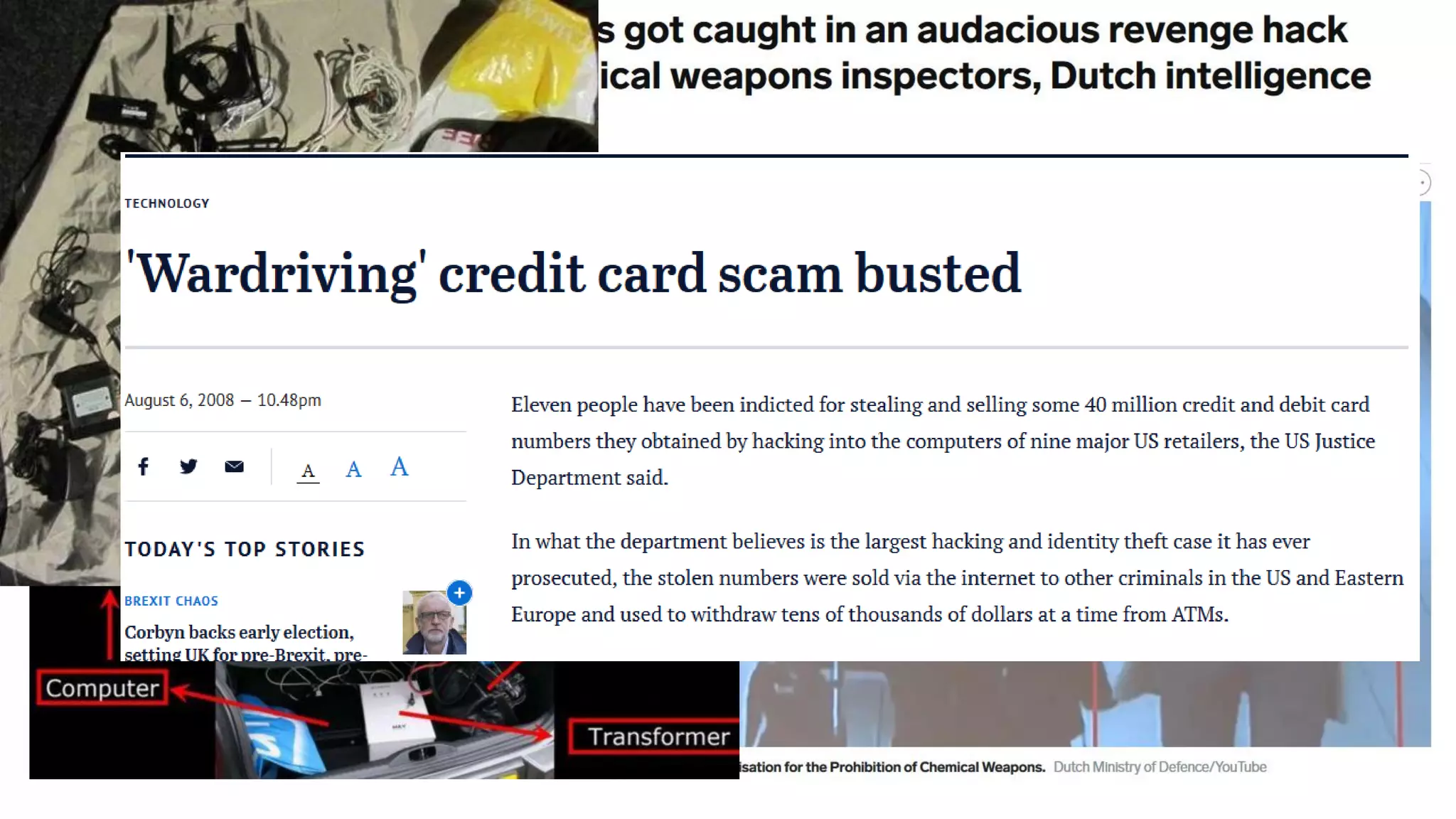
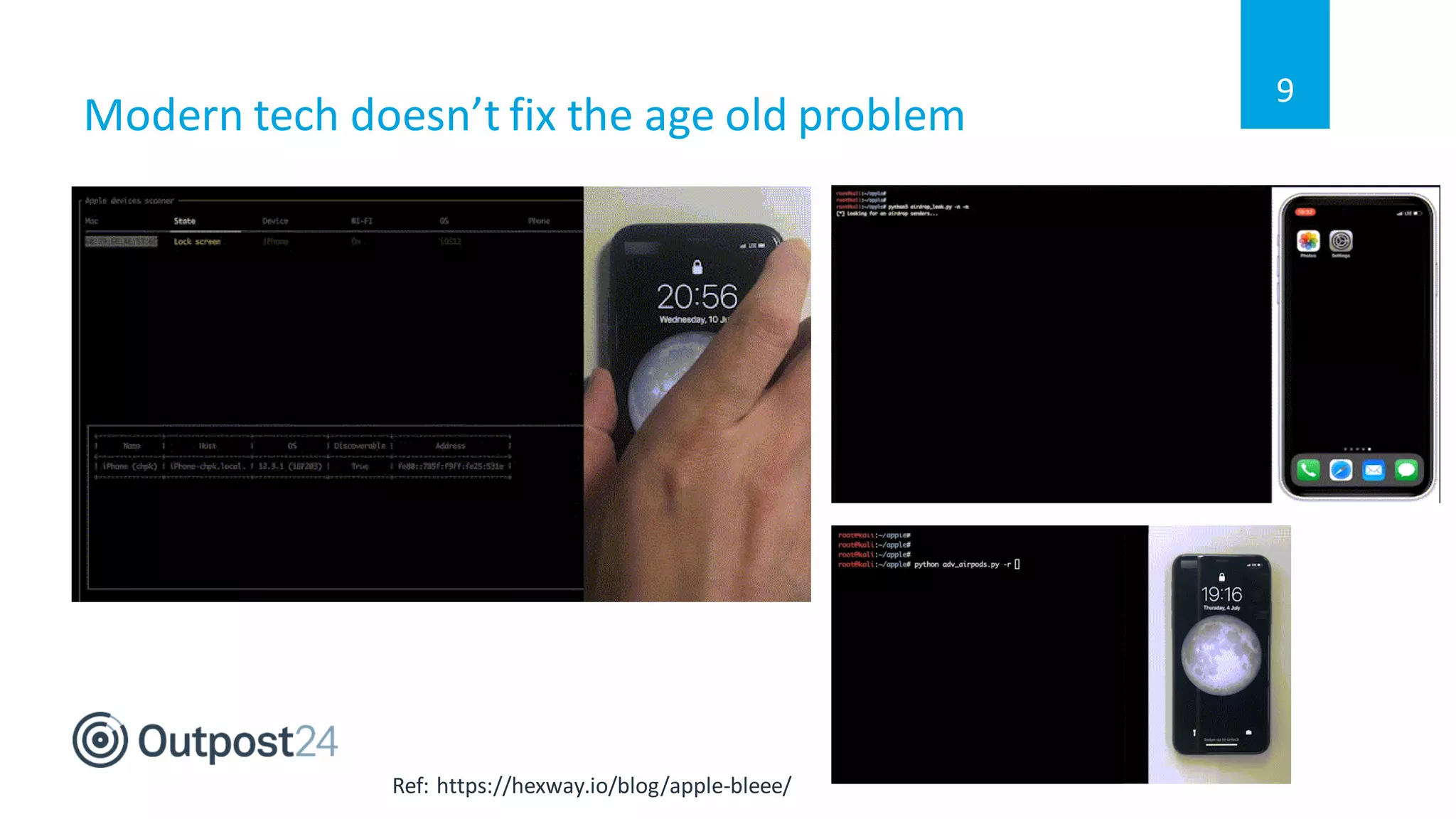
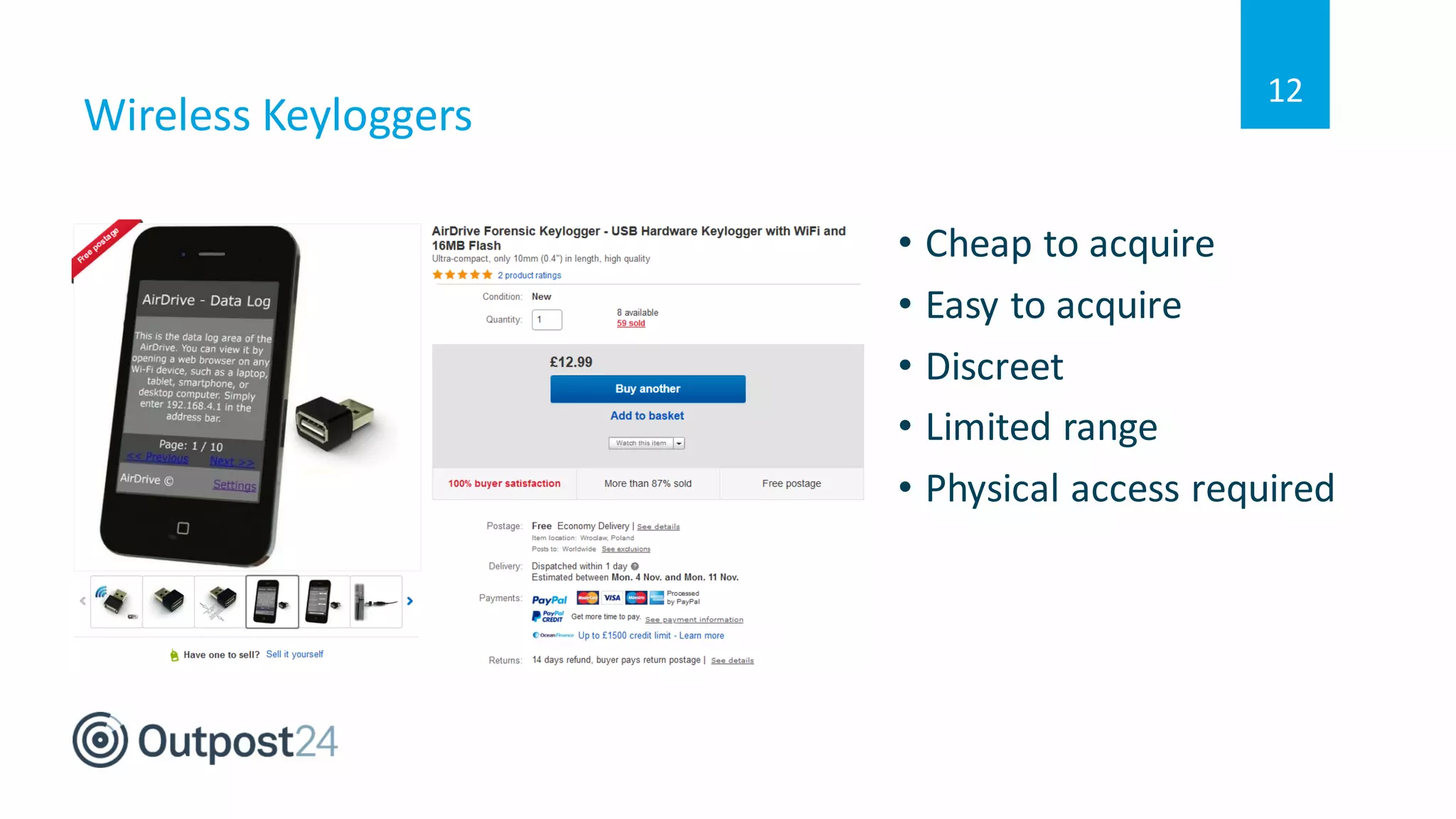
