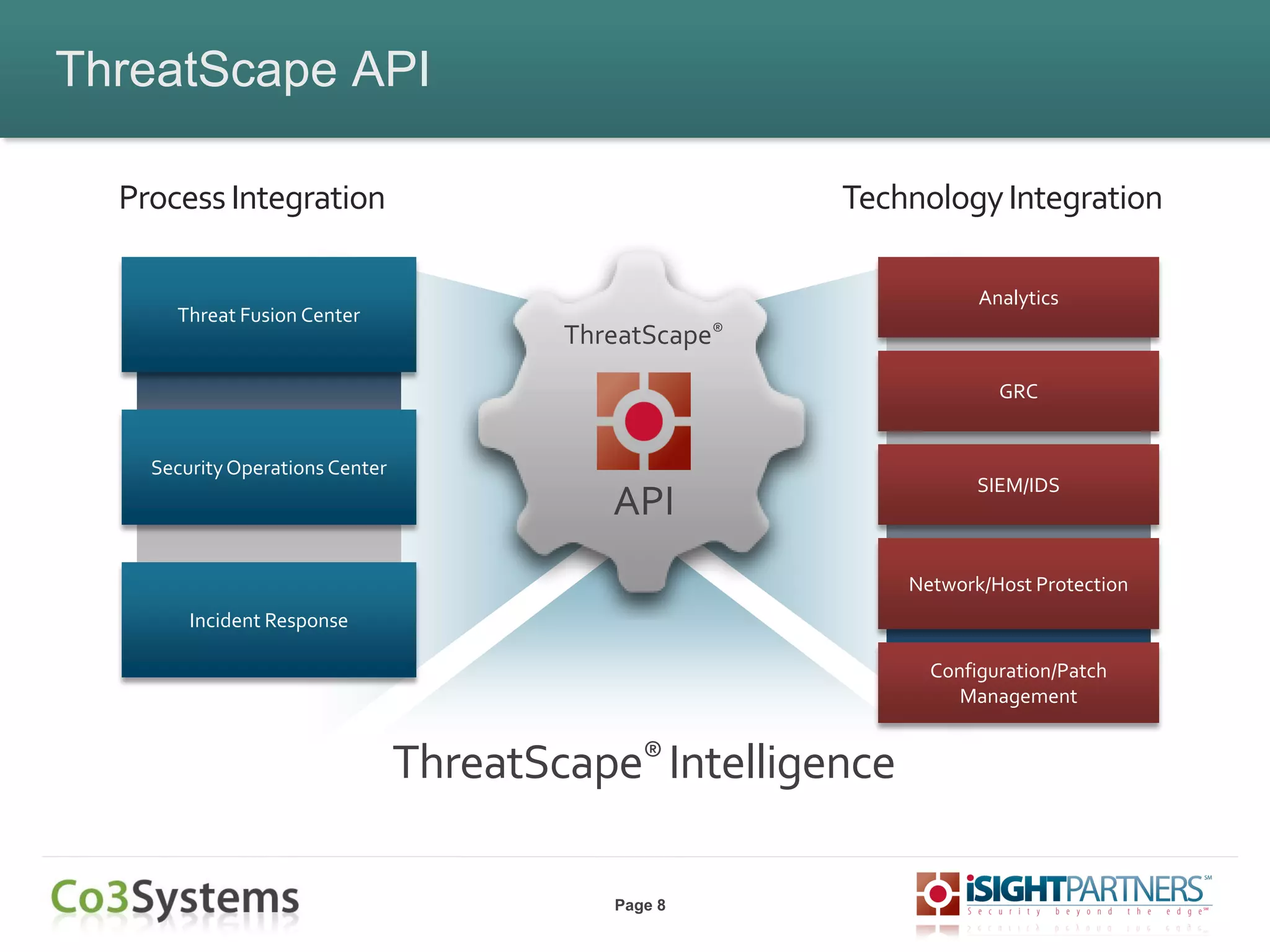
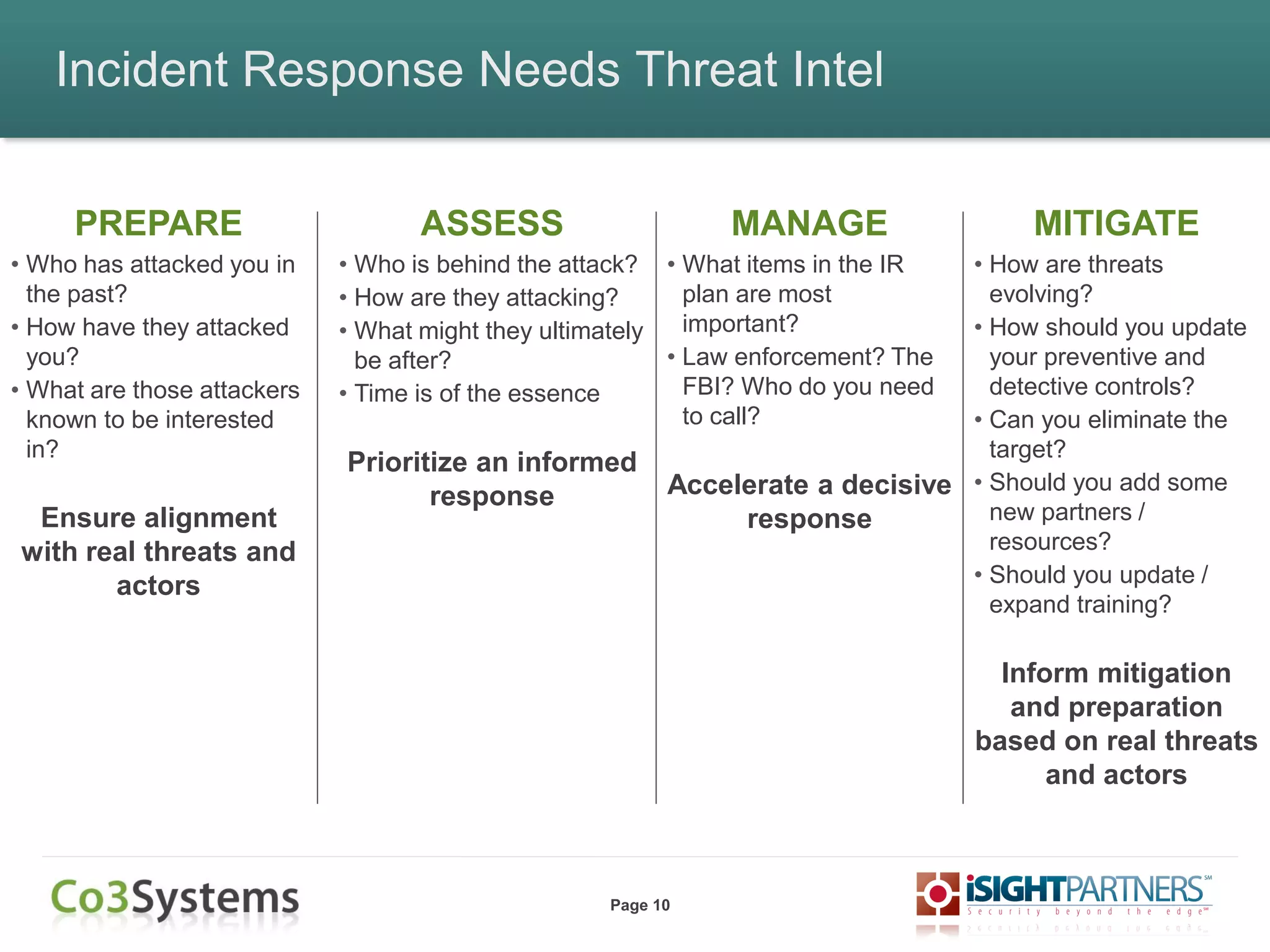
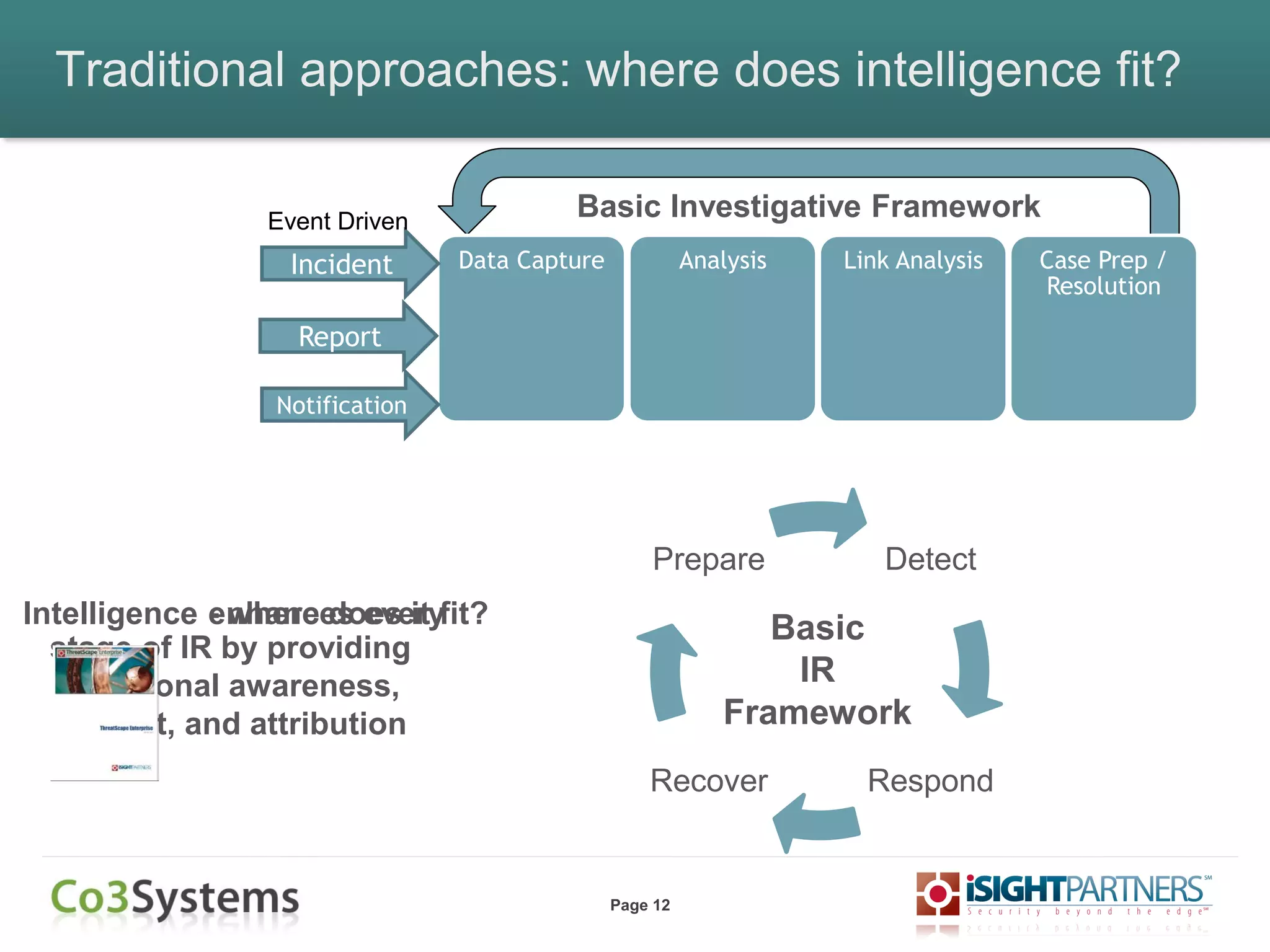
