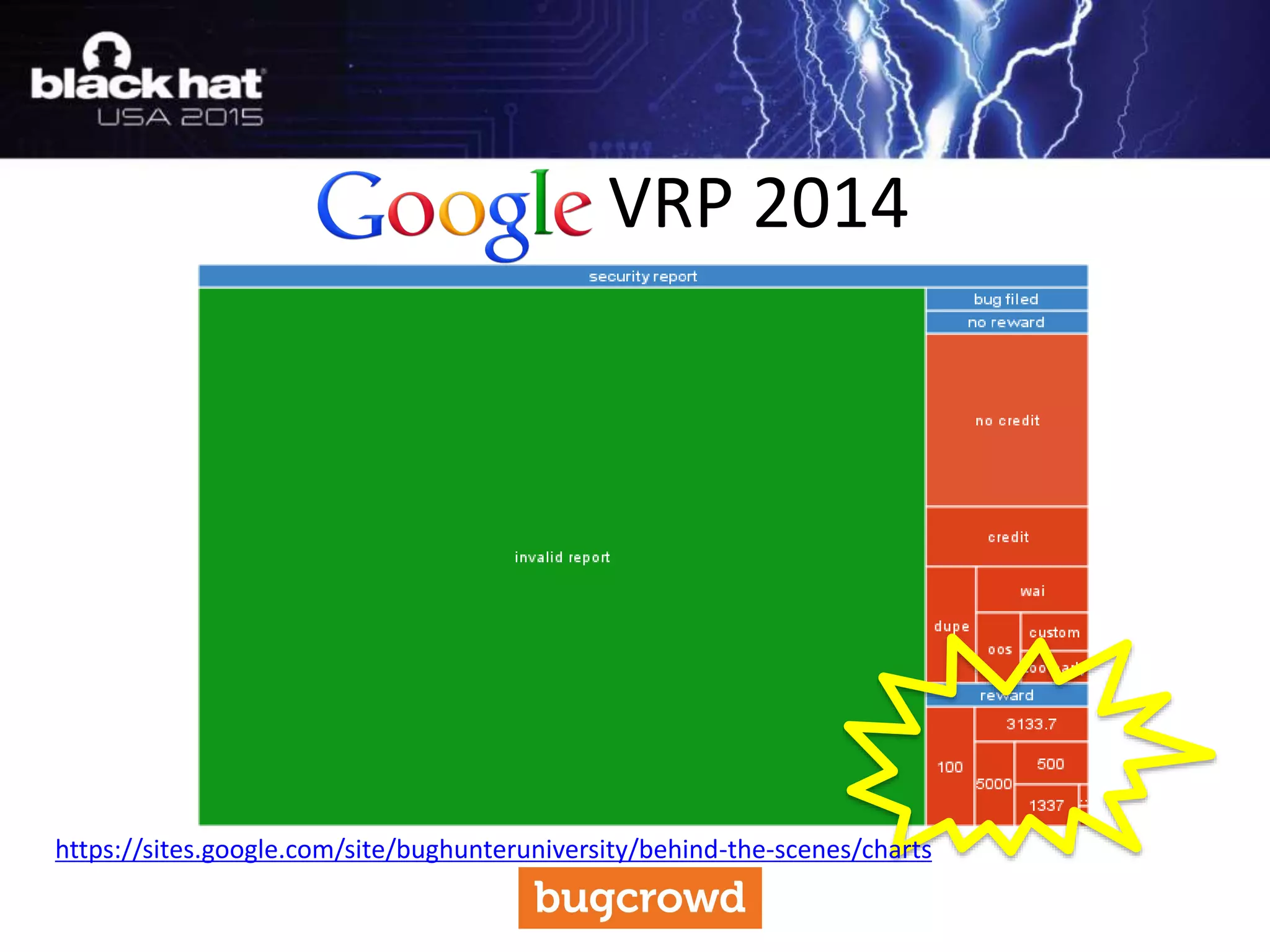
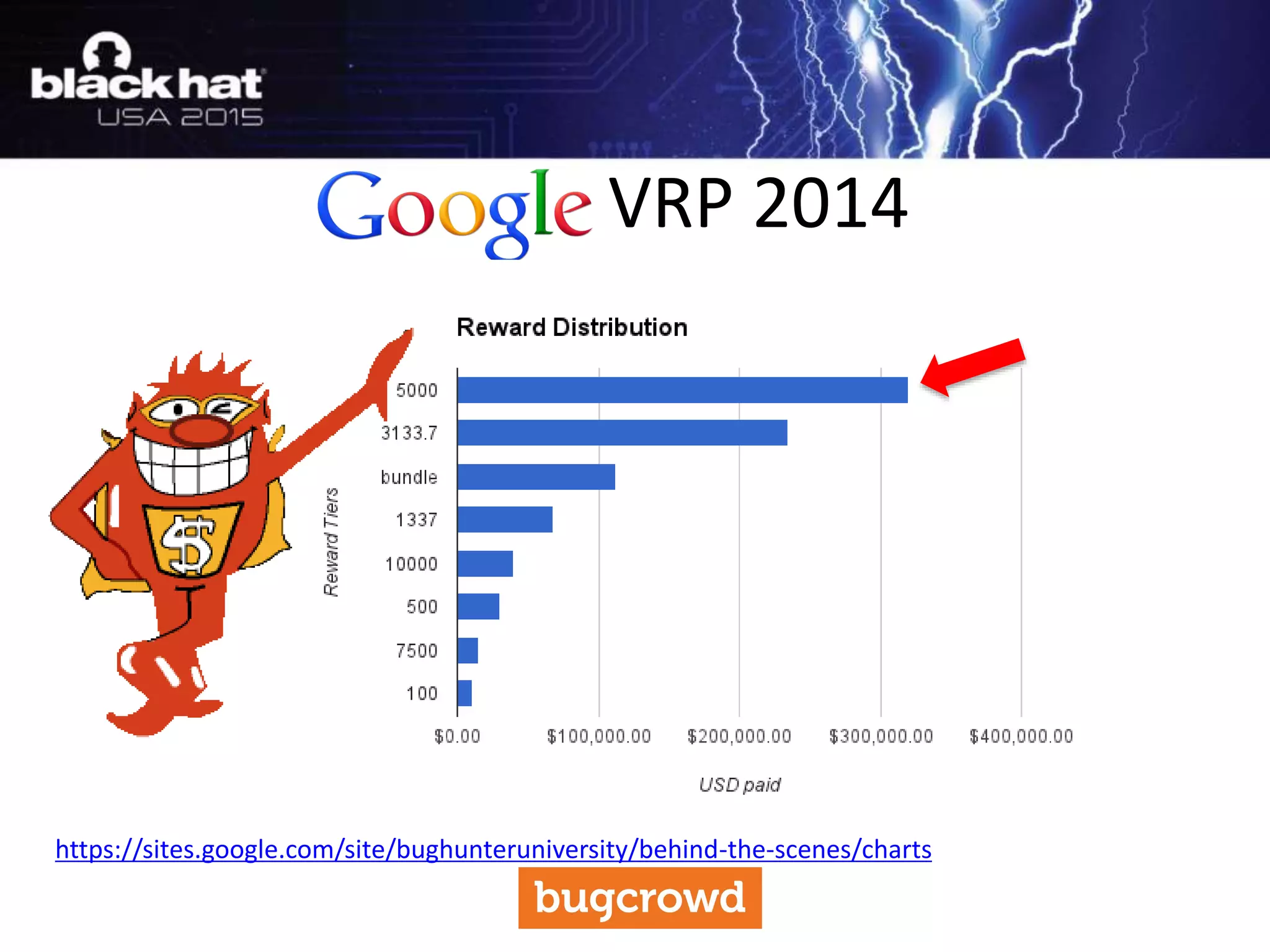
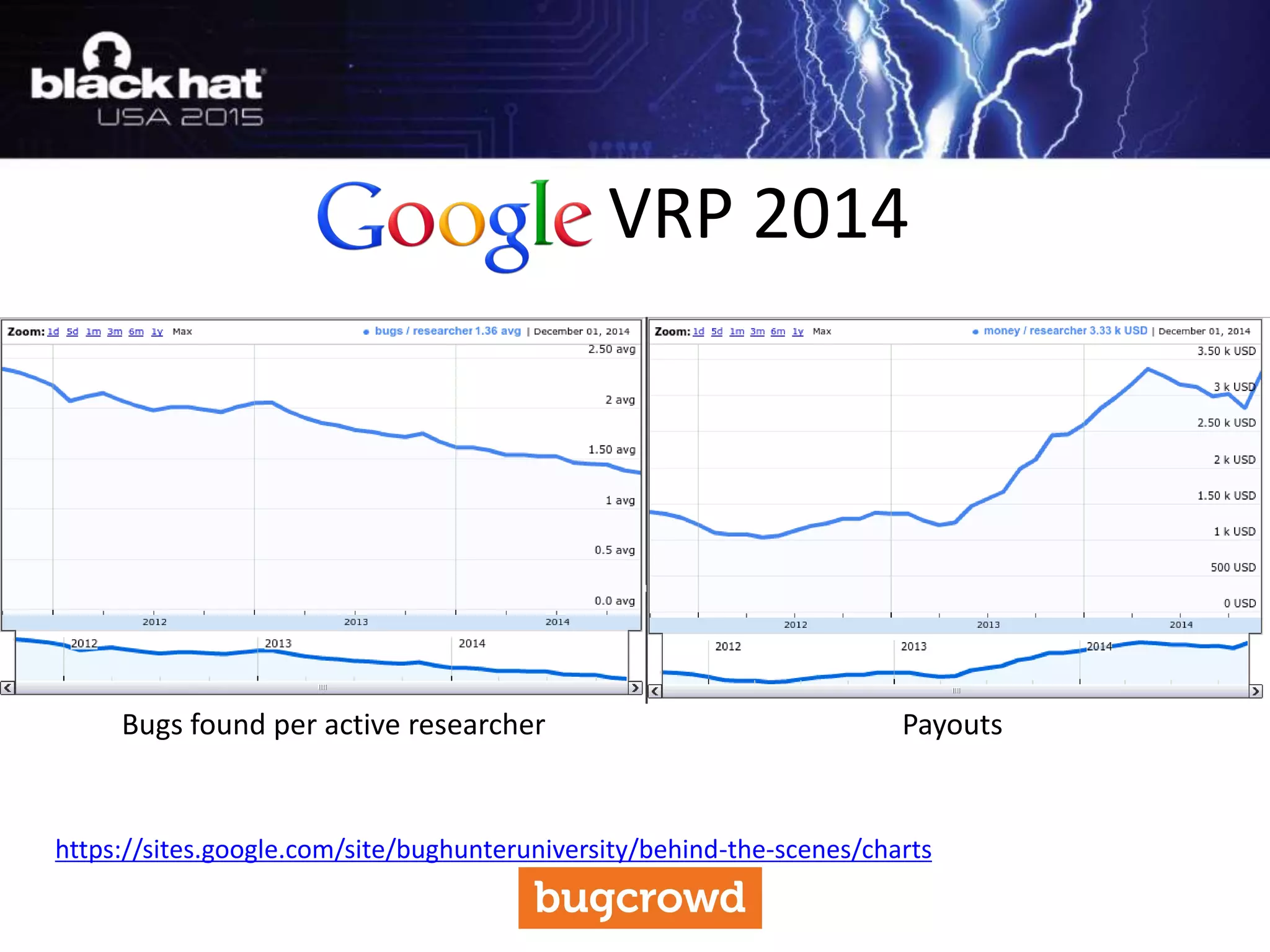
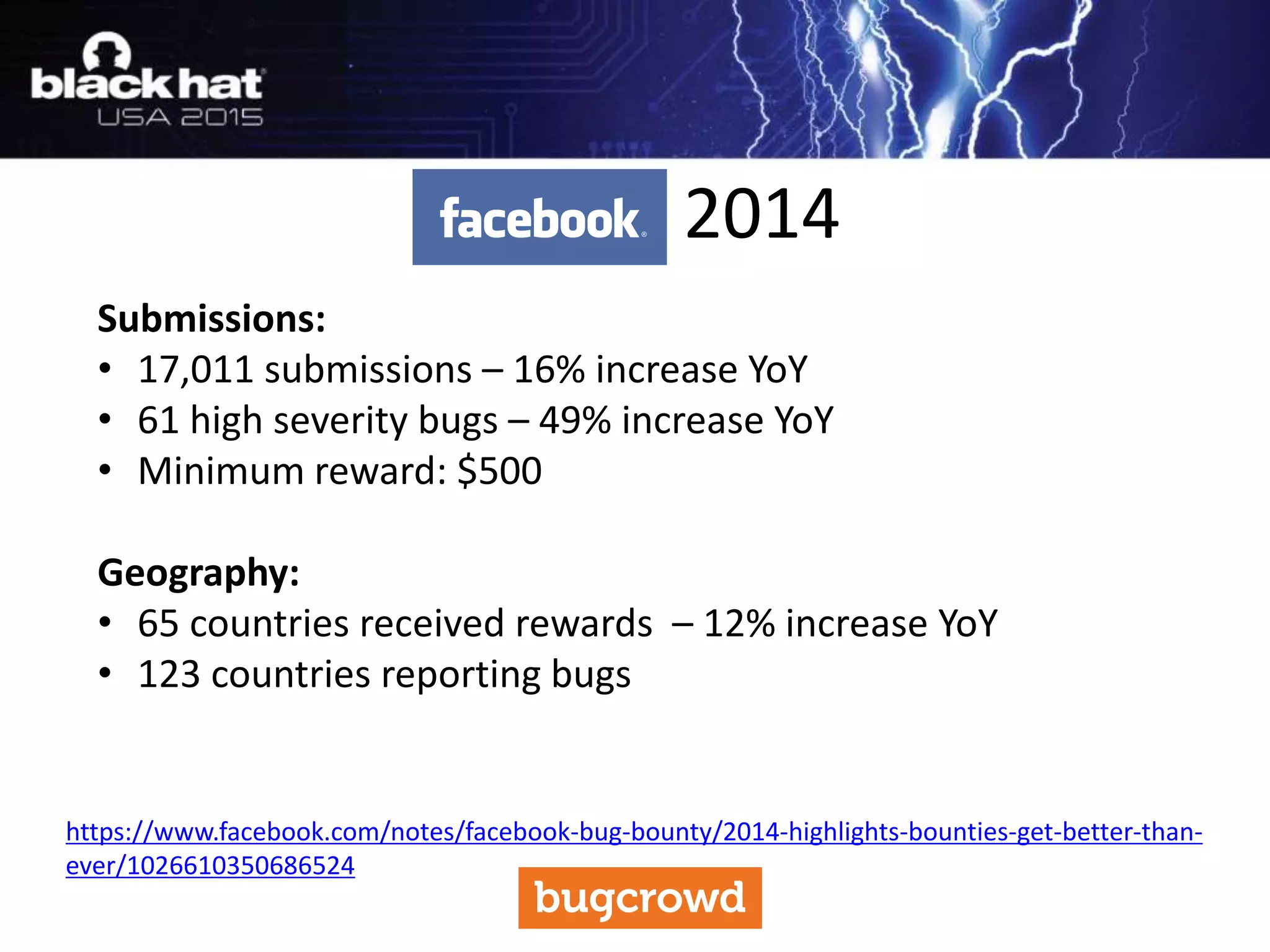
