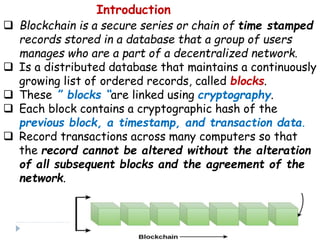
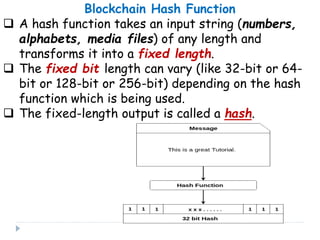
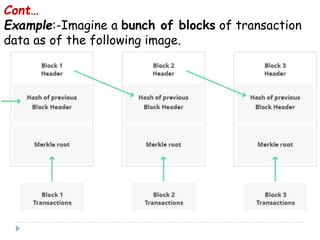
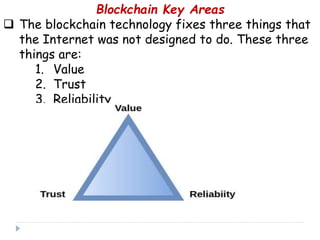
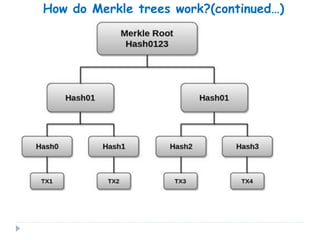
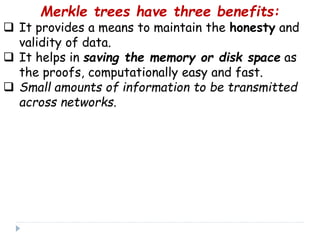
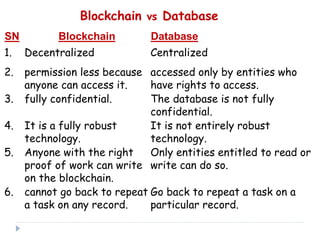
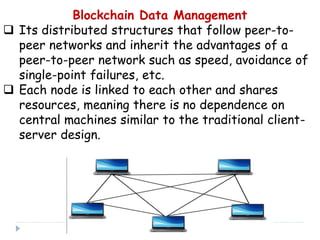
Blockchain is a distributed database that records transactions in blocks that are linked using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data. This allows record of transactions to be recorded across decentralized networks and prevents alteration of the record without agreement of the network. Blockchain uses cryptography and consensus algorithms to ensure security and verification of transactions without the need for centralized authorities.