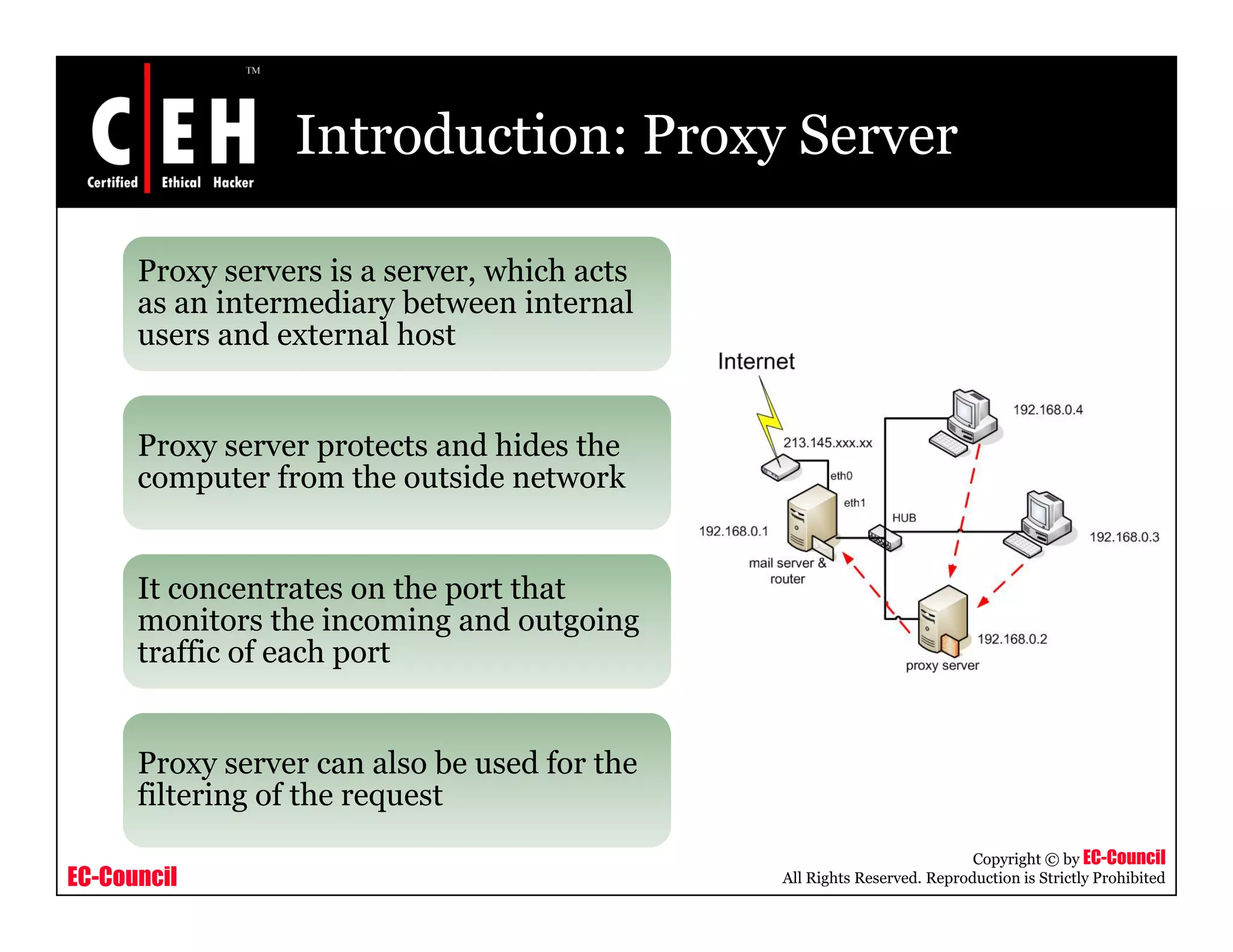
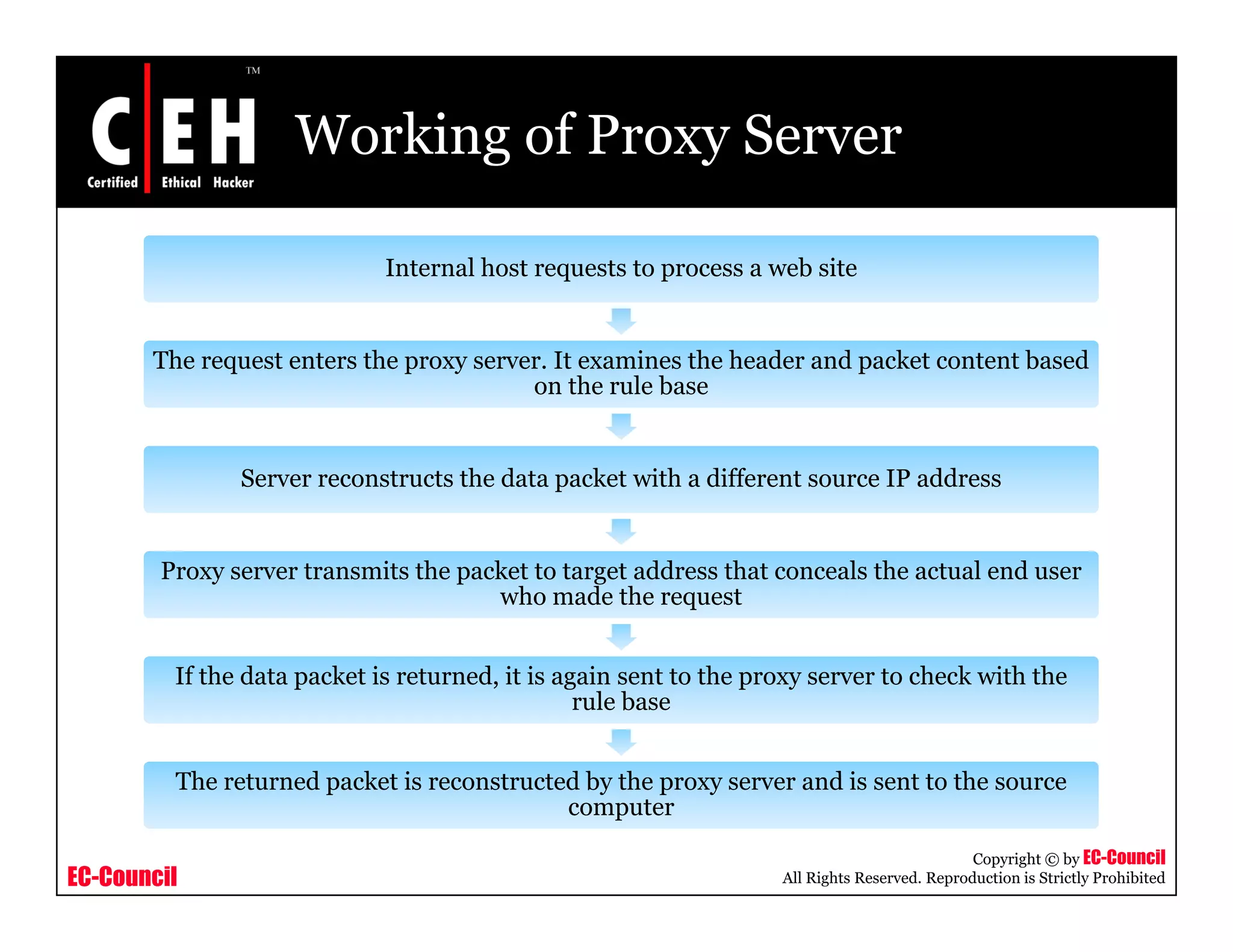
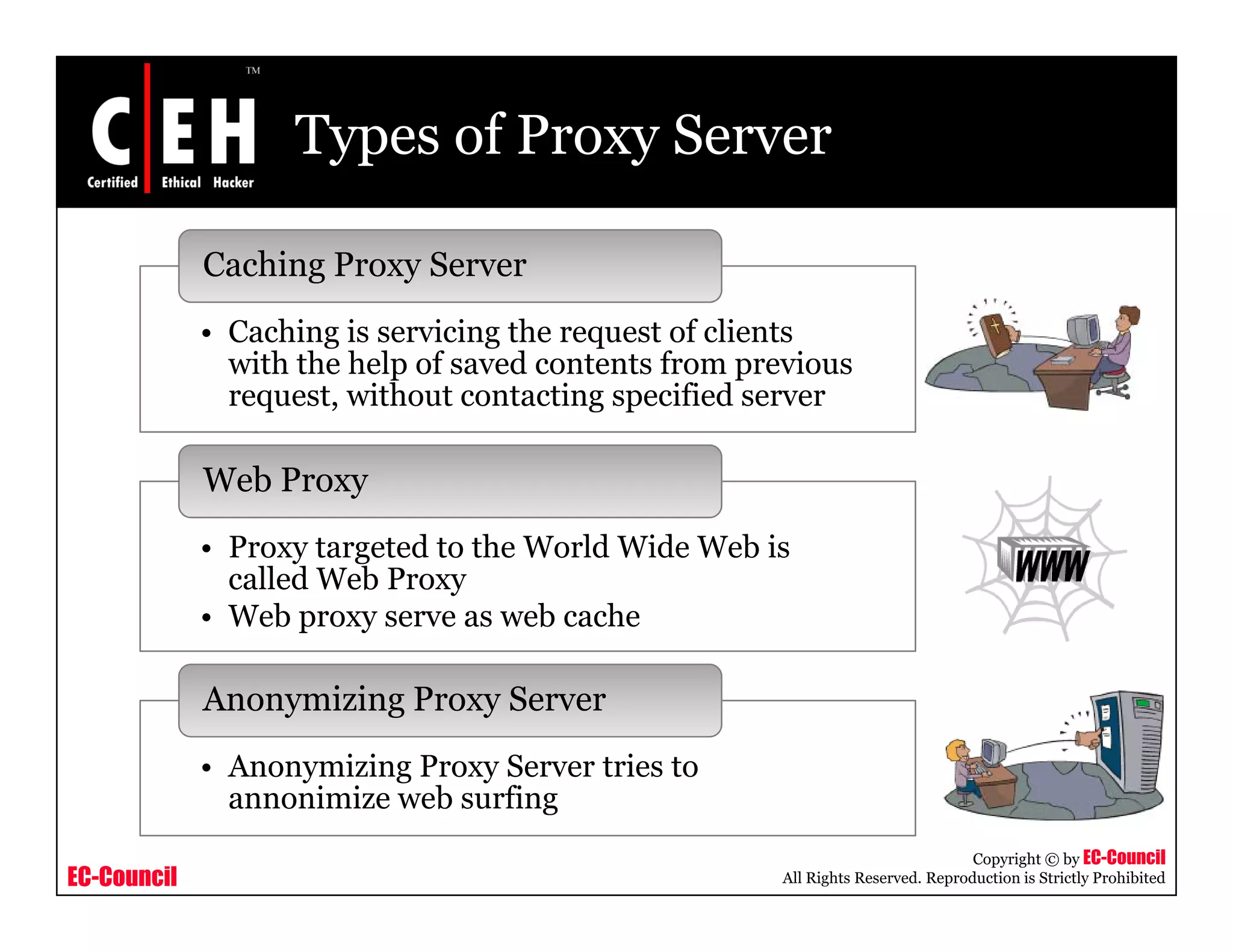
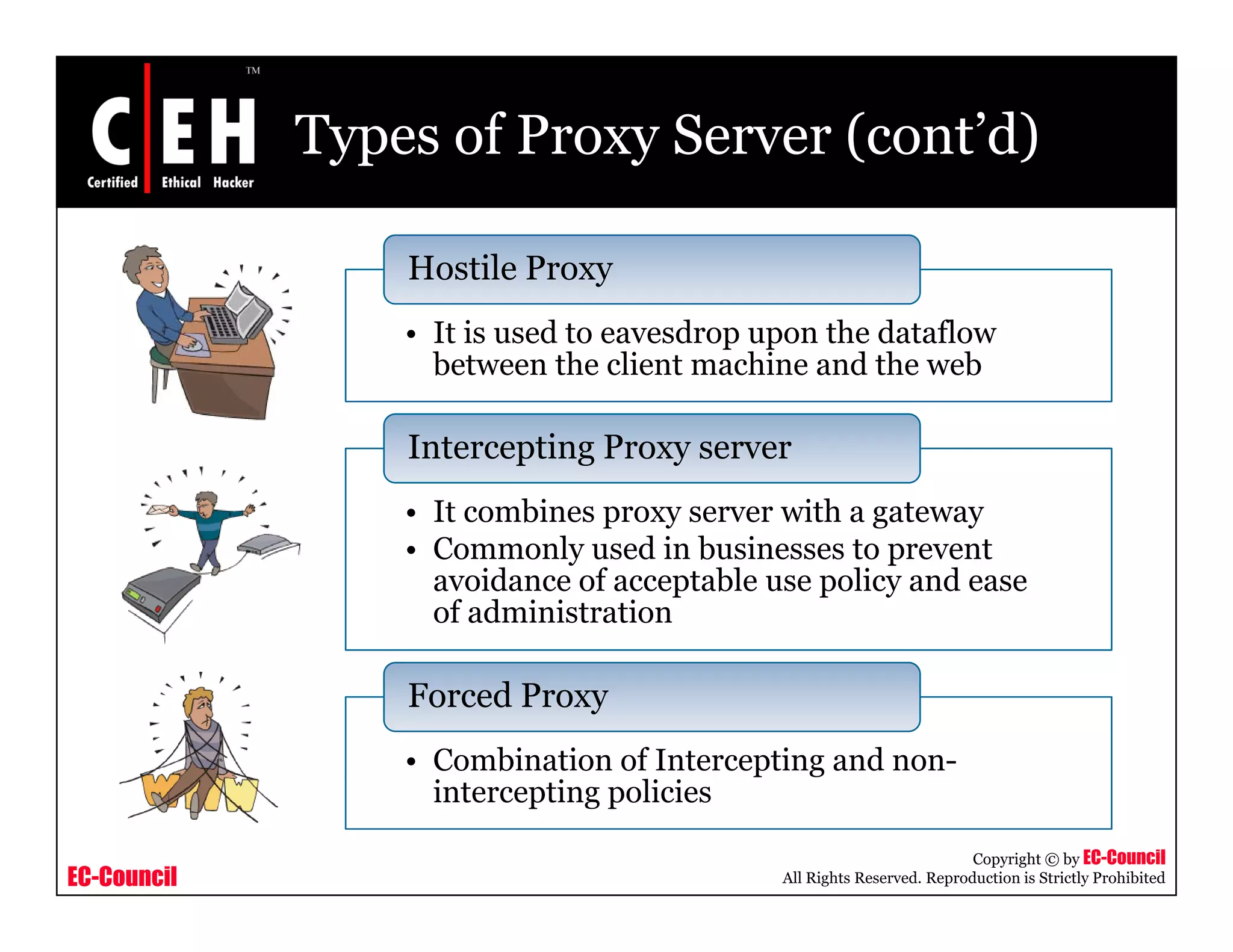
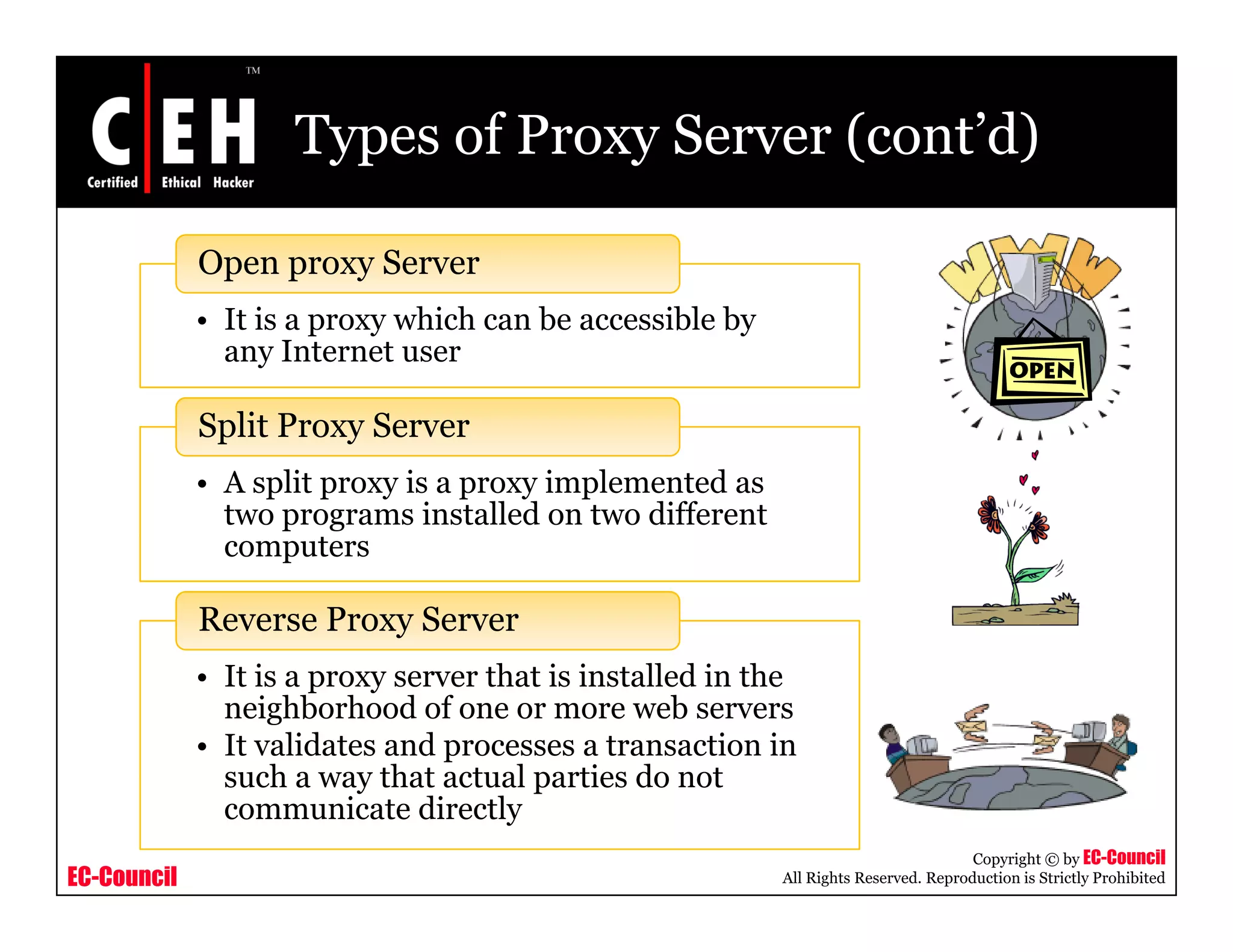