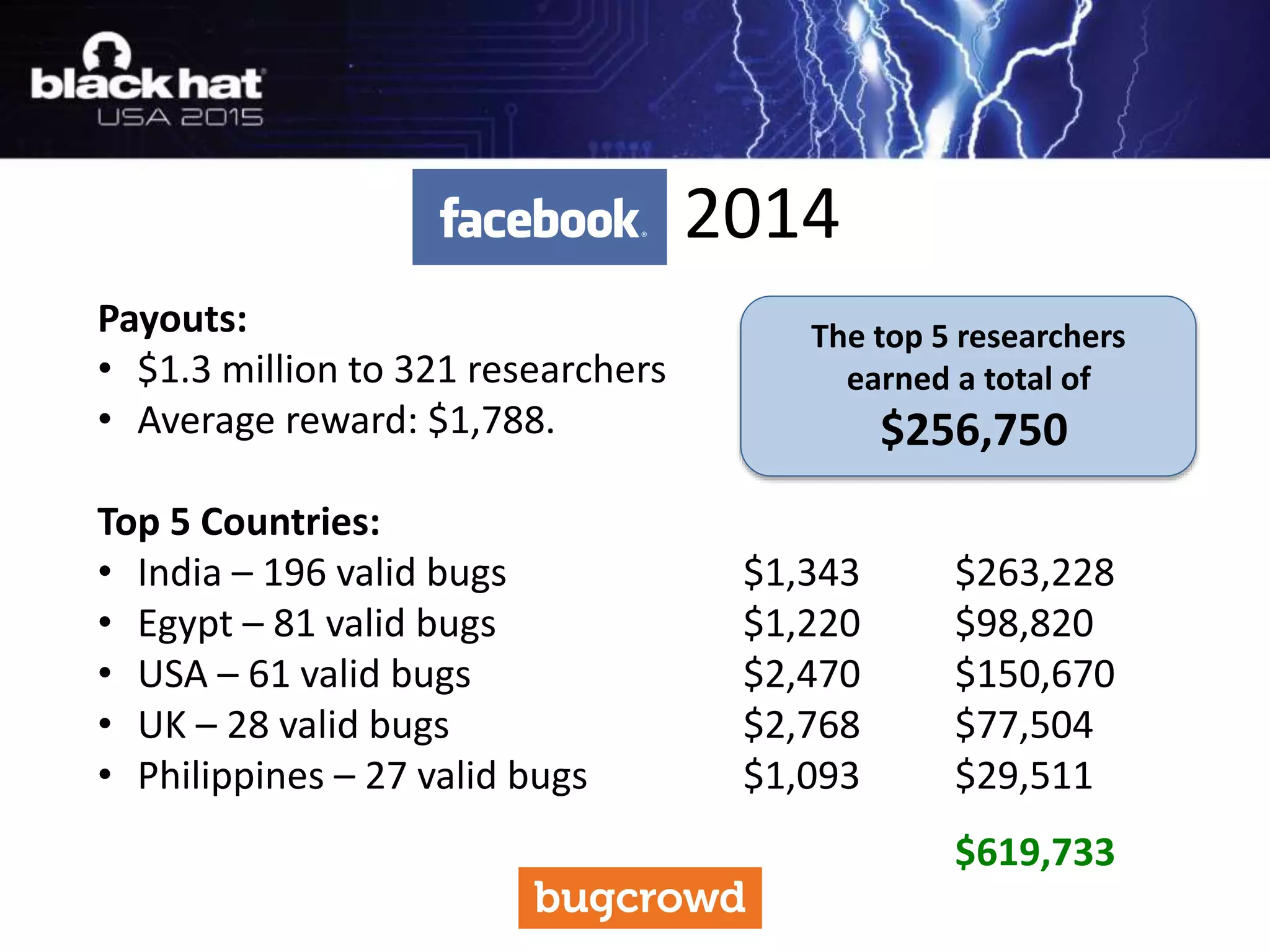
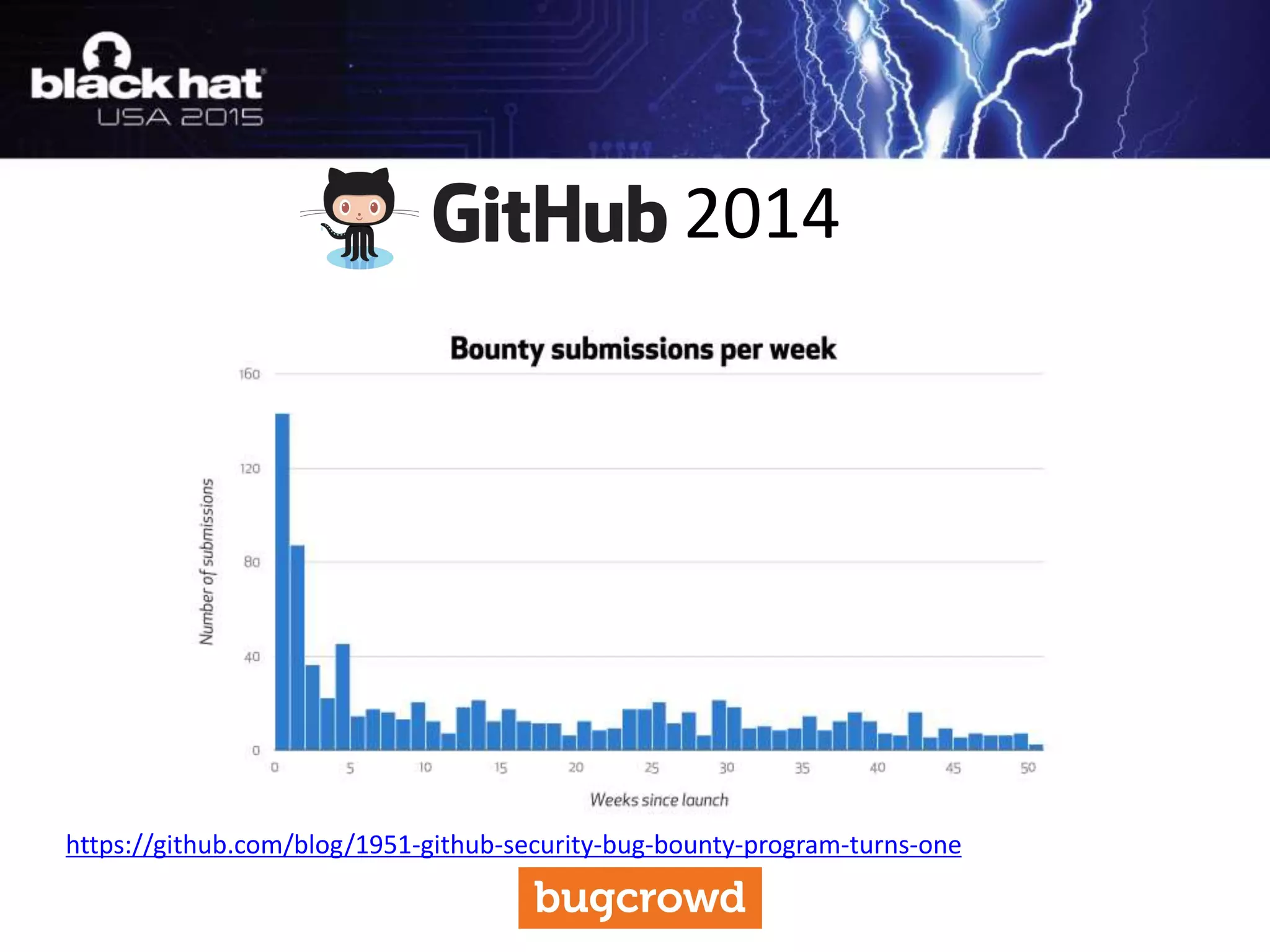
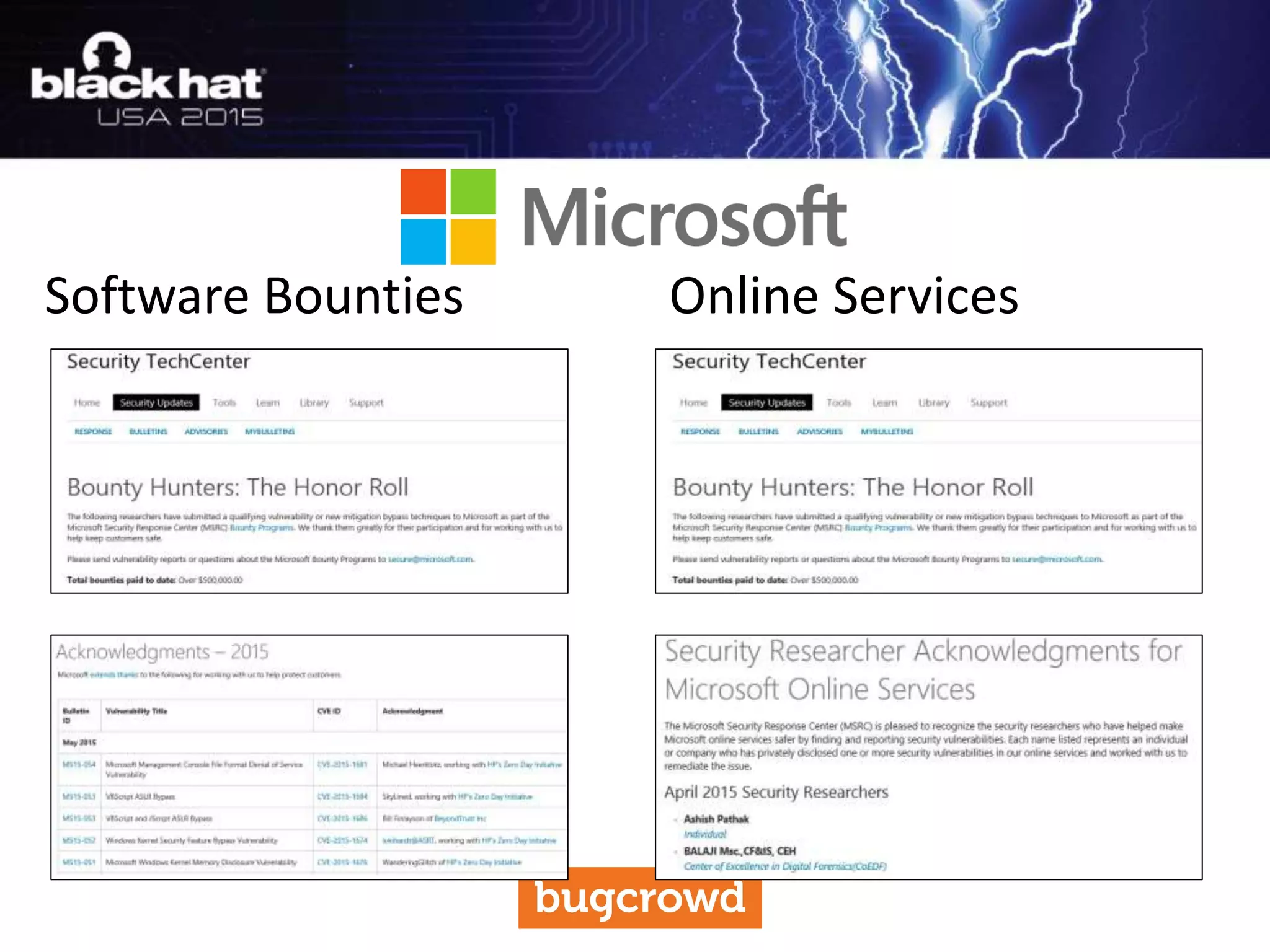
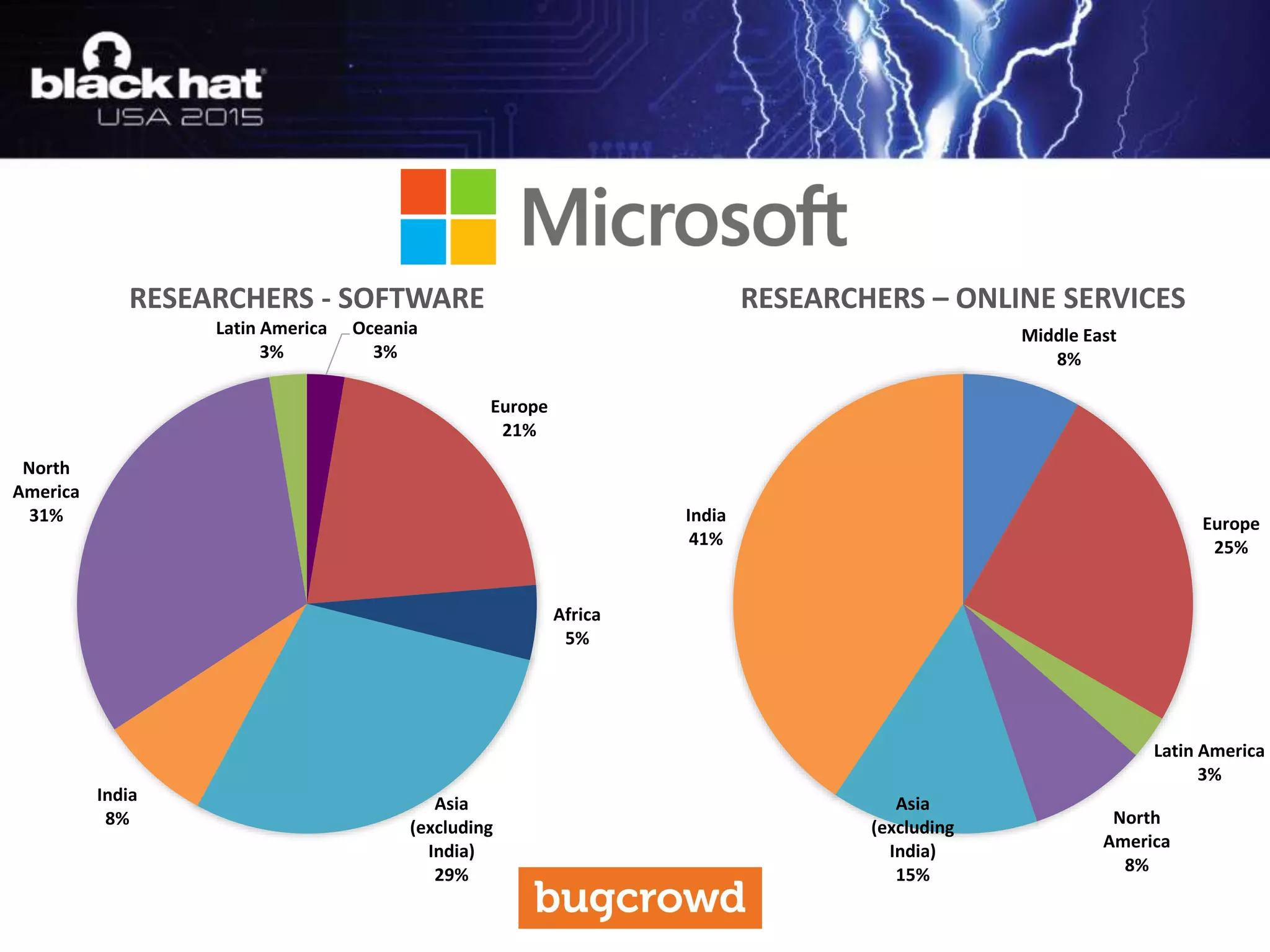
