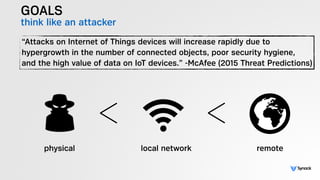
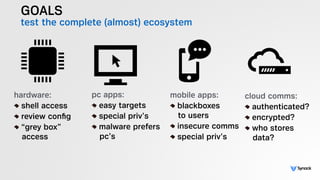
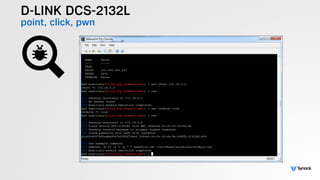
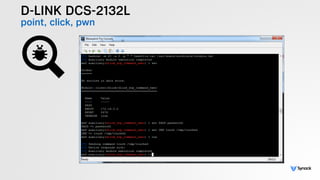
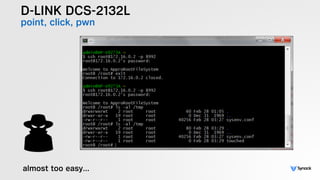
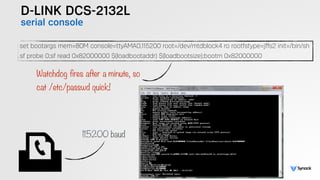
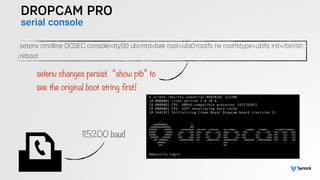
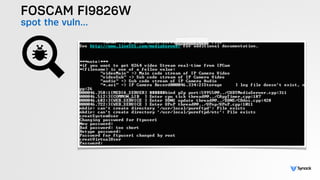
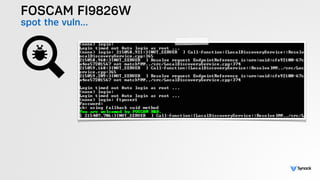
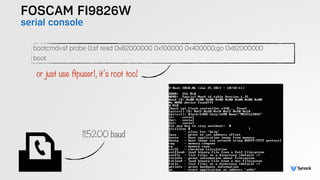
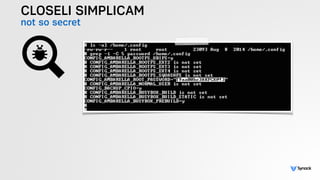
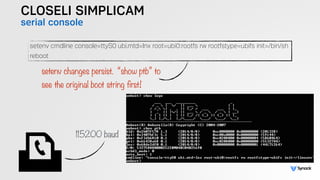
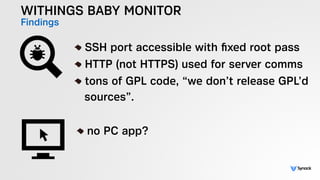
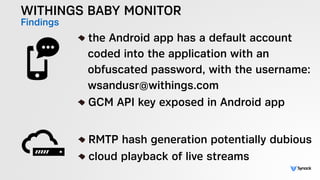
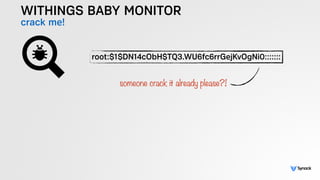
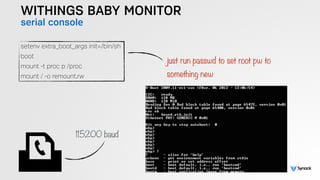
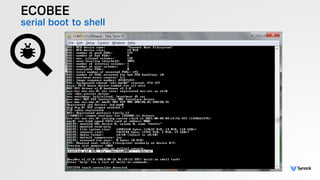
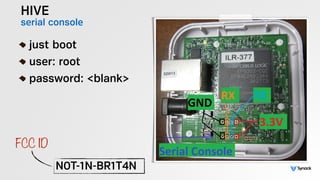
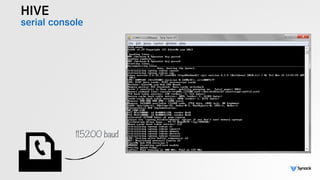
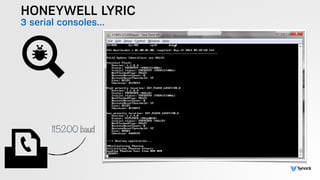
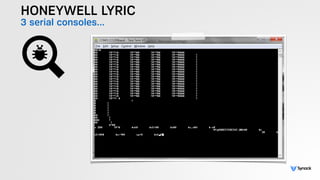
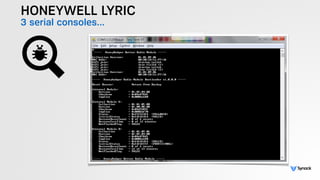
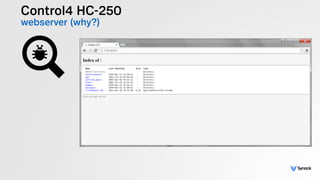
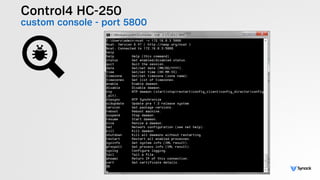
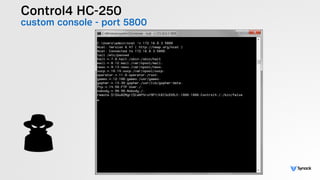
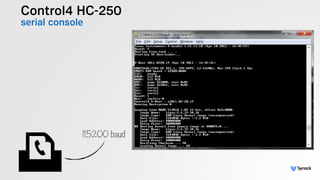
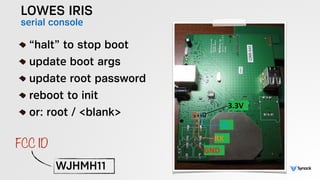
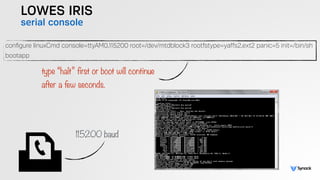
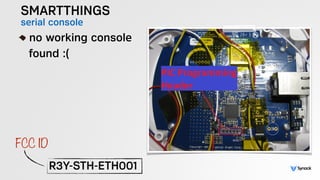
The document presents the findings from testing 14 different IoT devices, detailing various security vulnerabilities related to hardware, PC apps, mobile apps, and cloud communications. Key issues identified include insecure communications, the presence of default passwords, and lack of certificate pinning across many devices. The testing employed a range of techniques aimed at understanding how these devices can be compromised, highlighting concerns about the rapid growth of connected devices and their security implications.