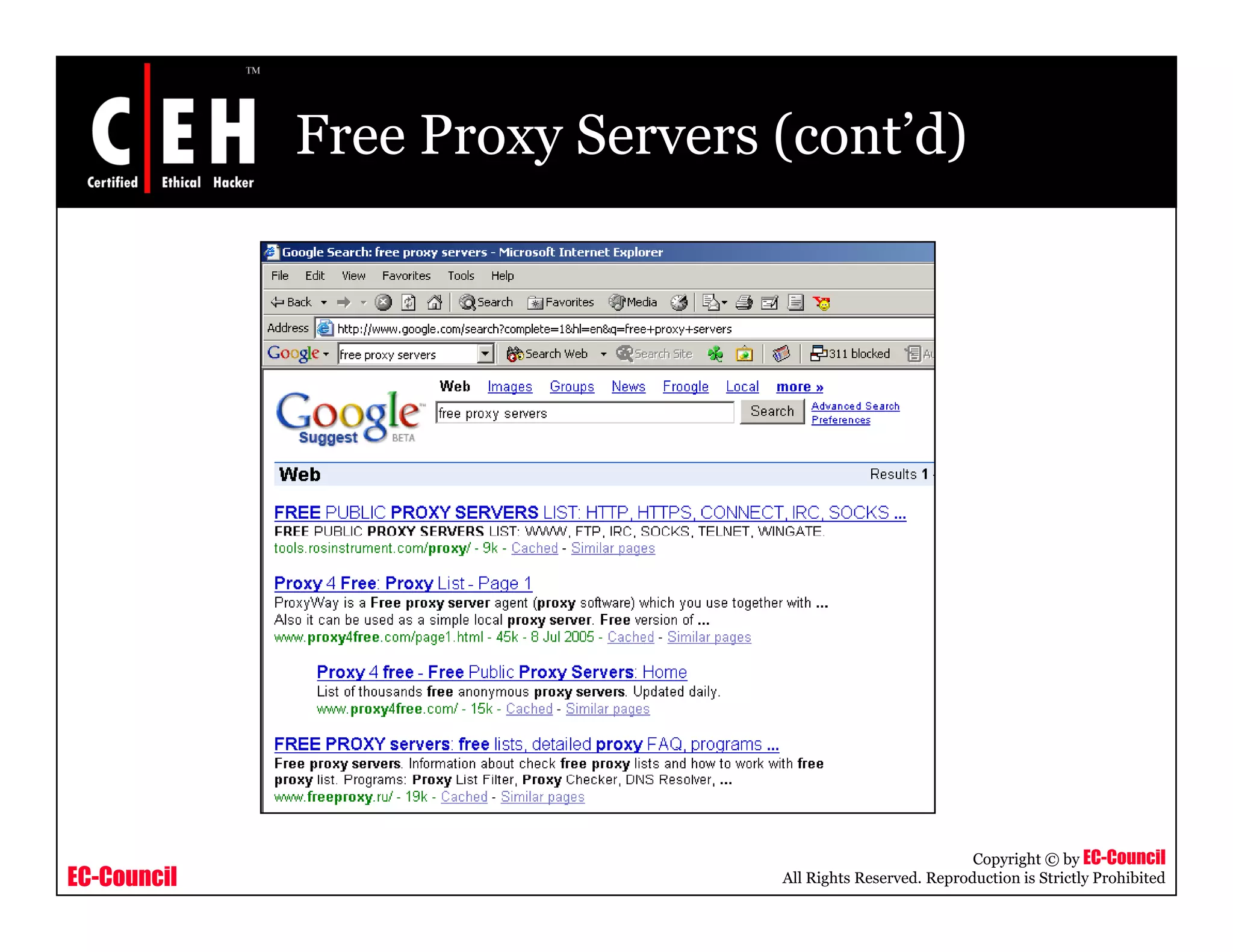
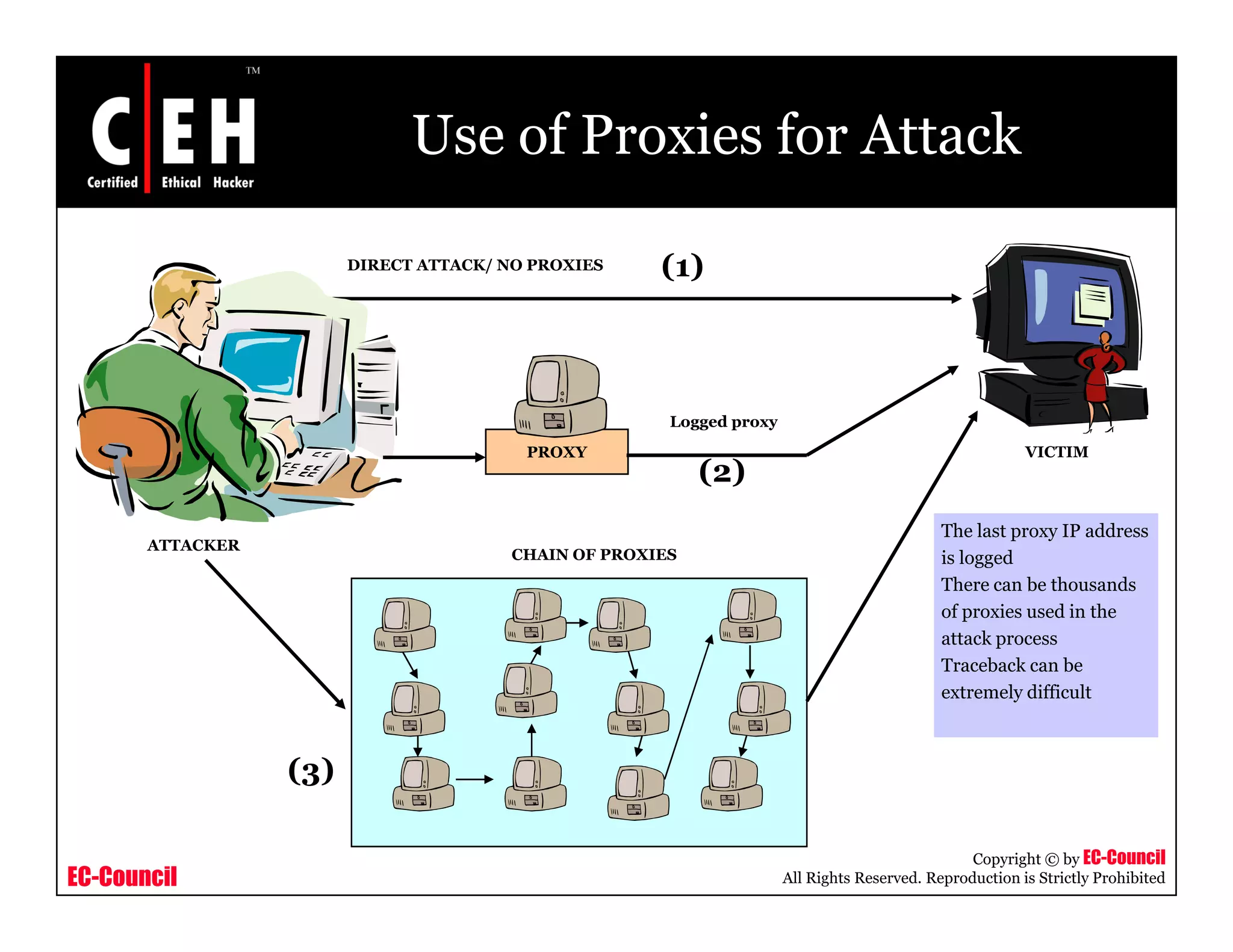
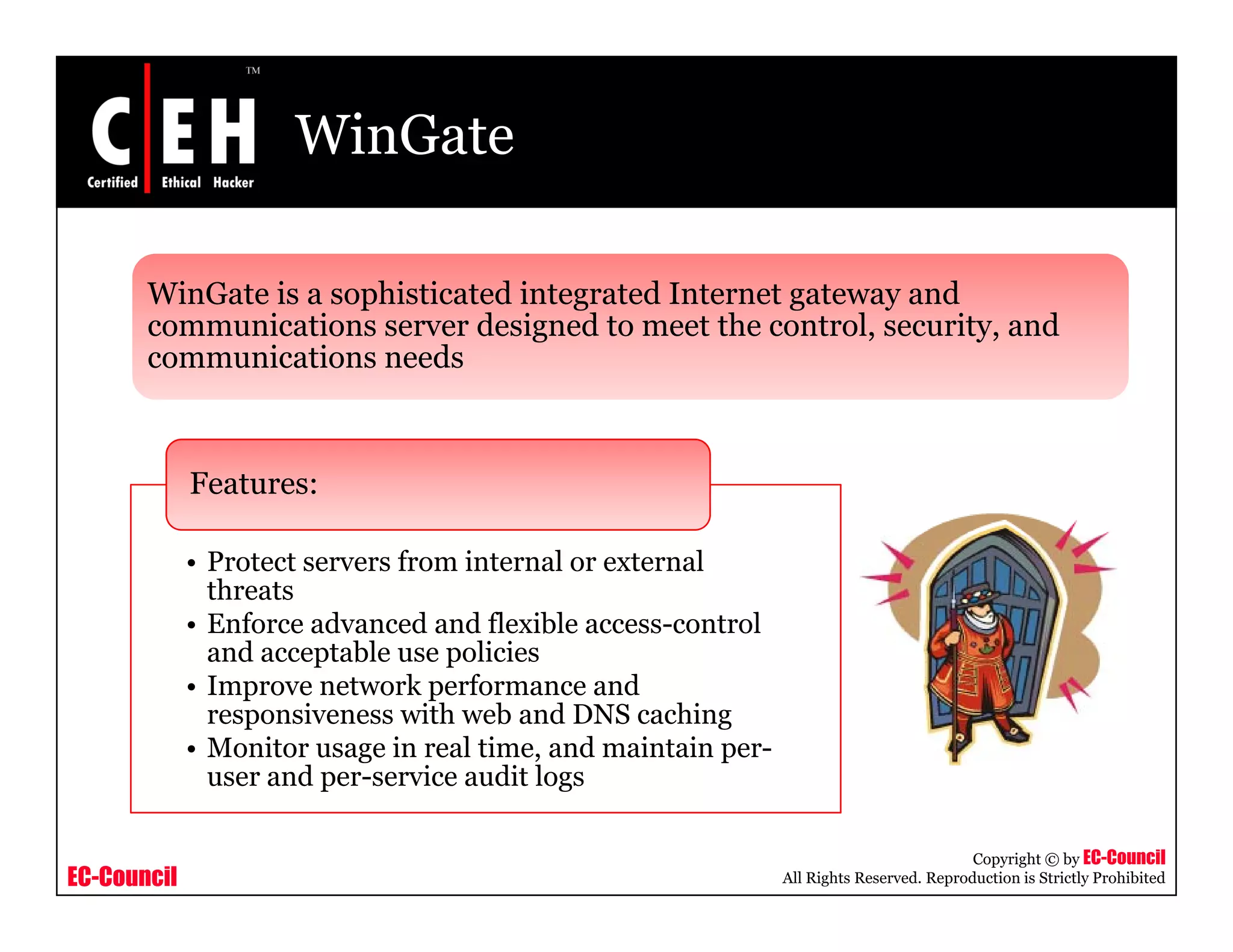
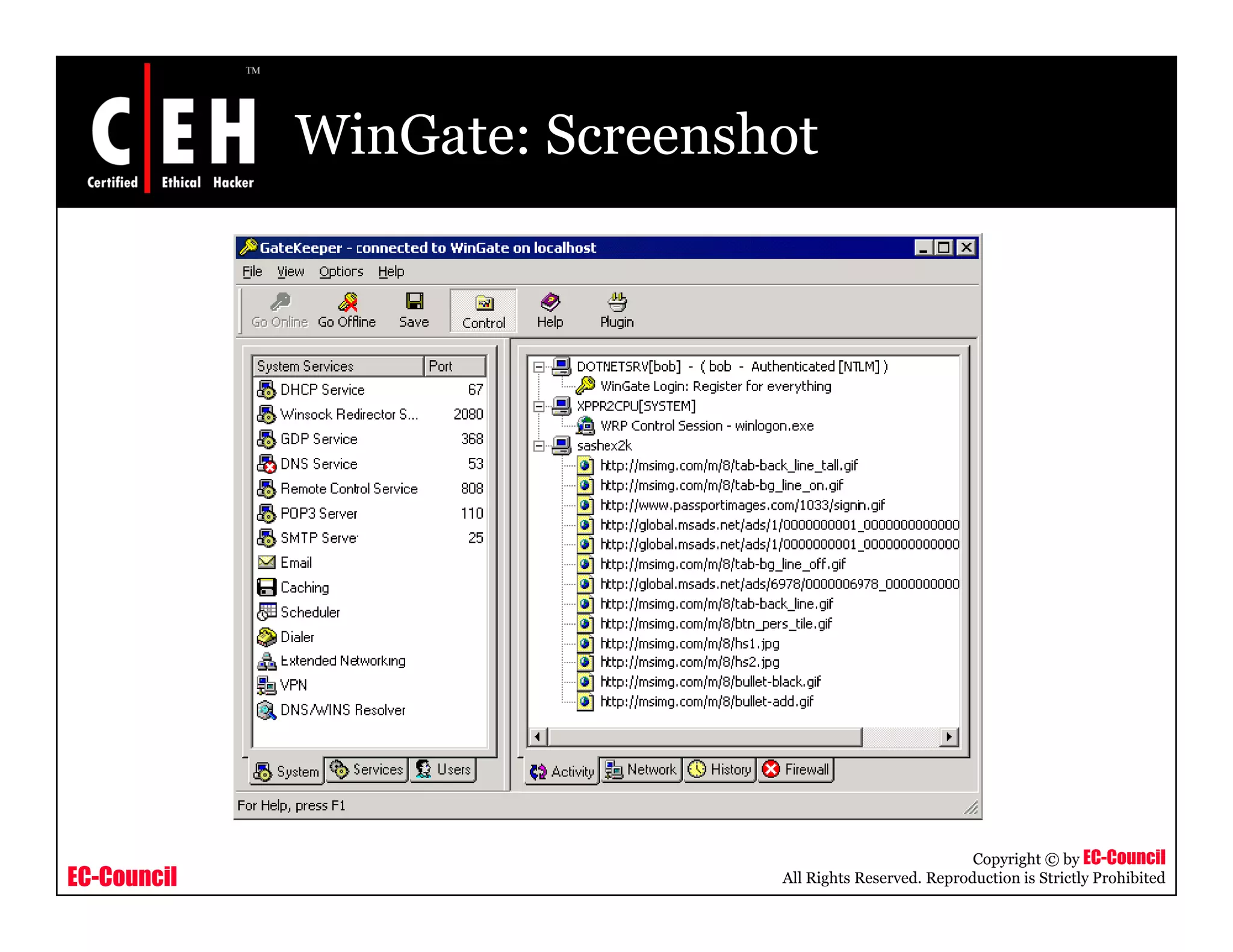
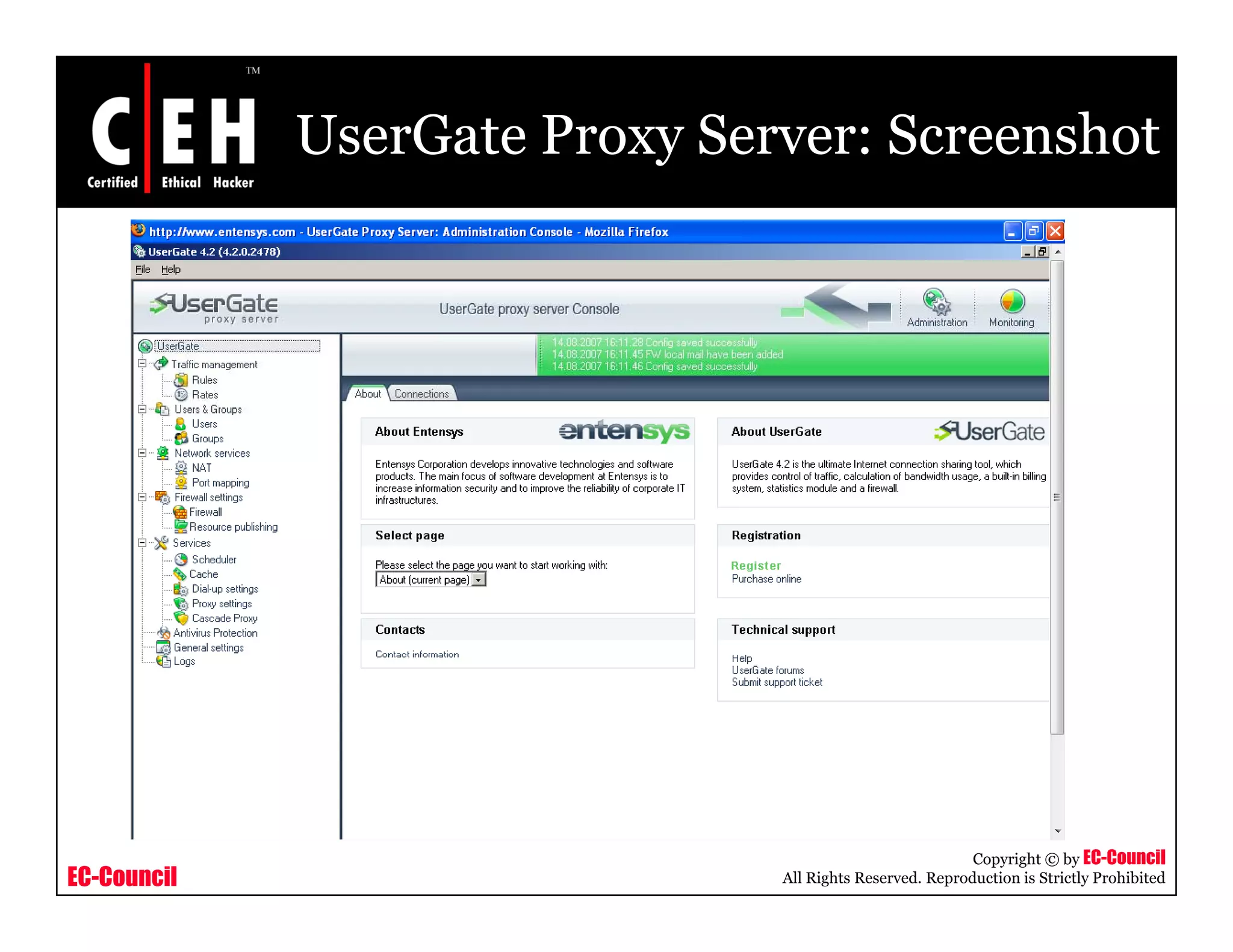
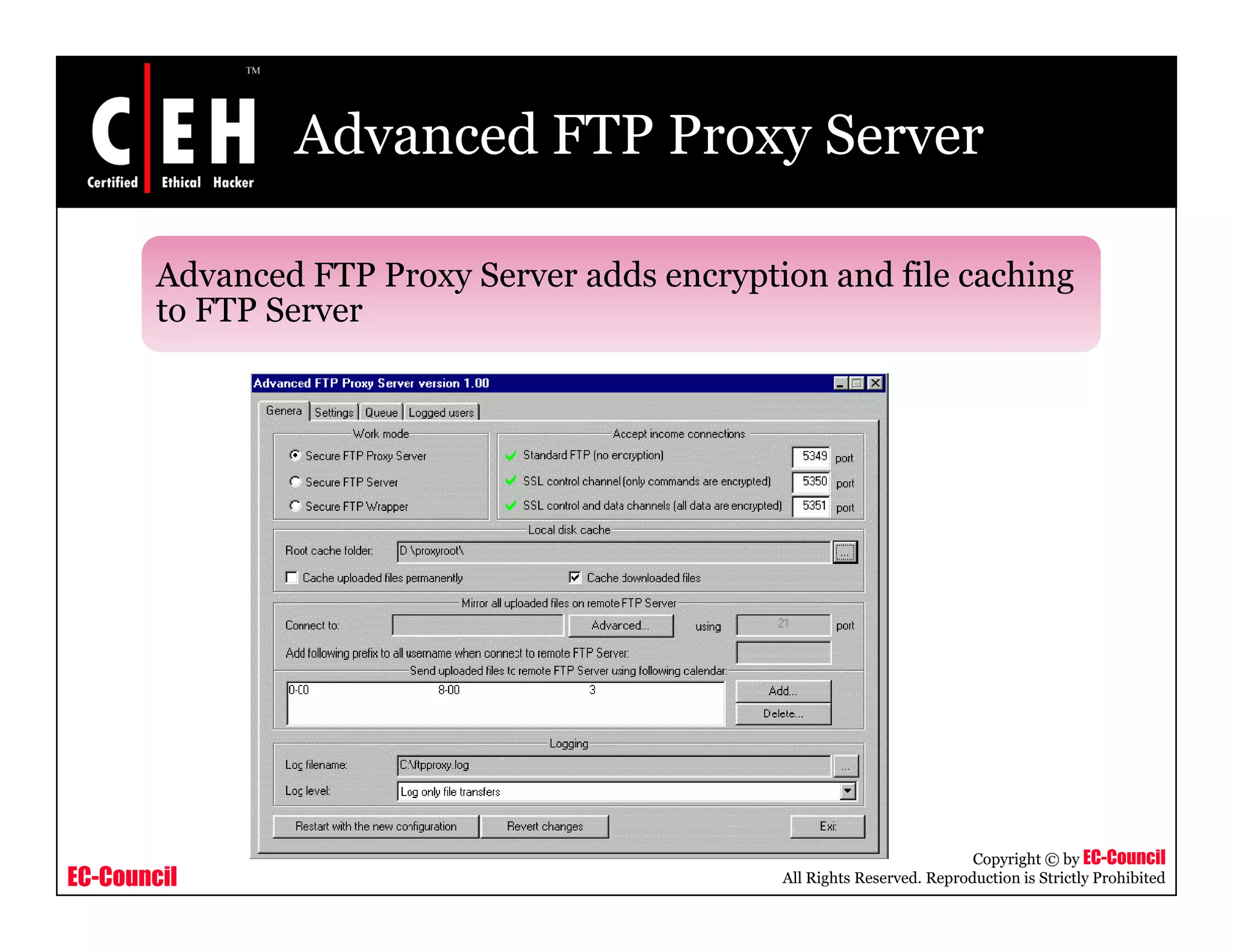