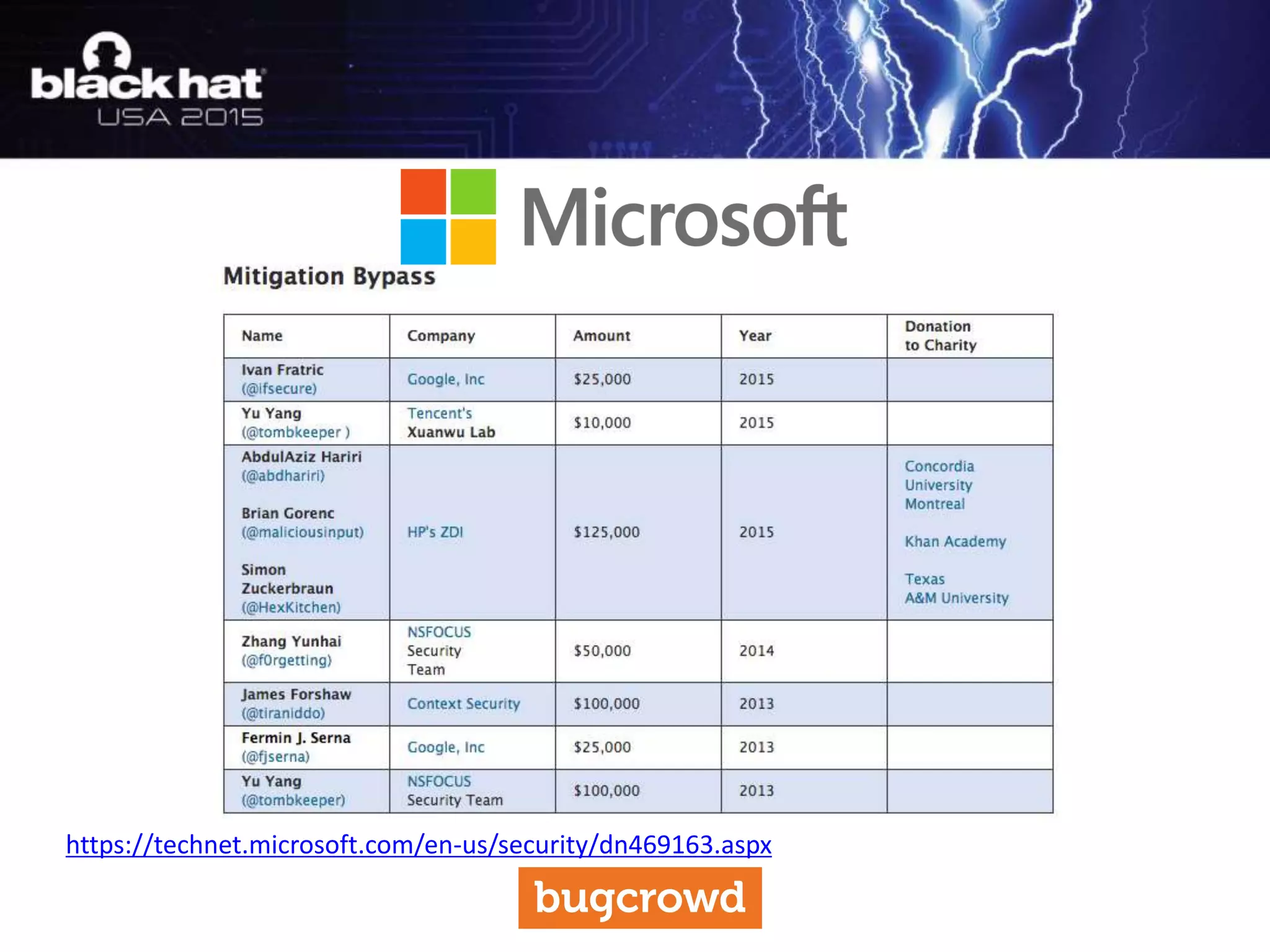
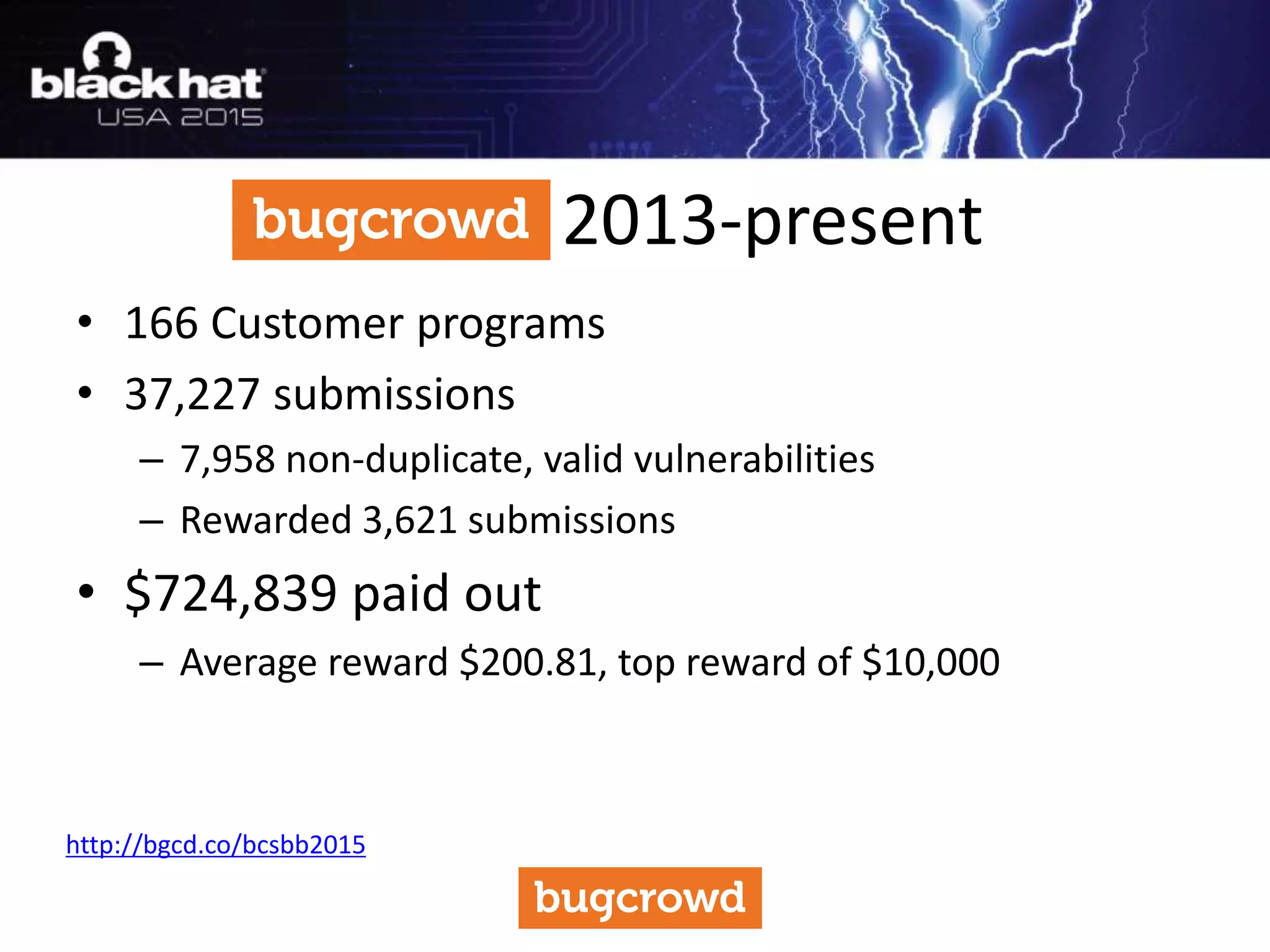
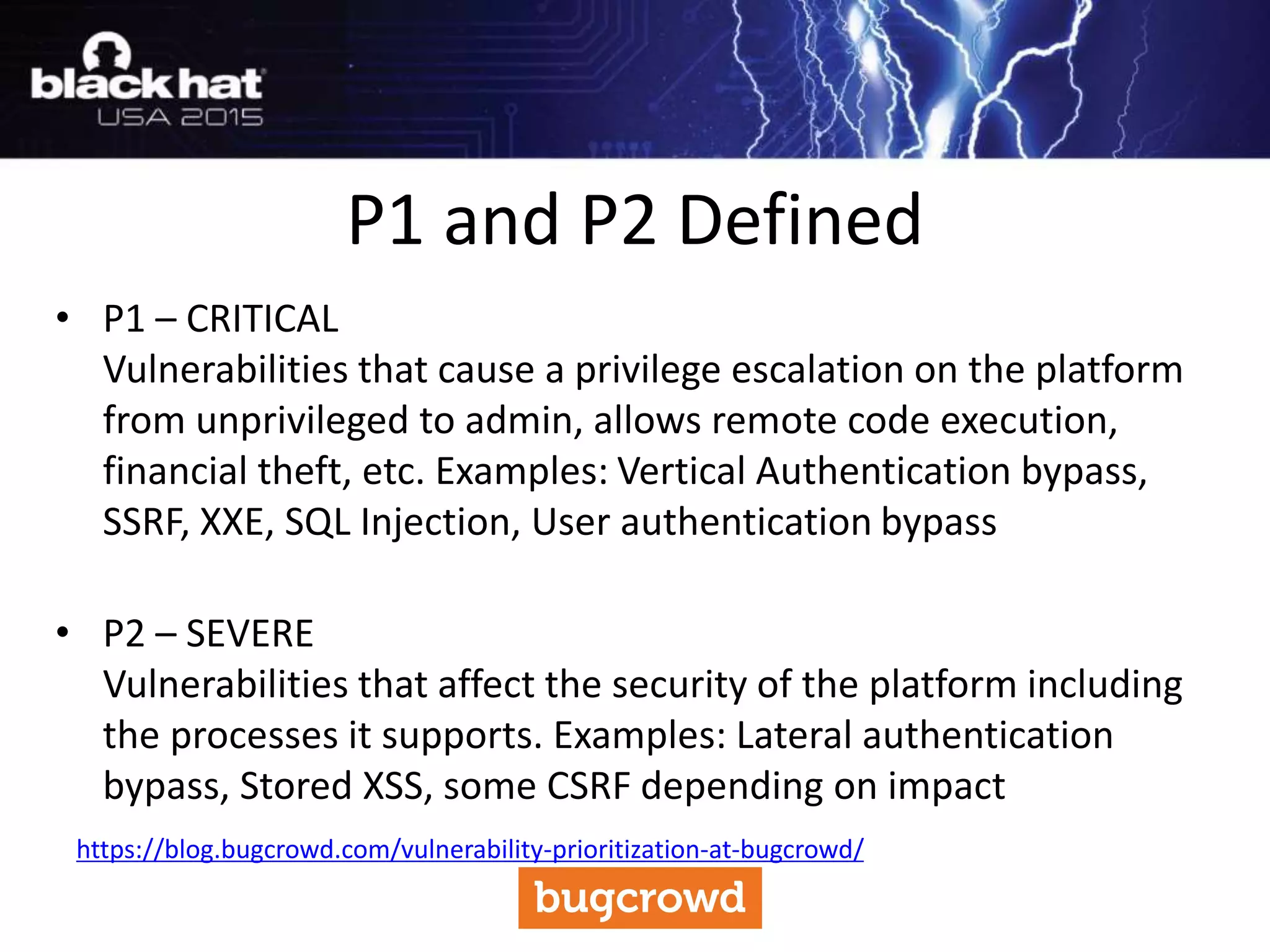
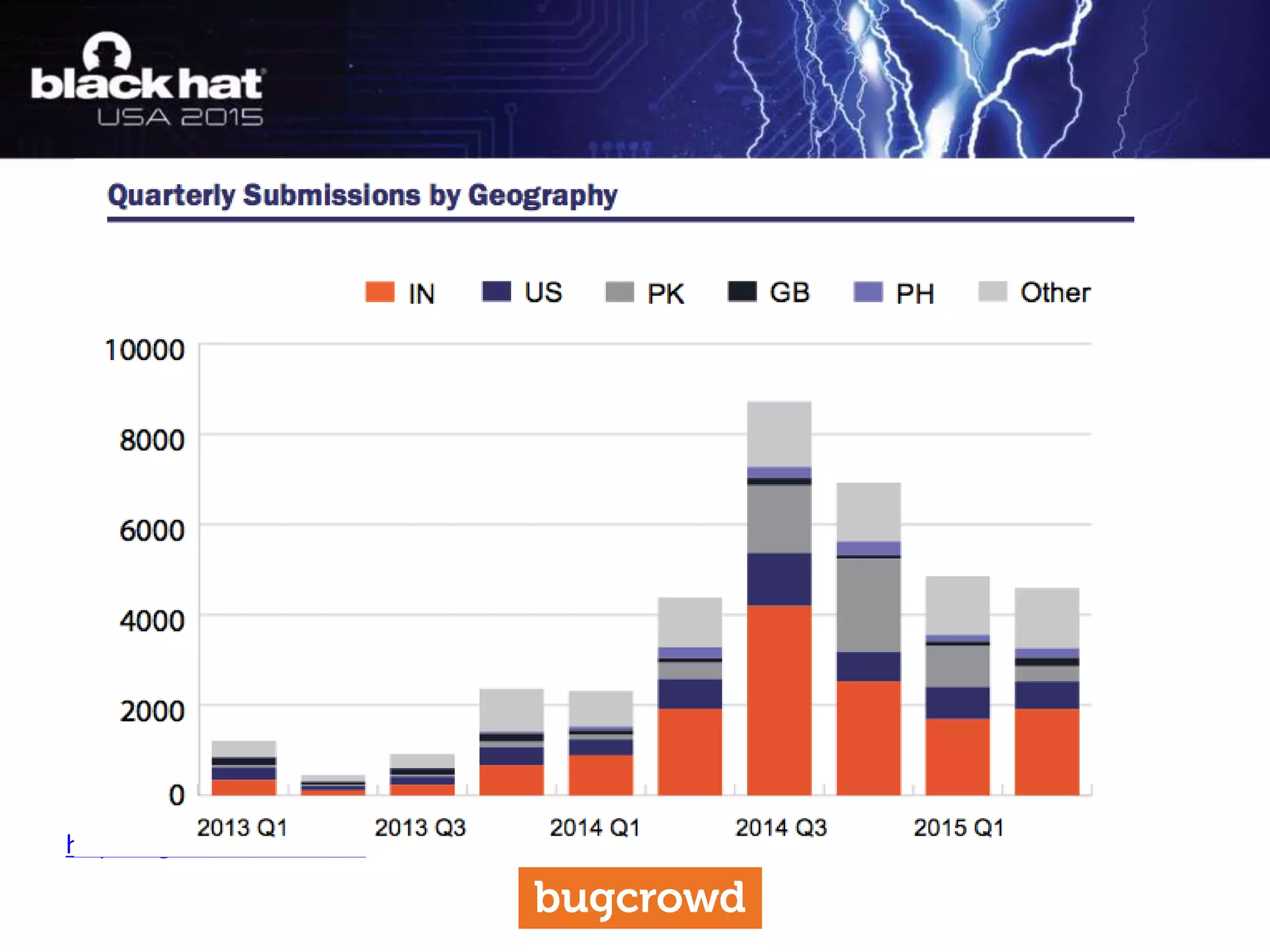
