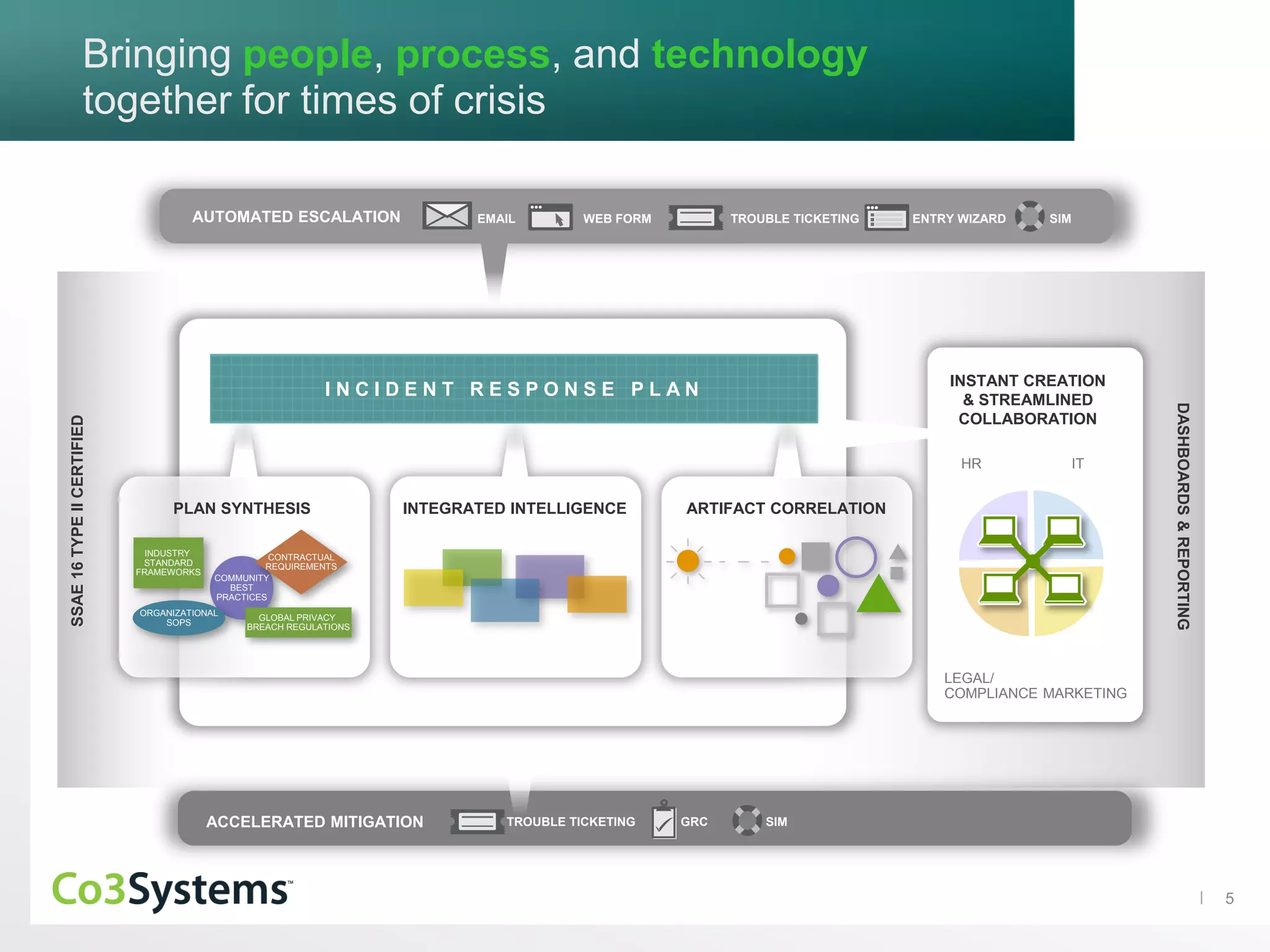
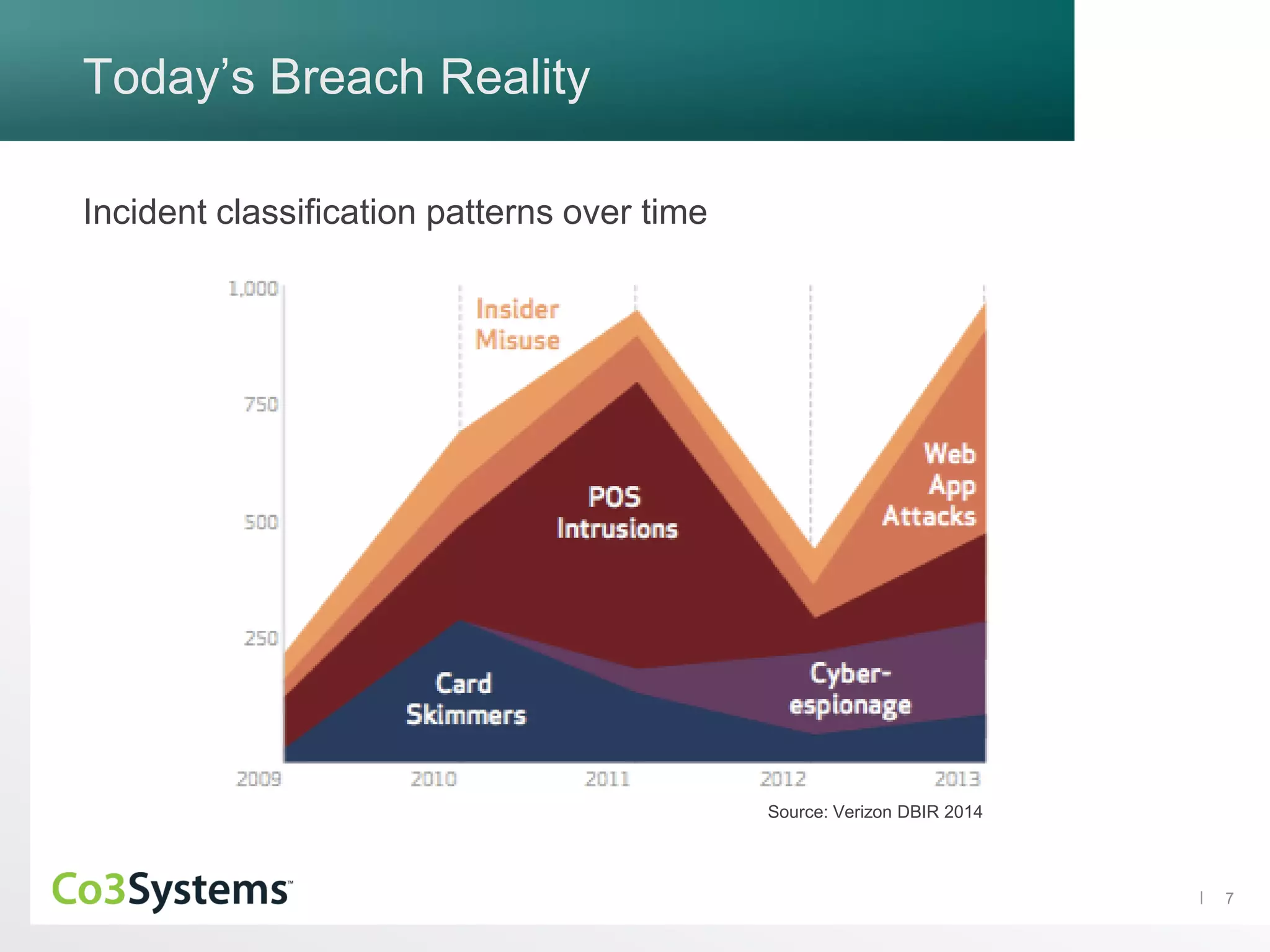
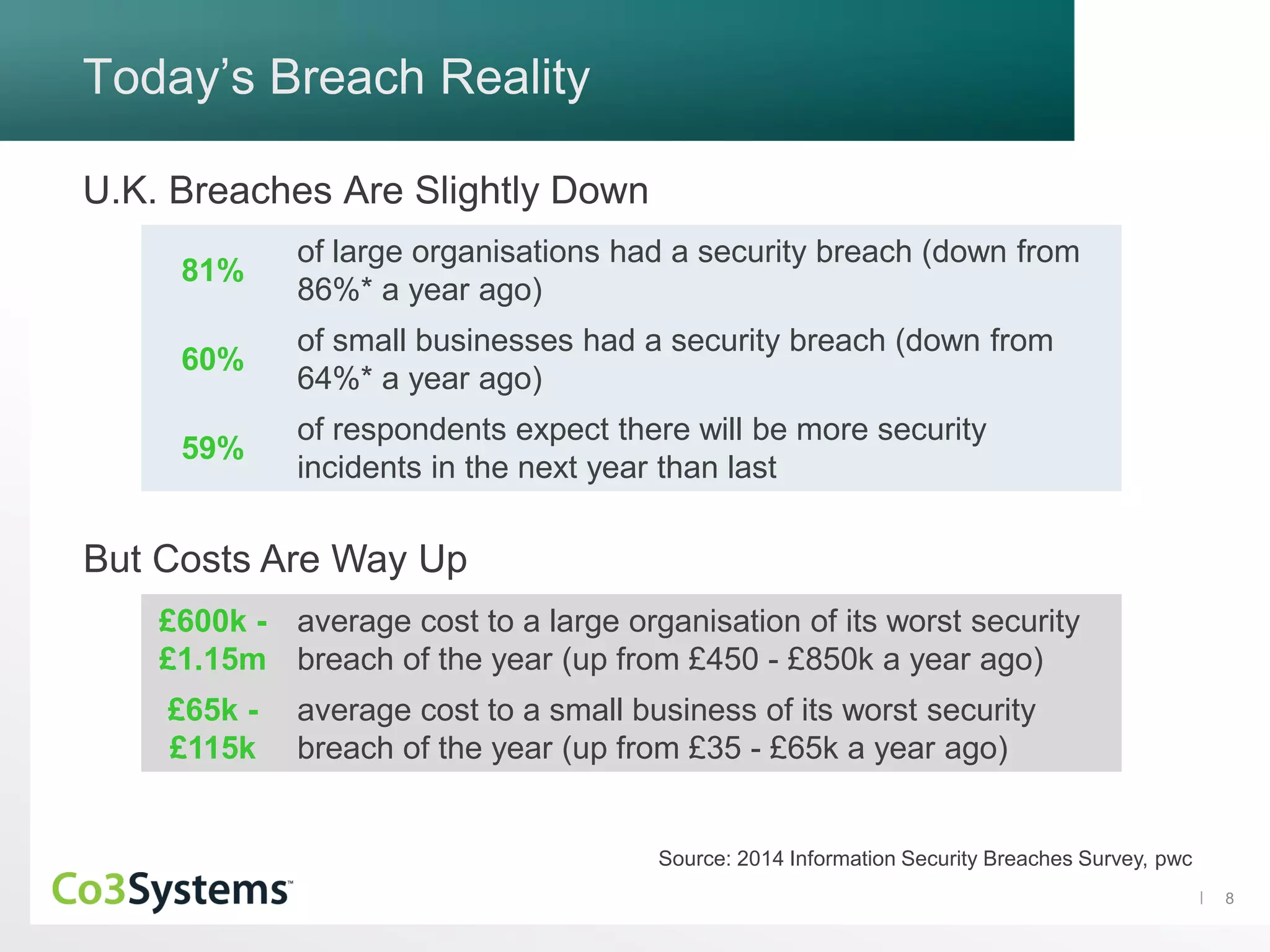
