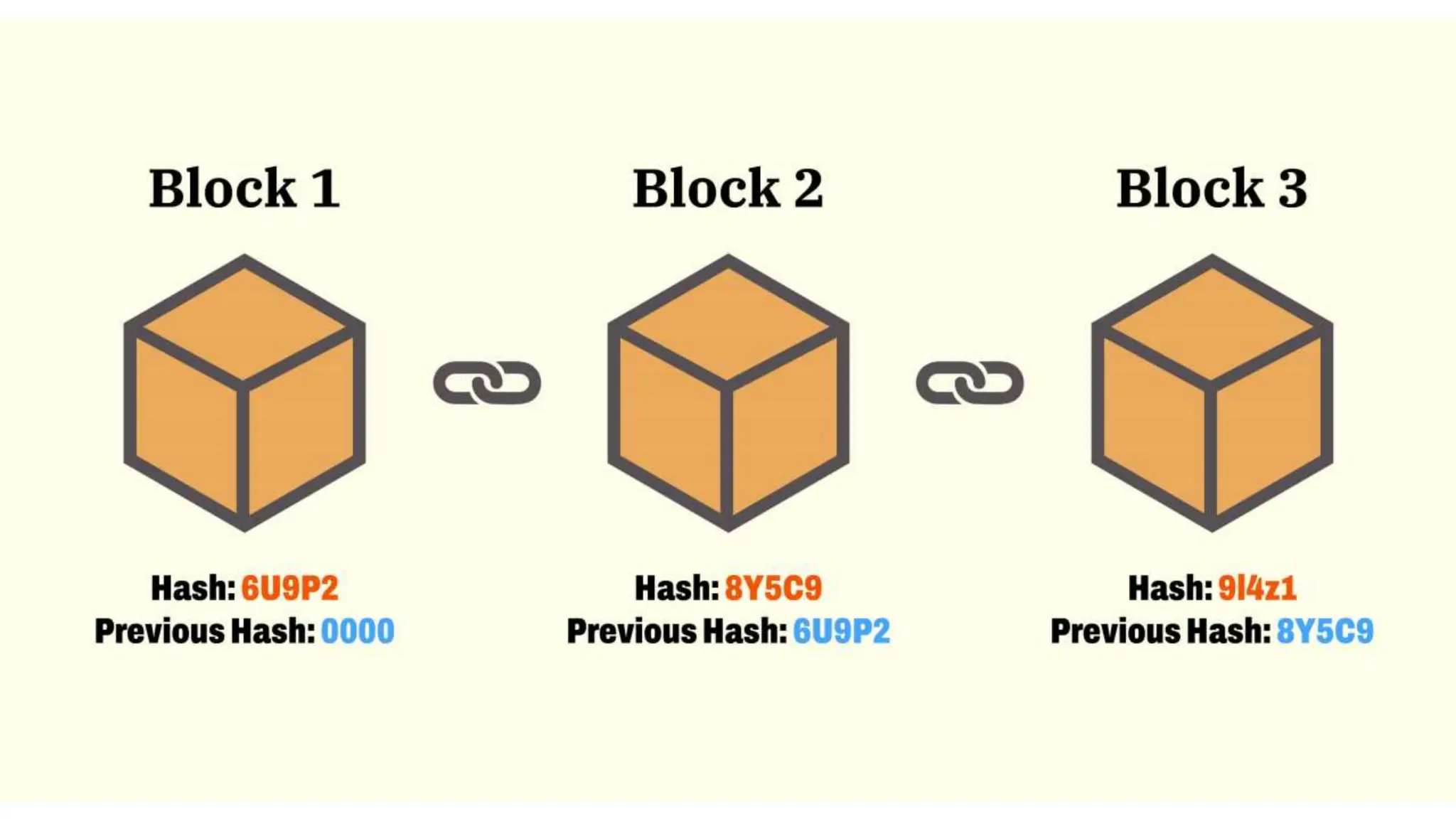