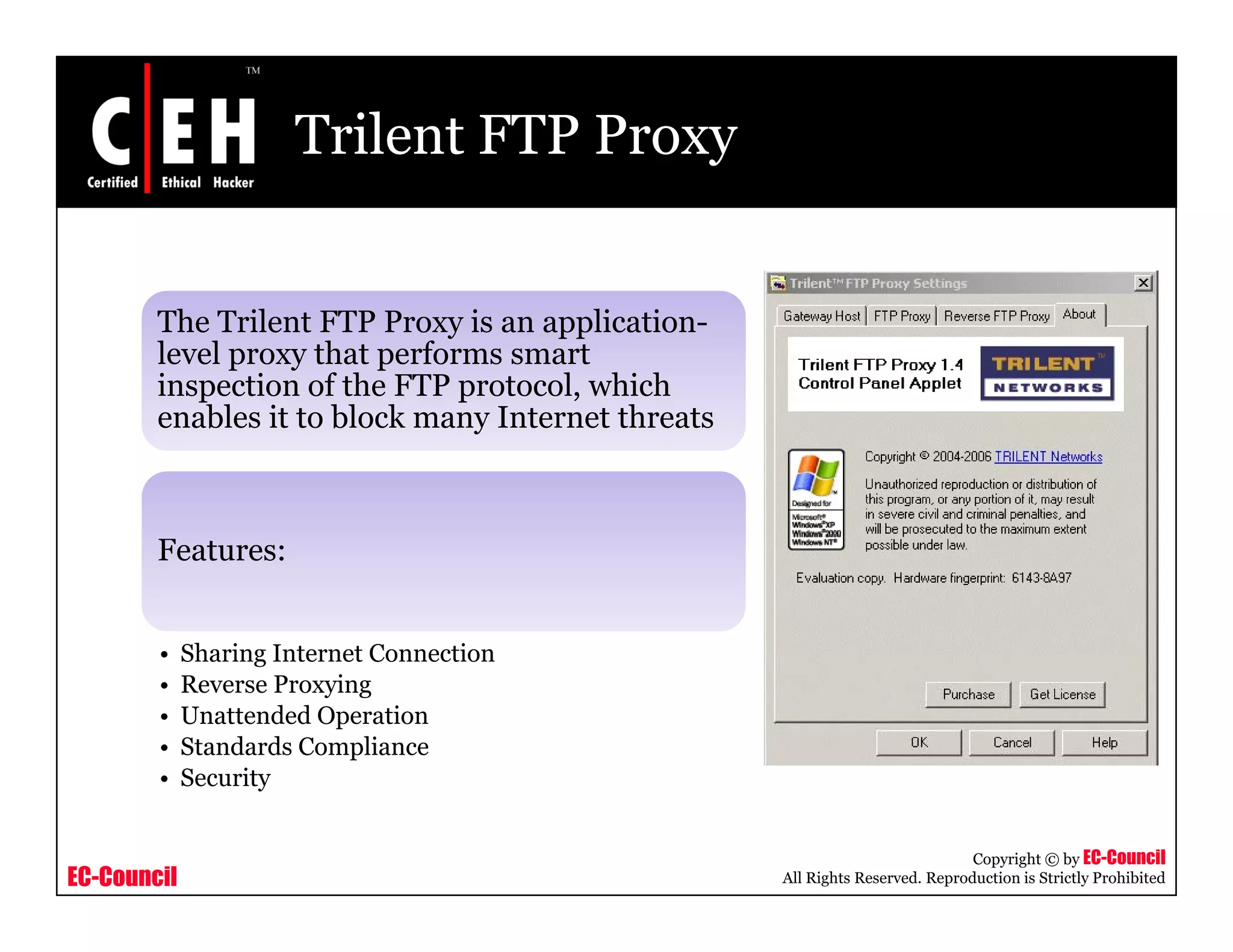
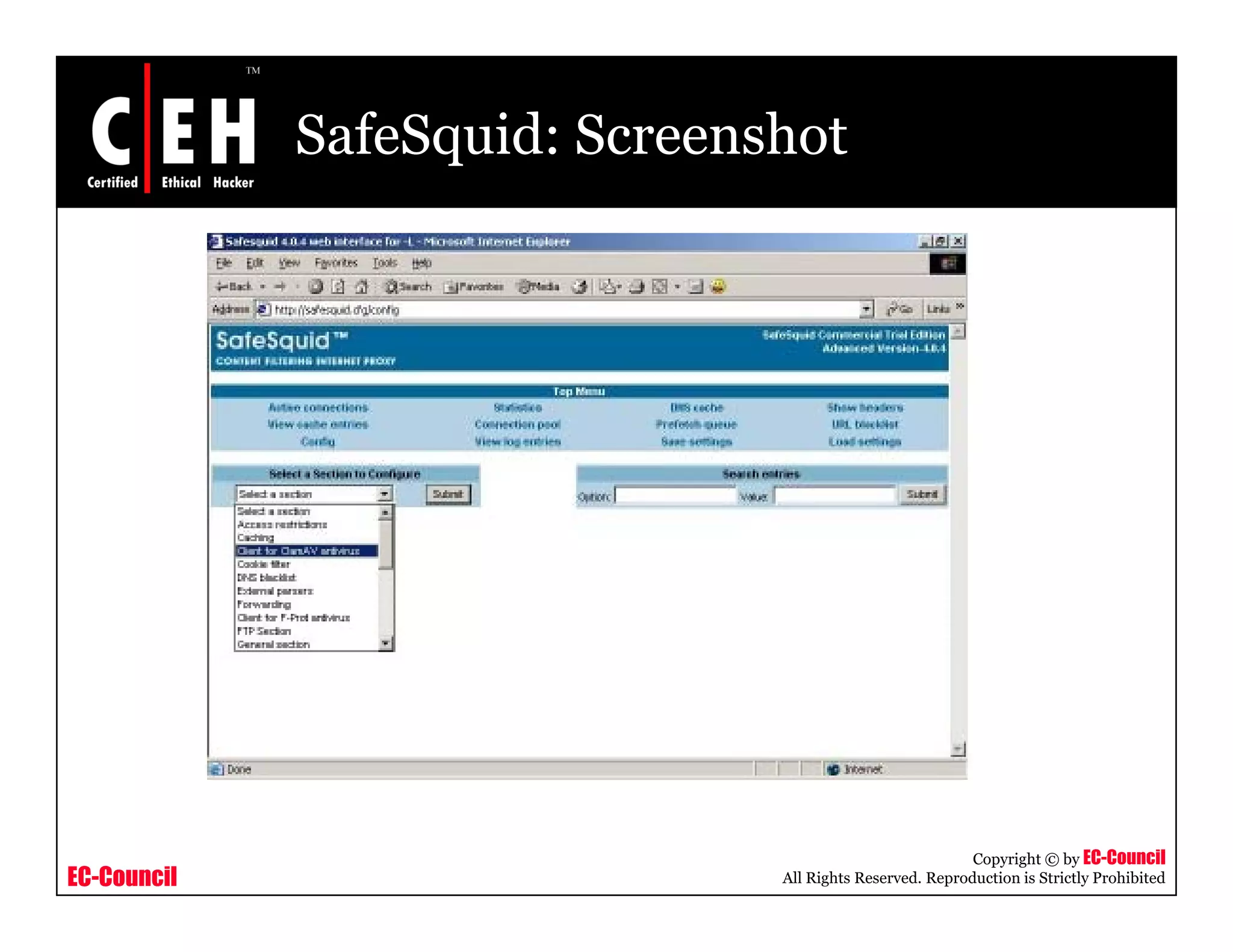
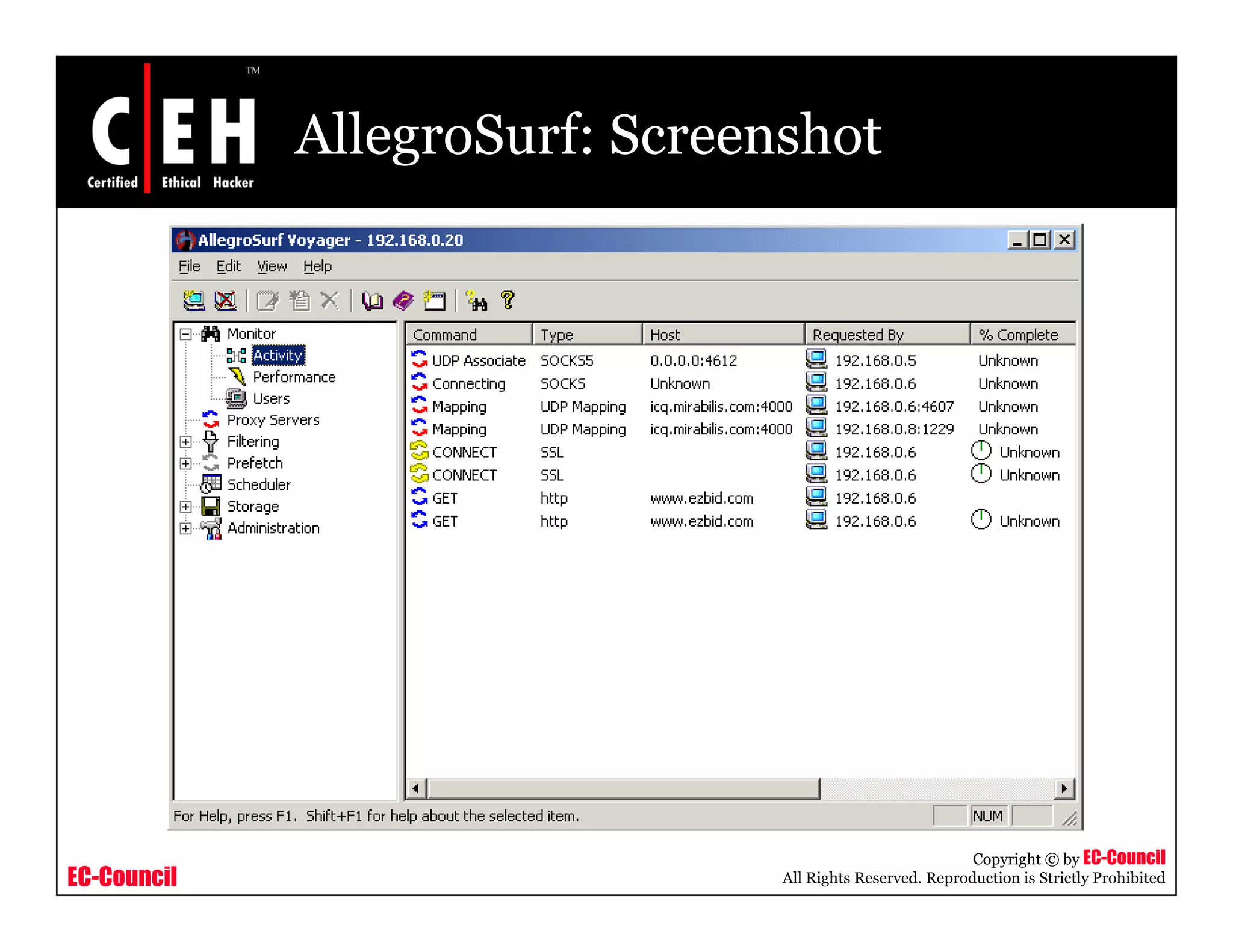
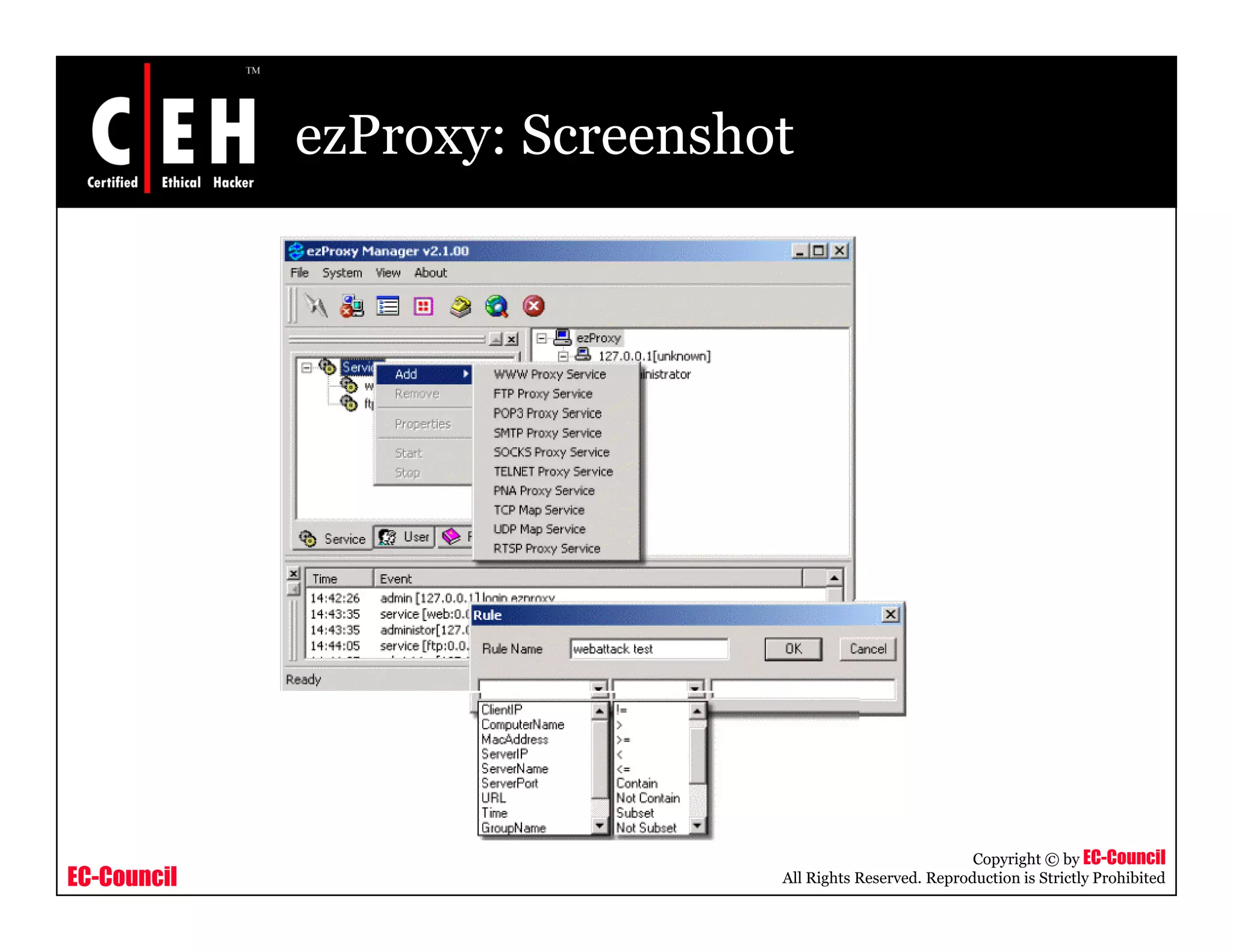
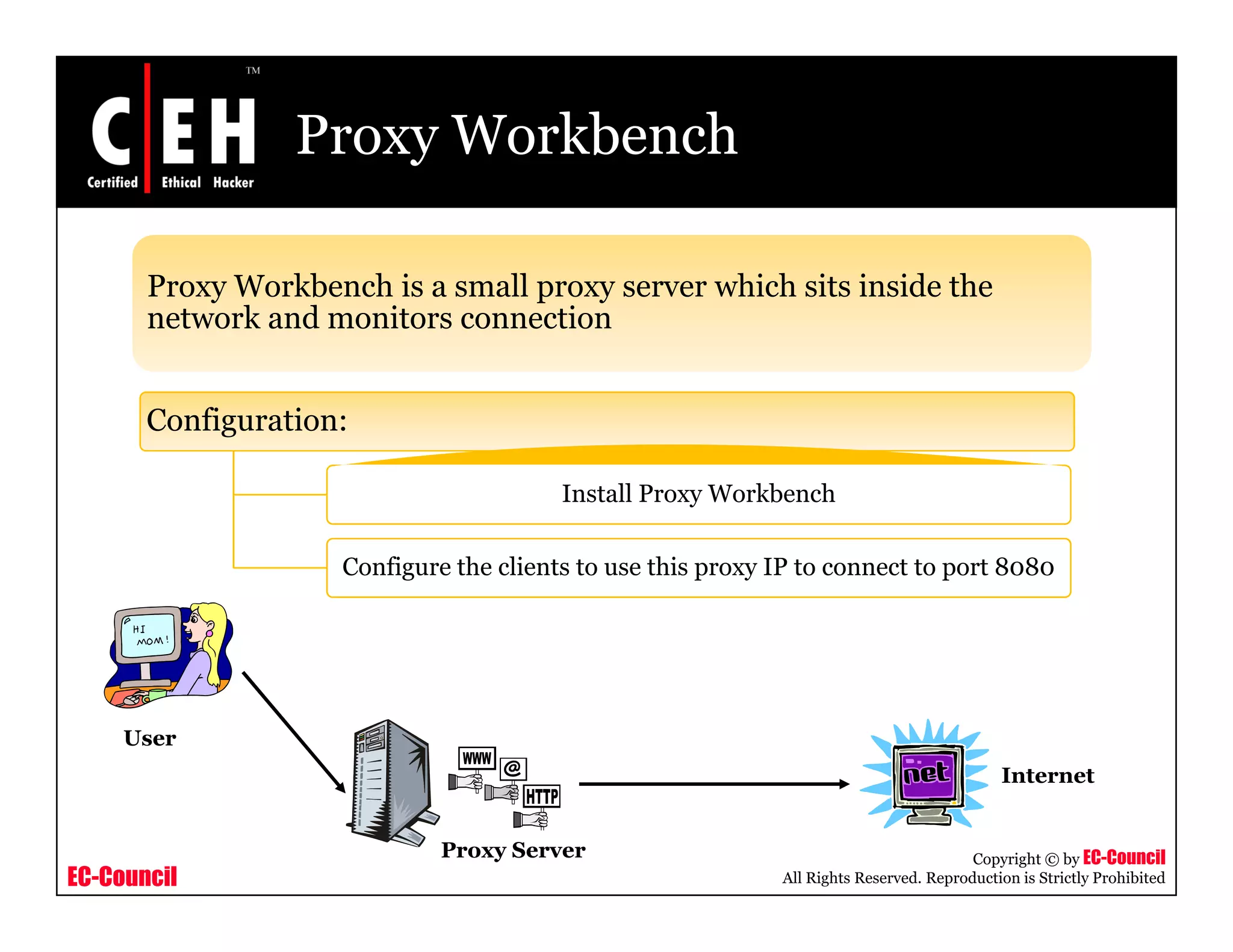
