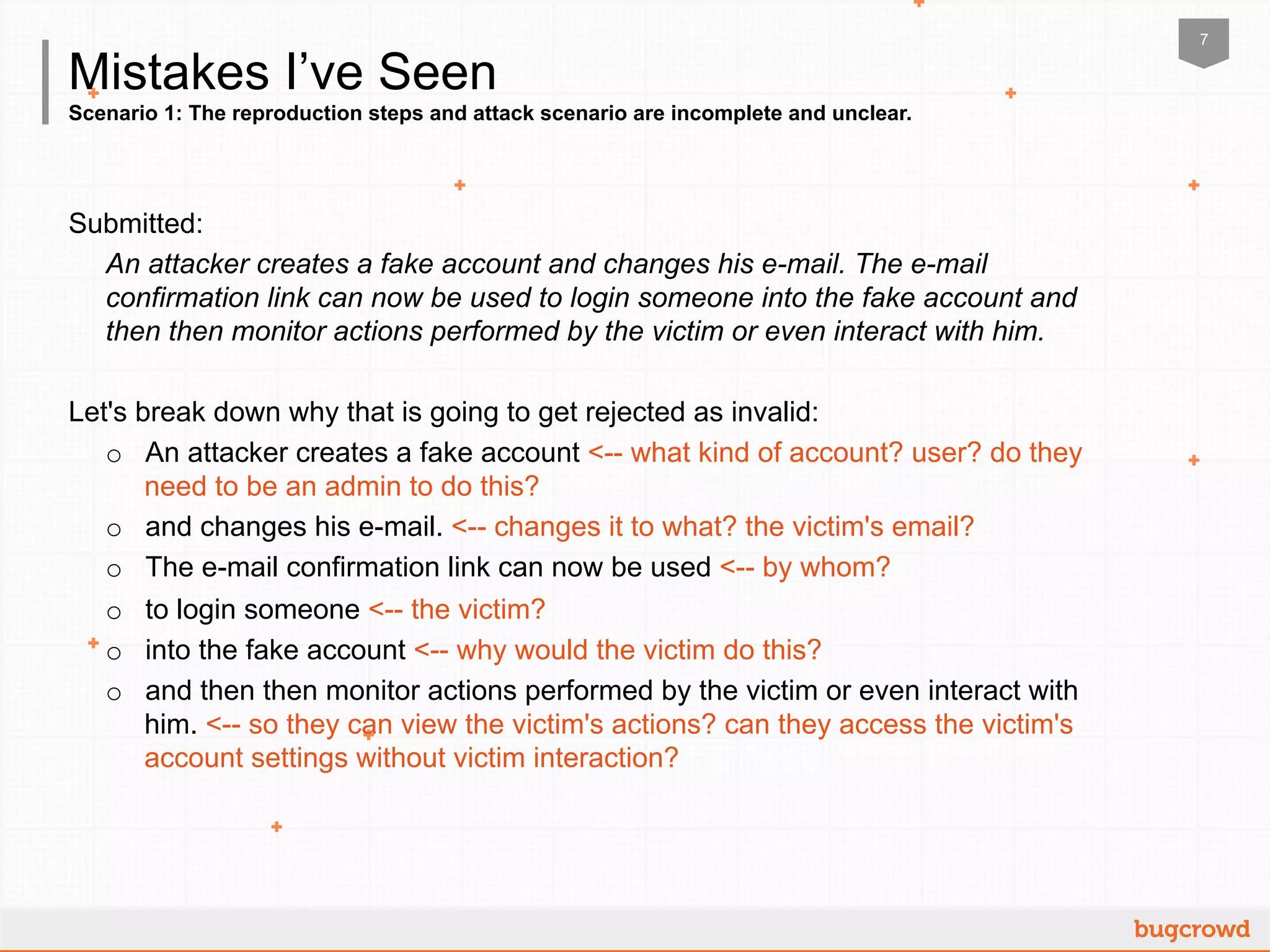
The document outlines guidelines for submitting vulnerabilities in a crowdsourced cybersecurity context to maximize payouts. Key steps include understanding the bounty brief, clearly communicating the impact of vulnerabilities using the STRIDE model, and providing proof of concept for validation. It emphasizes avoiding scenarios that lack clarity, depend on other vulnerabilities, or are not true vulnerabilities to ensure successful submissions.