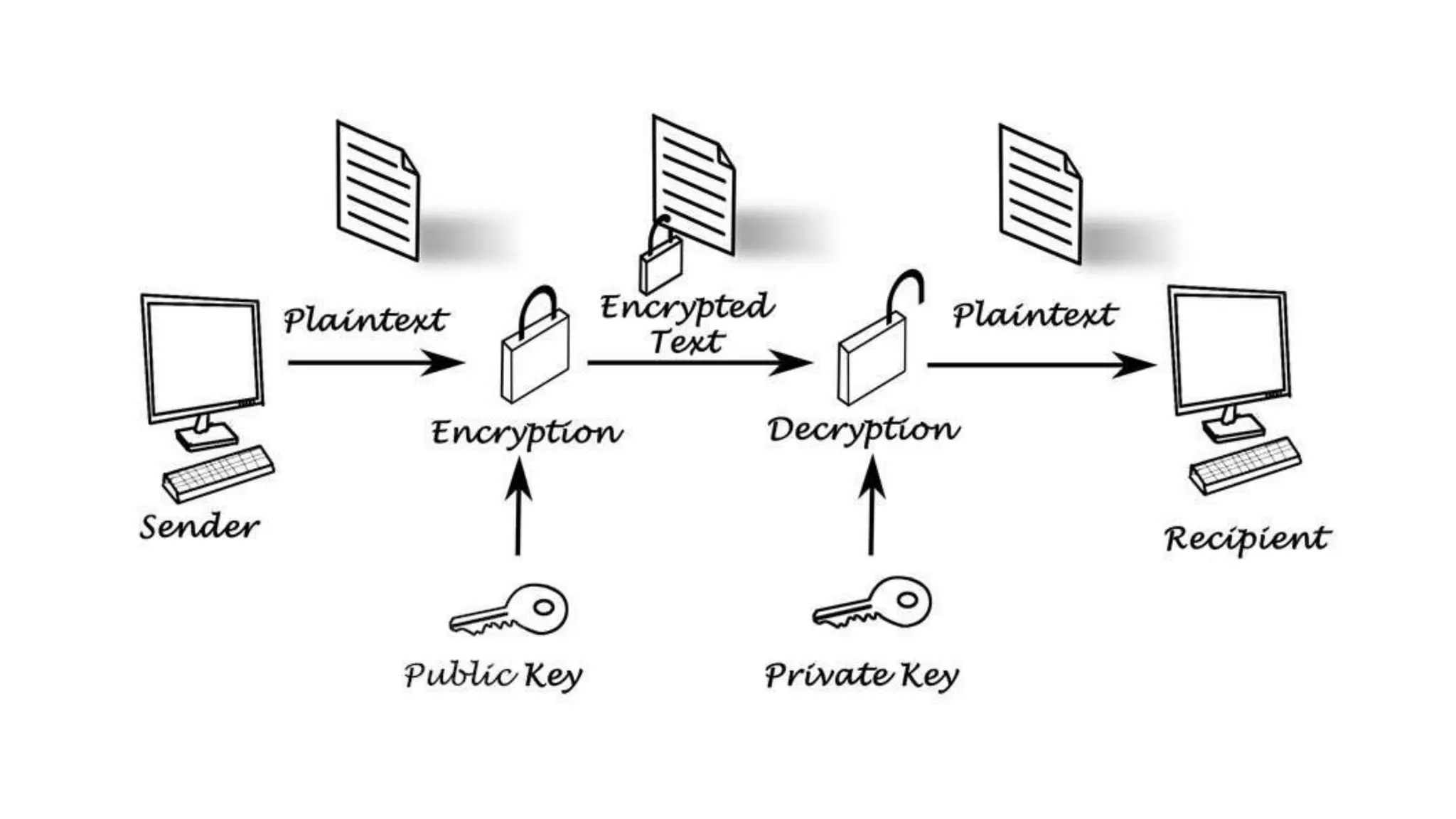