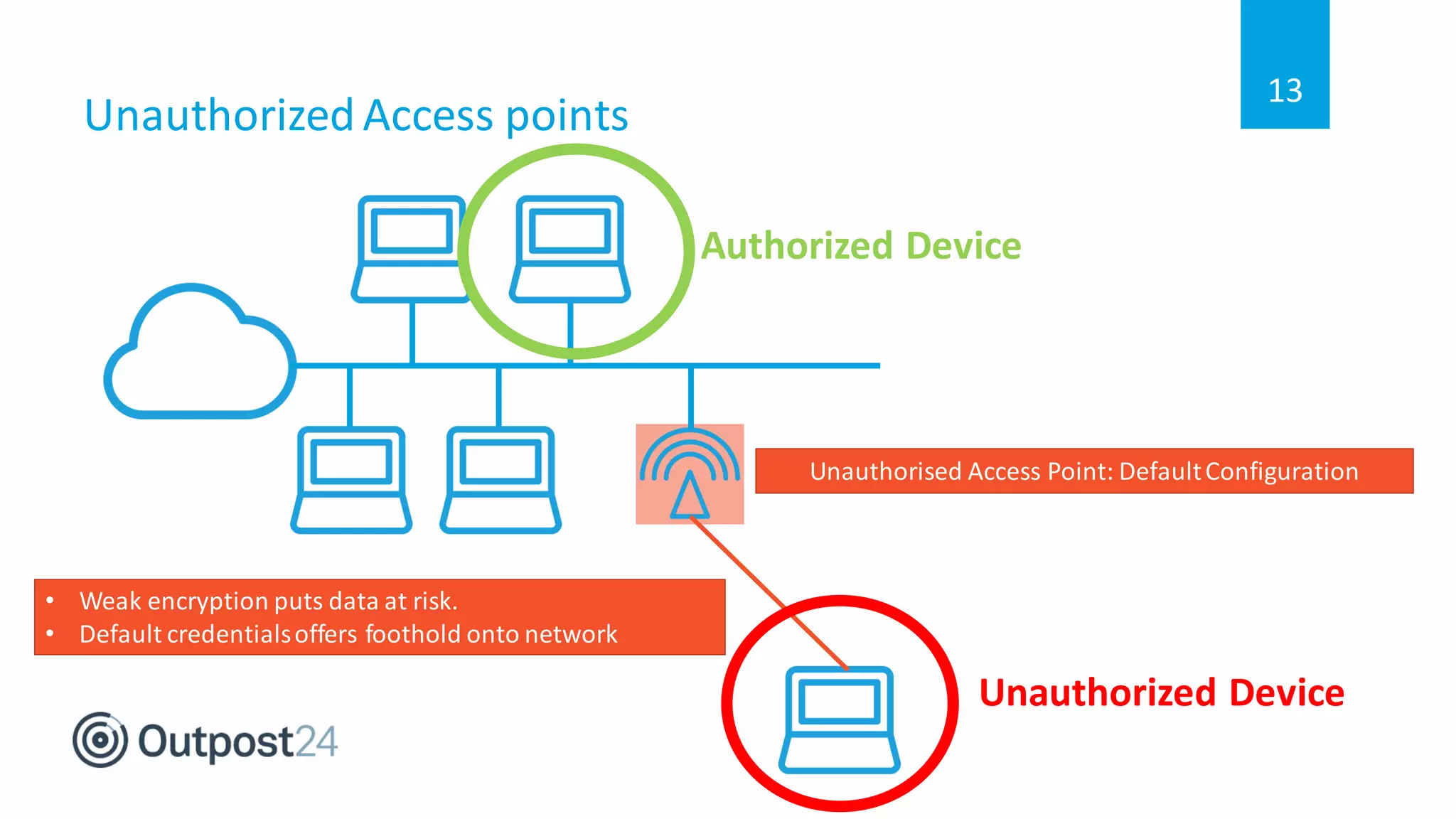
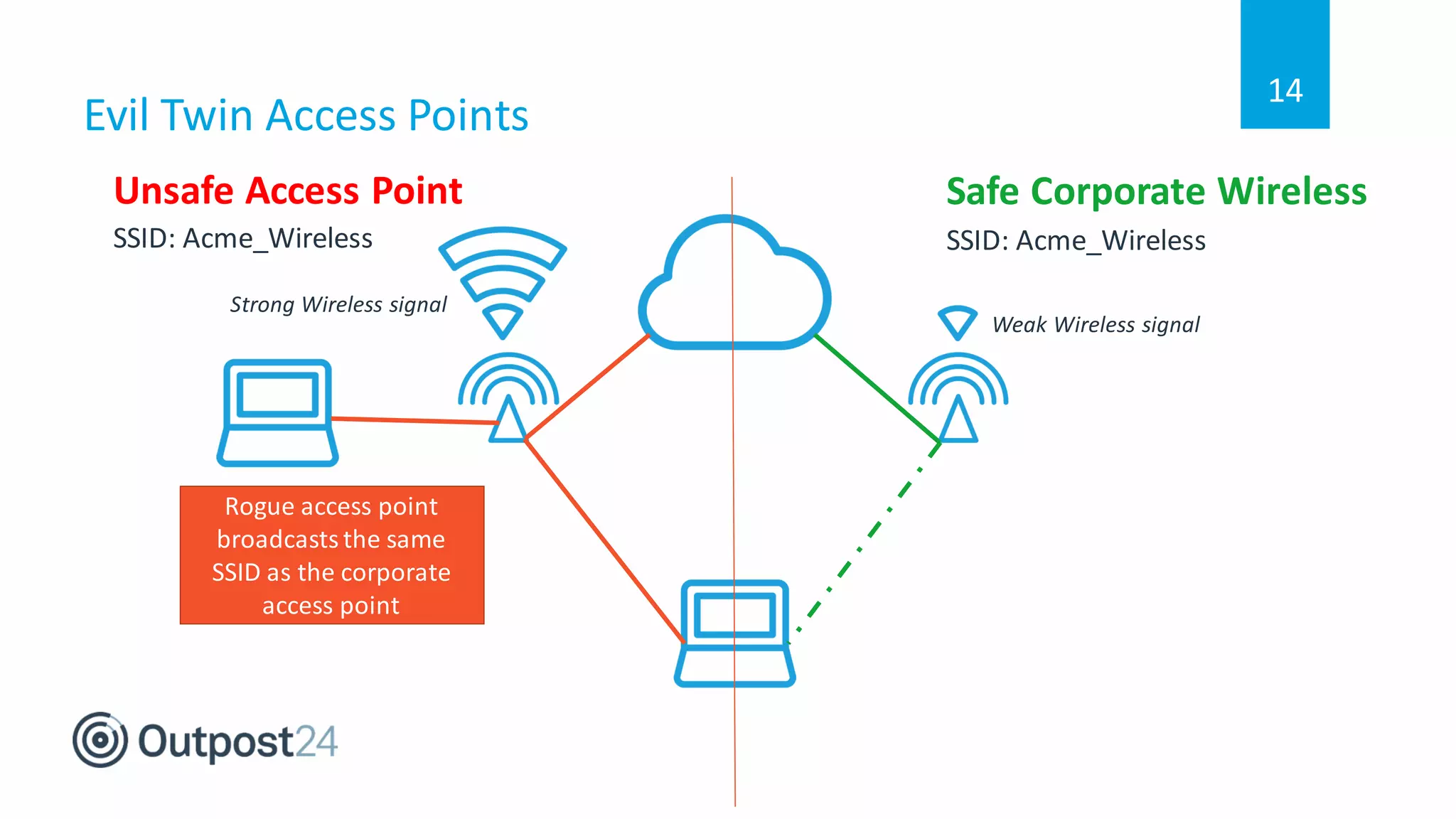
