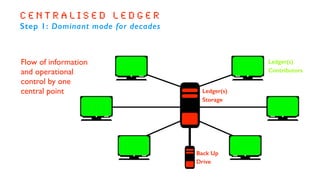
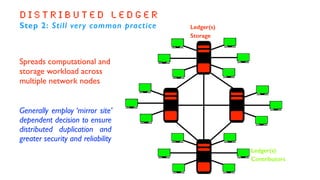
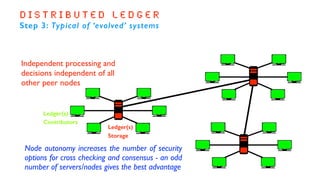
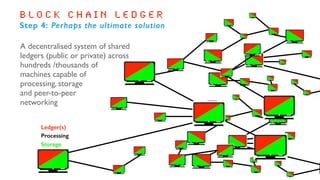
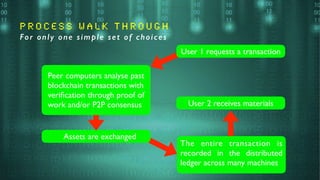
The document outlines the basics and implications of blockchain technology, emphasizing its decentralized nature and security advantages over traditional transaction systems. It discusses the evolution from centralized ledgers to distributed ledgers and ultimately to blockchain ledgers, which enable secure, peer-to-peer transactions without intermediaries. Additionally, it highlights the potential applications of blockchain across various sectors while emphasizing its open-source, user-driven characteristics.