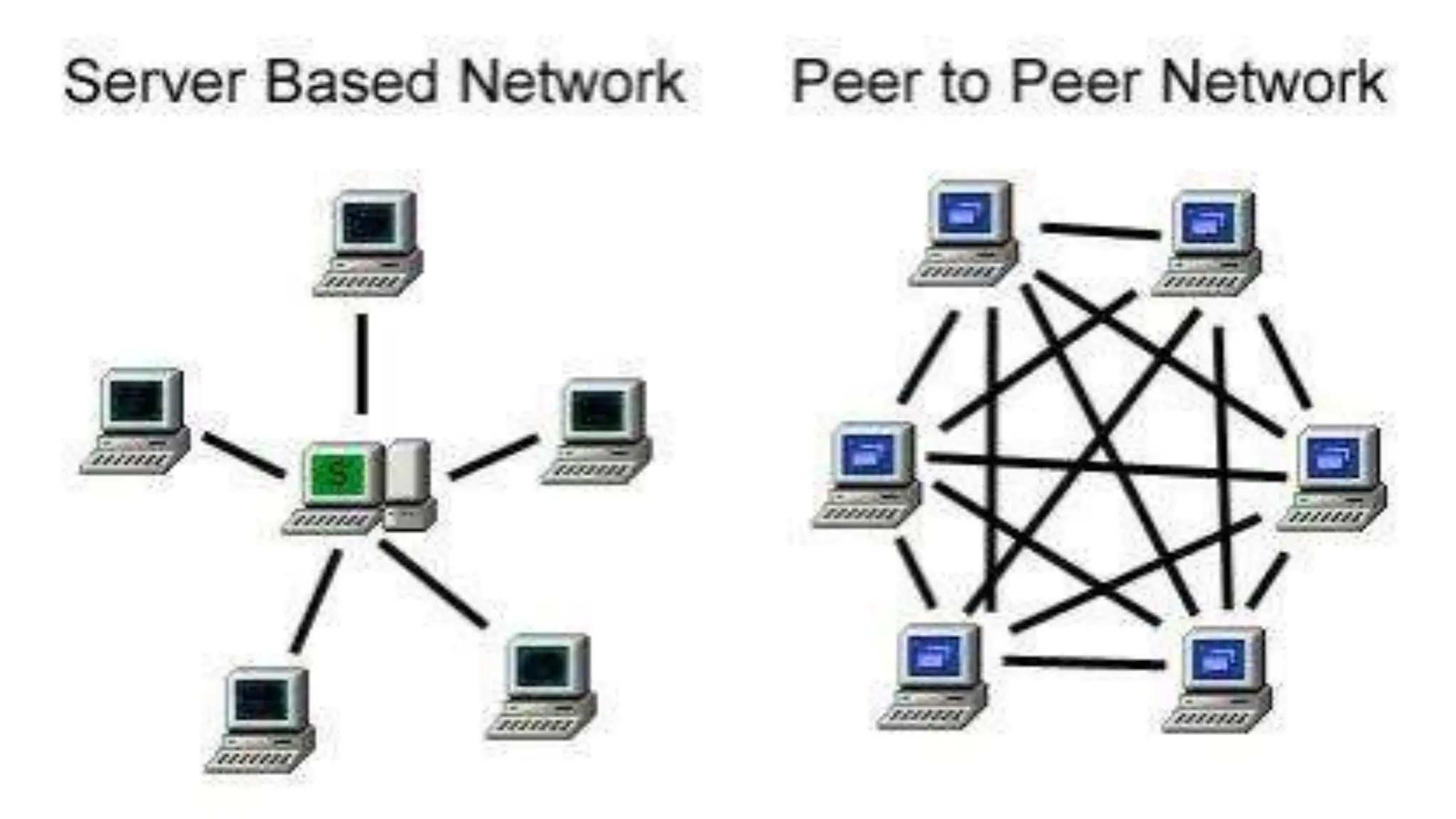