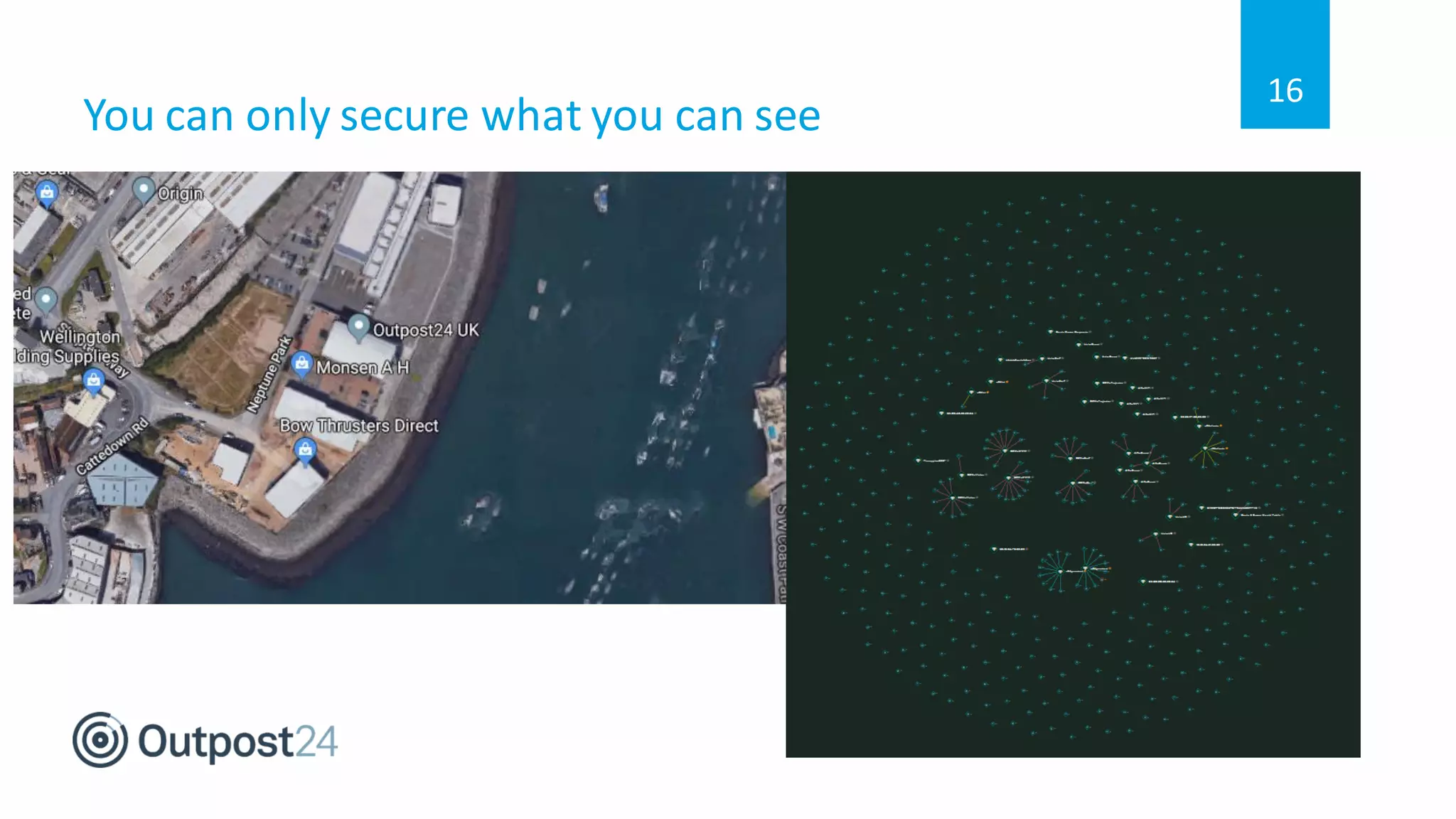
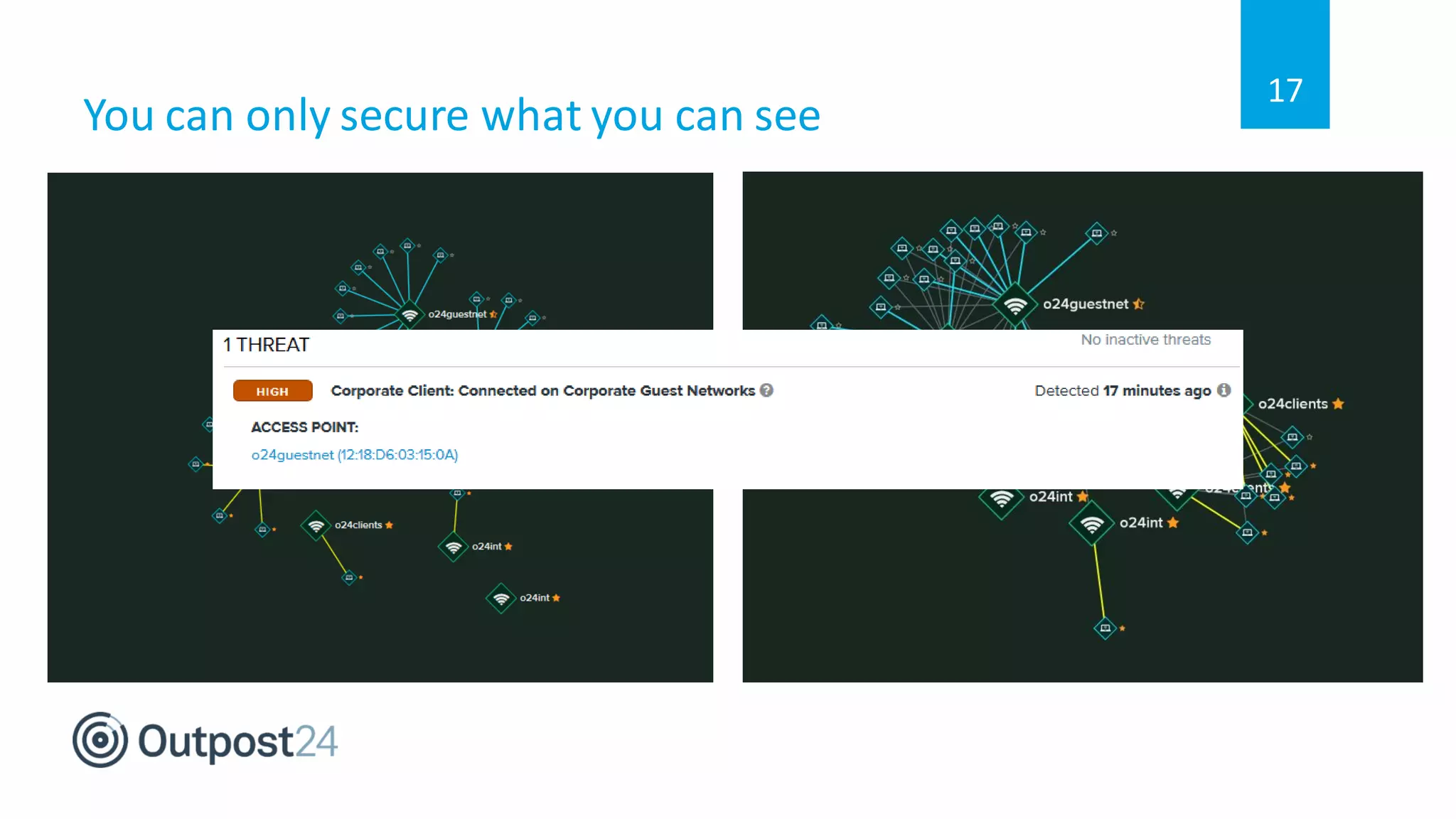
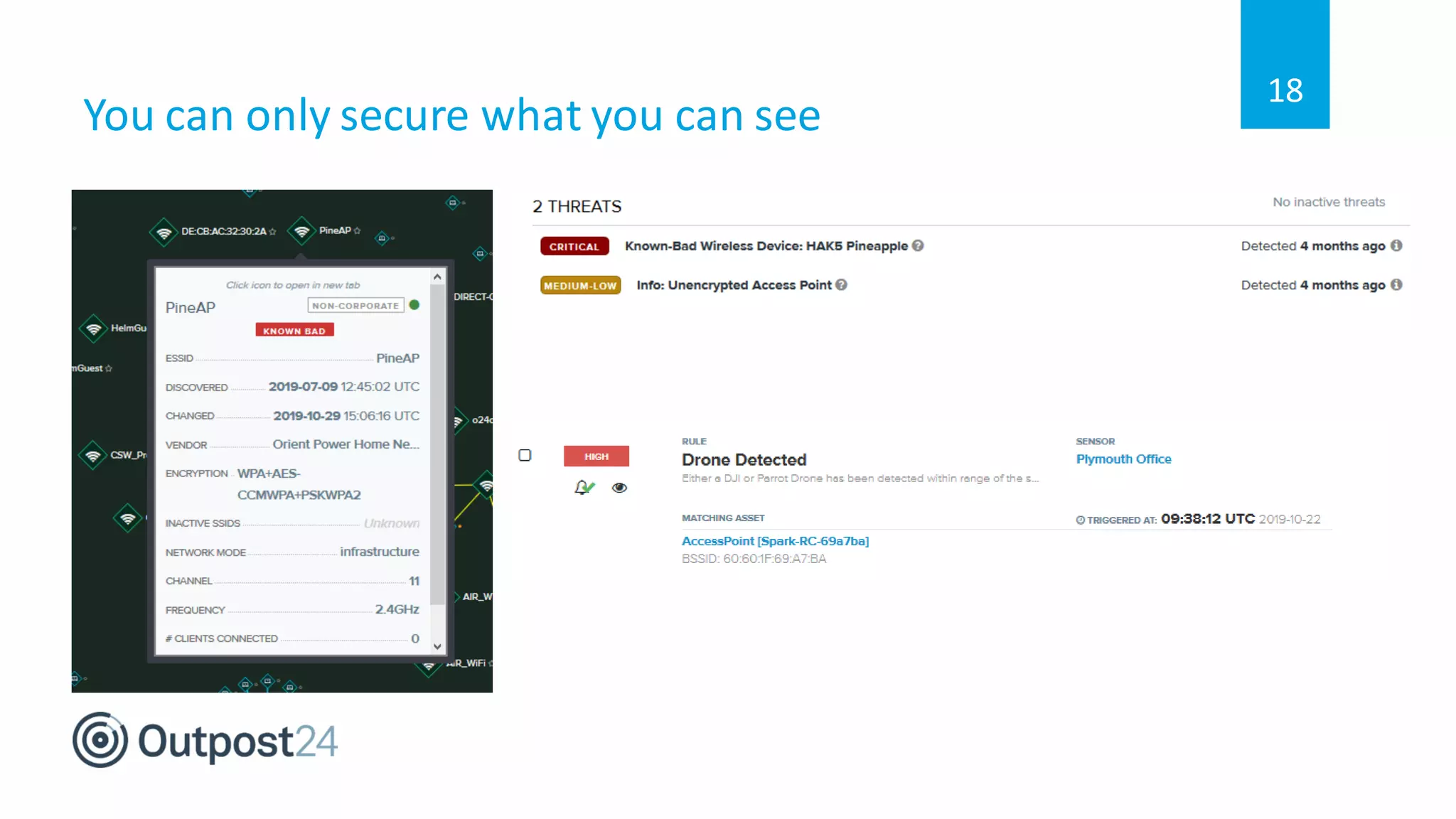
