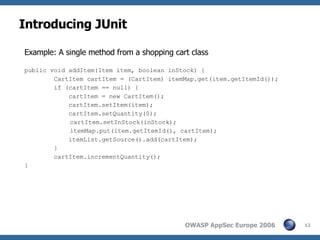
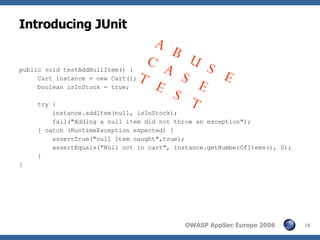
The document discusses integrating security testing into the typical iterative development lifecycle through automated software tests at various stages, including unit tests, integration tests, and acceptance tests. It provides examples of using JUnit for unit testing and tools like Cactus, Selenium, and WATIR for integration and acceptance testing to validate valid/invalid inputs and test for vulnerabilities like SQL injection and cross-site scripting.
![Security Testing through Automated Software Tests Stephen de Vries, Principal Consultant, Corsaire [email_address]](https://image.slidesharecdn.com/owaspappseceu2006securitytestingthruautomatedswtests-1216183904881834-9/85/Security-Testing-1-320.jpg)


















![Testing Security in Unit Tests Test Invalid Input: public void testIllegalCharactersInPhoneNumber() { String number = "+(23)';[]232 - 321"; acc.setPhone(number); validator.validate(acc, errors); assertTrue(number+" did not cause a validation error.", errors.hasFieldErrors("phone")); } public void testAlphabeticInPhoneNumber() { String number = "12a12121"; acc.setPhone(number); validator.validate(acc, errors); assertTrue(number+" did not cause a validation error.", errors.hasFieldErrors("phone")); }](https://image.slidesharecdn.com/owaspappseceu2006securitytestingthruautomatedswtests-1216183904881834-9/85/Security-Testing-23-320.jpg)












