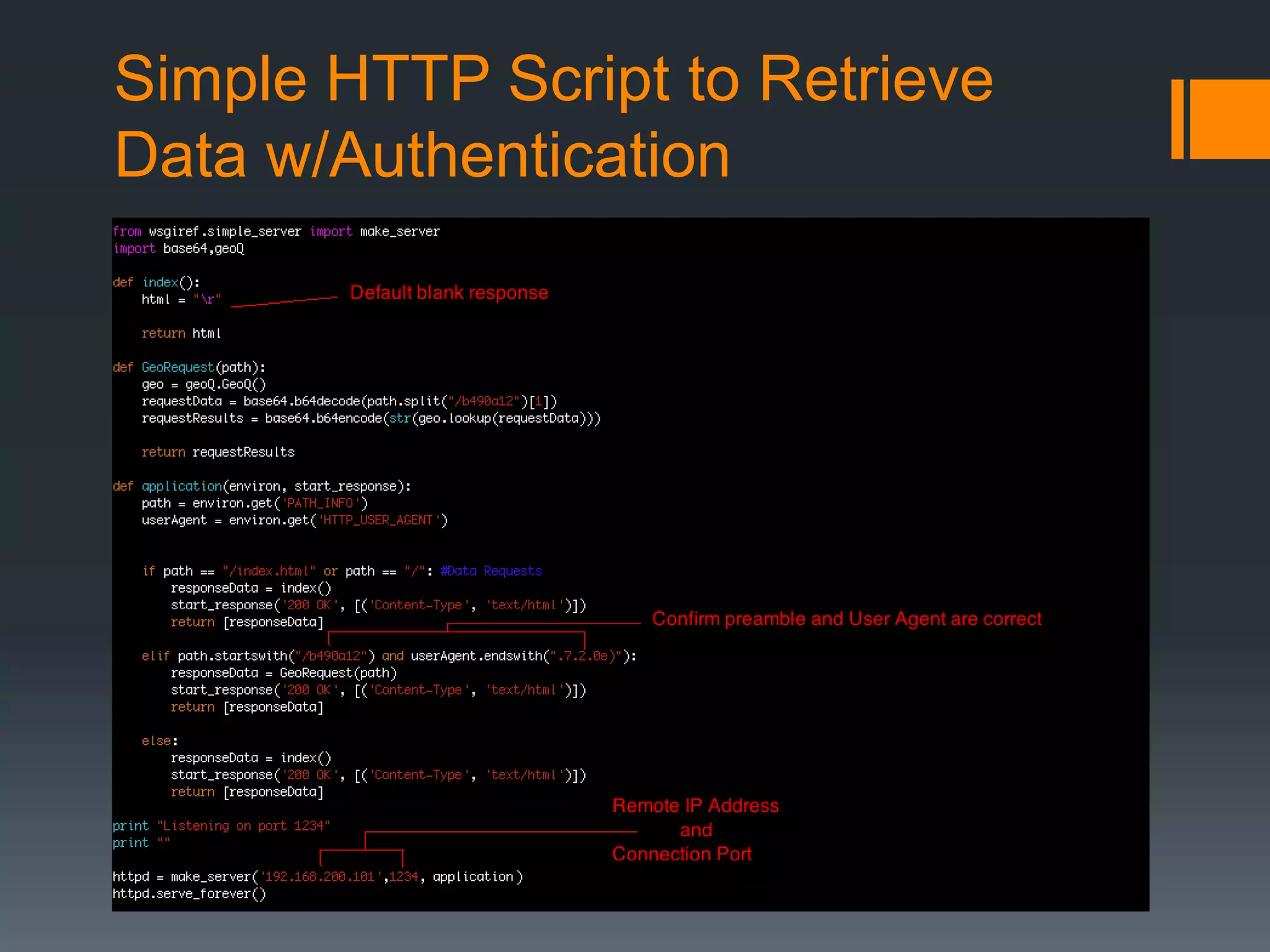
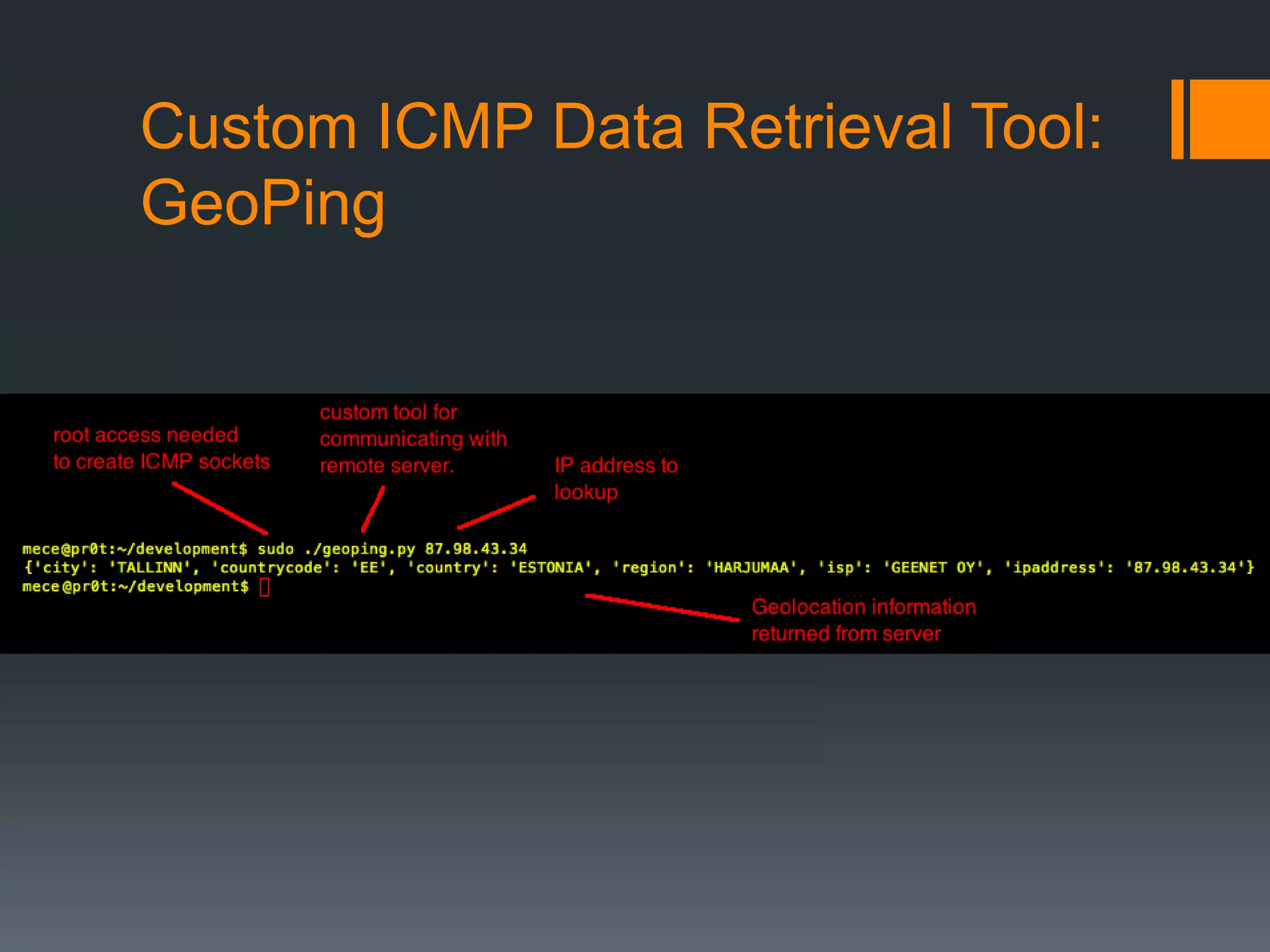
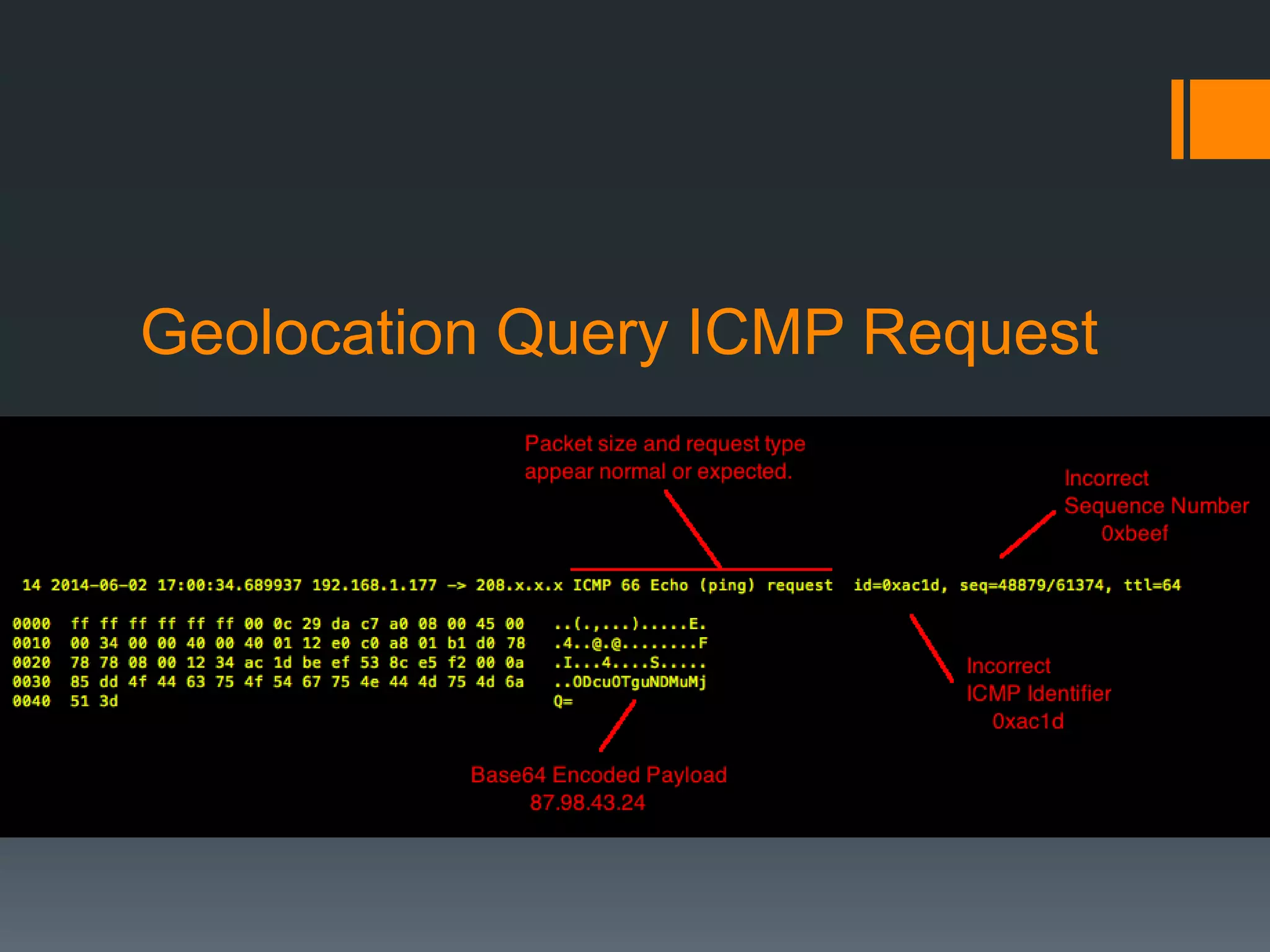
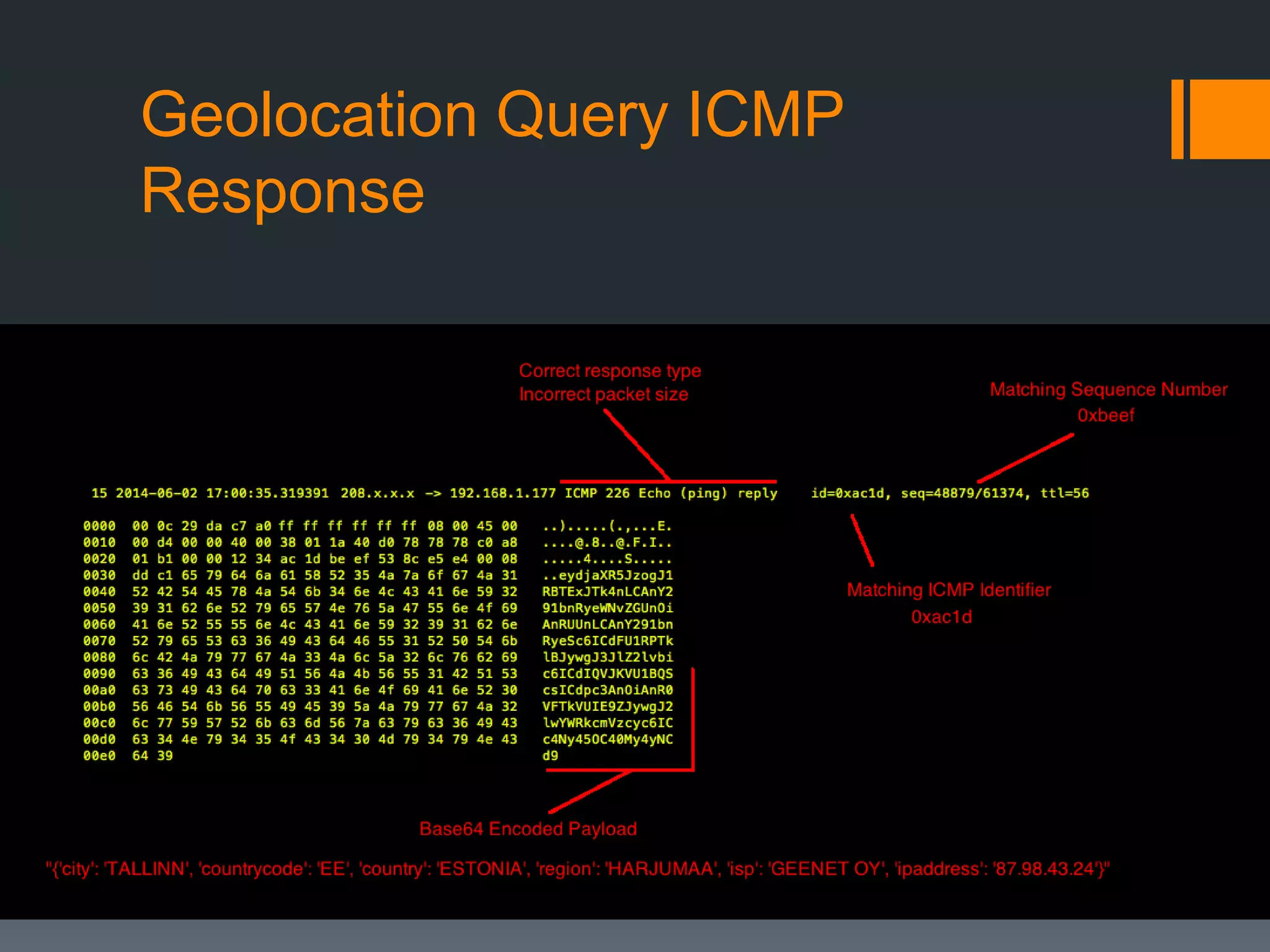
The document discusses insights into organizational security through the lens of web servers, highlighting the ongoing threats they face due to outdated services and vulnerabilities. It covers the evolution of web servers, various malicious campaigns, and the potential risks associated with compromised servers being used for malicious purposes. Key recommendations include keeping servers patched, upgrading as needed, and maintaining diligence in security practices.