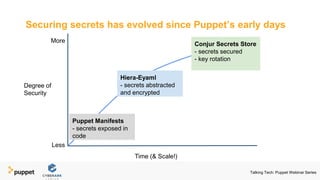
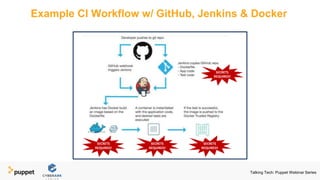
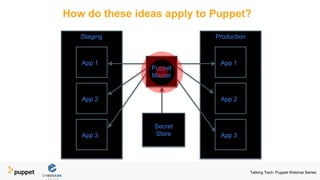
Puppet presents a webinar series titled 'Talking Tech' focusing on technology solutions for infrastructure and security policy as code, featuring collaboration with CyberArk Conjur. The series covers various topics including managing infrastructure, enhancing security in DevOps, and securing secrets using automated processes. Key takeaways emphasize automating operations, abstracting secrets from code, and implementing security best practices such as encryption, rotation, and auditing.












![Puppet Manifests using Conjur
################## Site.pp ##################
node 'default' {
require secrets
file { '/tmp/dbpass':
ensure => file,
content => "${secrets::postgres_password.unwrap}",
show_diff => false, # don't log file content
}
file { '/tmp/token':
ensure => file,
content => "${secrets::vendor_oauth_token.unwrap}",
show_diff => false,
}
}
################## Secrets.pp ##################
class { 'conjur':
account => 'demo',
appliance_url => 'http://conjur',
authn_login => "host/app-${::trusted['hostname']}",
host_factory_token => Sensitive('placeholder-for-HF-token'),
version => 5,
}
class secrets {
$vendor_oauth_token = conjur::secret('app/vendor-oauth-token')
$postgres_password = conjur::secret('app/postgres-password')
}
Talking Tech: Puppet Webinar Series](https://image.slidesharecdn.com/puppetandcyberarkwebinarfinal-171108233138/85/Delivering-Infrastructure-and-Security-Policy-as-Code-with-Puppet-and-CyberArk-Conjur-24-320.jpg)
![Conjur Policy that Controls Secrets Access
- !policy
id: app
annotations:
description: Conjur Puppet demo app policy
body:
# Roles
- !layer app
- !host-factory
annotations:
description: factory for new app node identities
layers: [ !layer app ]
# Secrets
- !variable
id: vendor-oauth-token
annotations:
description: authenticate vendor access to service endpoint
- !variable
id: postgres-password
annotations:
description: login credential for app database
# Entitlements
- !group users
- !permit
role: !group users
privileges: [ read, execute ]
resources: [ !variable vendor-oauth-token, !variable postgres-
password ]
- !grant
role: !group users
members:
- !layer app
Talking Tech: Puppet Webinar Series](https://image.slidesharecdn.com/puppetandcyberarkwebinarfinal-171108233138/85/Delivering-Infrastructure-and-Security-Policy-as-Code-with-Puppet-and-CyberArk-Conjur-25-320.jpg)