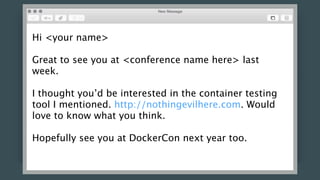
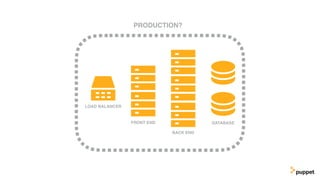
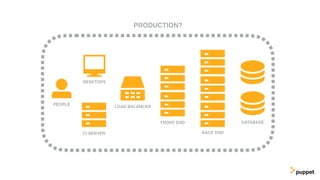
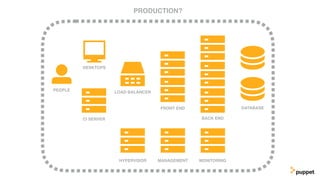
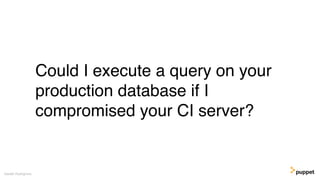
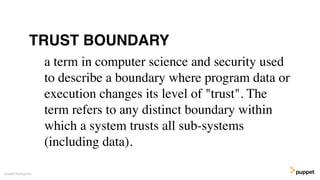
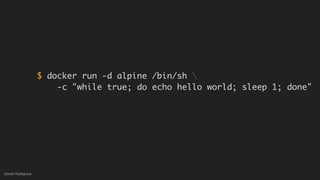
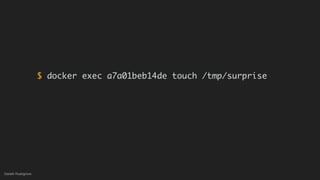
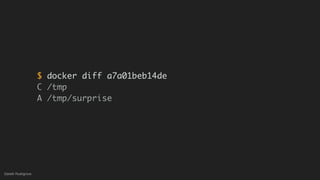
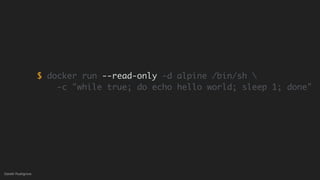
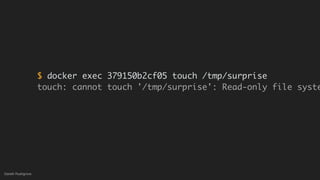
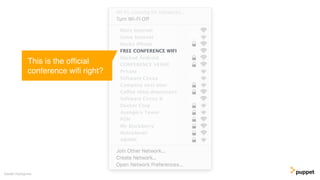
This document discusses threat modeling and how to properly scope security assessments. It provides examples of how threat modeling can be applied, including getting the full scope of the system correct and identifying risks. The document warns that developer laptops and conferences pose security risks and outlines some mitigation approaches like two-factor authentication and separation of duties. The overall message is that modern development approaches require keeping security top of mind.



















































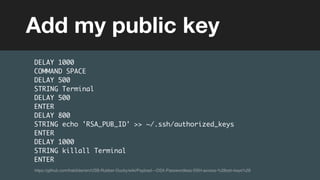
![(without introducing more risk)
$ curl -s https://api.github.com/users/<username>/events/public
| jq '.[].payload.commits[0].author.email'
| sort
| uniq
| grep -v "null"
Email from GitHub user](https://image.slidesharecdn.com/thinkingevilthoughts-160905083401/85/Thinking-Evil-Thoughts-74-320.jpg)