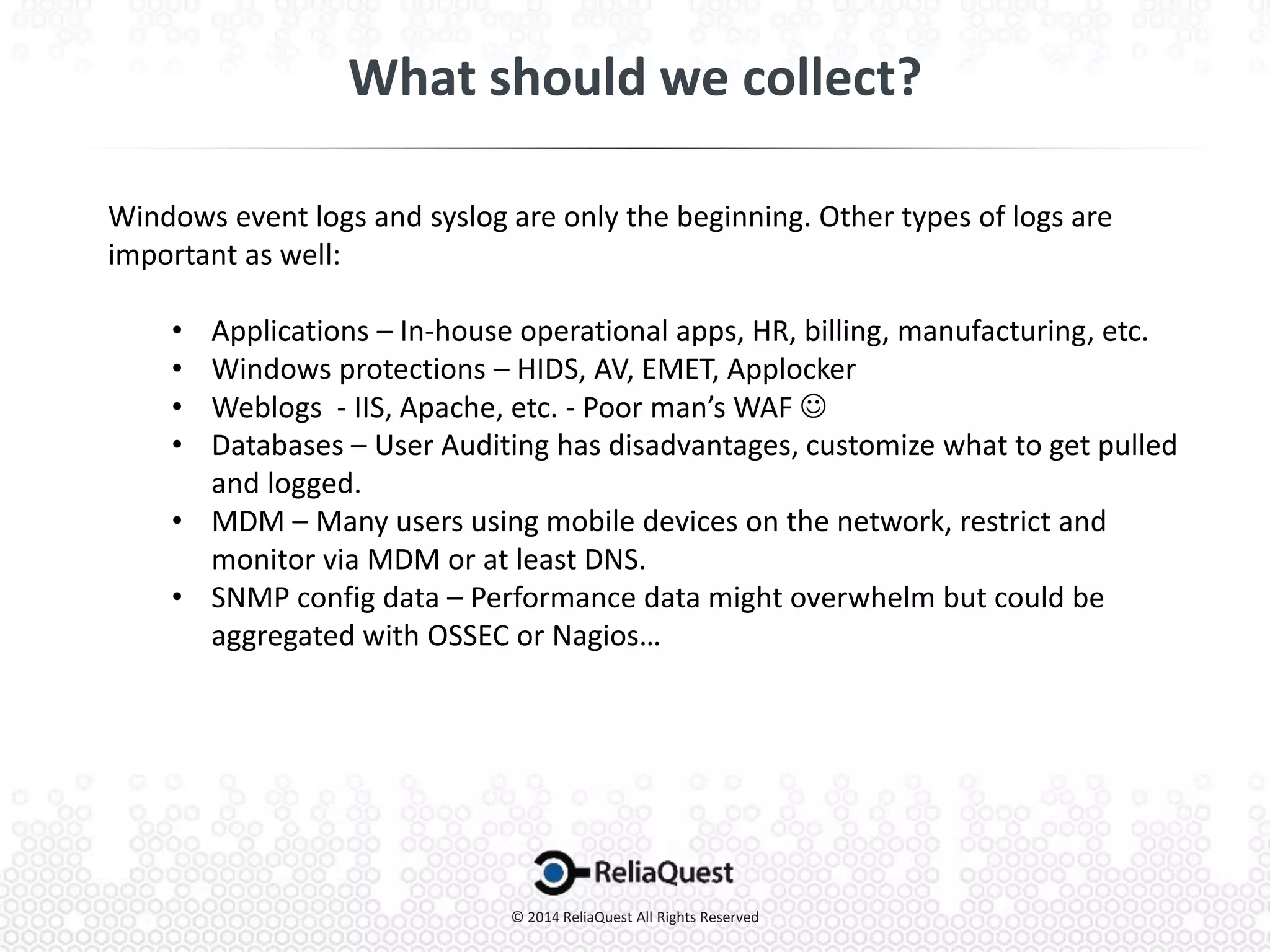
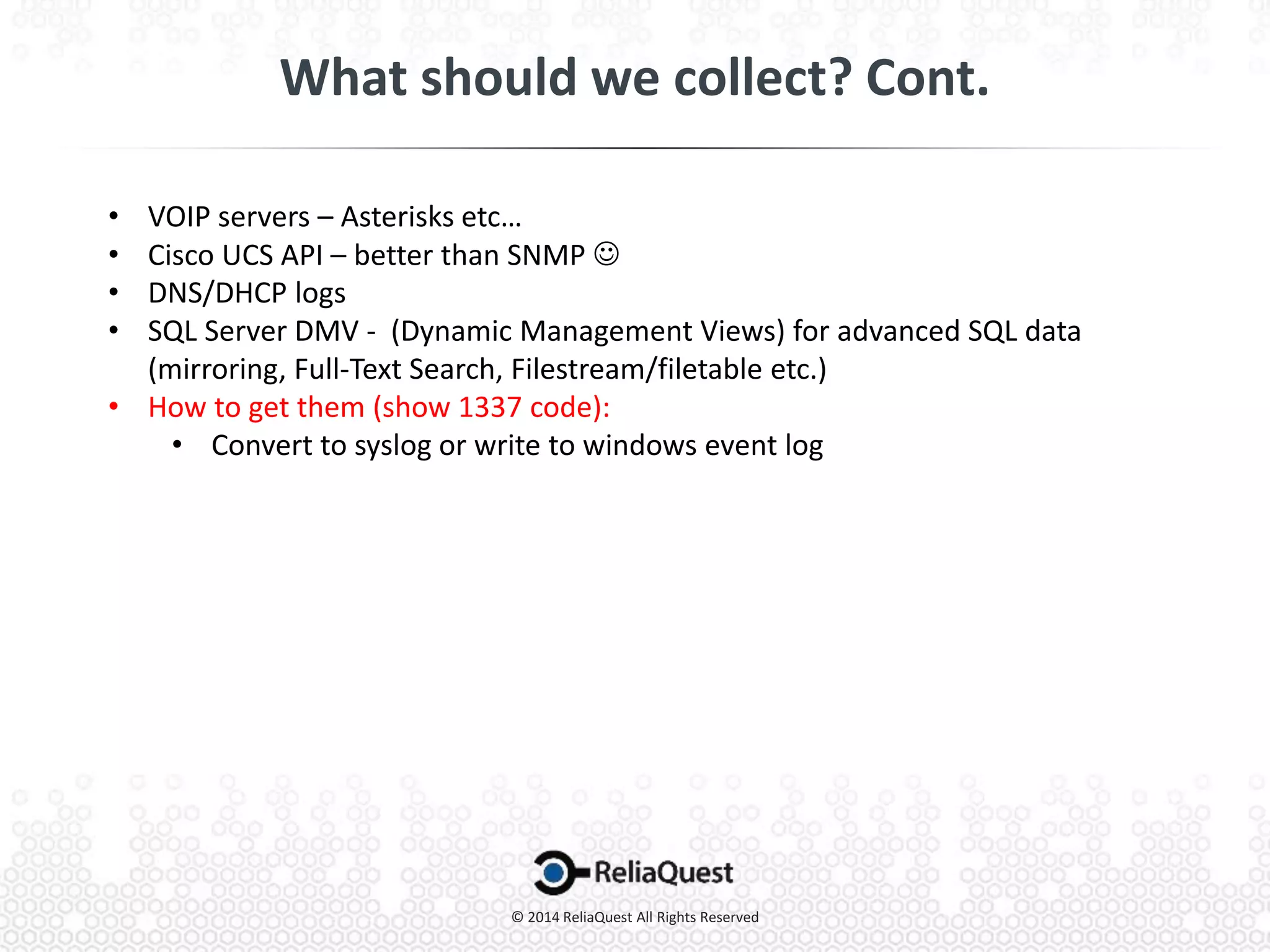
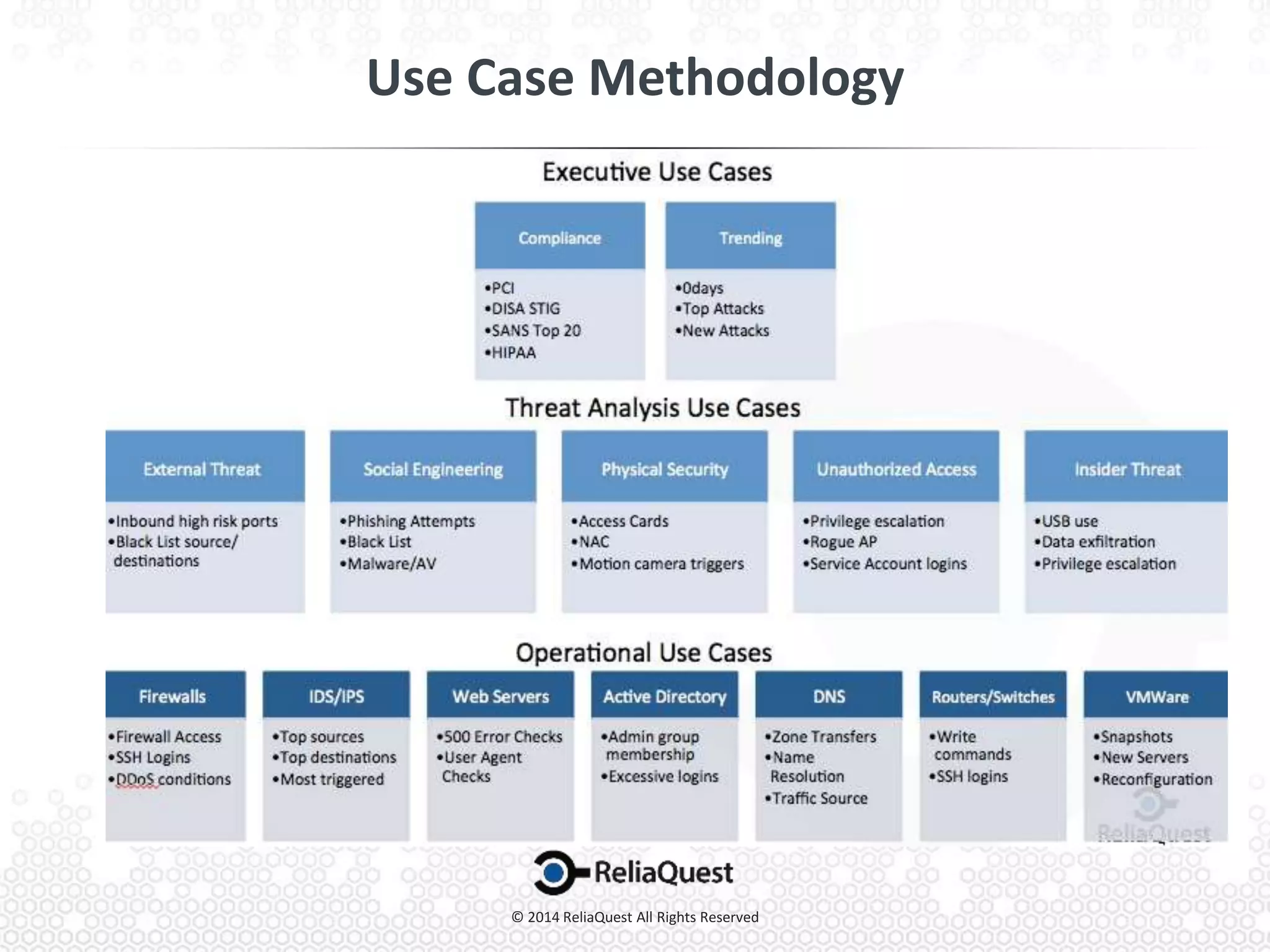
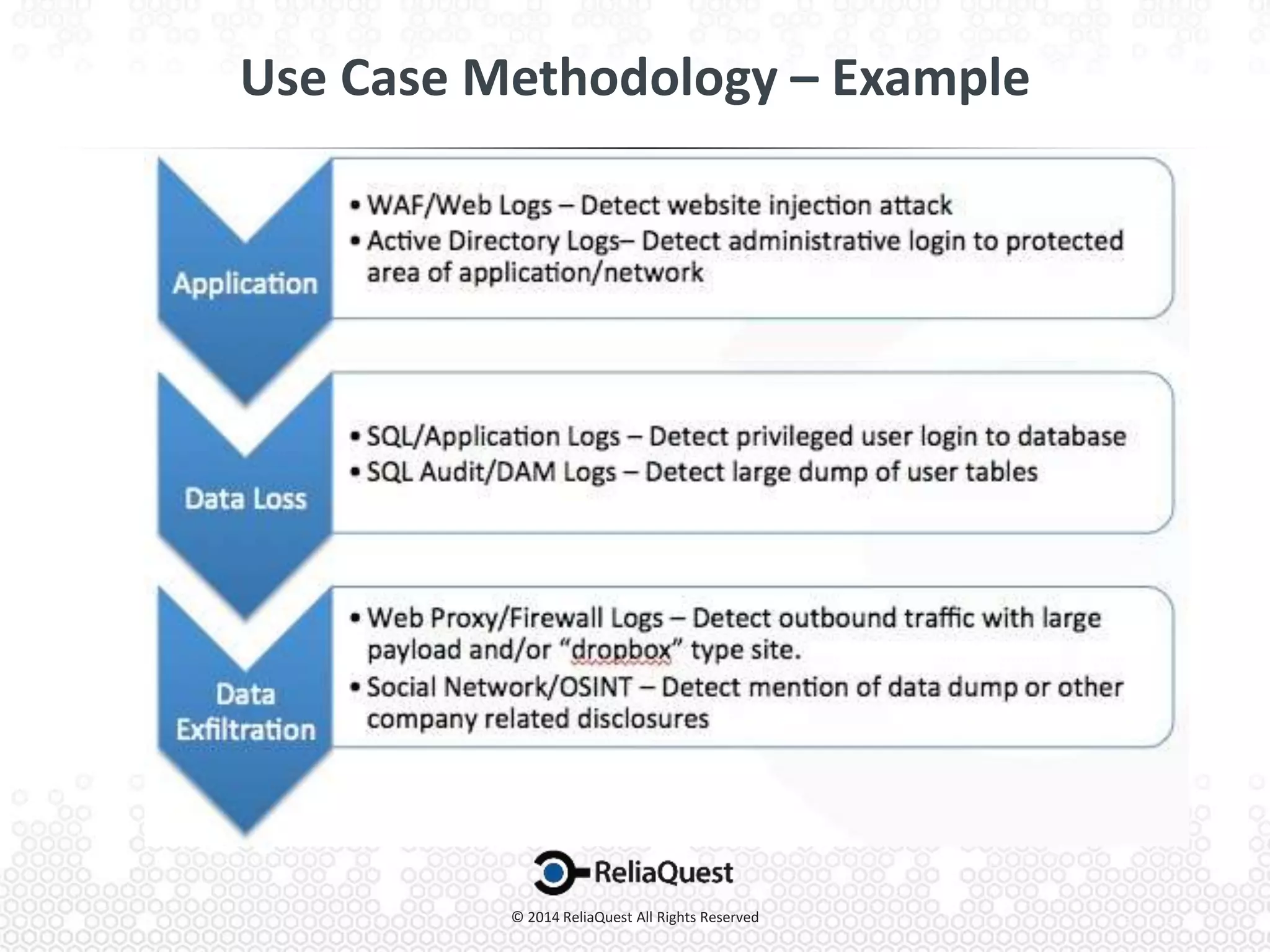
Joe Partlow discusses advanced SIEM optimization, highlighting its importance in monitoring and analyzing security logs to defend against threats. He emphasizes the need for constant configuration and tuning of SIEM systems to manage the overwhelming volume of logs and alerts from various sources. Strategies for improving SIEM effectiveness include aggregating events, tuning alerts, and ensuring visibility across all network segments and applications.