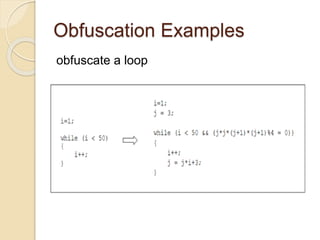
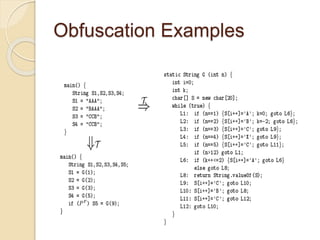
Code obfuscation techniques make code unintelligible or hard to understand. They are used by software companies to protect intellectual property and by malicious actors to avoid detection from antivirus software. The document discusses different obfuscation techniques like randomization, data encoding, and logic structure obfuscation. It also covers how obfuscated scripts can be used by attackers for information loss, downloading malware, or redirecting users to malicious sites. Antivirus software tries to detect obfuscated malware using techniques like signature matching, emulation, and analyzing script behavior after deobfuscation.