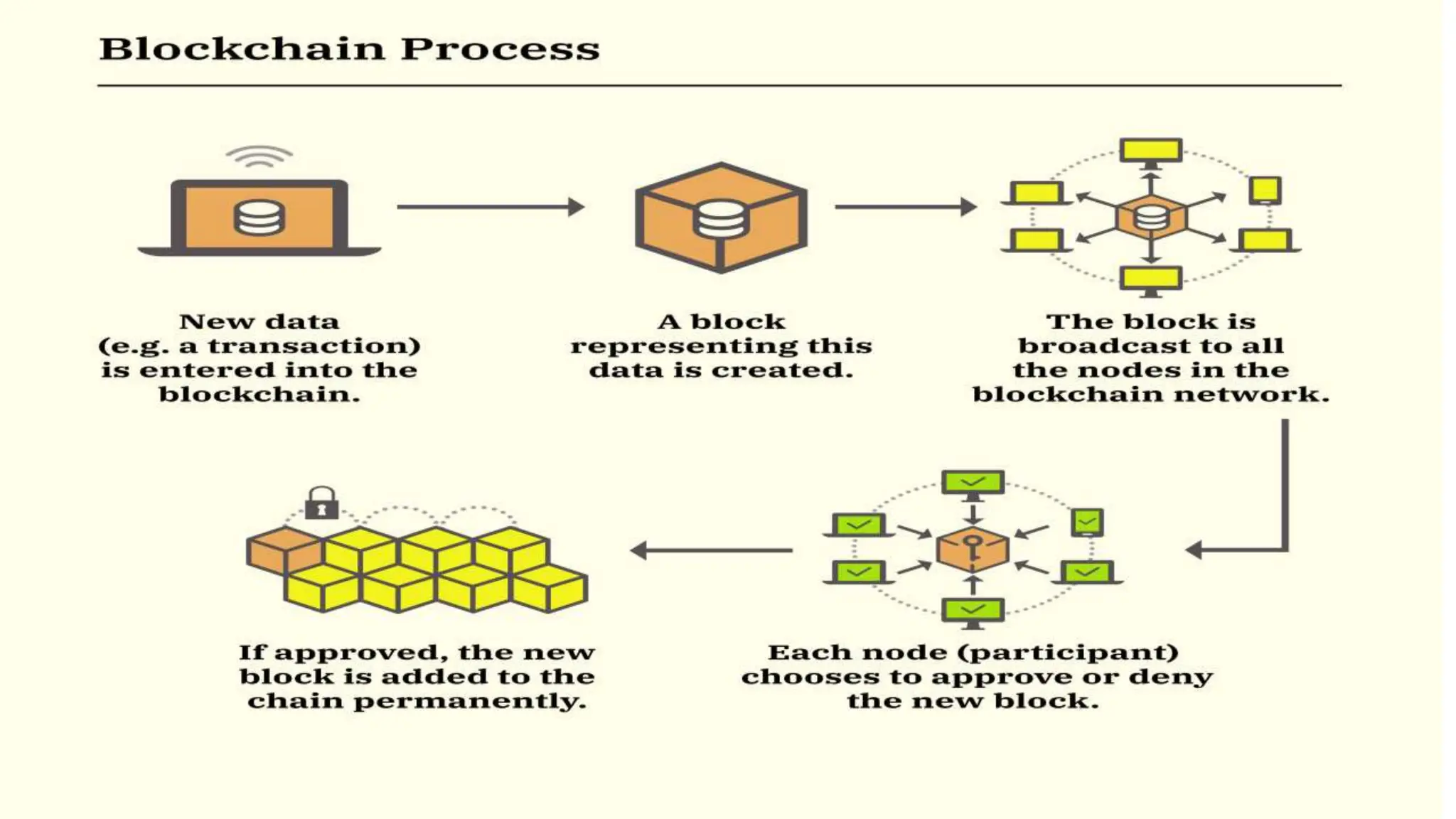
