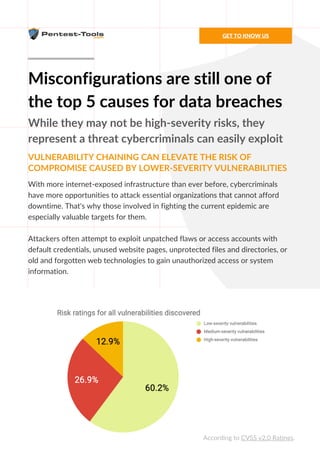
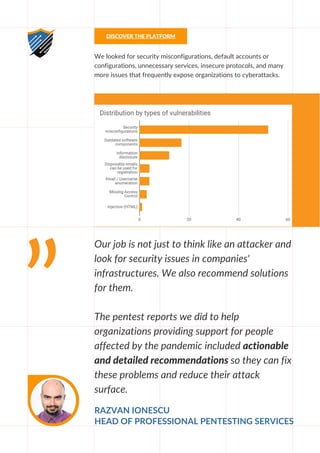
The report discusses the cybersecurity vulnerabilities discovered during free penetration tests offered to companies fighting the COVID-19 pandemic. It highlights key security issues such as misconfigurations, outdated software, and information disclosure, while presenting actionable recommendations to enhance defenses. The findings aim to help organizations better protect their critical operations against opportunistic cybercriminals.