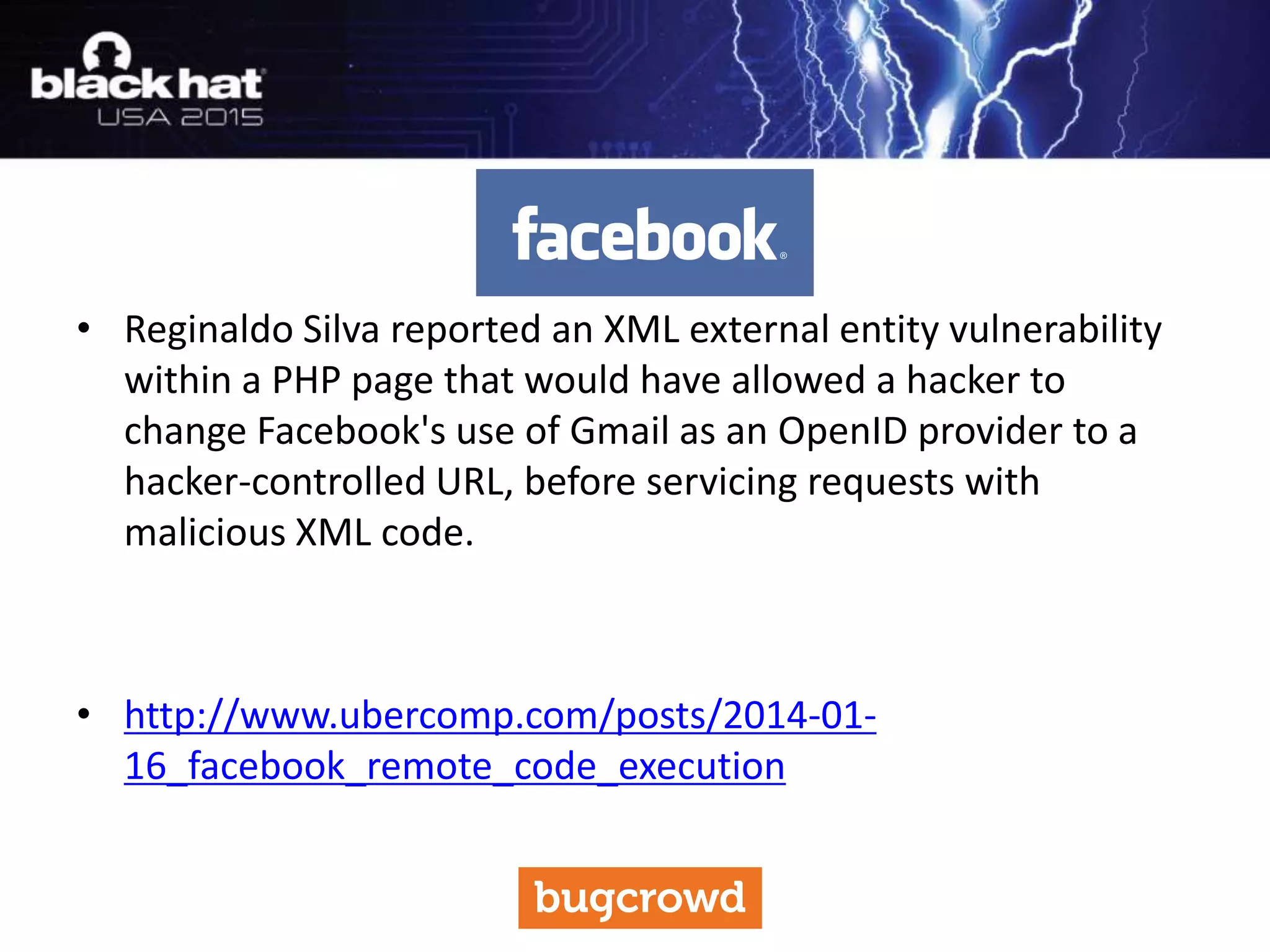
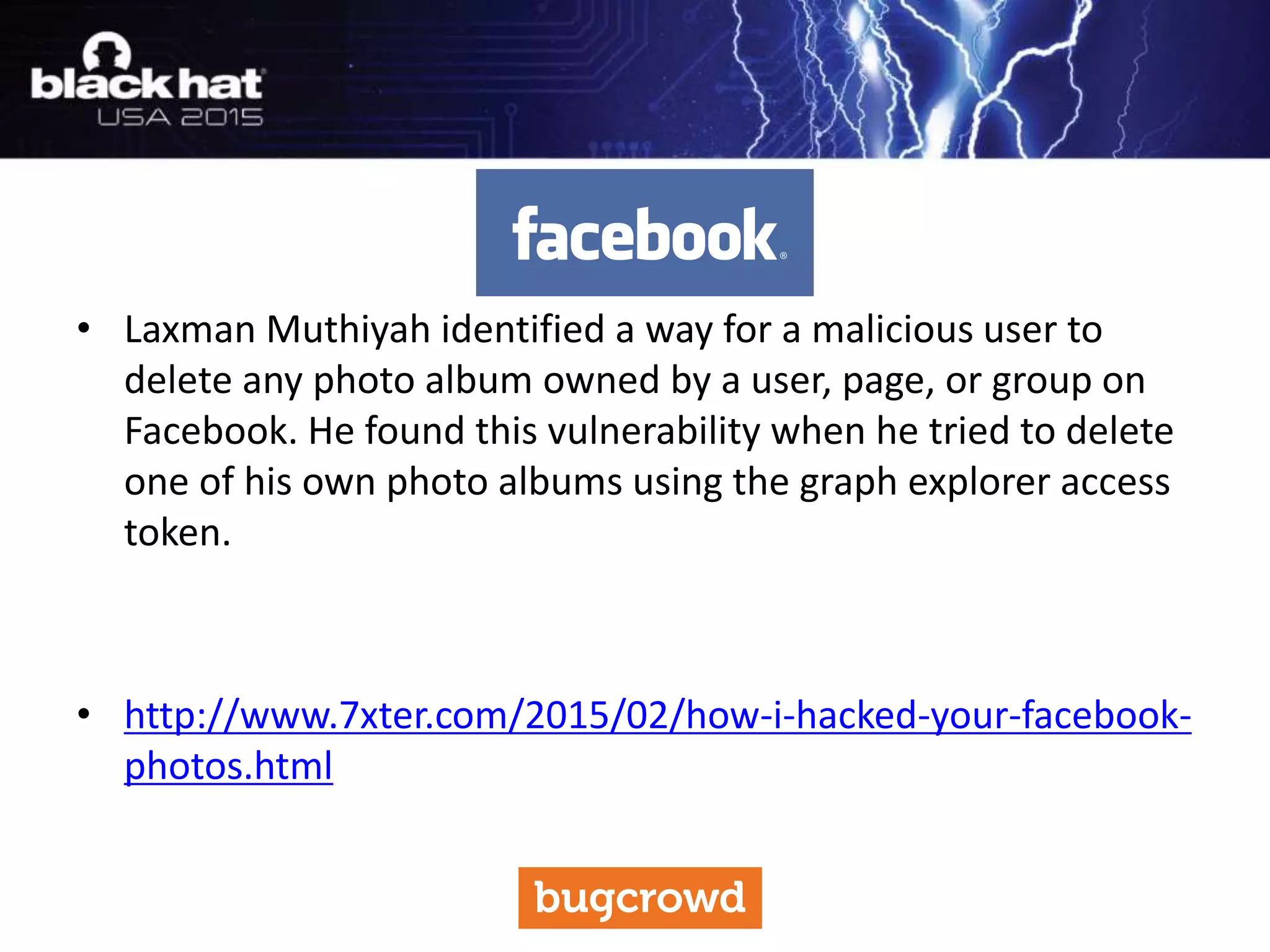
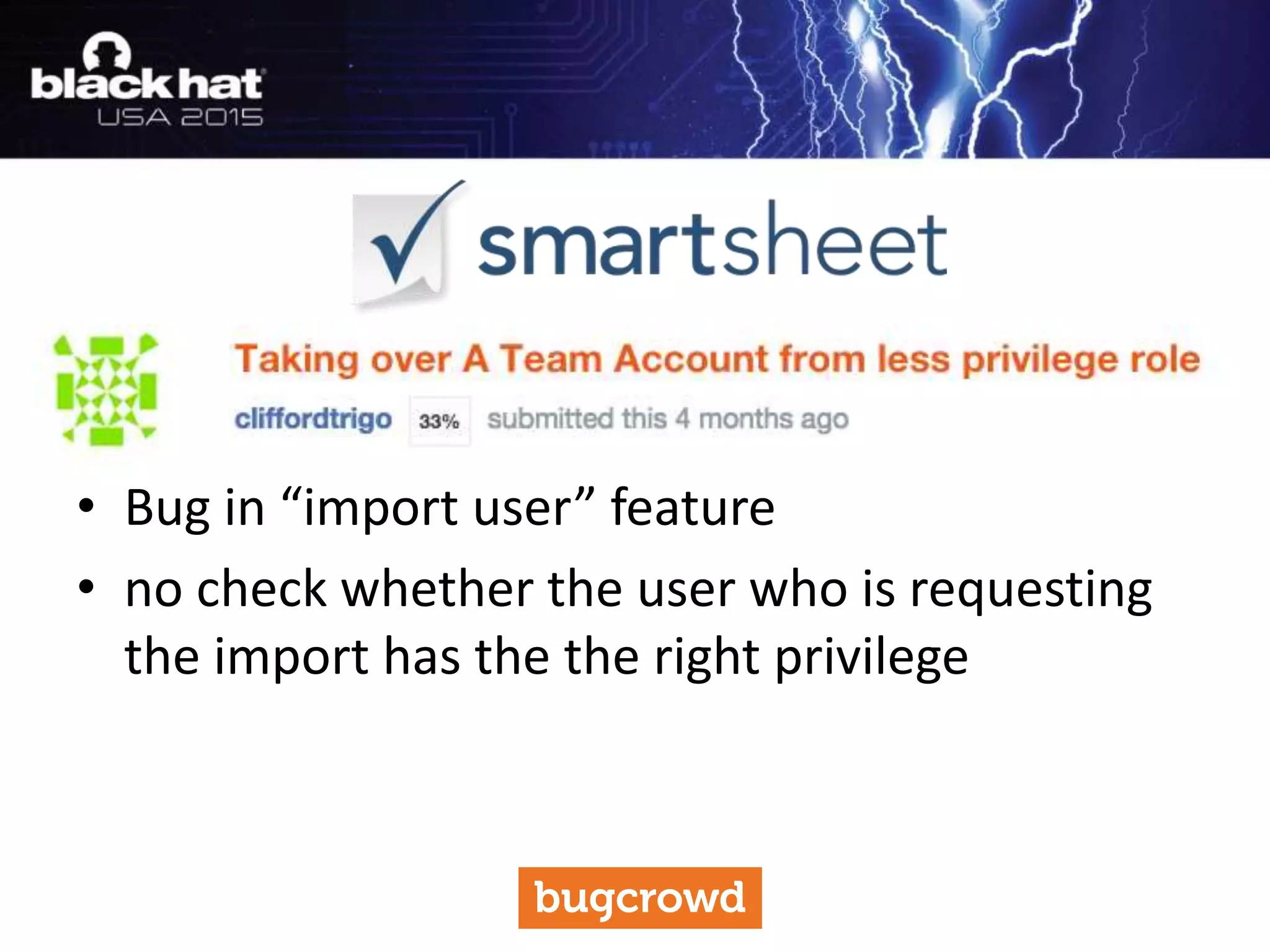
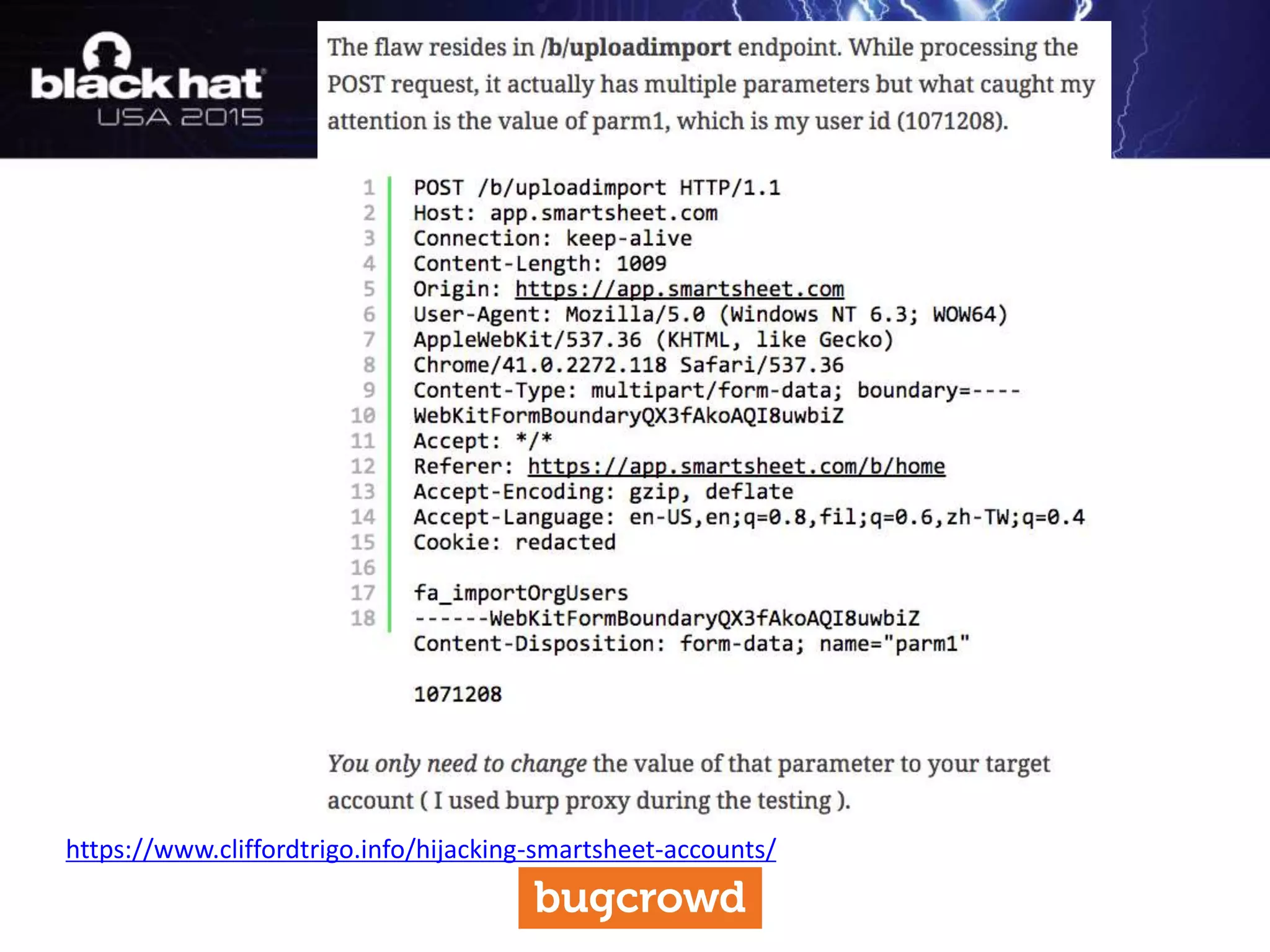