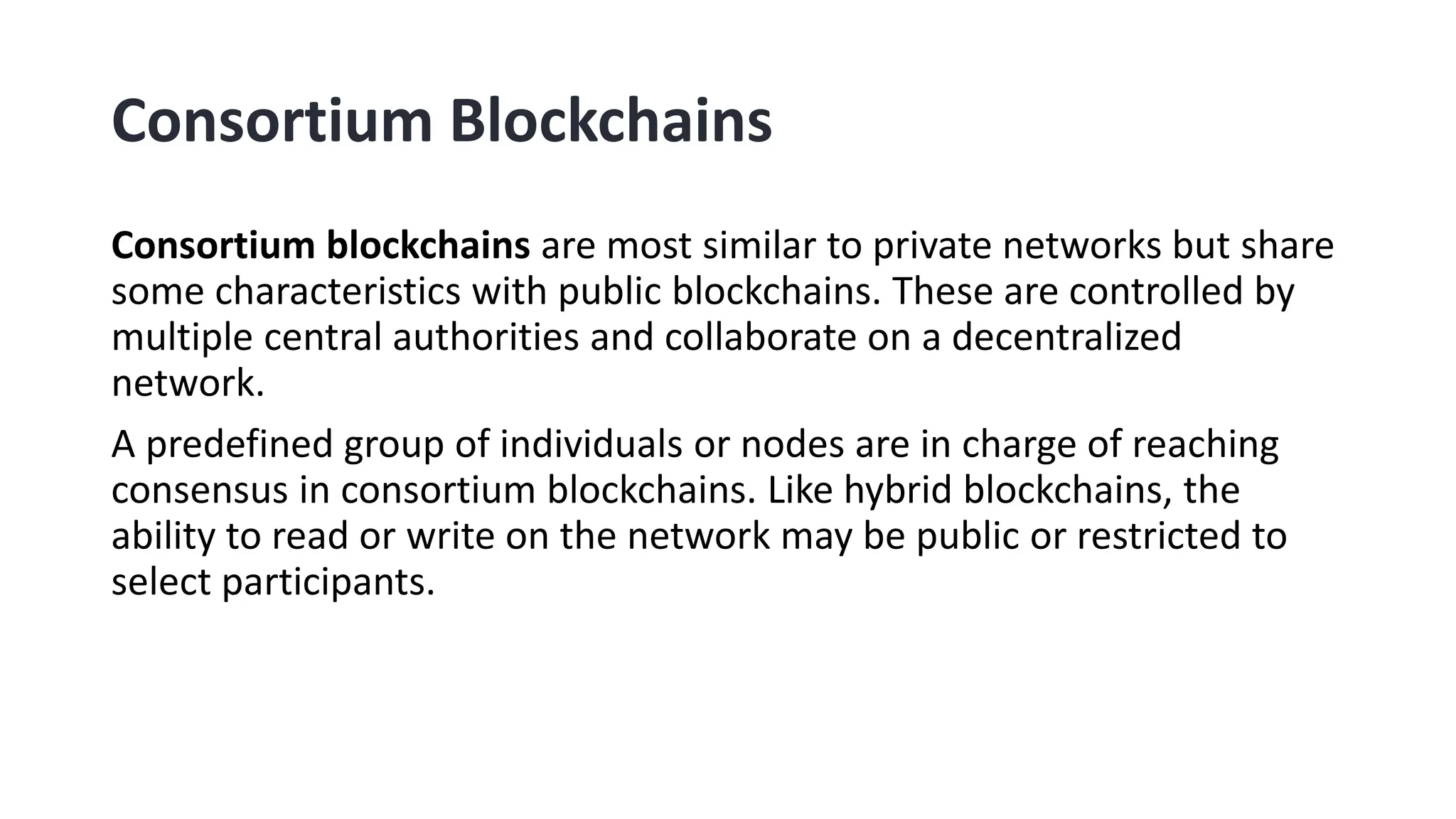