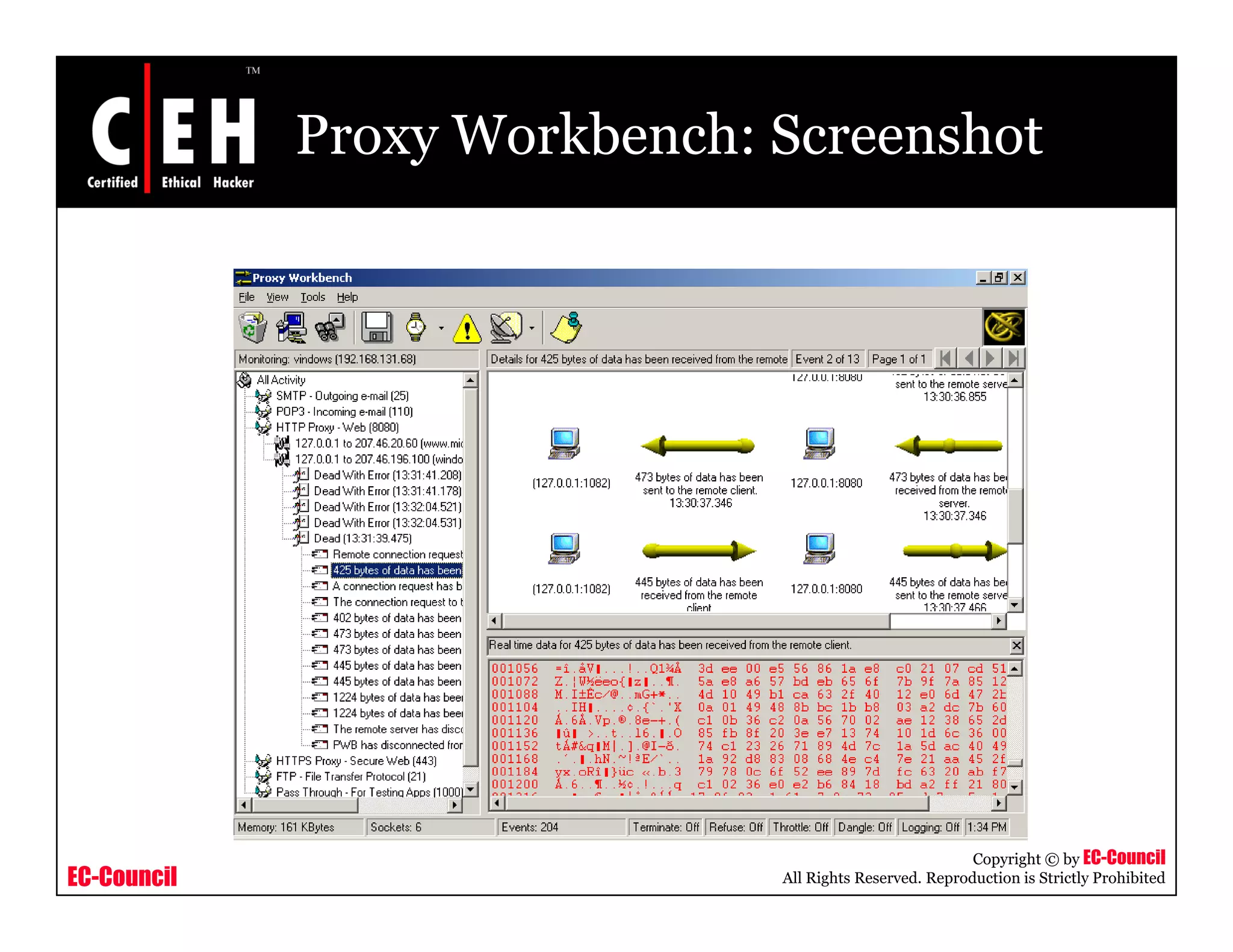
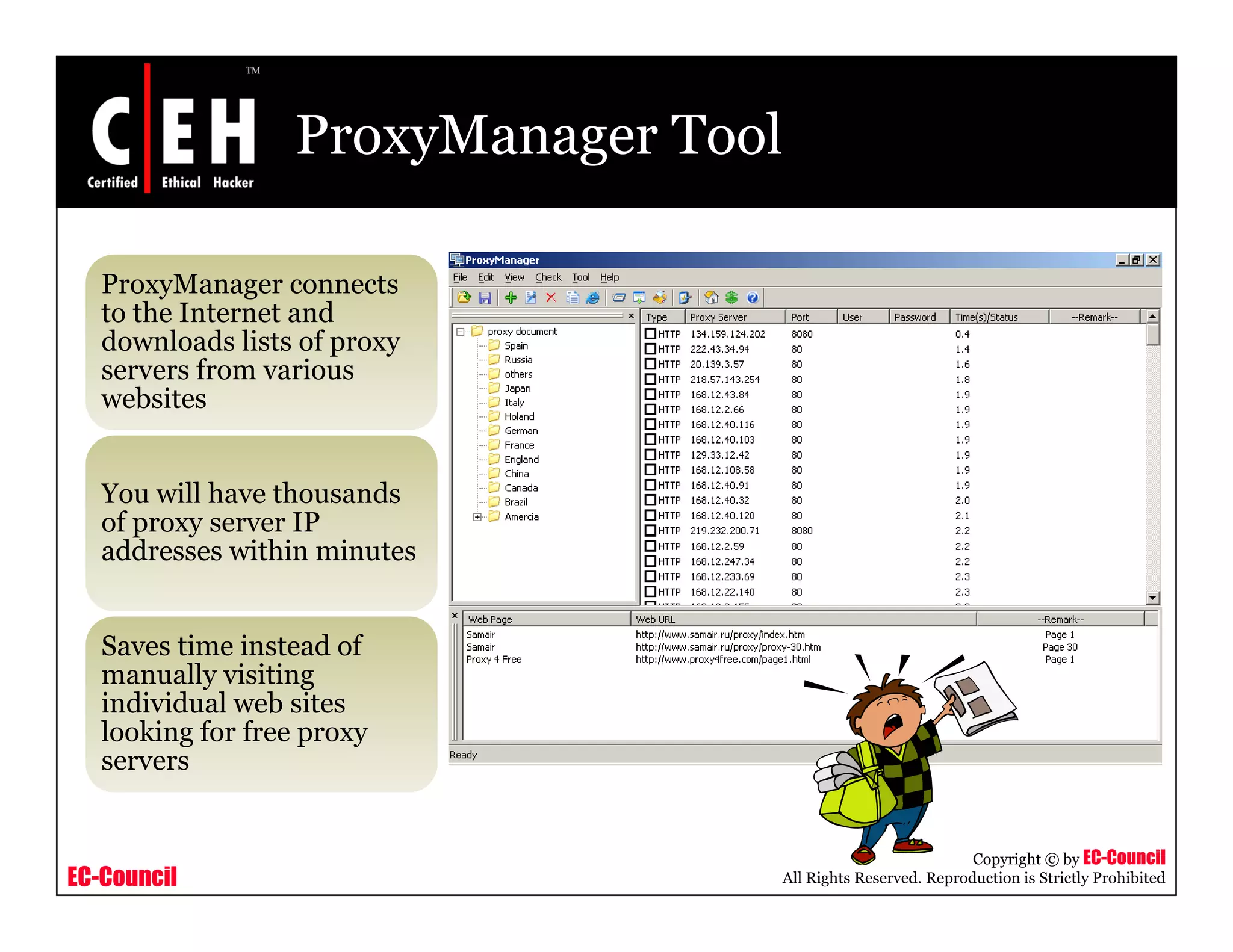
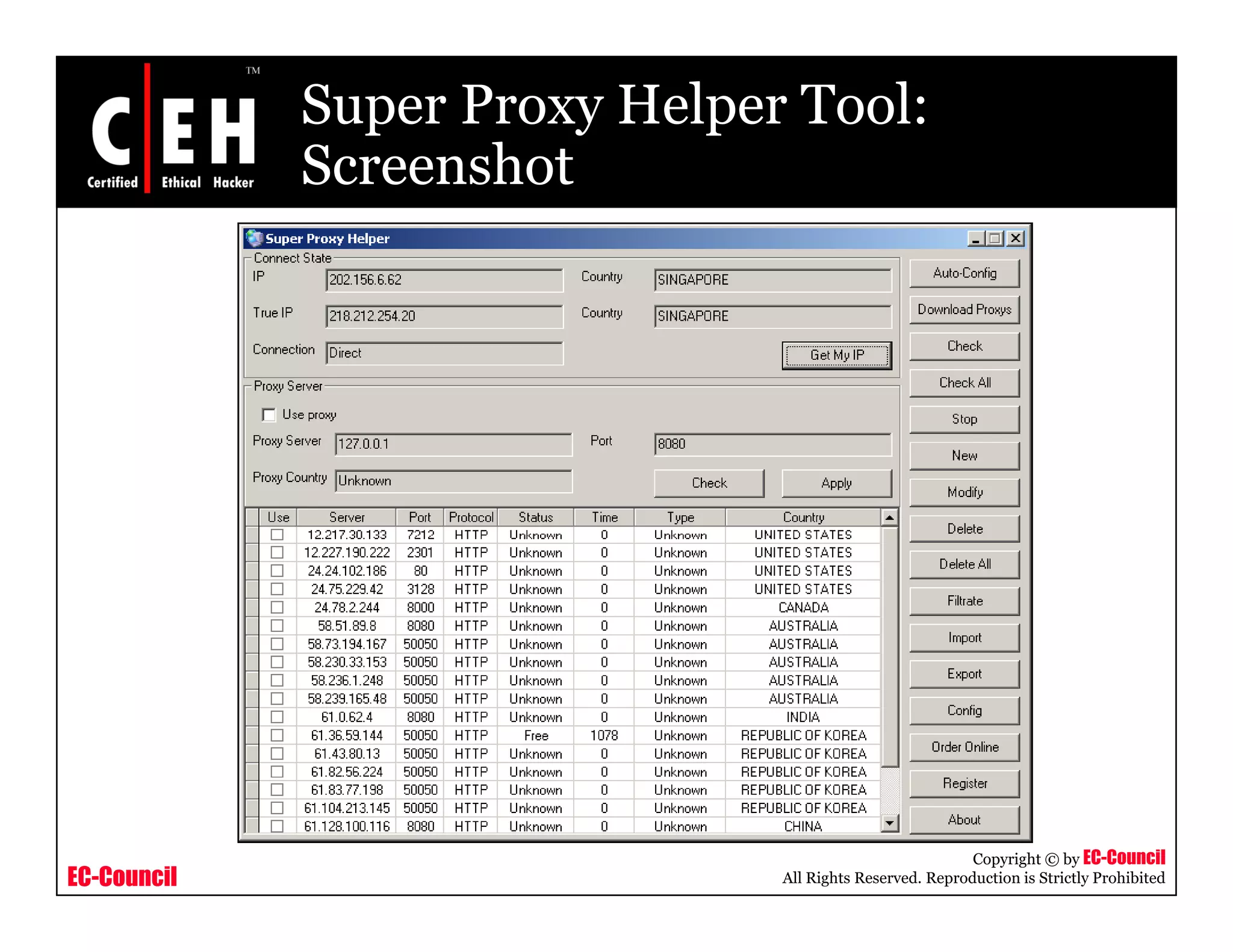
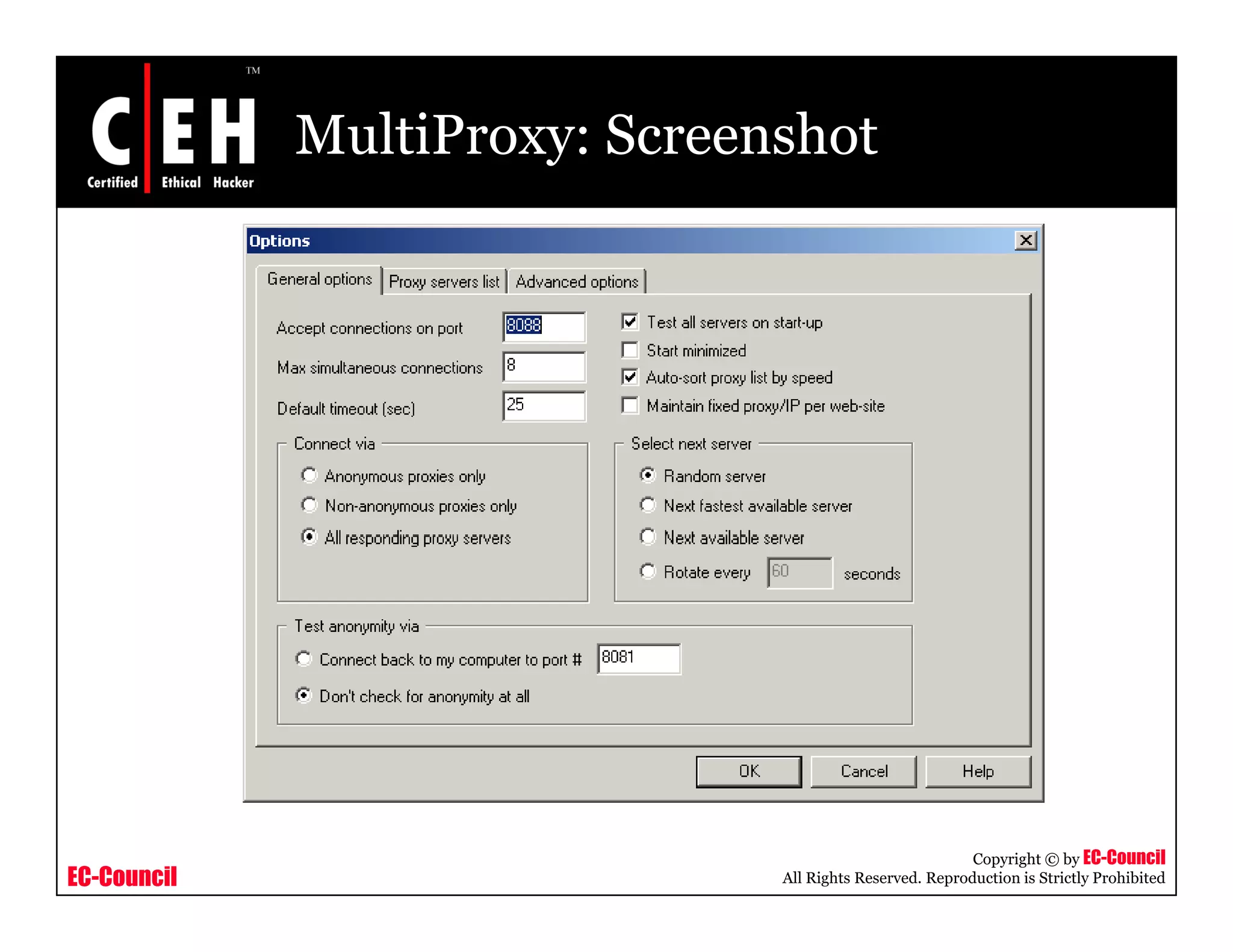
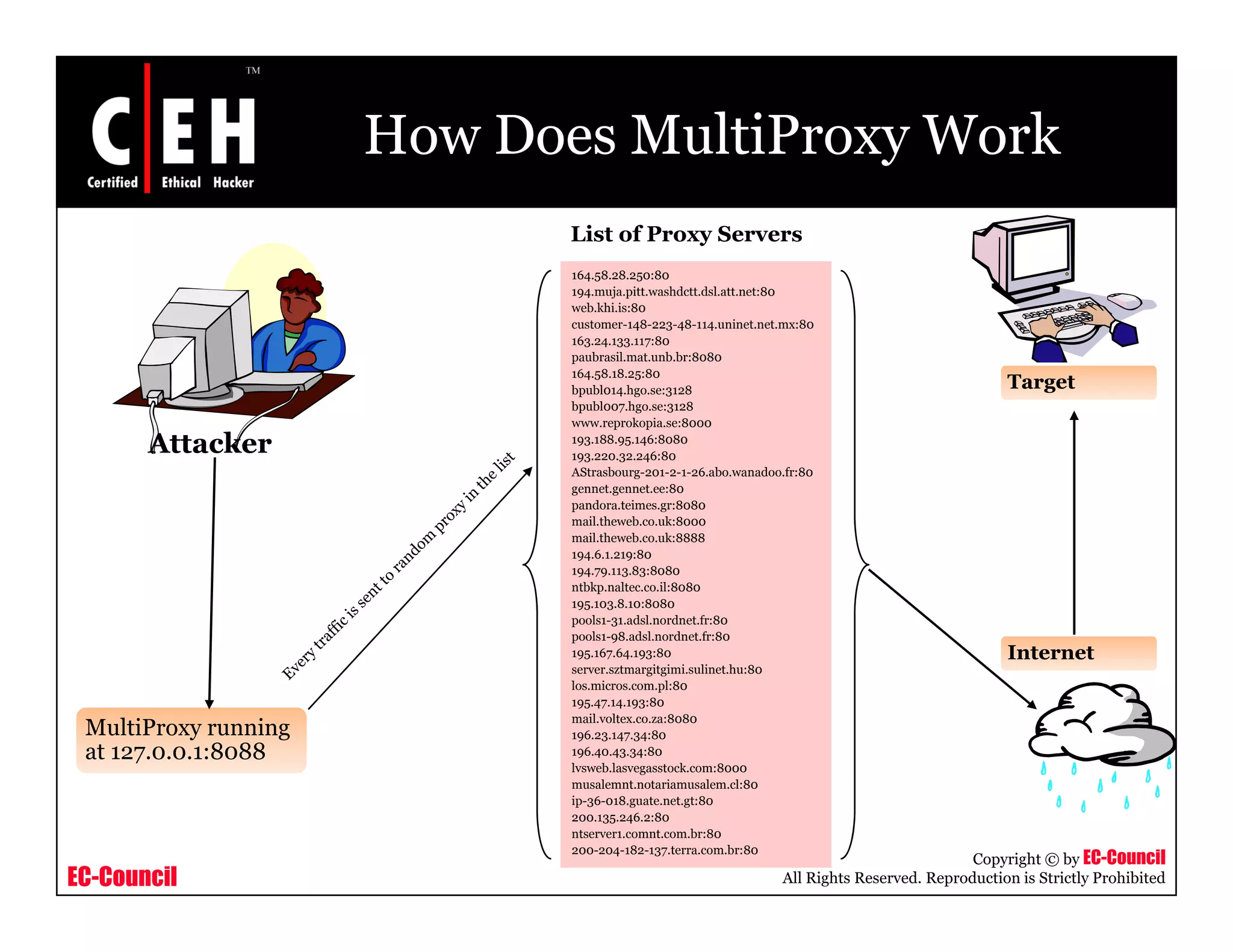
