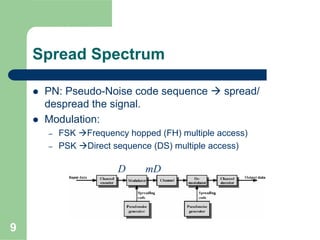
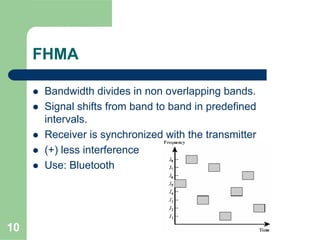
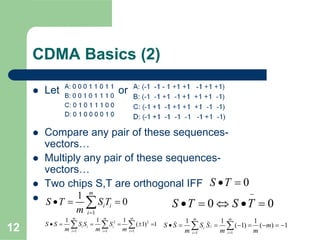
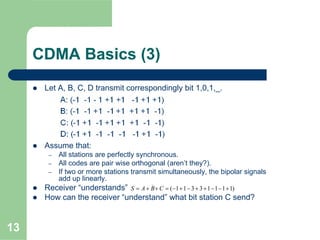
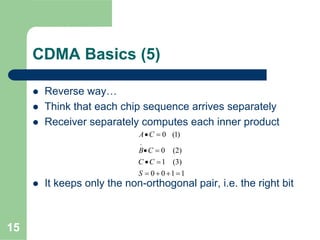
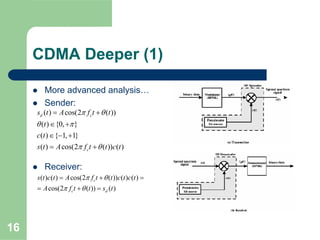
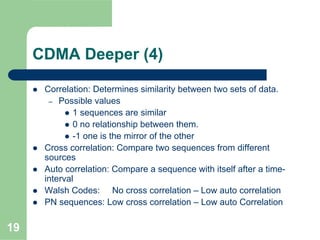
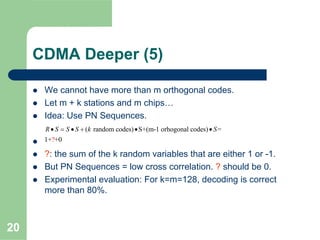
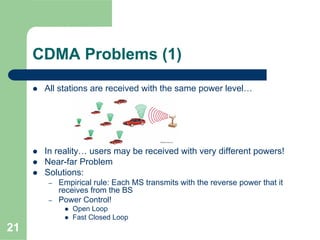
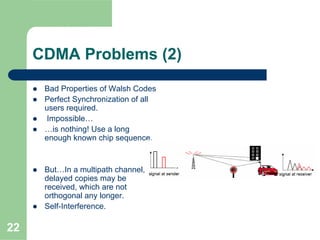
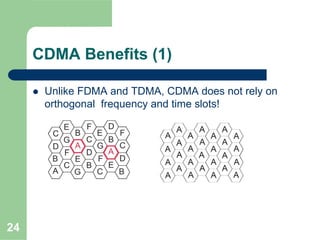
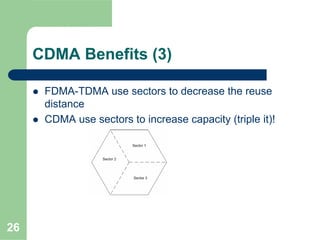
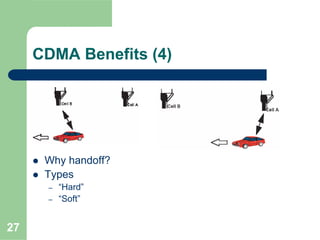
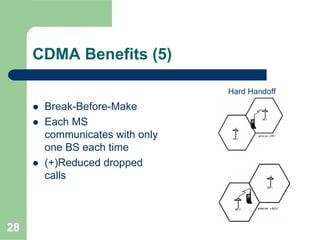
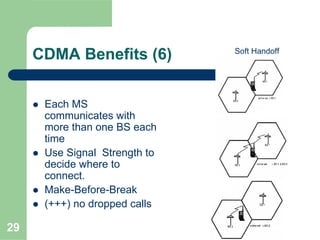
CDMA allows multiple users to access a shared radio channel simultaneously by assigning each user a unique code. It avoids having to divide access by time or frequency and enables higher capacity compared to TDMA or FDMA. While CDMA faces challenges from synchronization errors and interference, it provides benefits like soft handoff between cells, higher capacity due to dynamic allocation, and reuse of frequencies in each sector which further increases capacity.