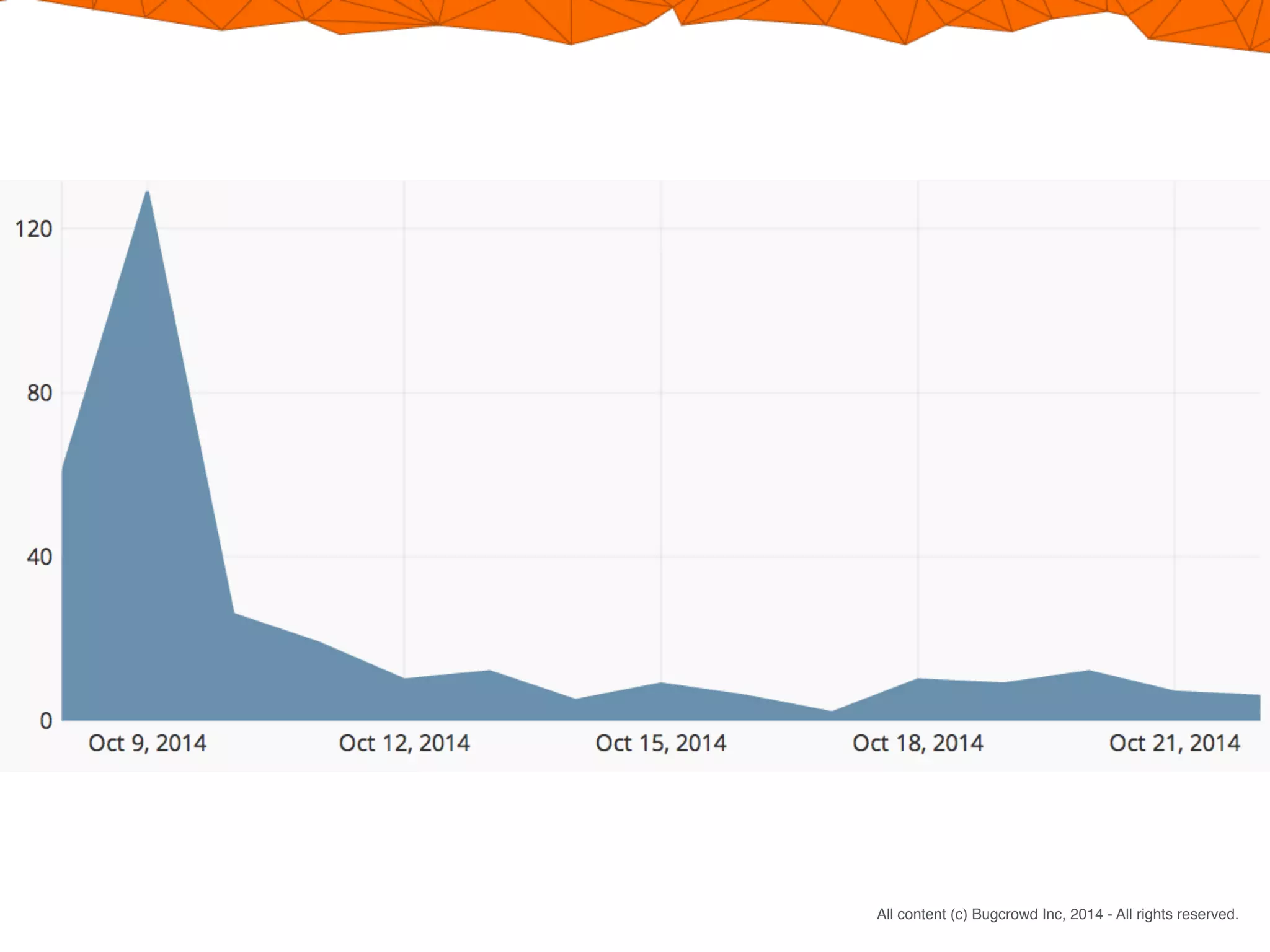
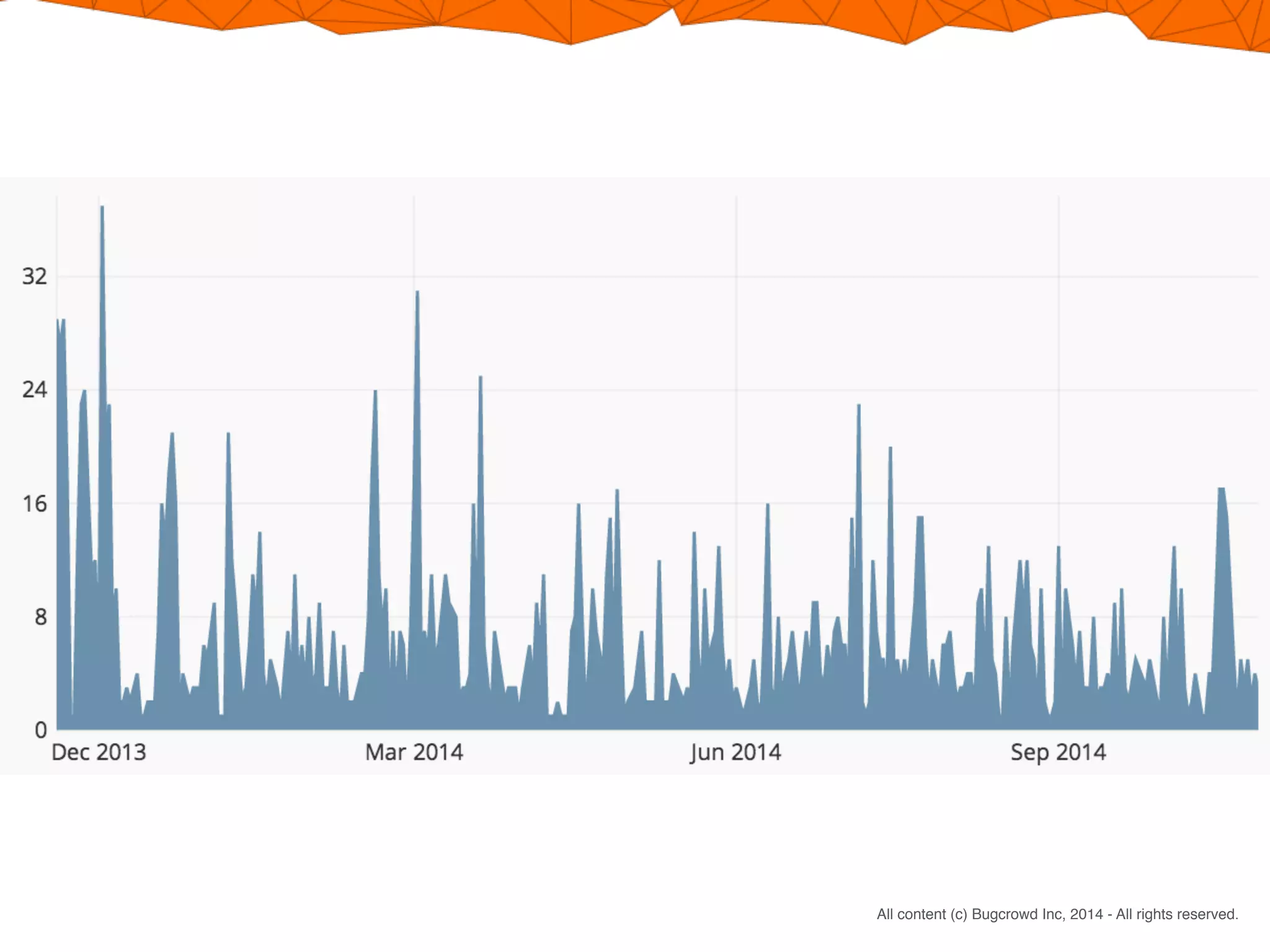
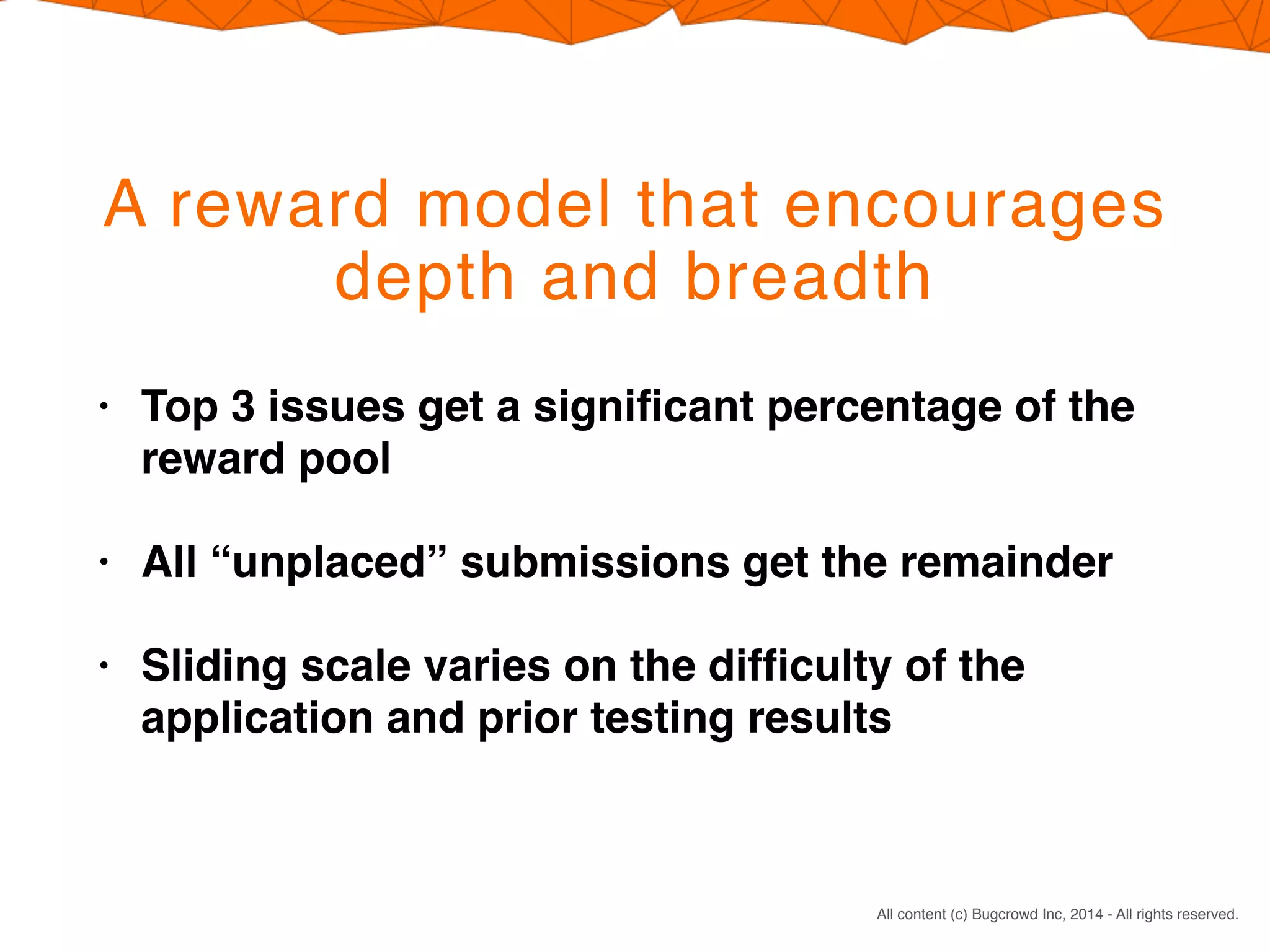
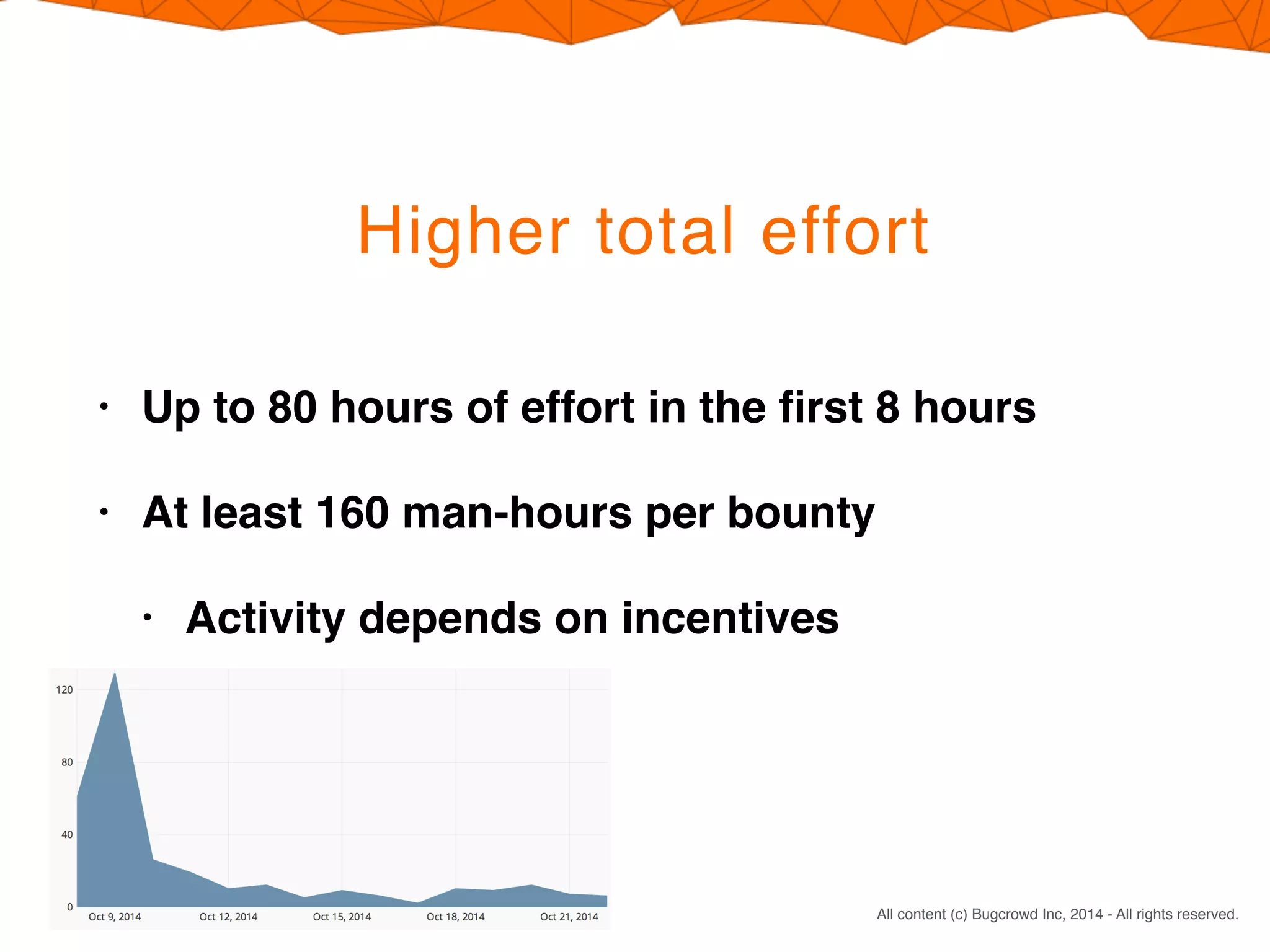
Crowdsourcing a penetration test through Bugcrowd's Flex model offers four main benefits: 1) You pay only for valid vulnerabilities found rather than researcher time spent; 2) Engaging many skilled researchers across different specialties increases the likelihood of finding issues; 3) The reward structure encourages in-depth testing by incentivizing top submissions; 4) This results in significantly more testing effort within similar timeframes as a traditional penetration test.



![CONFIDENTIAL. DO NOT DISTRIBUTE.
All content (c) Bugcrowd Inc, 2014 - All rights reserved.
How does it work?
• Program Setup
• Program Kickoff and Invitations
• Program Runs [2 weeks on average]
• Analysis [96 hours on average]
• Report Delivery and Access](https://image.slidesharecdn.com/4reasonstocrowdsourceyourpentest-150802181952-lva1-app6891/75/4-Reasons-to-Crowdsource-Your-Pen-Test-7-2048.jpg)