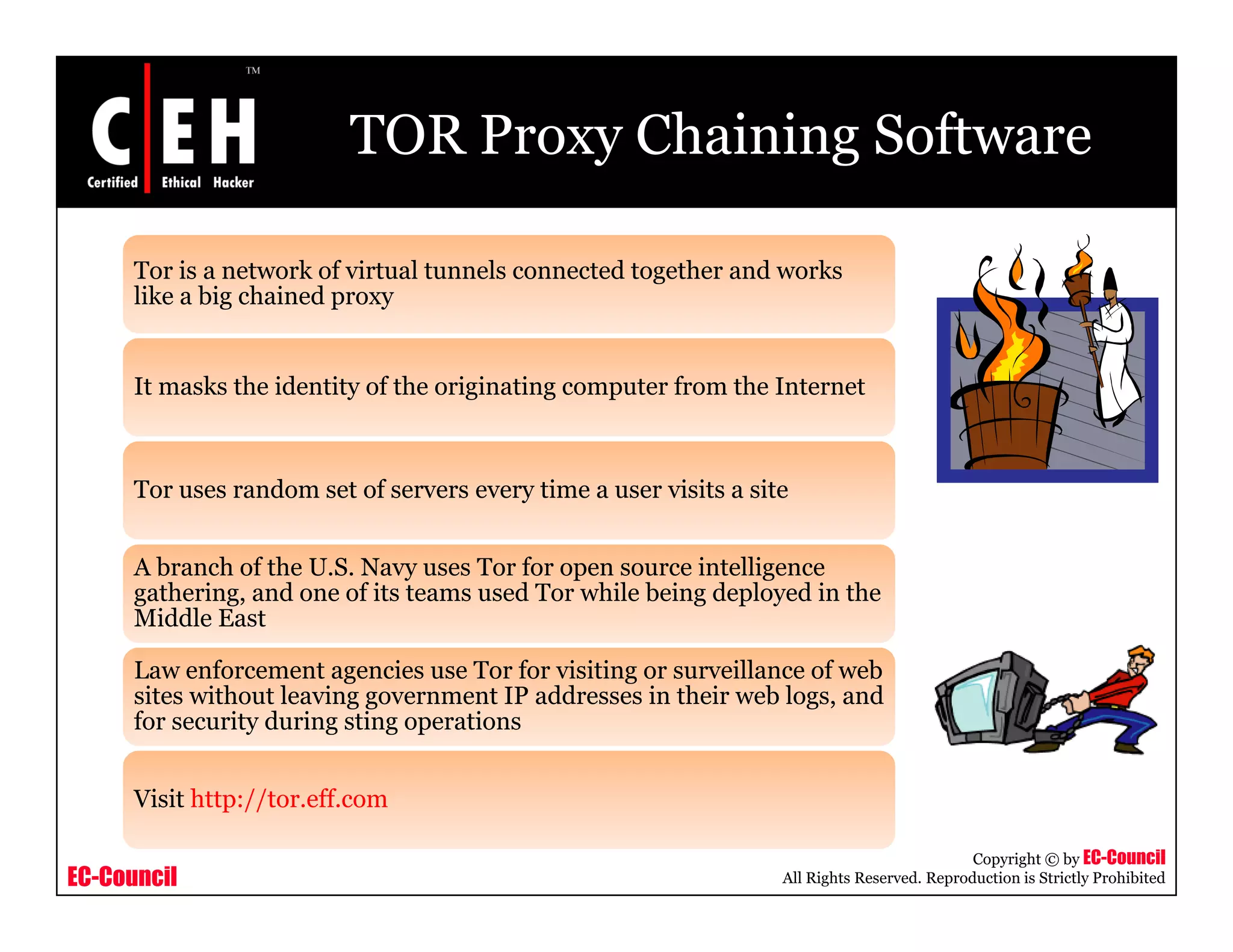
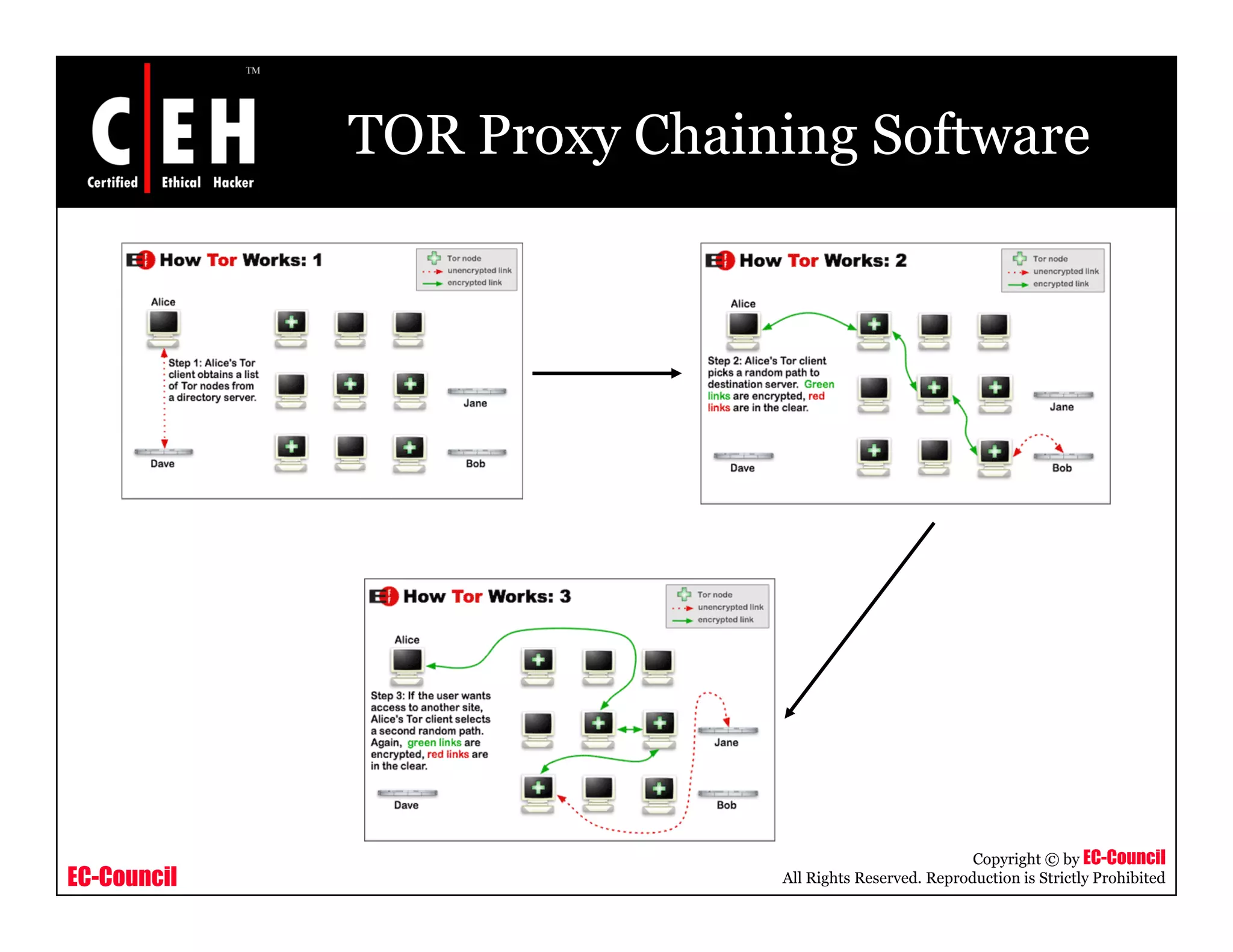
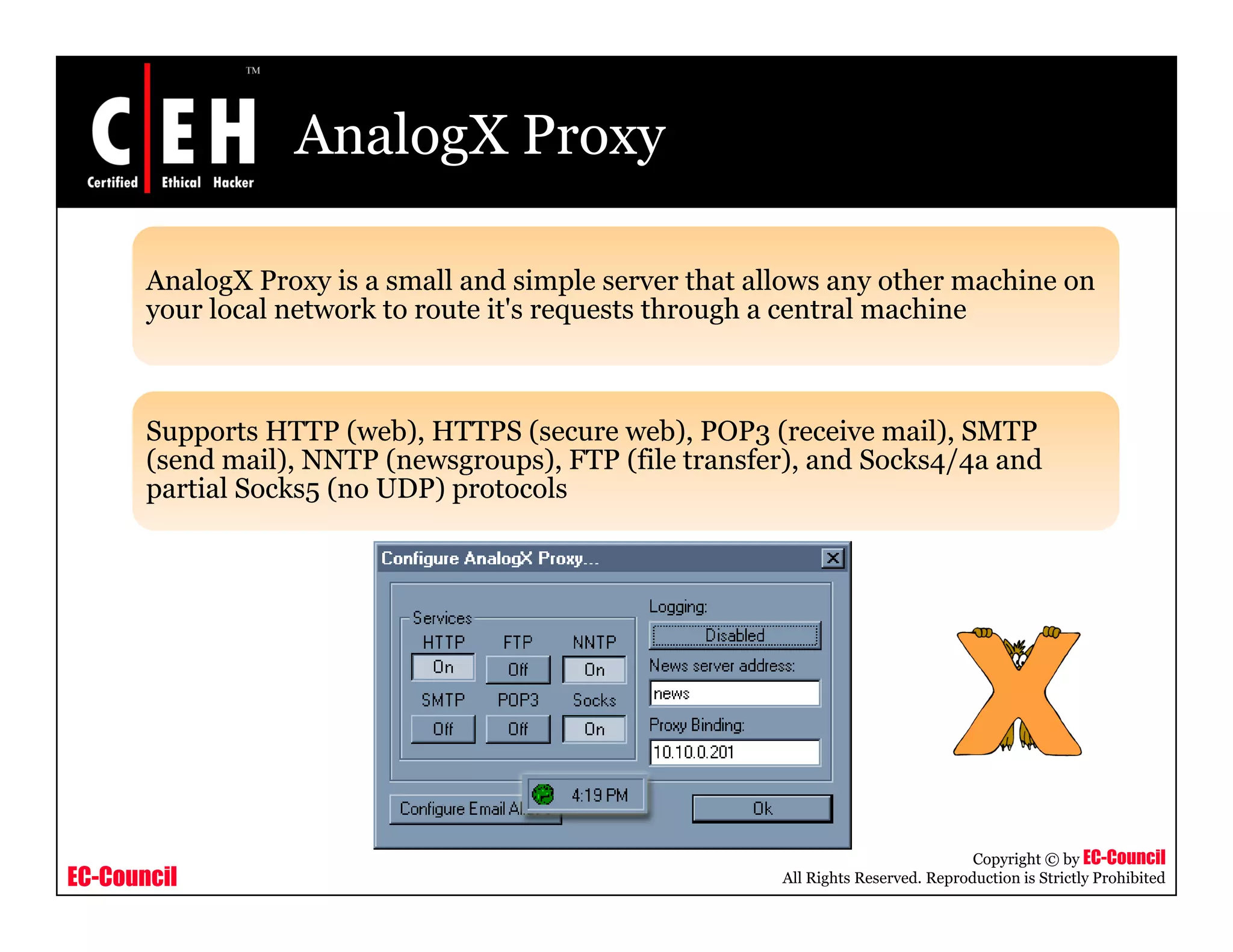
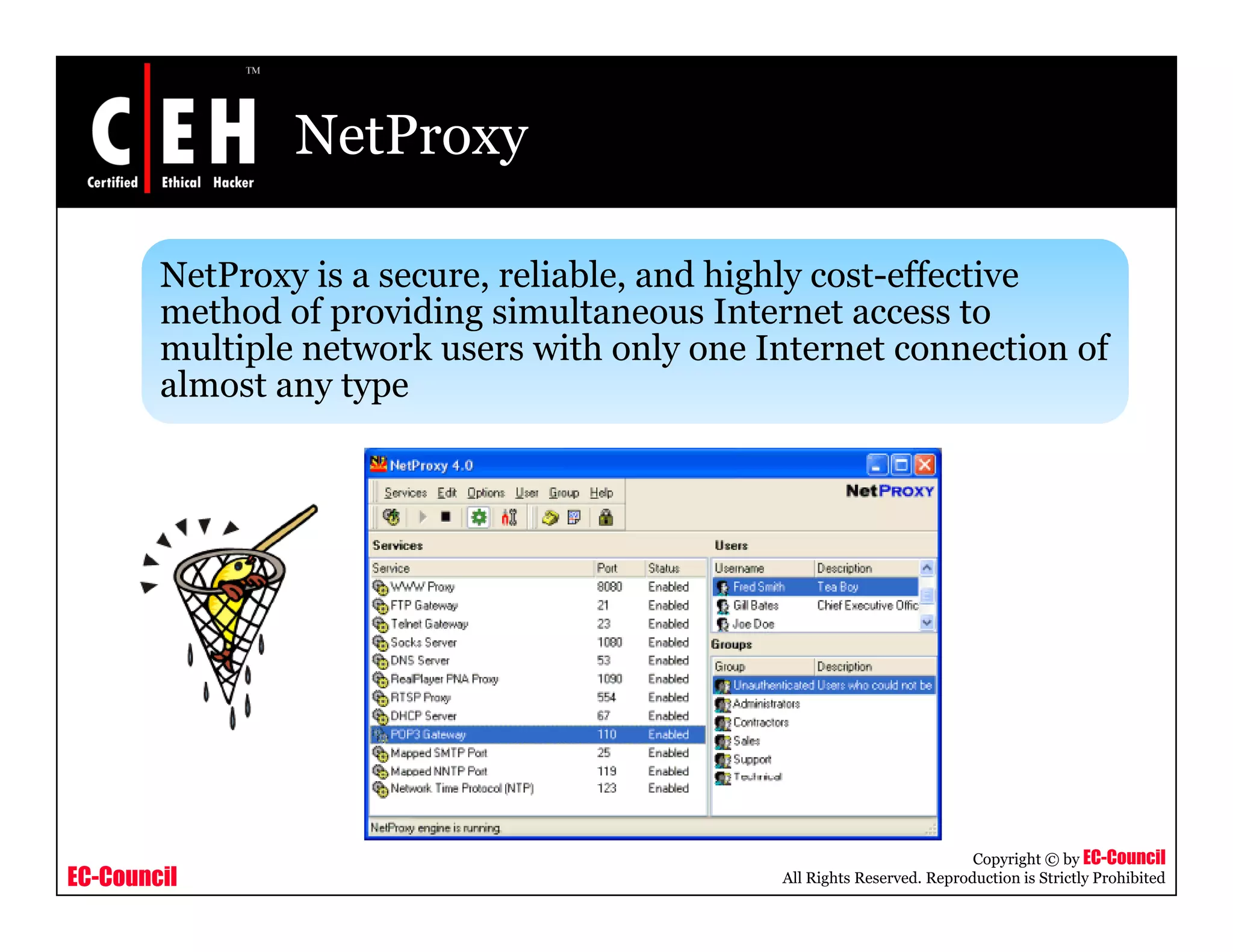
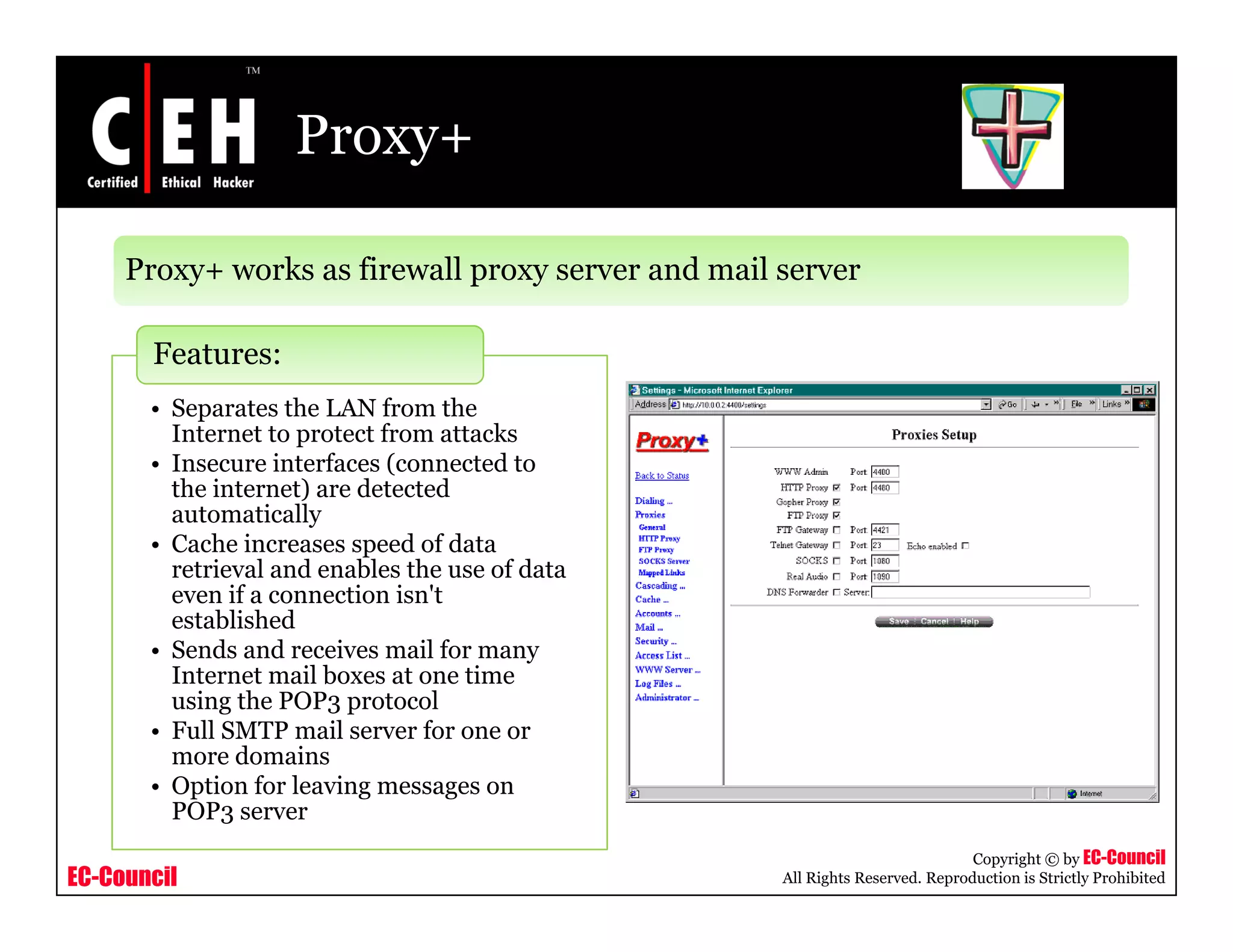
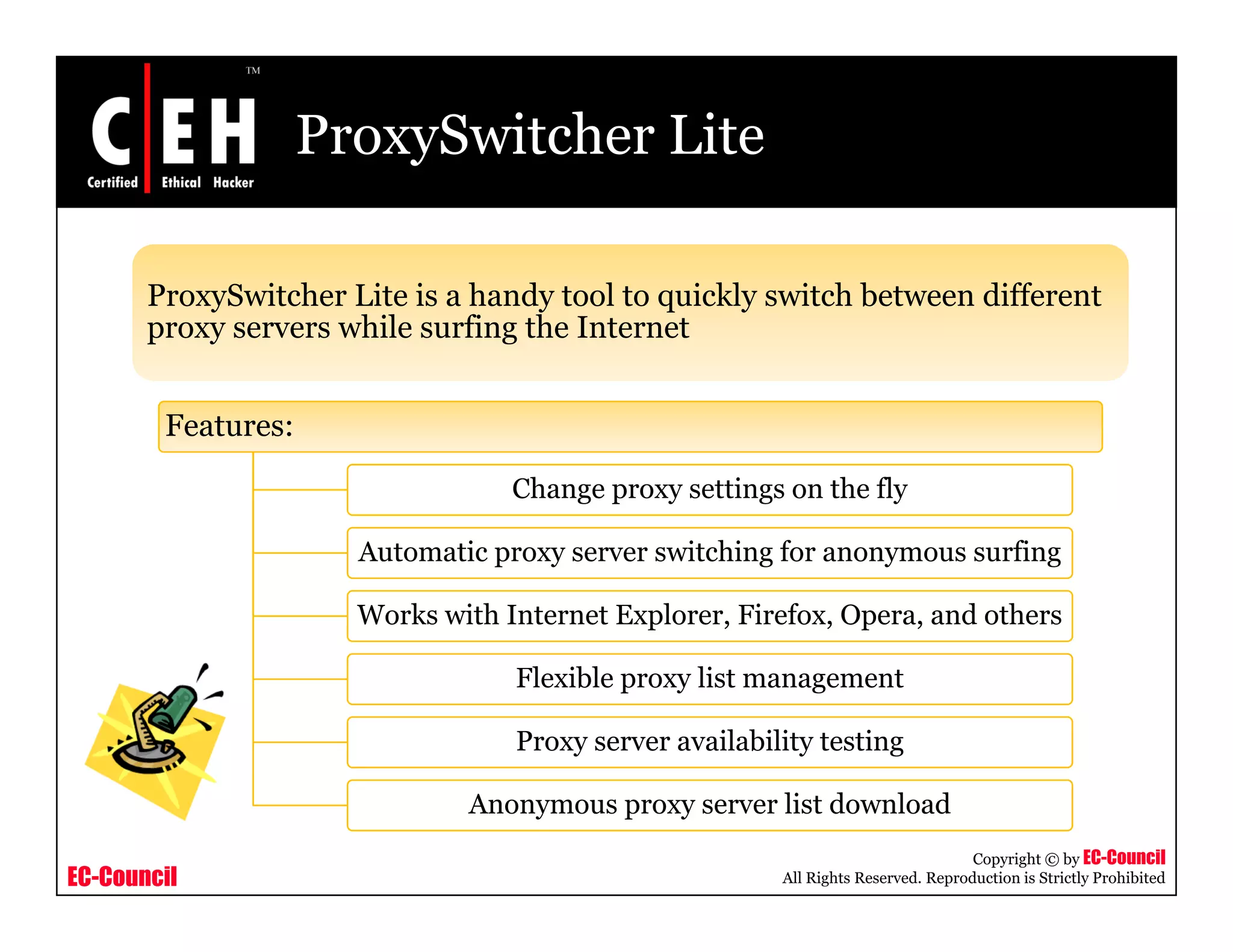