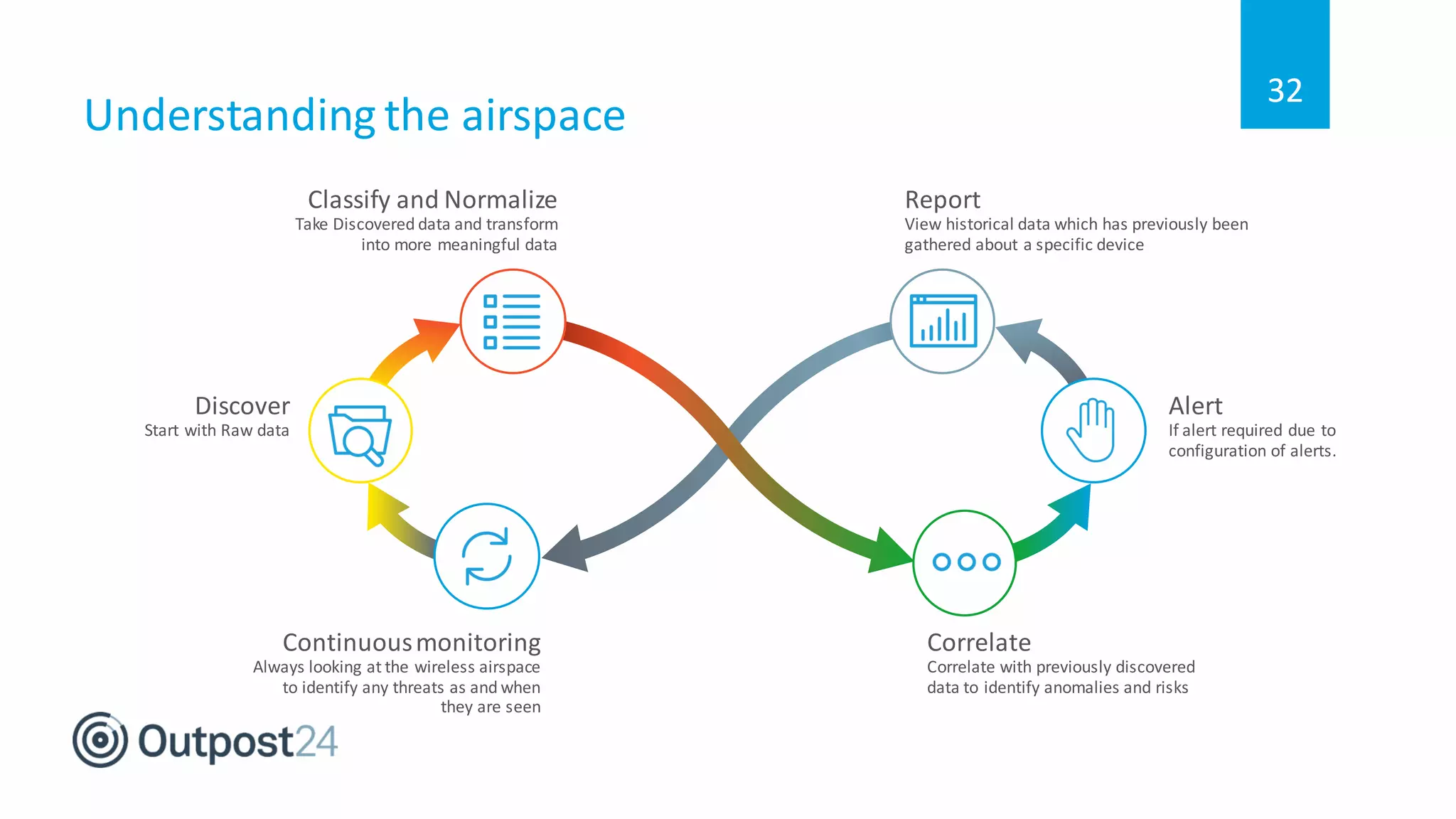
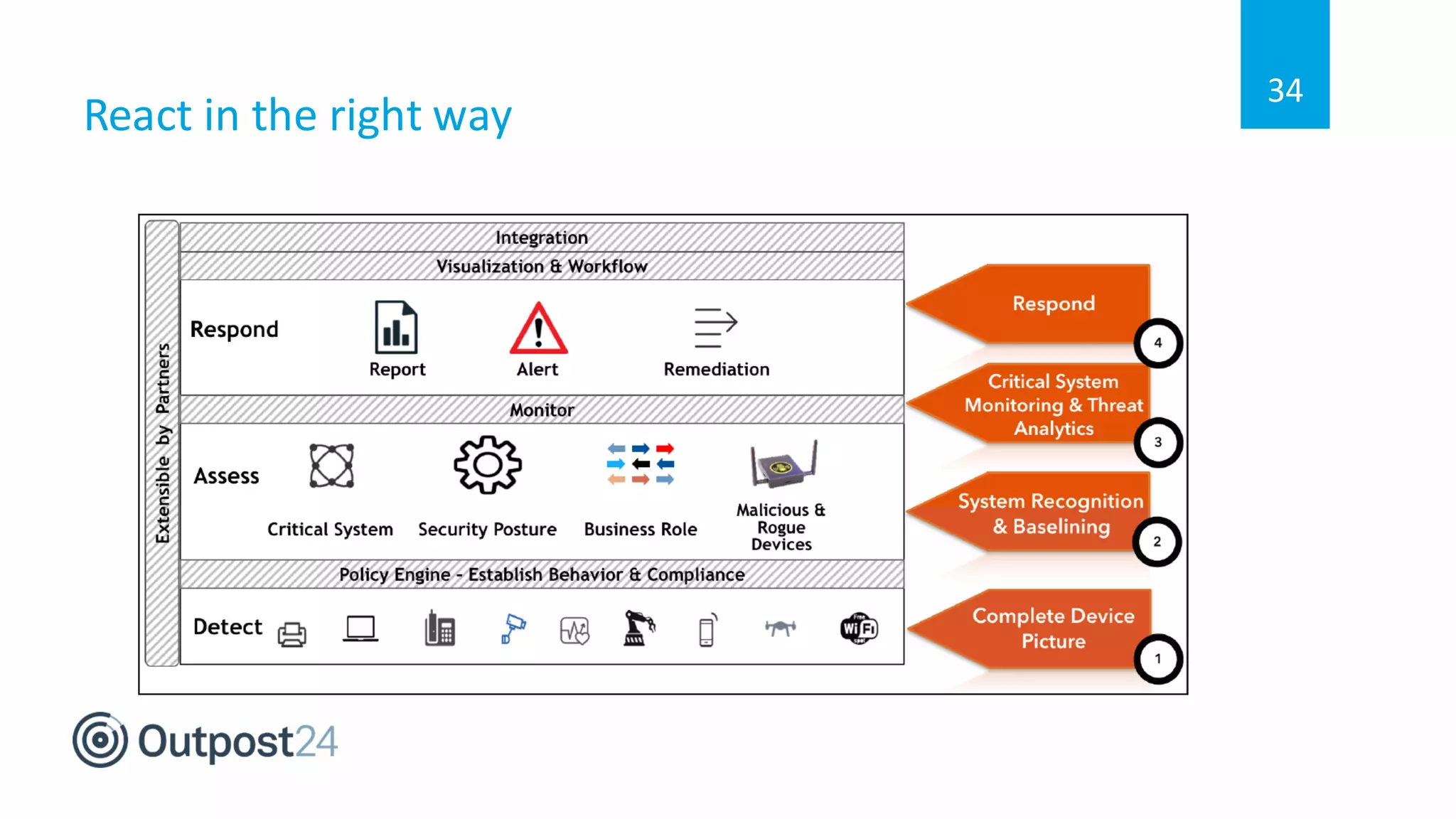
The document discusses common wireless security threats, particularly focusing on shadow devices and airborne attacks that can bypass security measures. It emphasizes the importance of asset visibility and the need for effective monitoring and enforcement of network access policies to mitigate risks. The key takeaway is that awareness and proactive security measures are essential in the evolving wireless landscape to prevent unauthorized access.