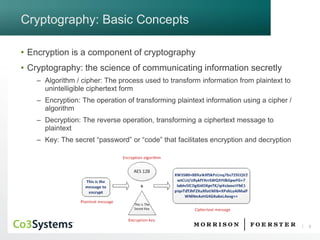
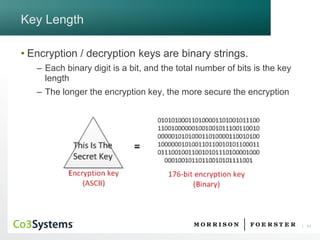
This document provides an overview of encryption and incident response management. It begins with an agenda for a presentation on encryption, practical considerations, and legal limitations. It then discusses cryptography concepts like encryption, decryption, and hashing. It covers the goals of cryptography including privacy, authentication, integrity and non-repudiation. Next, it discusses symmetric, asymmetric and hashing algorithms as well as encryption versus hashing. The document then covers practical considerations like key length, encryption in transit versus storage. It also discusses legal requirements for encryption in various jurisdictions and restrictions on encryption. Finally, it discusses secure implementation, key management, and incident response management.