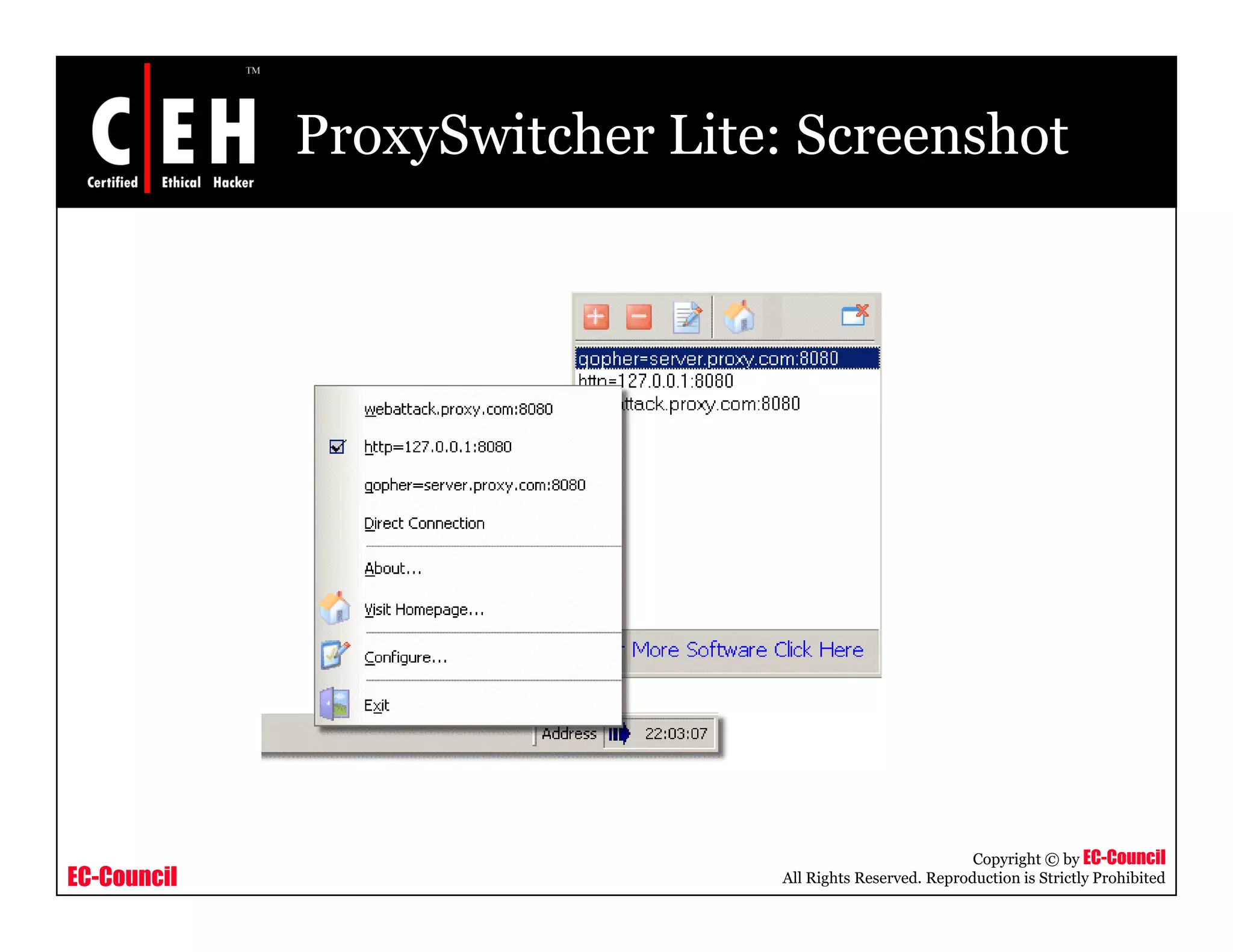
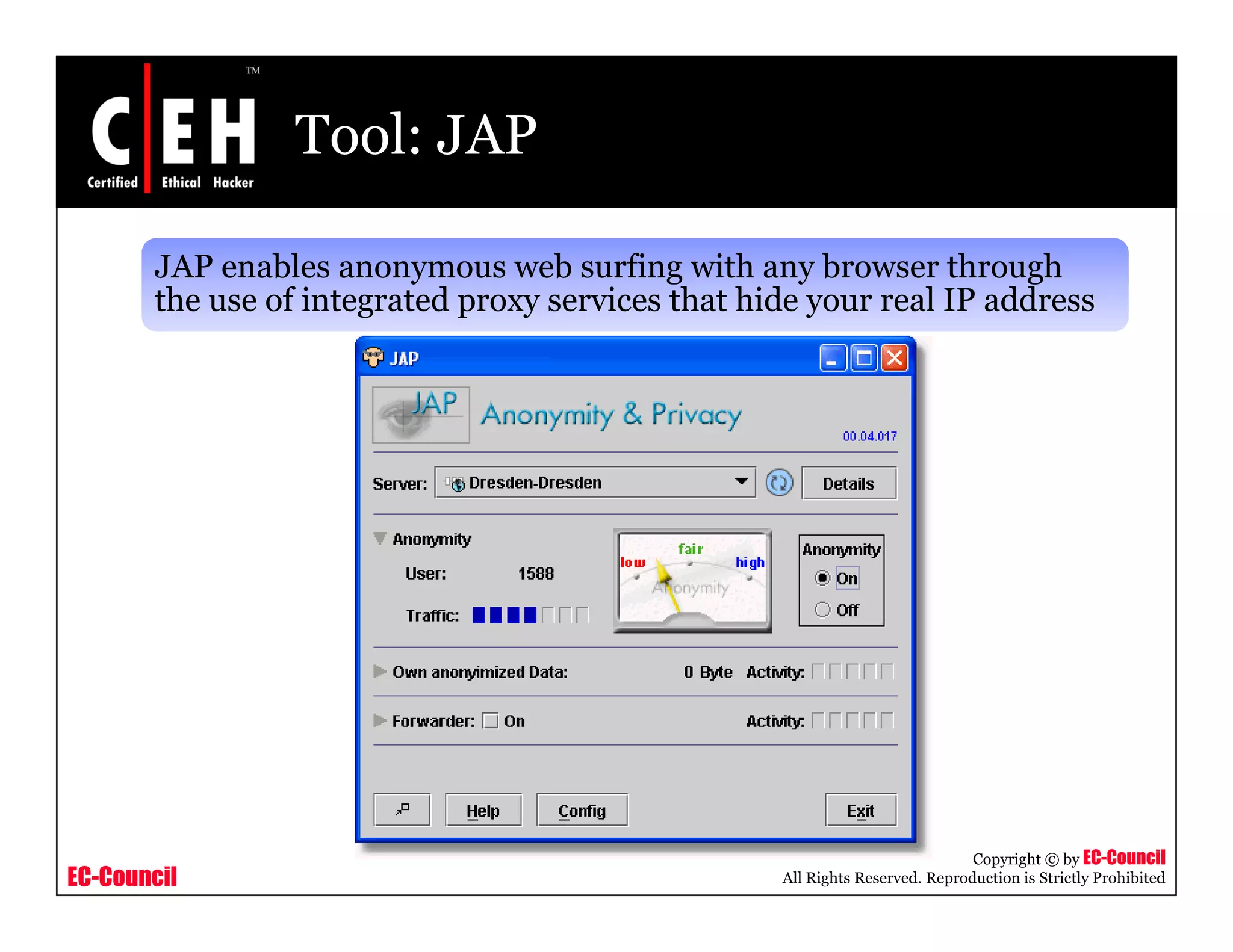
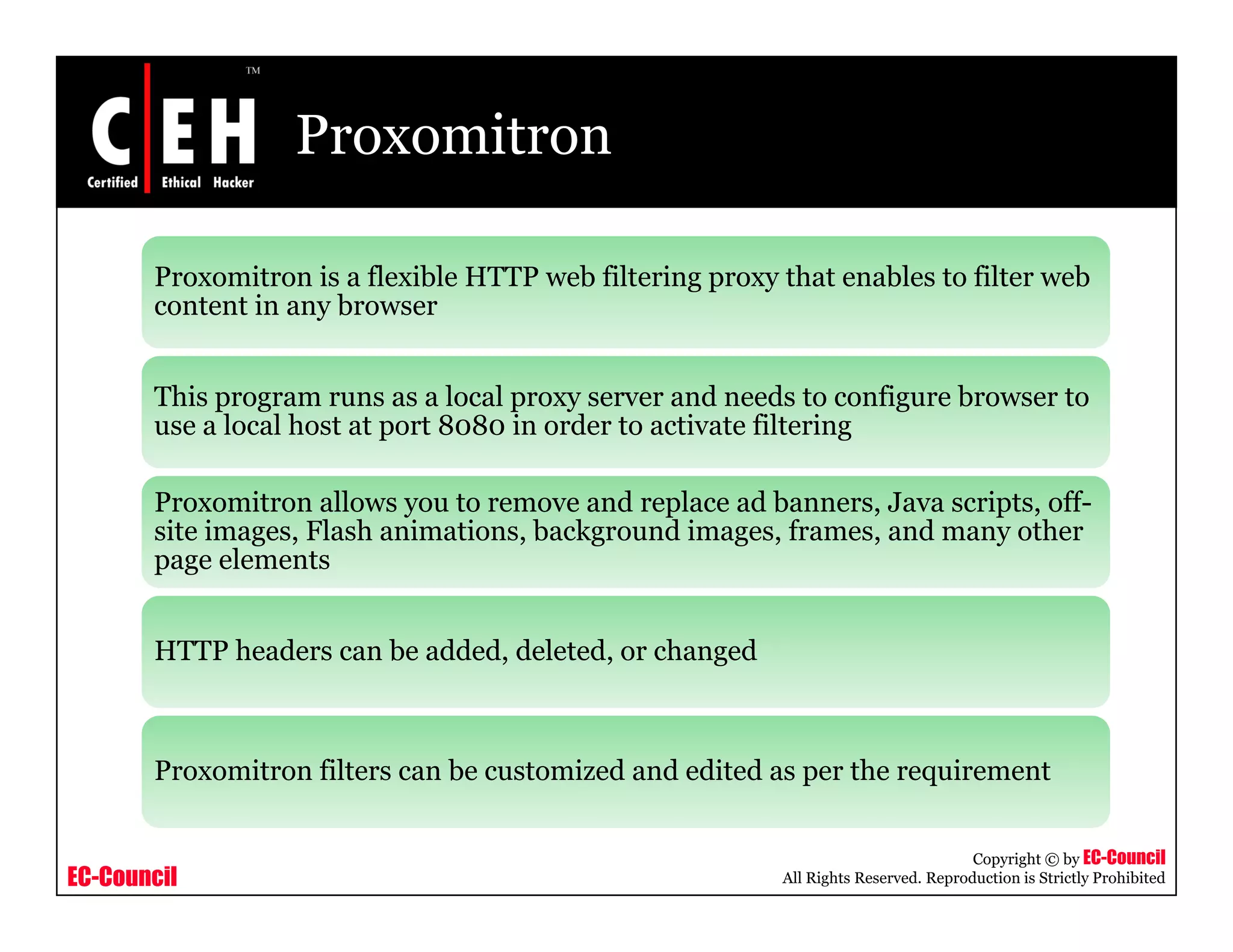
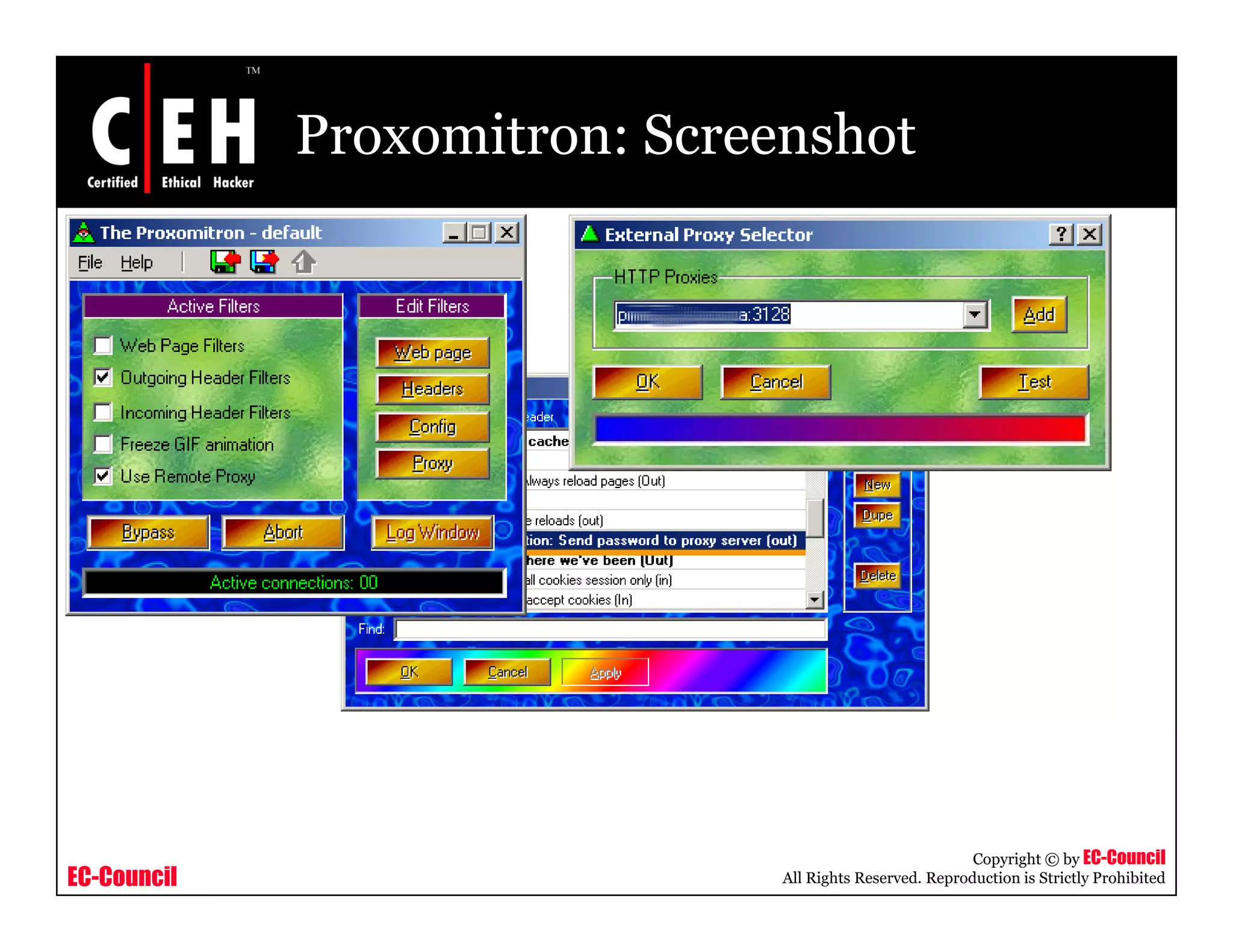
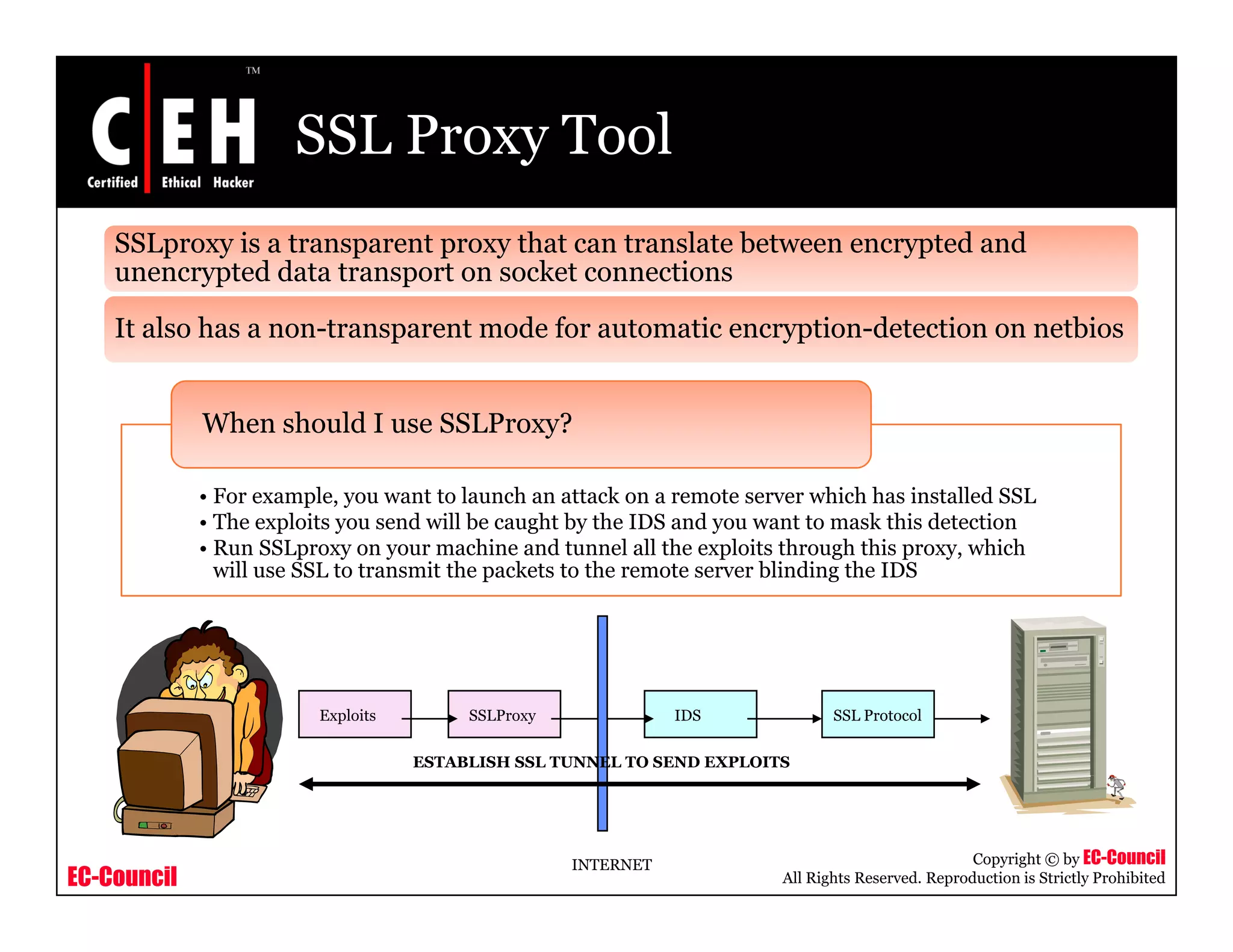