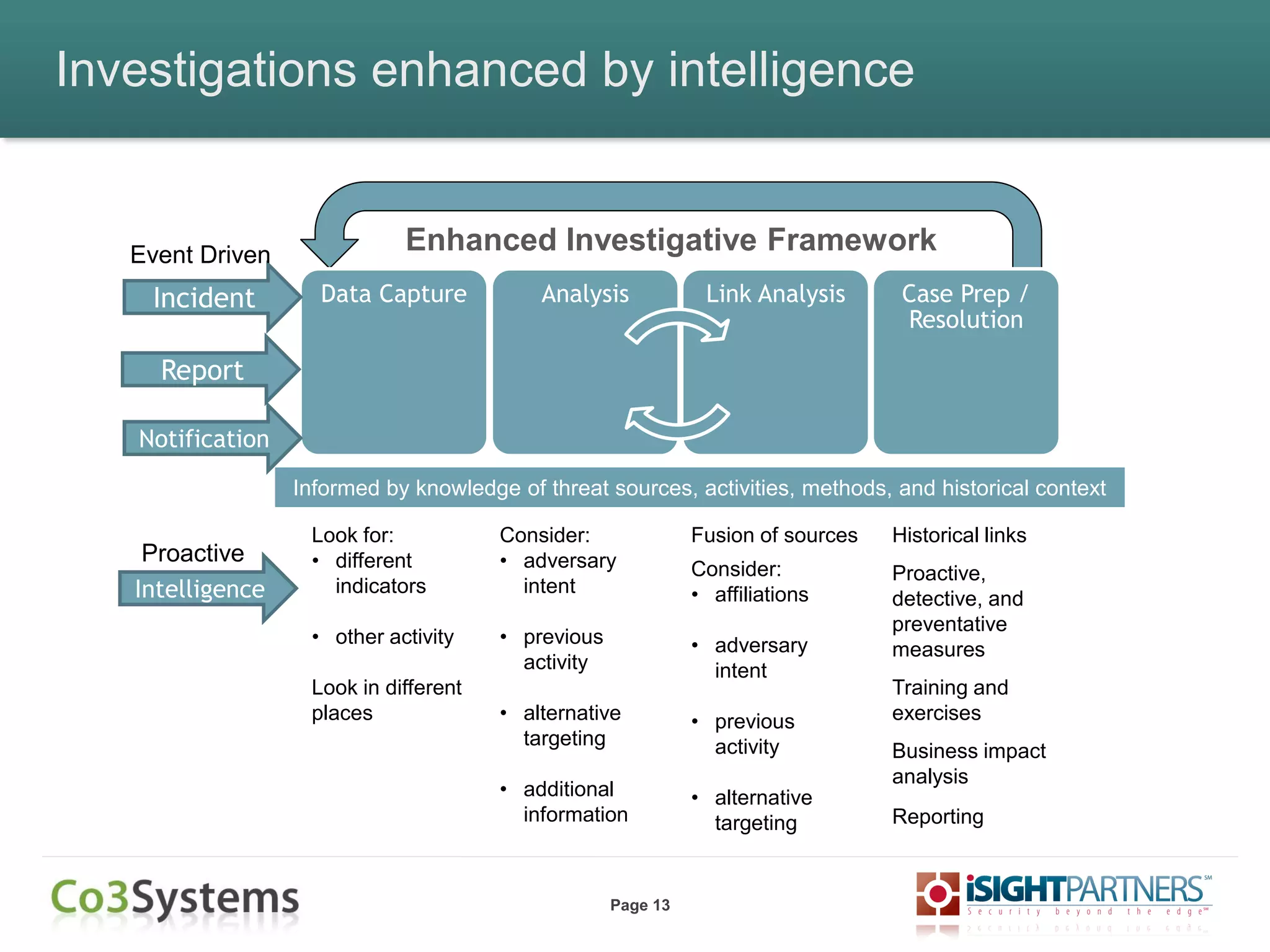
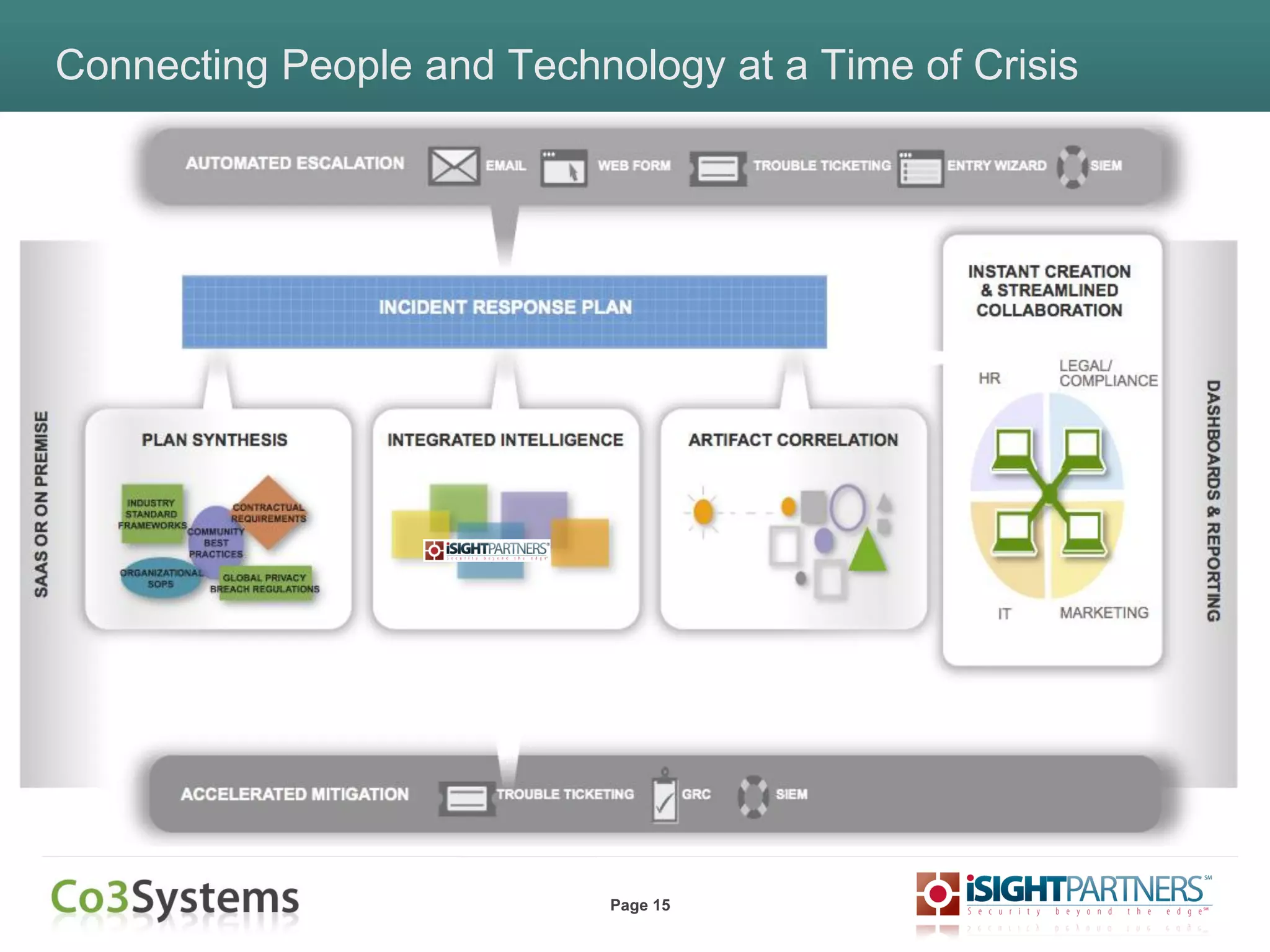
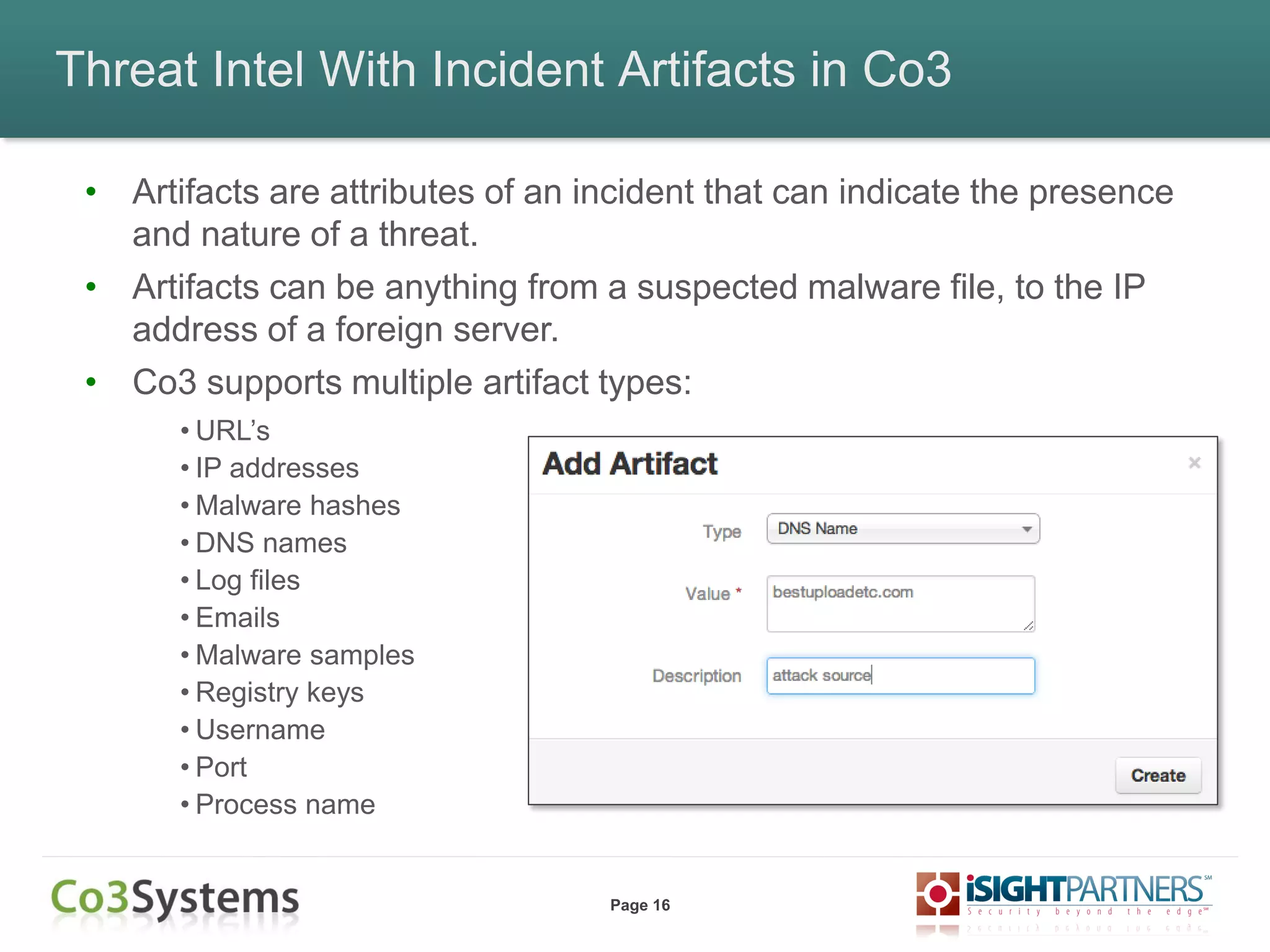
