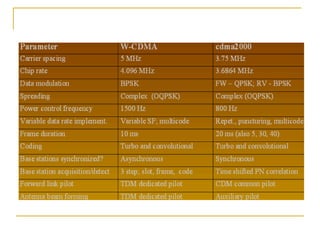
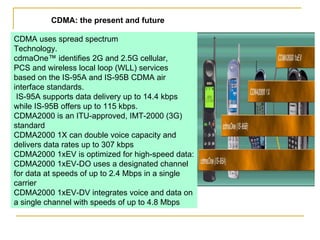
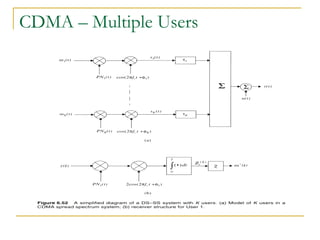
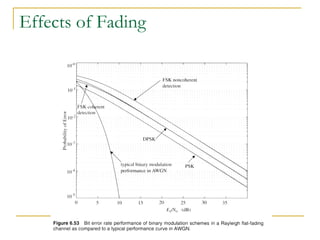
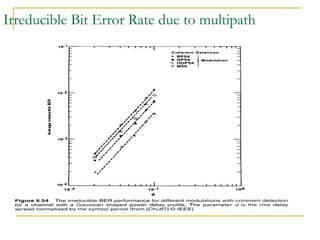
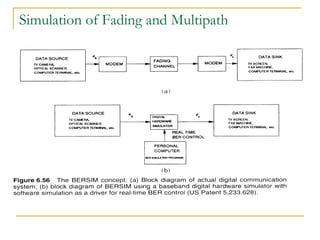
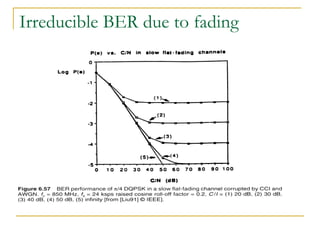
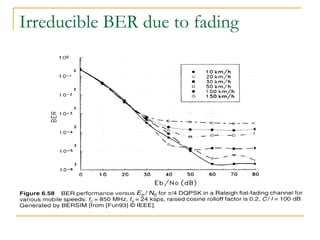
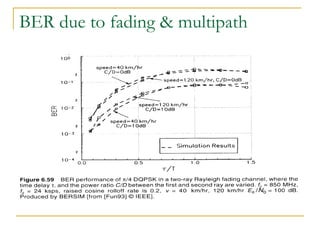
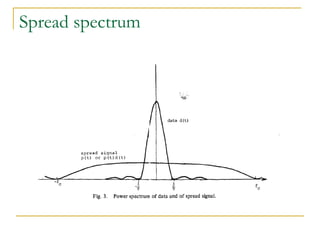
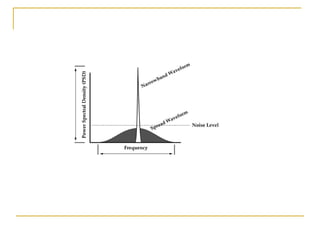
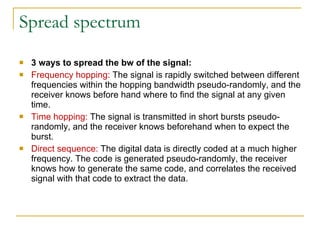
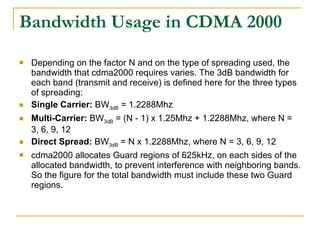
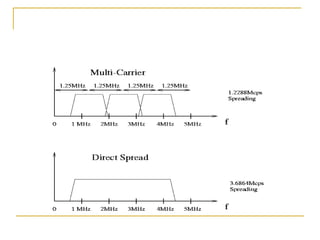
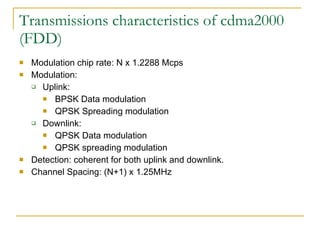
The document discusses spread spectrum technology and CDMA. It describes three types of spread spectrum techniques: frequency hopping, time hopping, and direct sequence. It then discusses CDMA2000 and how the bandwidth required varies depending on the spreading factor and type. It provides details on the transmission characteristics of CDMA2000 such as modulation schemes and channel spacing.




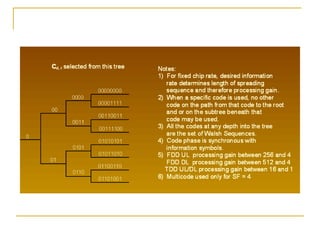
![Walsh codes Walsh codes are defined as a set of N codes, denoted W j , for j = 0, 1, ... , N - 1, which have the following properties: W j takes on the values +1 and -1. W j [0] = 1 for all j . W j has exactly j zero crossings, for j = 0, 1, ... , N - 1. Each code W j is either even or odd with respect to its midpoint.](https://image.slidesharecdn.com/week7-120128072119-phpapp01/85/cdma-12-320.jpg)