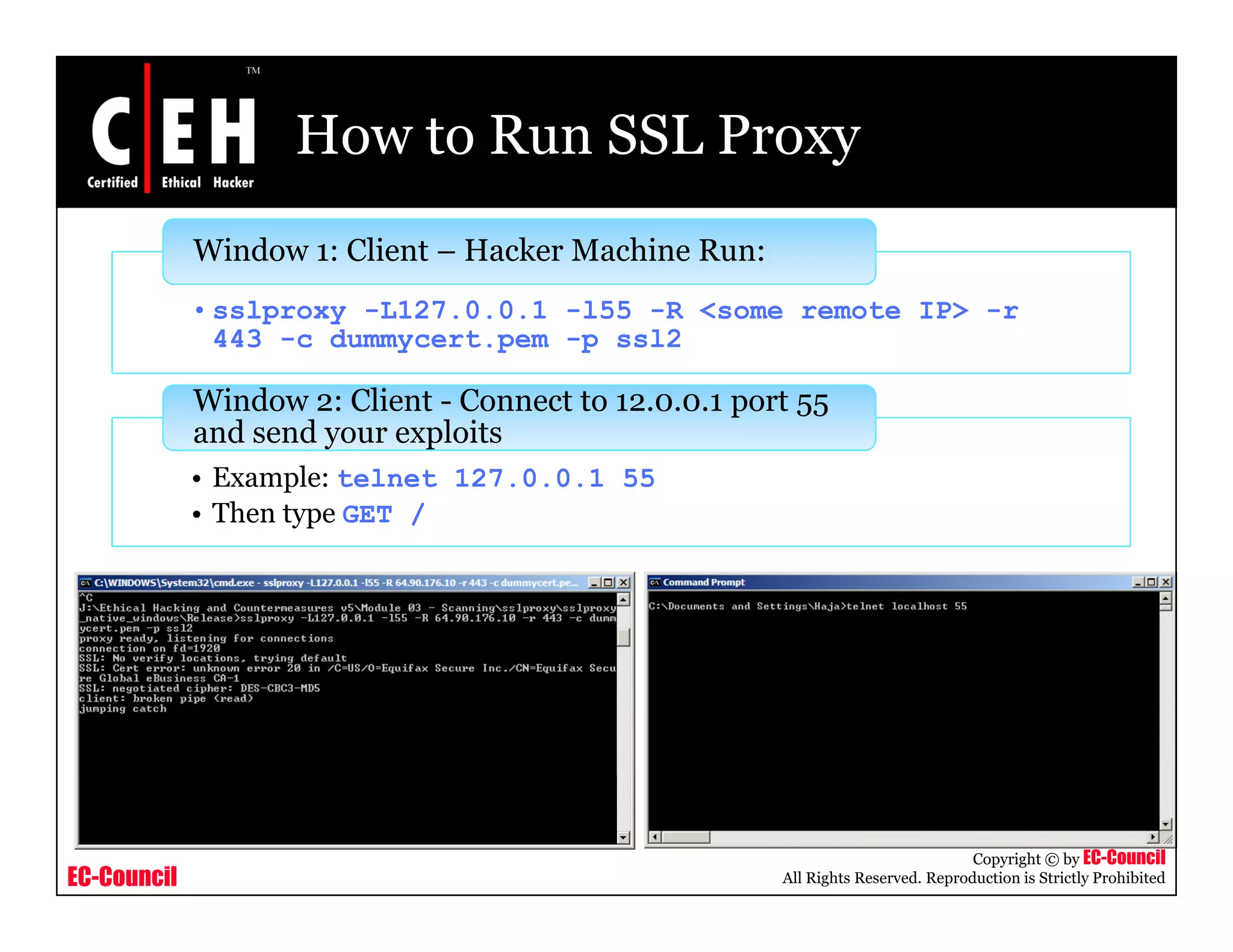
This document provides an overview of proxy server technologies. It defines what a proxy server is and its basic functions. It then discusses different types of proxy servers and several proxy server tools, including WinGate, UserGate, SafeSquid, AllegroSurf, ezProxy, and AnalogX Proxy. The document aims to familiarize readers with proxy servers, their roles, types and some common tools.