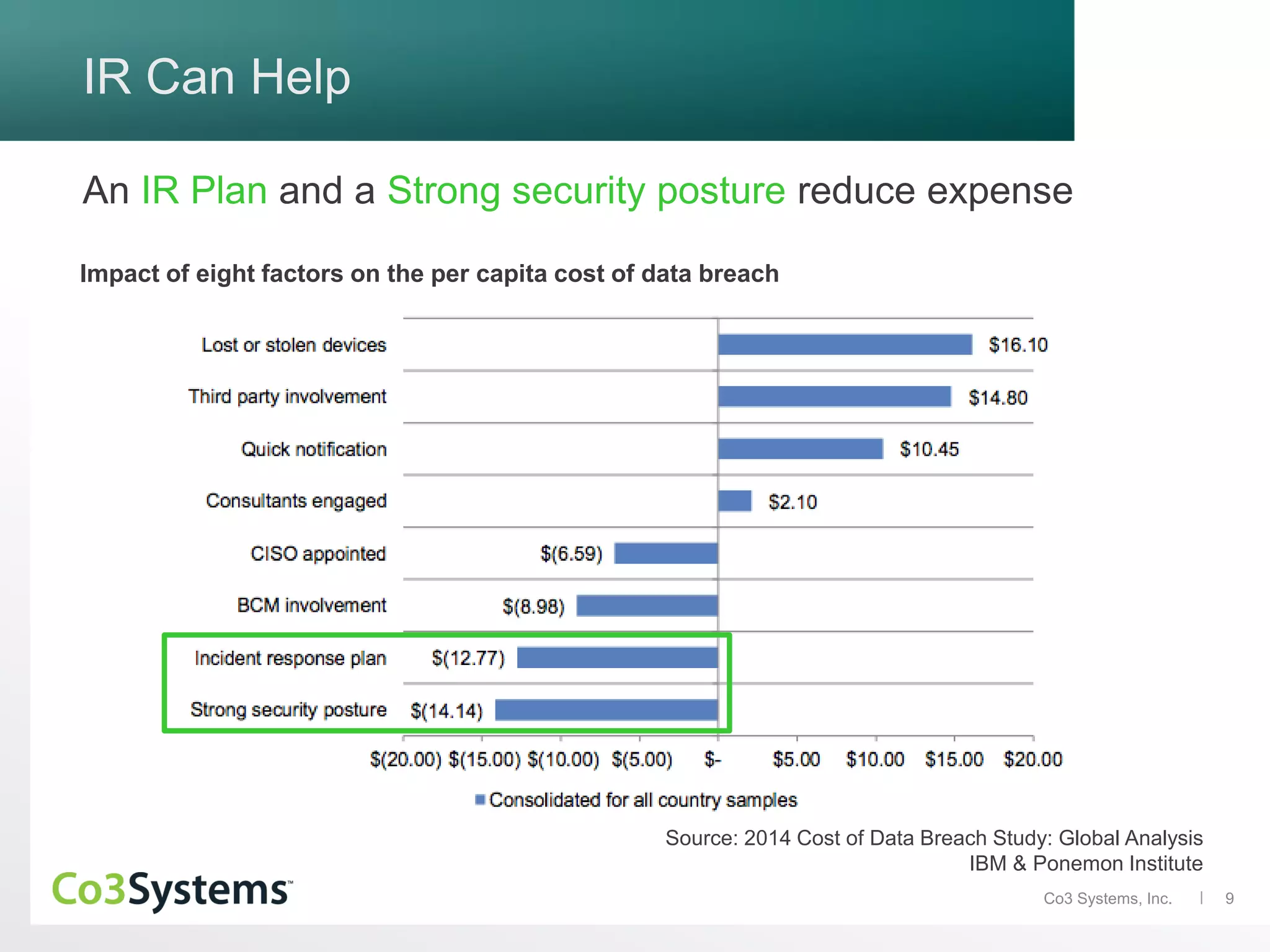
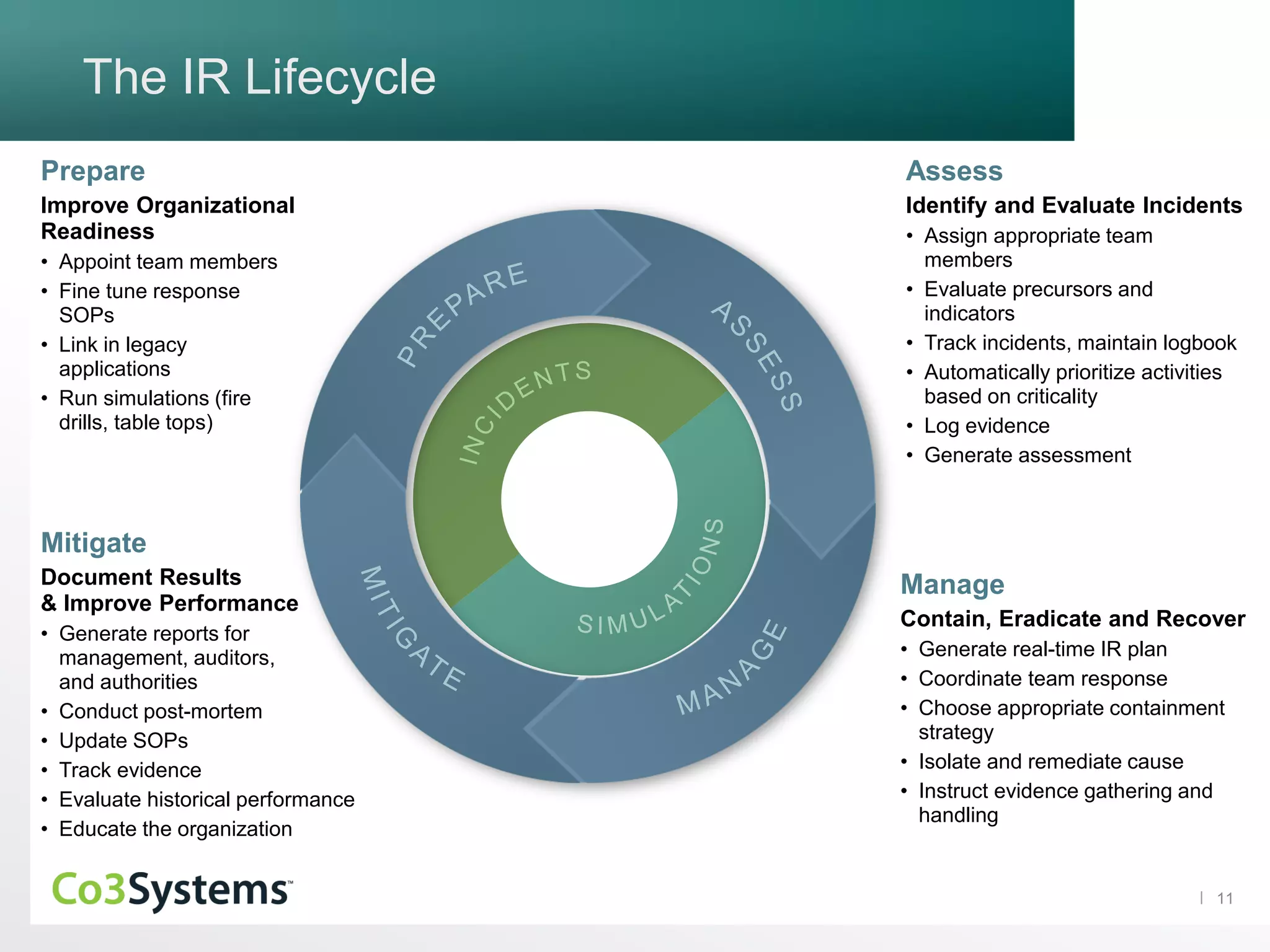