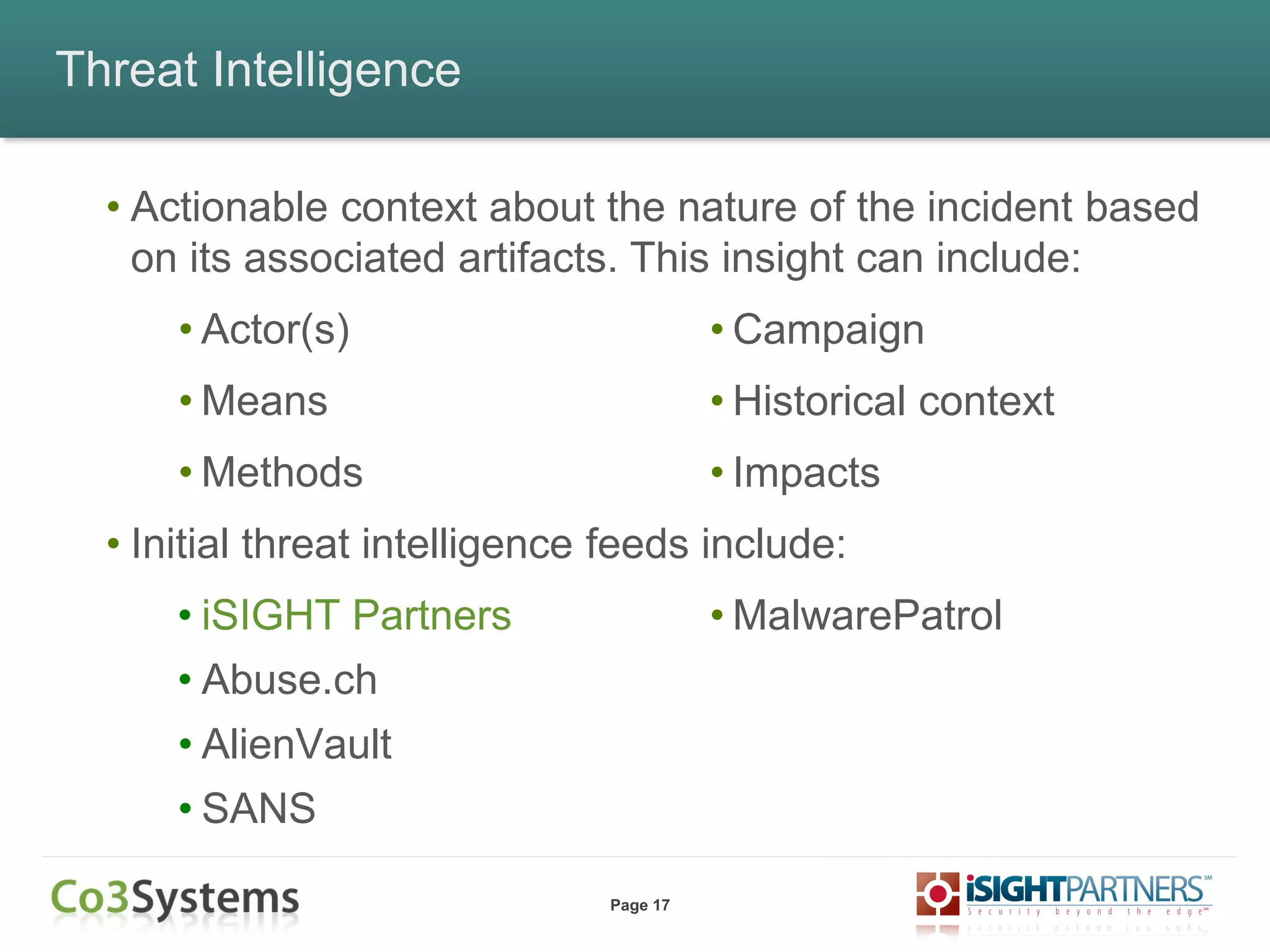
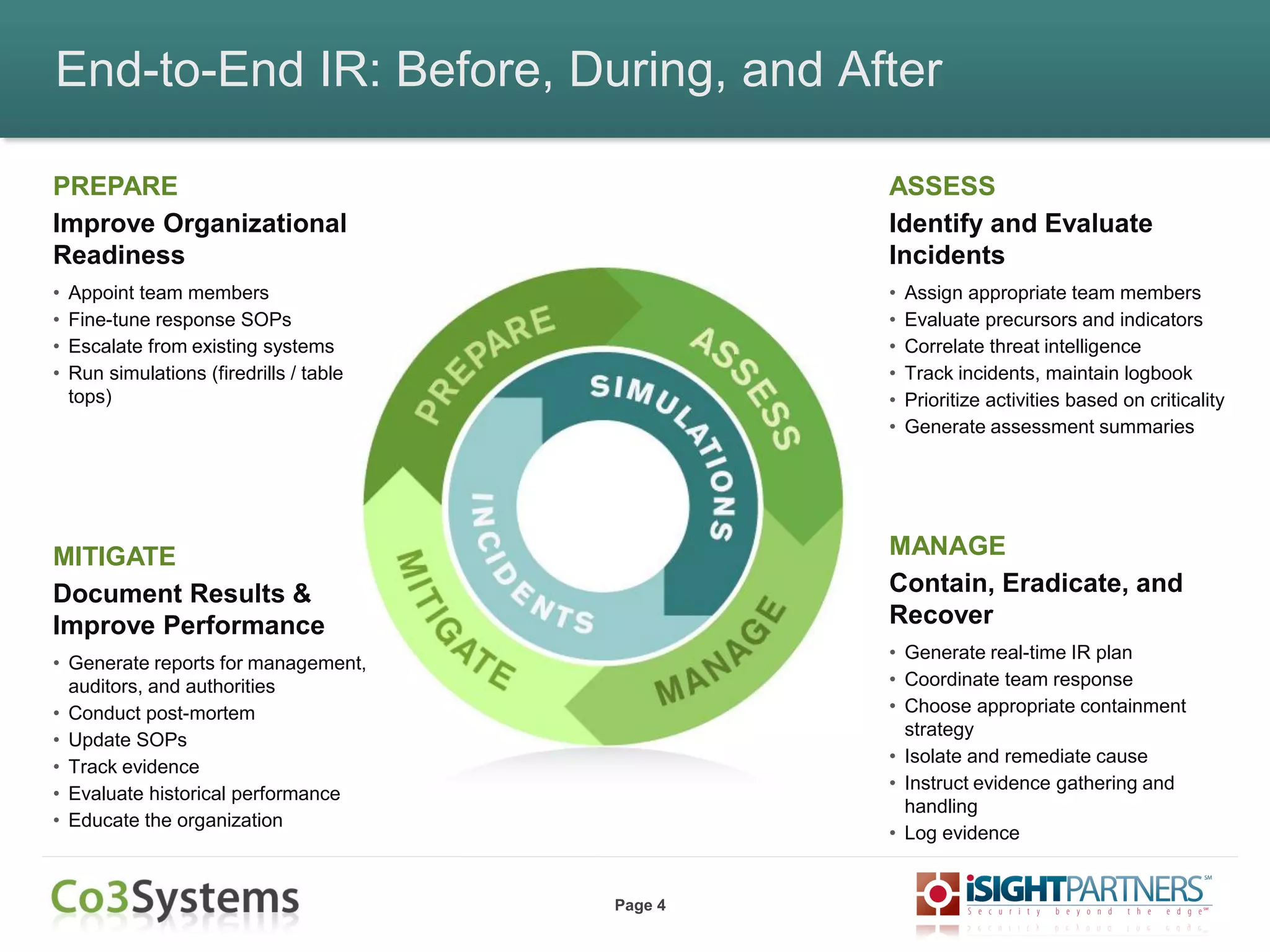
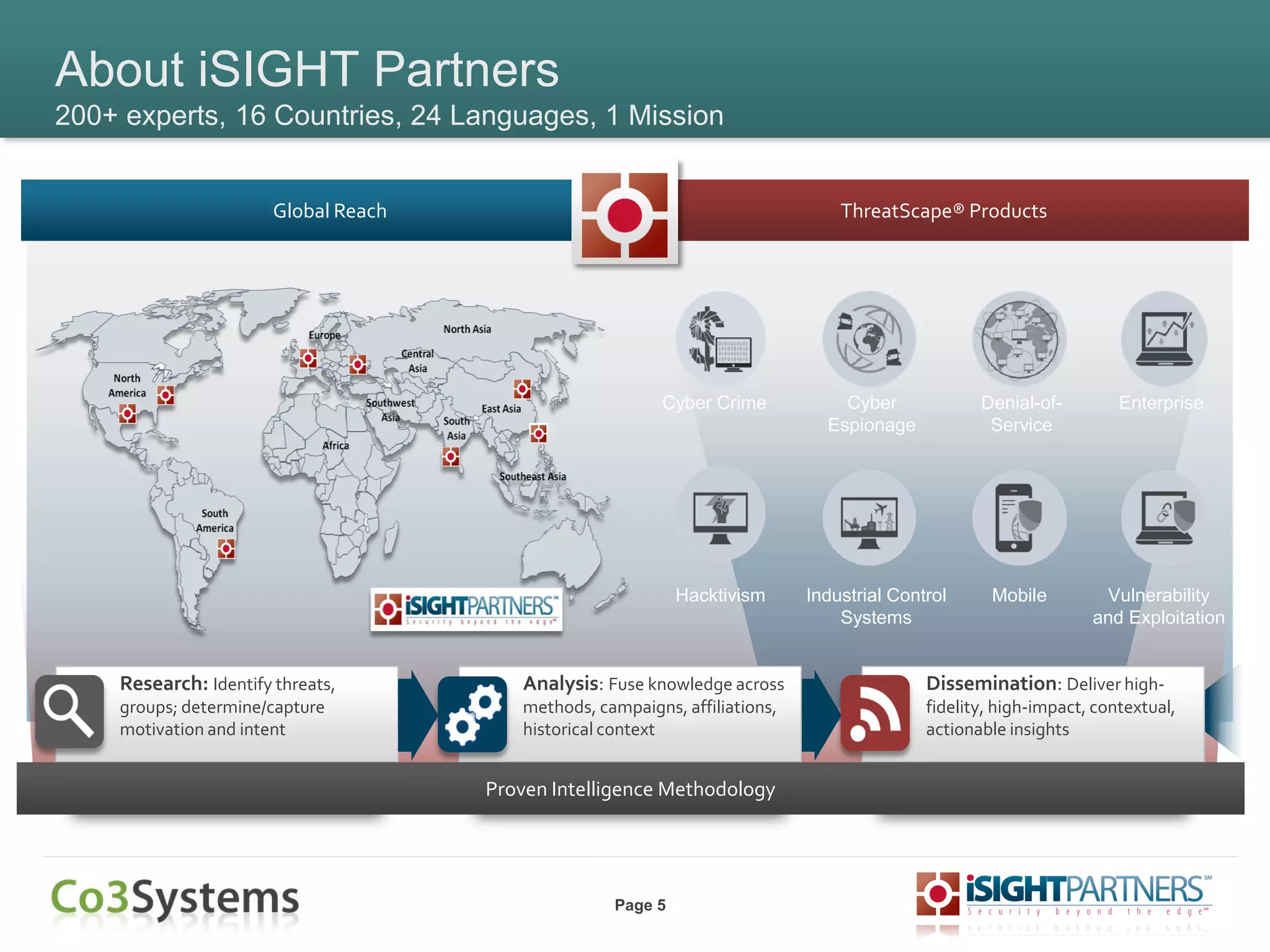
The document outlines strategies for enhancing incident response (IR) using threat intelligence, emphasizing its importance in preparation, mitigation, assessment, and management throughout the IR process. It discusses how organizations can leverage actionable context from threat intelligence to improve decision-making and streamline response times. Additionally, it highlights the role of various experts and technologies in integrating threat intelligence into existing IR frameworks.