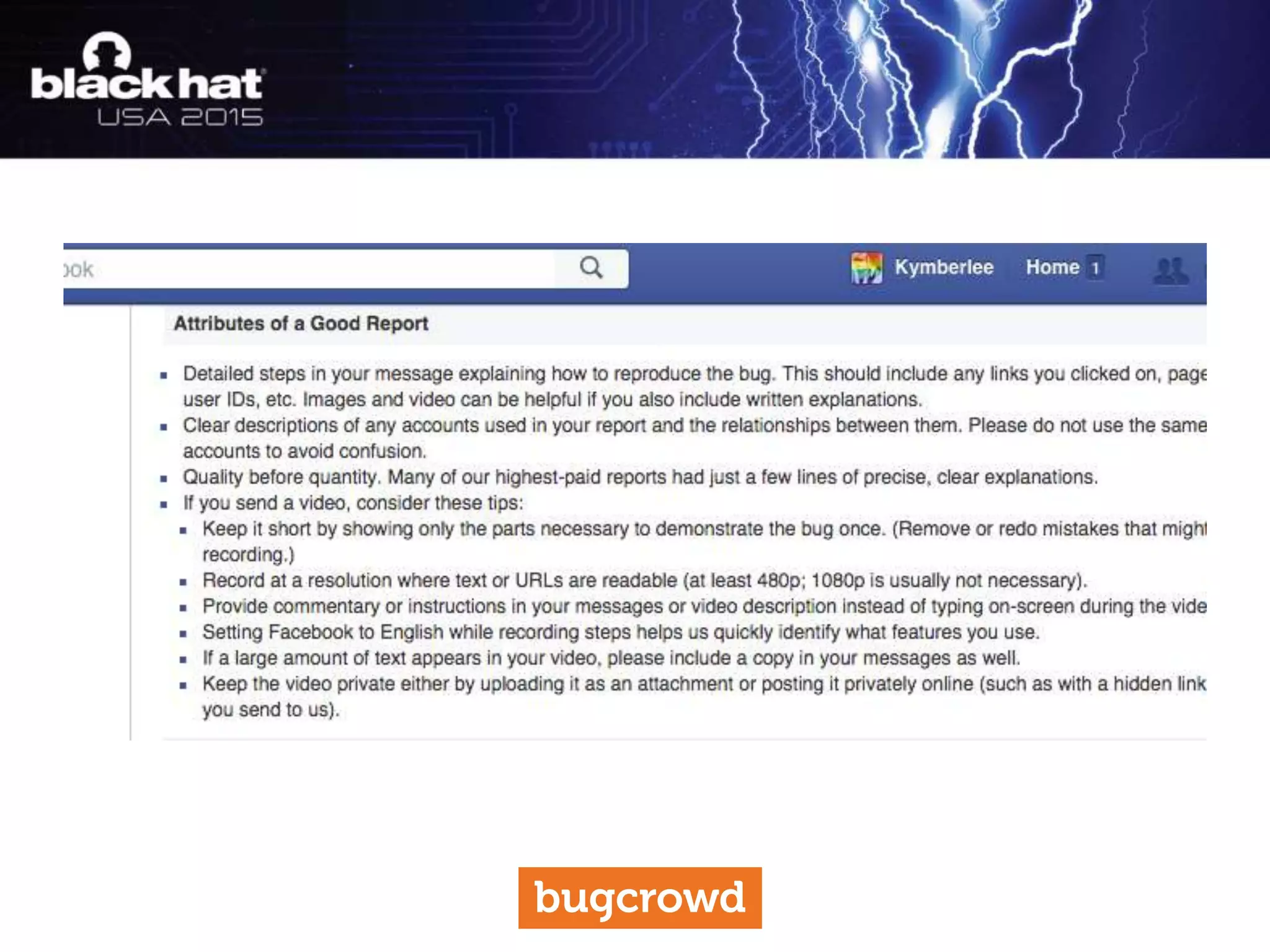
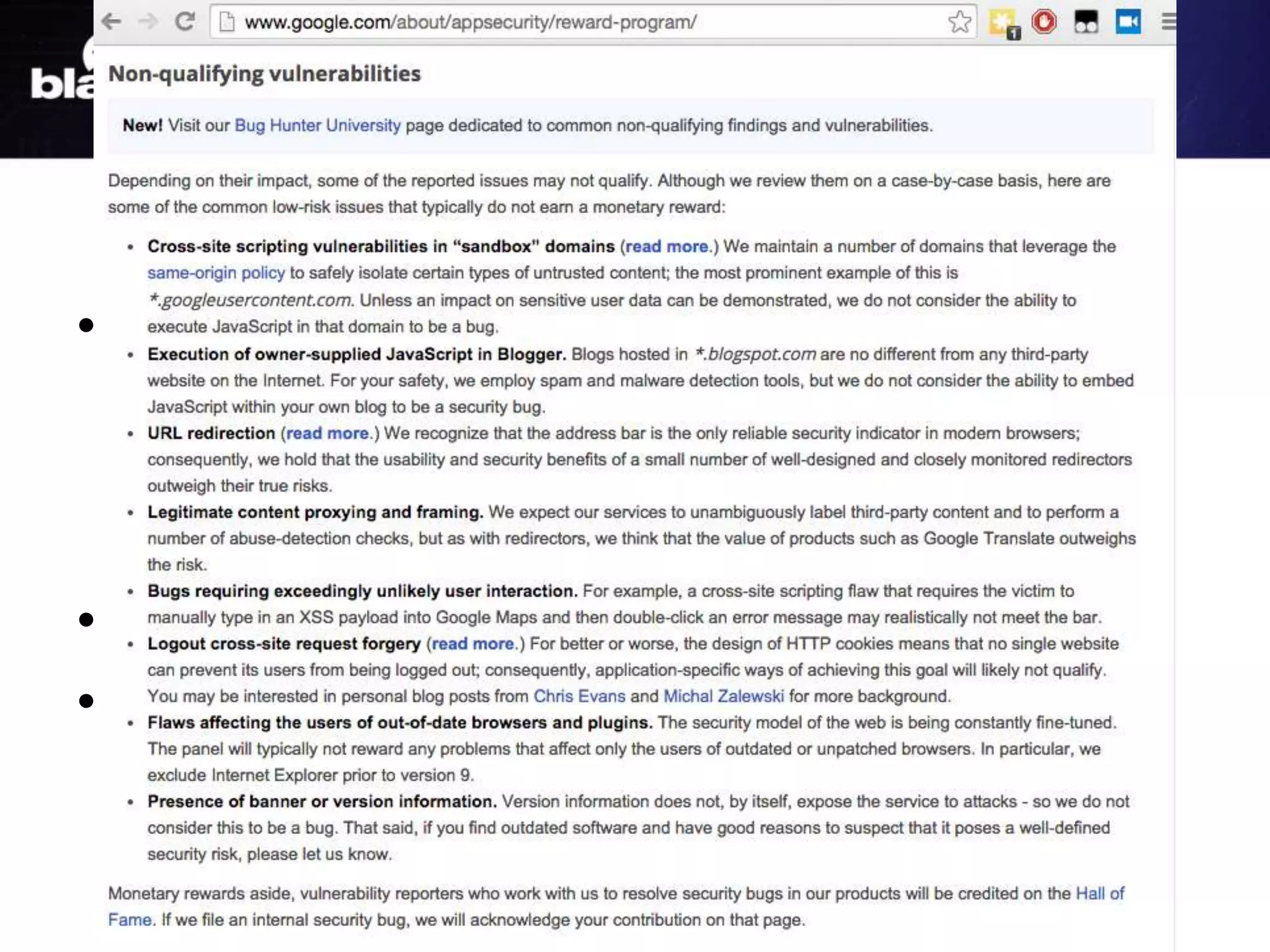
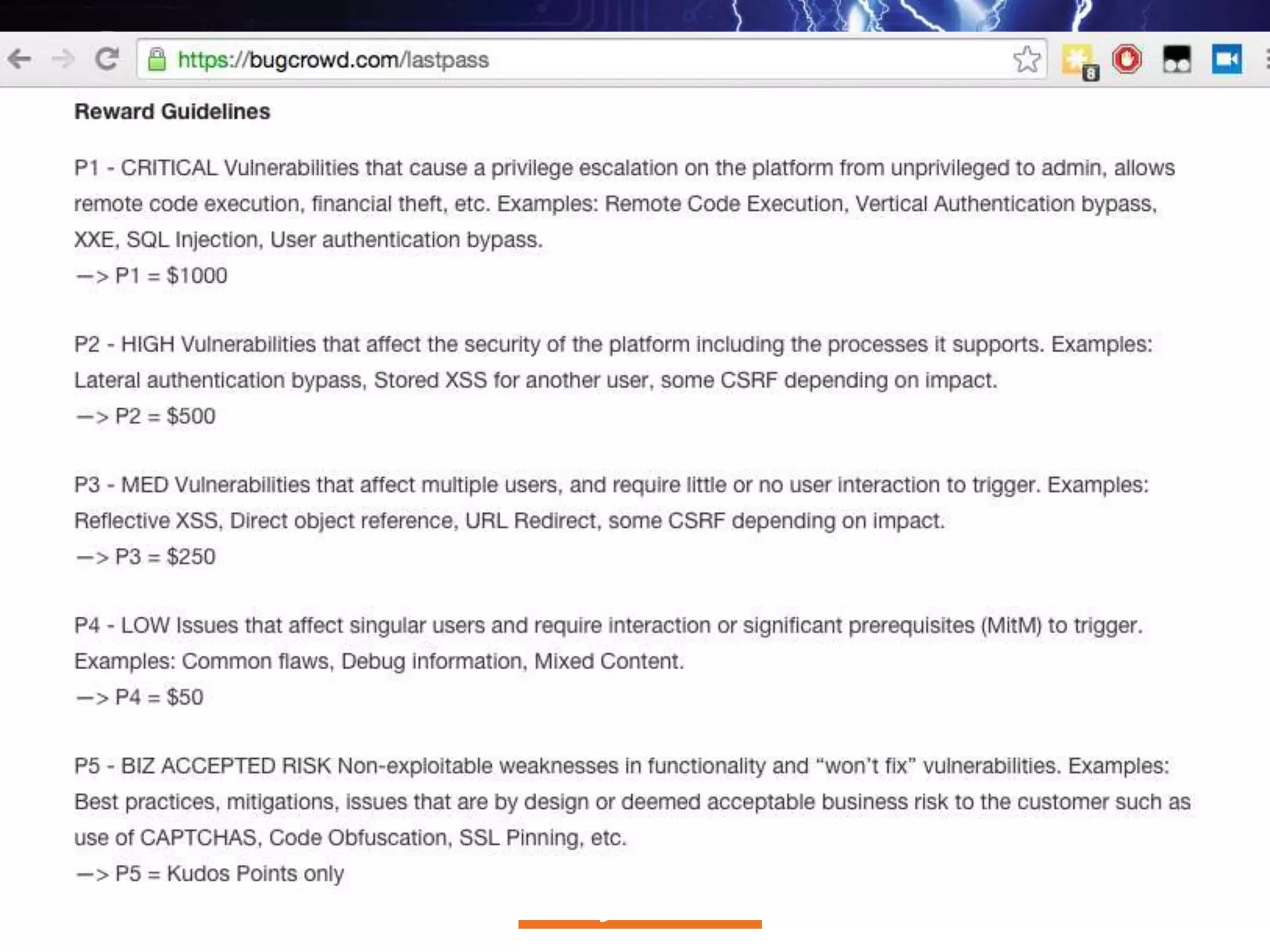
The document discusses critical vulnerabilities and bug bounty programs led by Kymberlee Price from Bugcrowd, emphasizing the significance of such programs in enhancing application security. It highlights the growth in submissions and payouts from bug researchers, along with the identification of high-priority vulnerabilities in various organizations worldwide. The presentation also outlines best practices for managing bug bounty programs, including documentation, engagement, and rewarding researchers effectively.