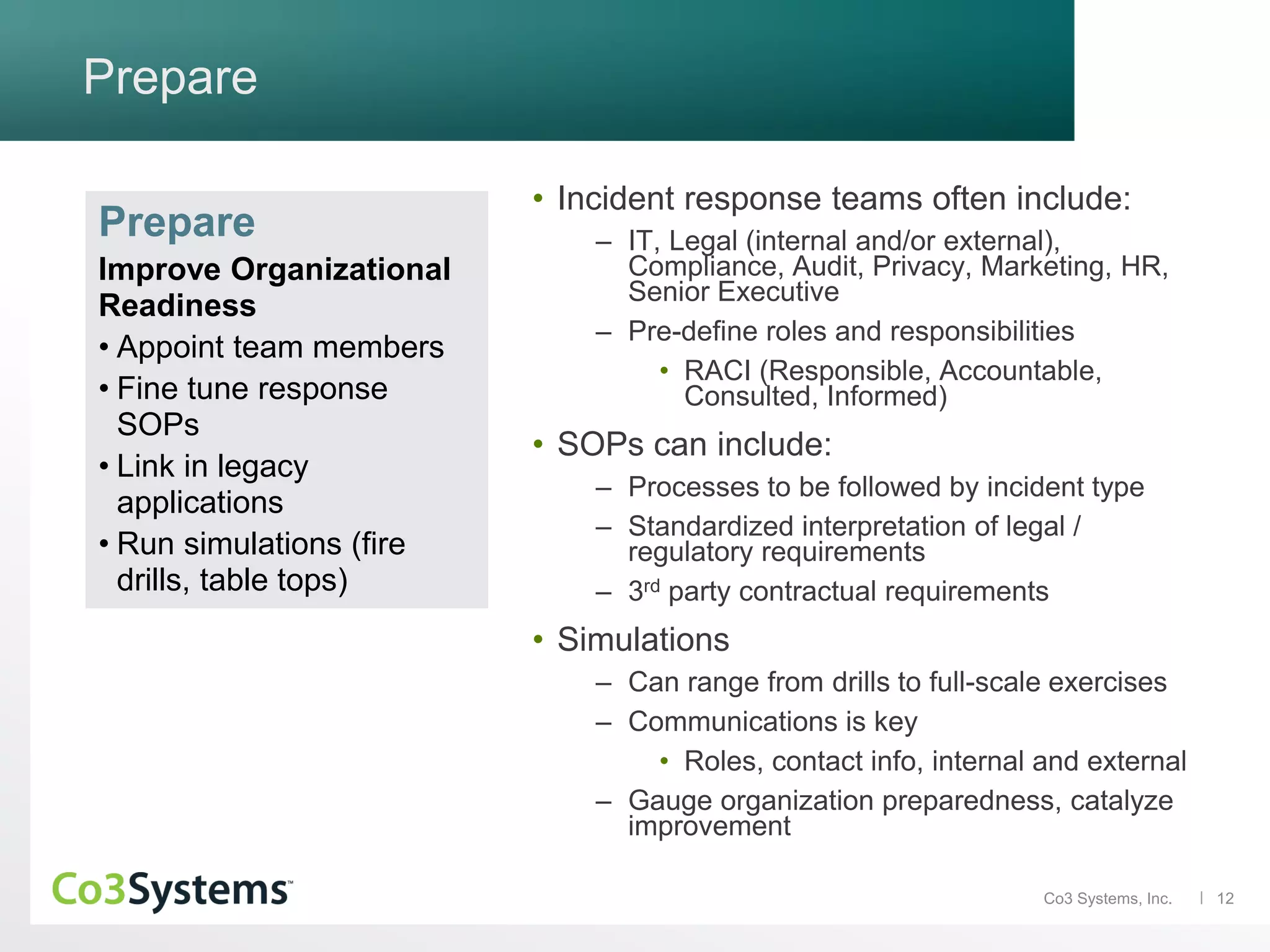
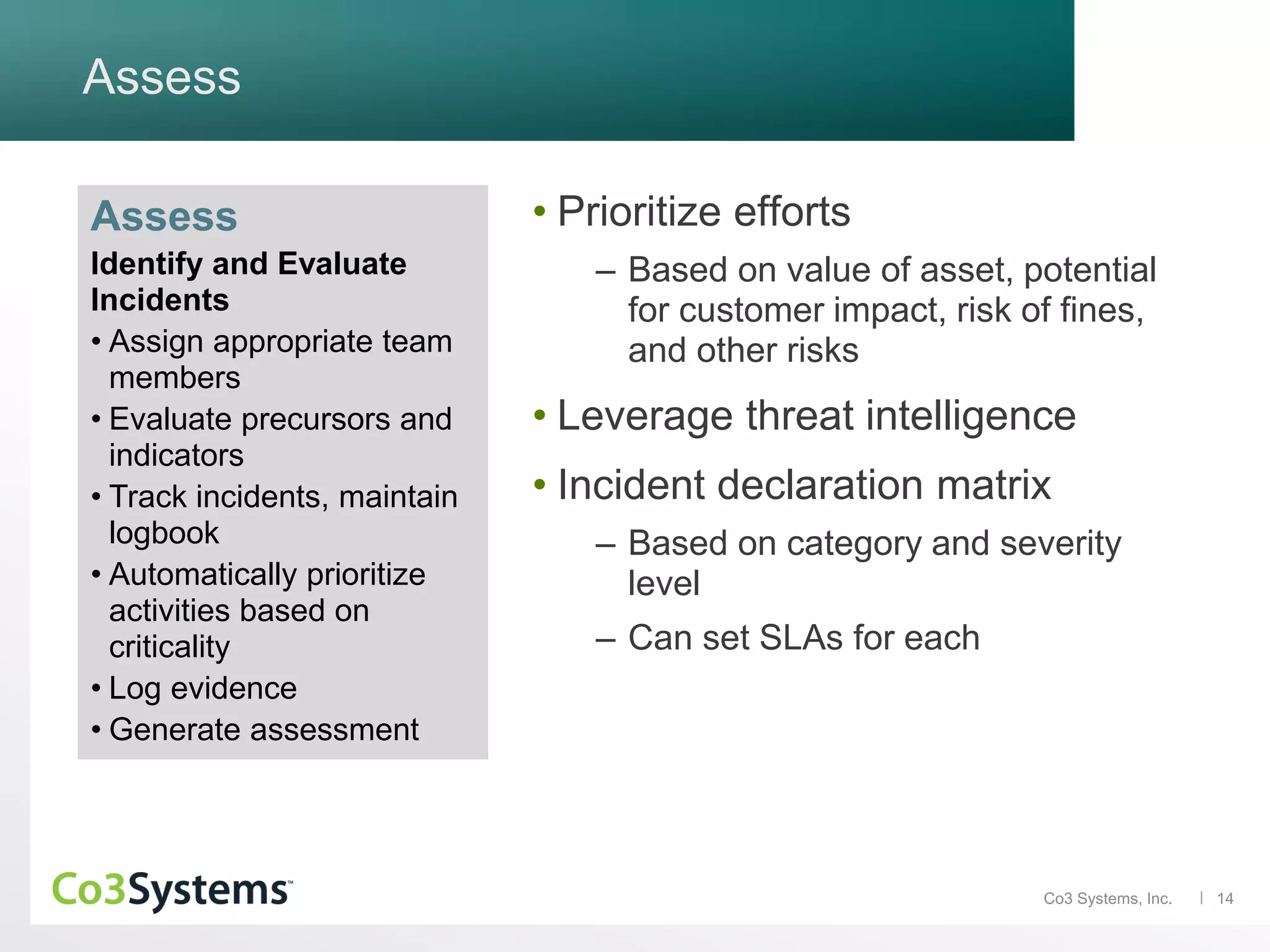
The document discusses the significance of co3 systems in enhancing incident response planning and reducing the financial impact of data breaches. It highlights the current breach reality, indicating that while breaches among large organizations have decreased slightly, their costs have risen significantly. The document also outlines the incident response lifecycle and emphasizes the importance of preparation, assessment, management, and mitigation in incident response strategies.