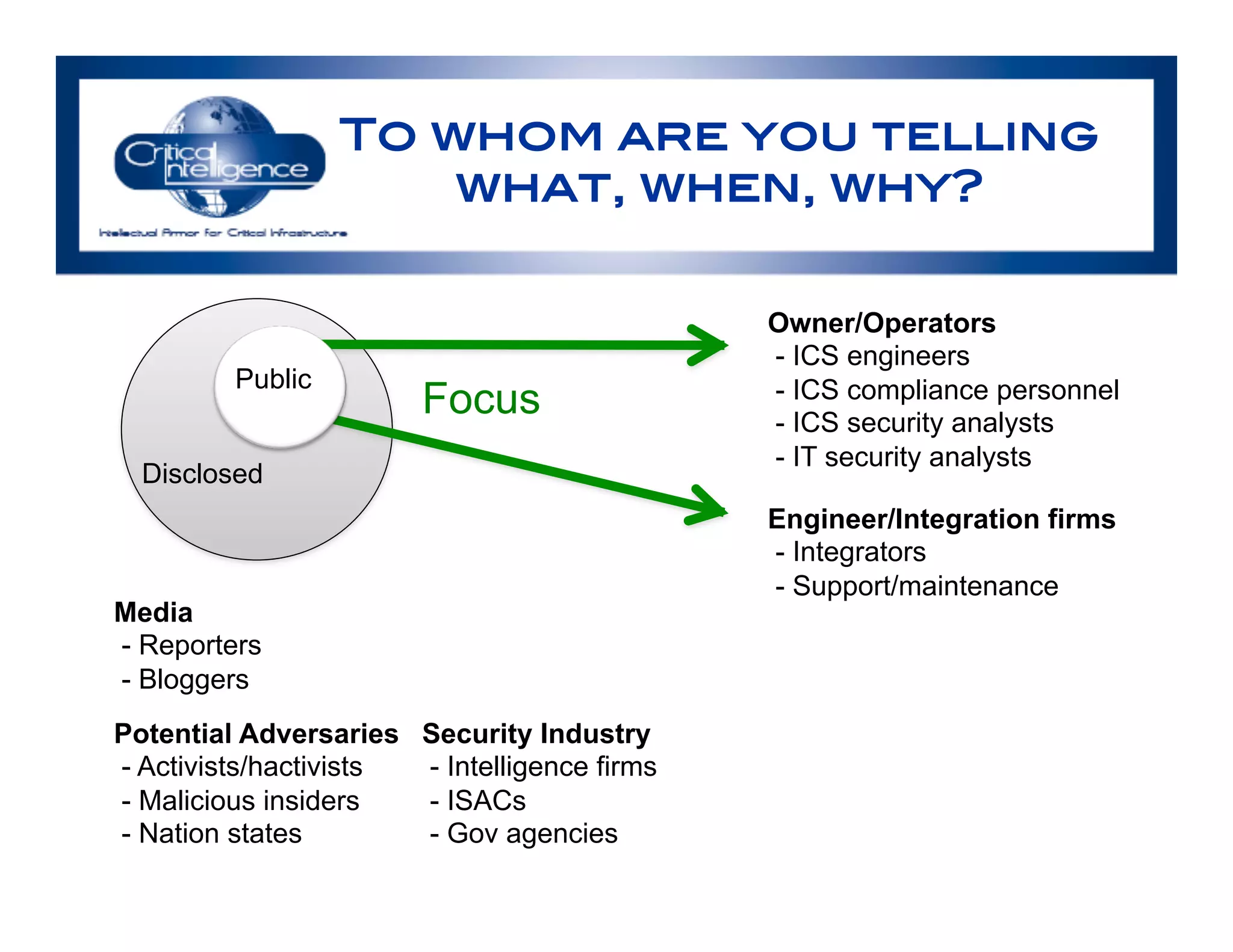
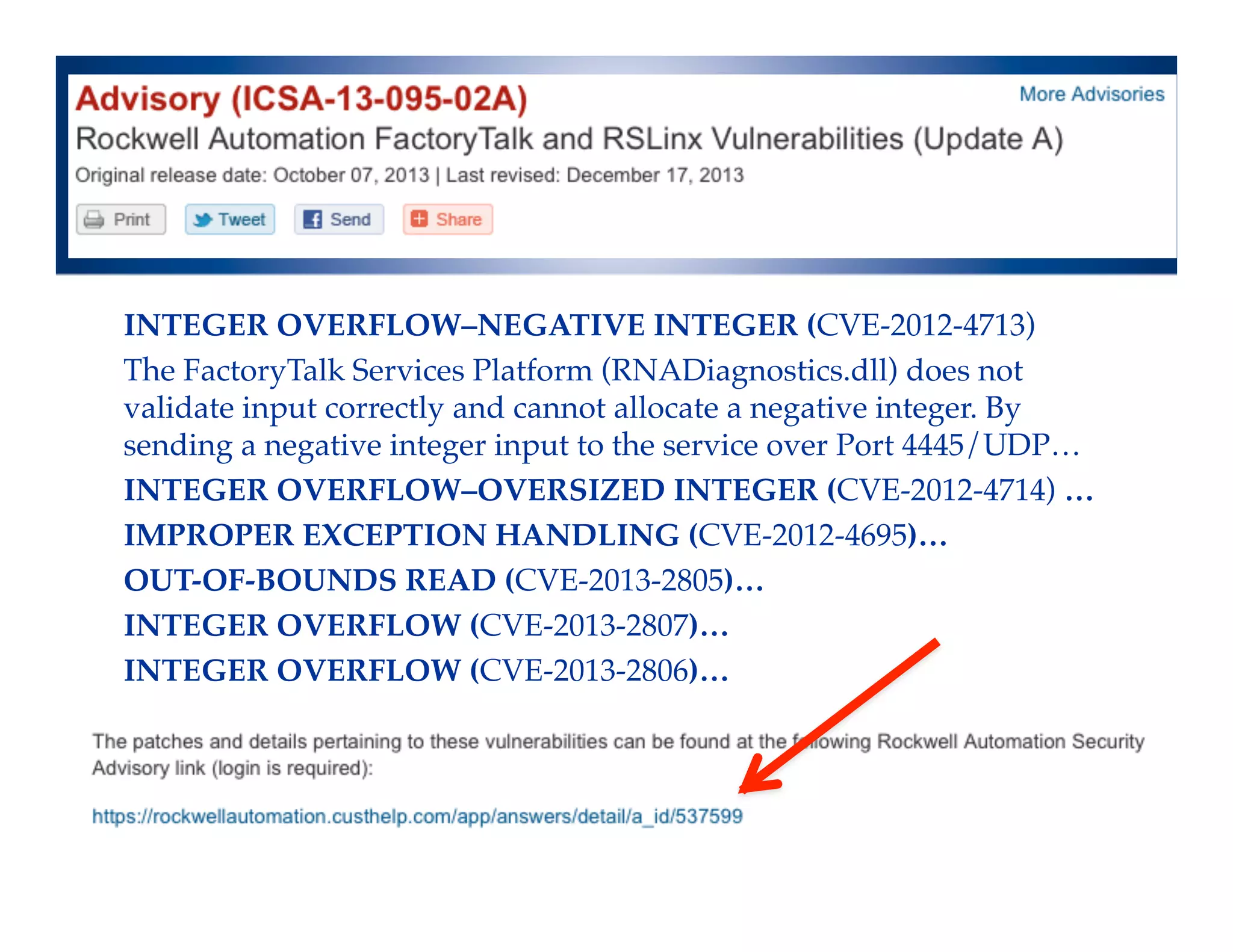
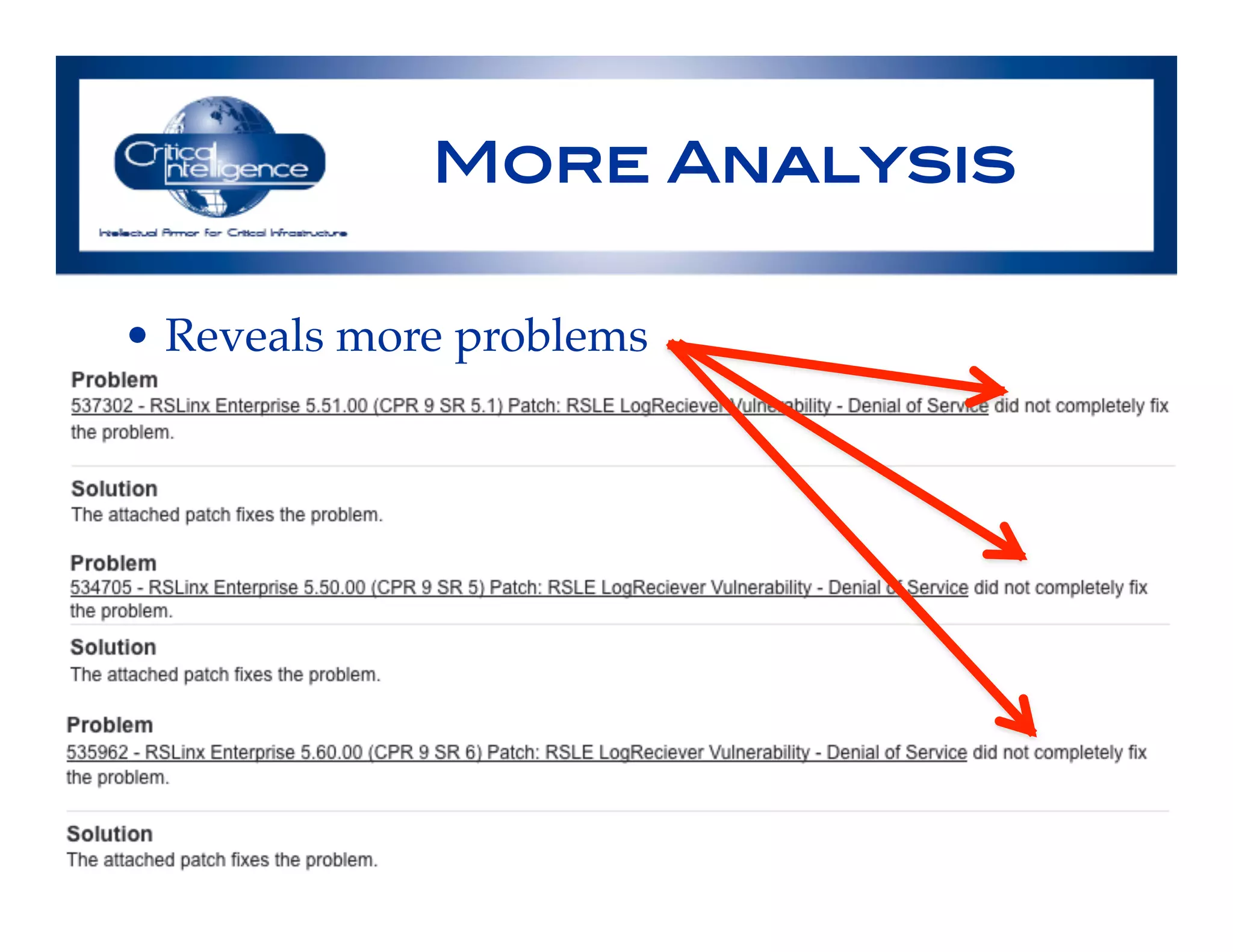
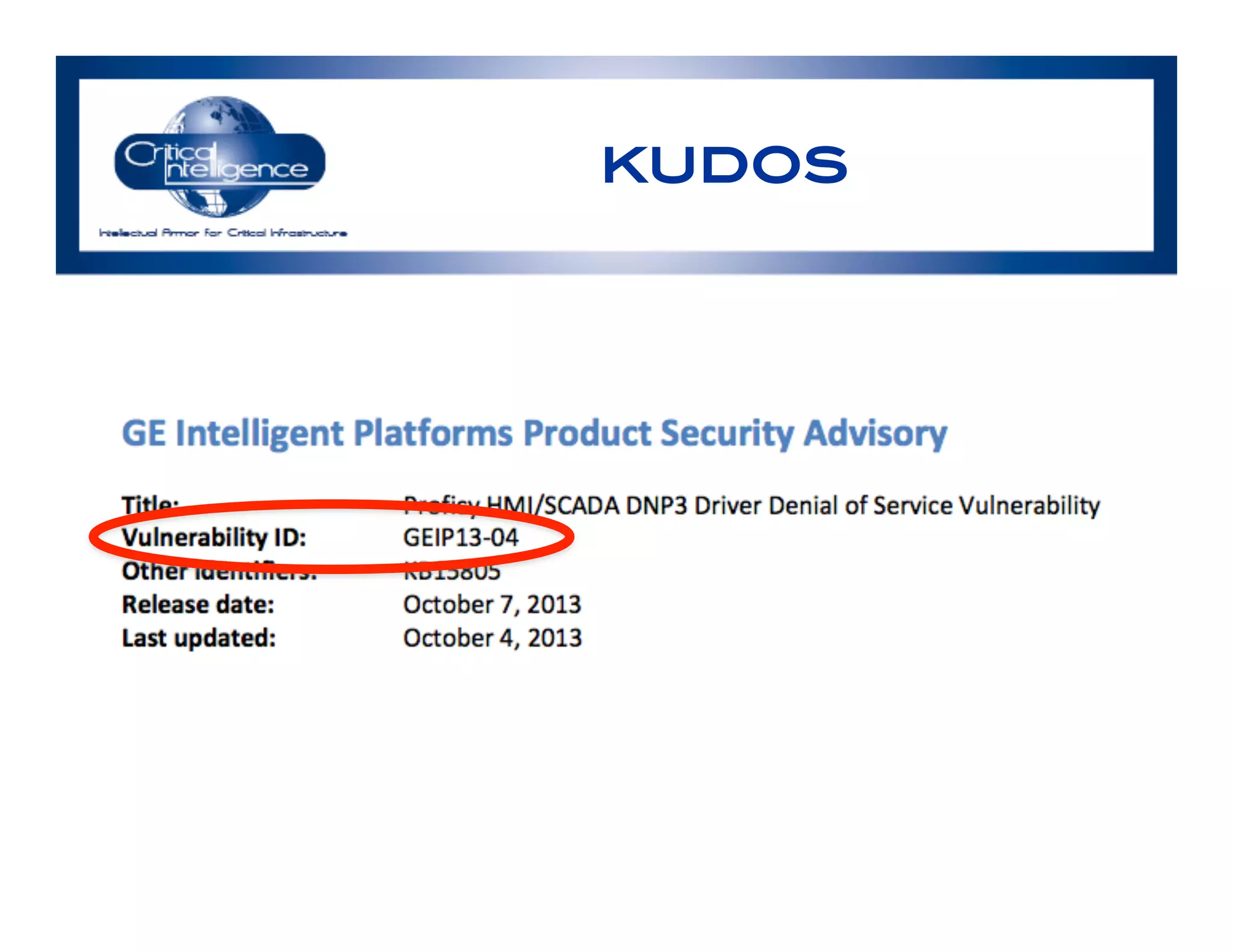
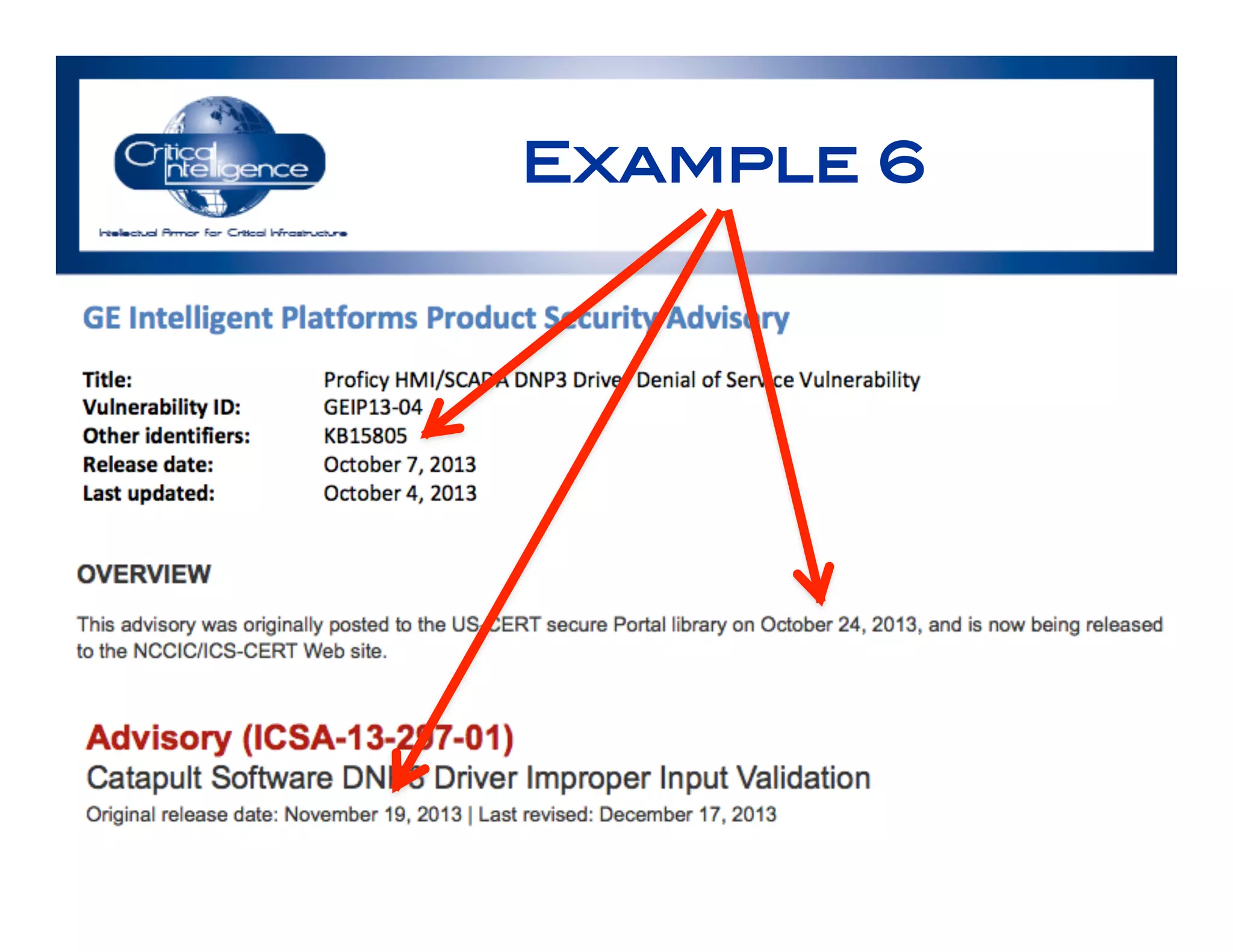
The document discusses an analysis of nearly 900 public industrial control system (ICS) vulnerabilities, highlighting the need for improved communication and analytical expertise in addressing these vulnerabilities. It provides