![Page 7
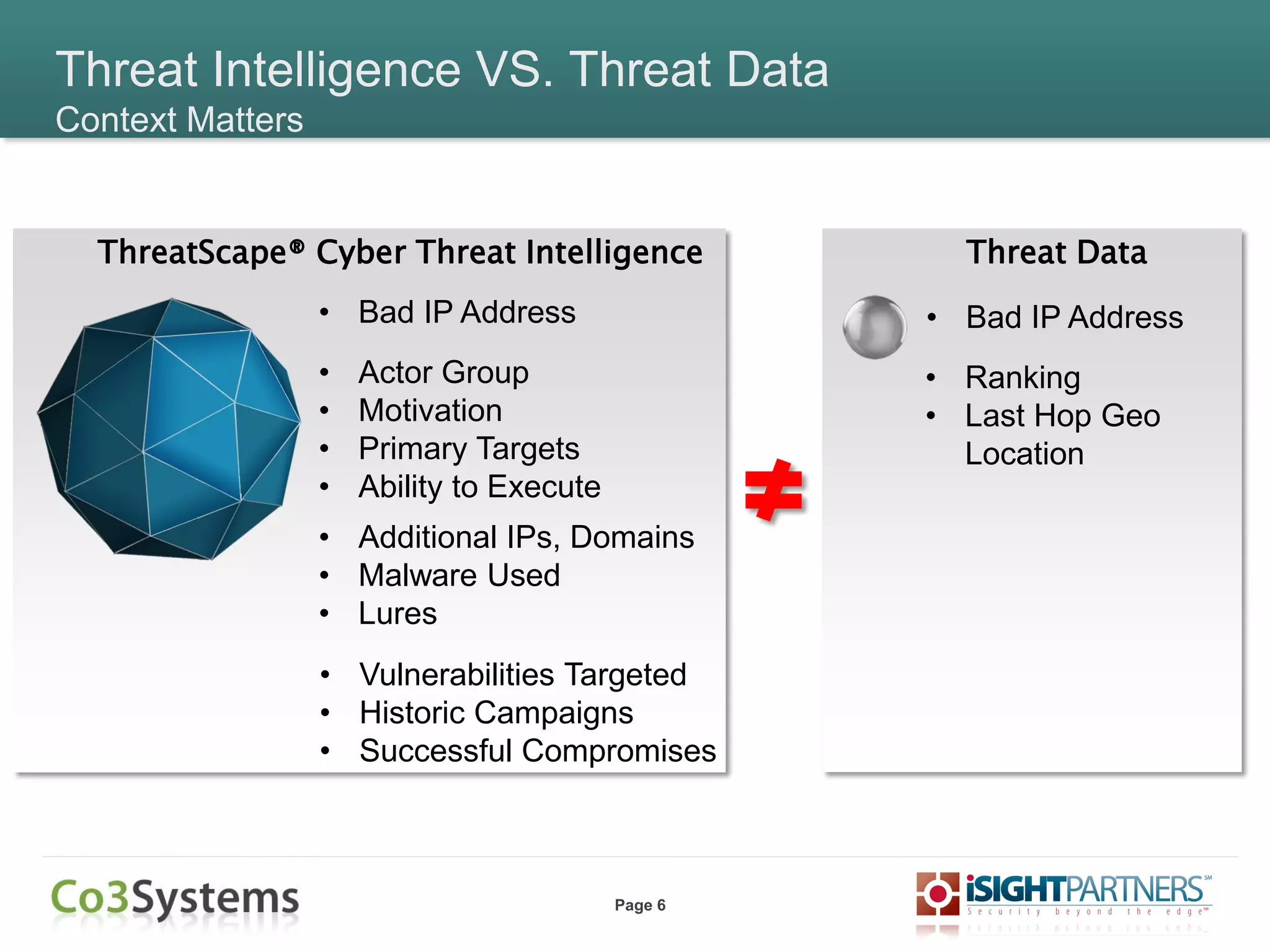
What is Threat Intelligence?
Name: uxsue.exe
Identifier: Gameover Zeus
Extension: exe
Type: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
Size: 329216
Packer: ['MinGW GCC 3.x']
MD5sum: 045b793b2a47fbea0d341424262c8c5b
Sha1: 5ca6943f557489b510bd0fe8825a7a68ef00af53
Sha256: 8a4036289762a4414382fee8463d2bc7892cd5cab8fb6995eb94706d47e781dd
Fuzzy: 6144:ka23d0lraSurrtt/xue1obsXD8J3Ej+rbC80tsX9GR:kFd0lWzrrtxdowT8U8hYR
MIME:
Compiled: 2012-10-10 17:33:25
Malware Payload Indicators:
Gameover Zeus is a frequently used Trojan in financial cybercrime
Basic Context:
Exploitation Vector:
hxxp://26.azofficemovers.com/links/persons_jobs.php
Unique Threat-focused Information:
We believe the following actors are either members of or are close
associates with the petr0vich group: …
Bottom Line:
Zeus Malware Author Probably Working with Gameover Zeus Operators,
but Current Level of Involvement Remains Uncertain
Contextual Analysis:
…the primary Zeus author partnered with the "petr0vich group,"
which most likely controls Gameover Zeus, to develop custom Zeus
versions…. his continued participation will probably help fuel further
innovative developments to Zeus.
Knowledge and context, not just data
Technical Threat](https://image.slidesharecdn.com/co3isight-threatintelfinal-140410133642-phpapp01/75/How-To-Turbo-Charge-Incident-Response-With-Threat-Intelligence-7-2048.jpg)