examples of vulnerabilities found in products from major vendors like Schneider Electric and Rockwell Automation, stressing the importance of proper disclosure and context from researchers. Key lessons include the necessity of unique identifiers for vulnerabilities, the critical role of trust in customer relationships, and the need for comprehensive analysis and proofreading.






![Example 1!
(same advisory)!
During install, Read/Write access by any user is permitted to MiCOM S1
Studio executables in the Program Files directory. This condition persists after
installation. As a result of this access, the configuration files and the Windows
service used by the program can be manipulated or modified by any user with
local computer access.!
!
Schneider Electric has released a new version of MiCOM S1 Studio SW,
V4.0.1, to address some of these vulnerabilities. The installation routine of
MiCOM 1 Studio V4.0.1 provides digital signature to all files related to the
use of MiCOM S1 Studio: Digital signature indicates [to] operating systems
and user that the libraries/executables are from Schneider Electric (Trusted
source).!](https://image.slidesharecdn.com/icsvulnerabilityanalysismcbride-nn11-140401112857-phpapp01/75/Writing-ICS-Vulnerability-Analysis-13-2048.jpg)













![Example 7!
January 2014 Advisory!
Affected Products!
-------------------!
The following [Vendor] versions are affected:!
• All versions released prior to December 1, 2013, !
• [Vendor Product Number] (Firmware from 2010), and !
• [Vendor Product Number] (Latest Firmware).!
!
!](https://image.slidesharecdn.com/icsvulnerabilityanalysismcbride-nn11-140401112857-phpapp01/75/Writing-ICS-Vulnerability-Analysis-31-2048.jpg)