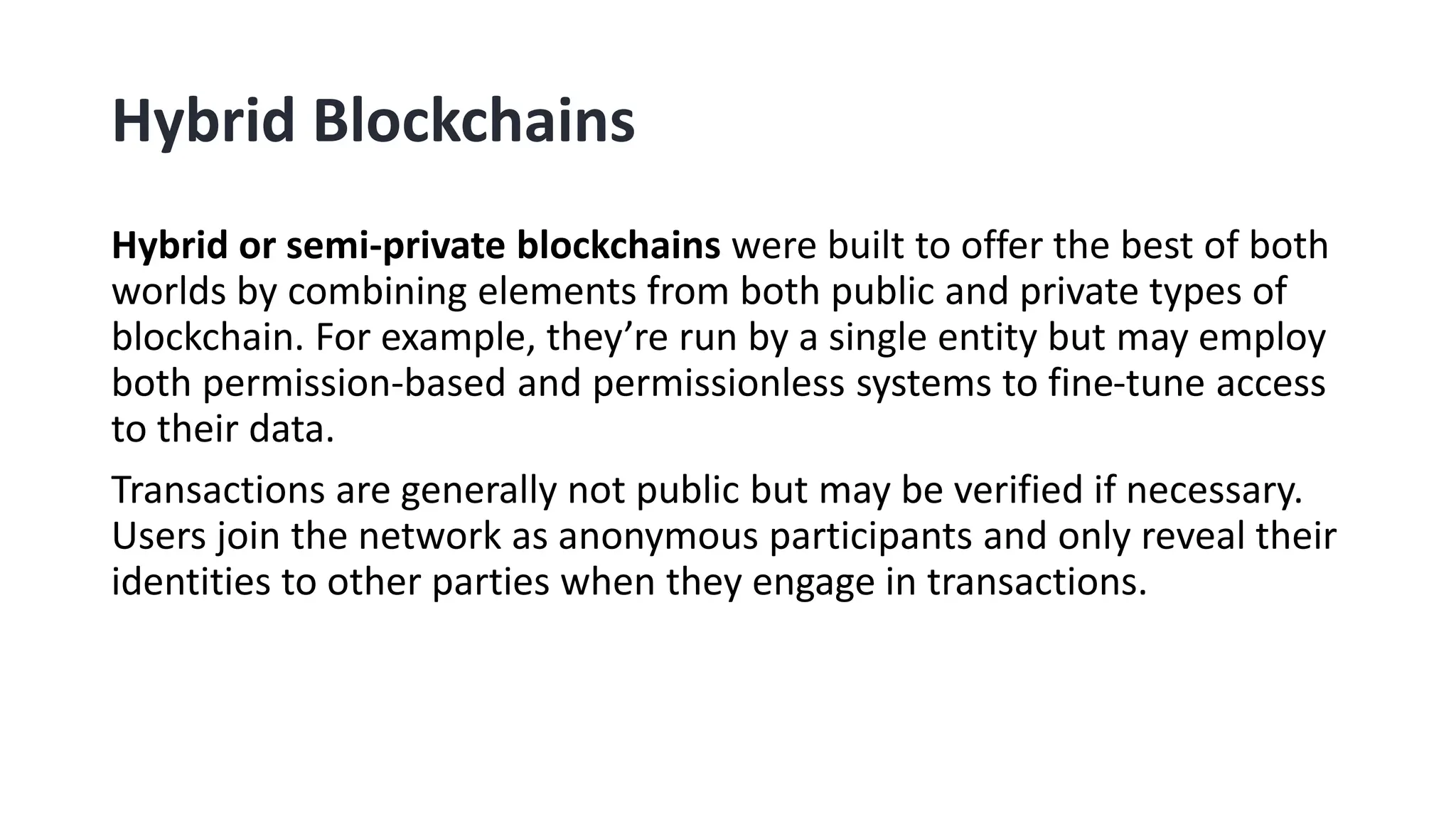
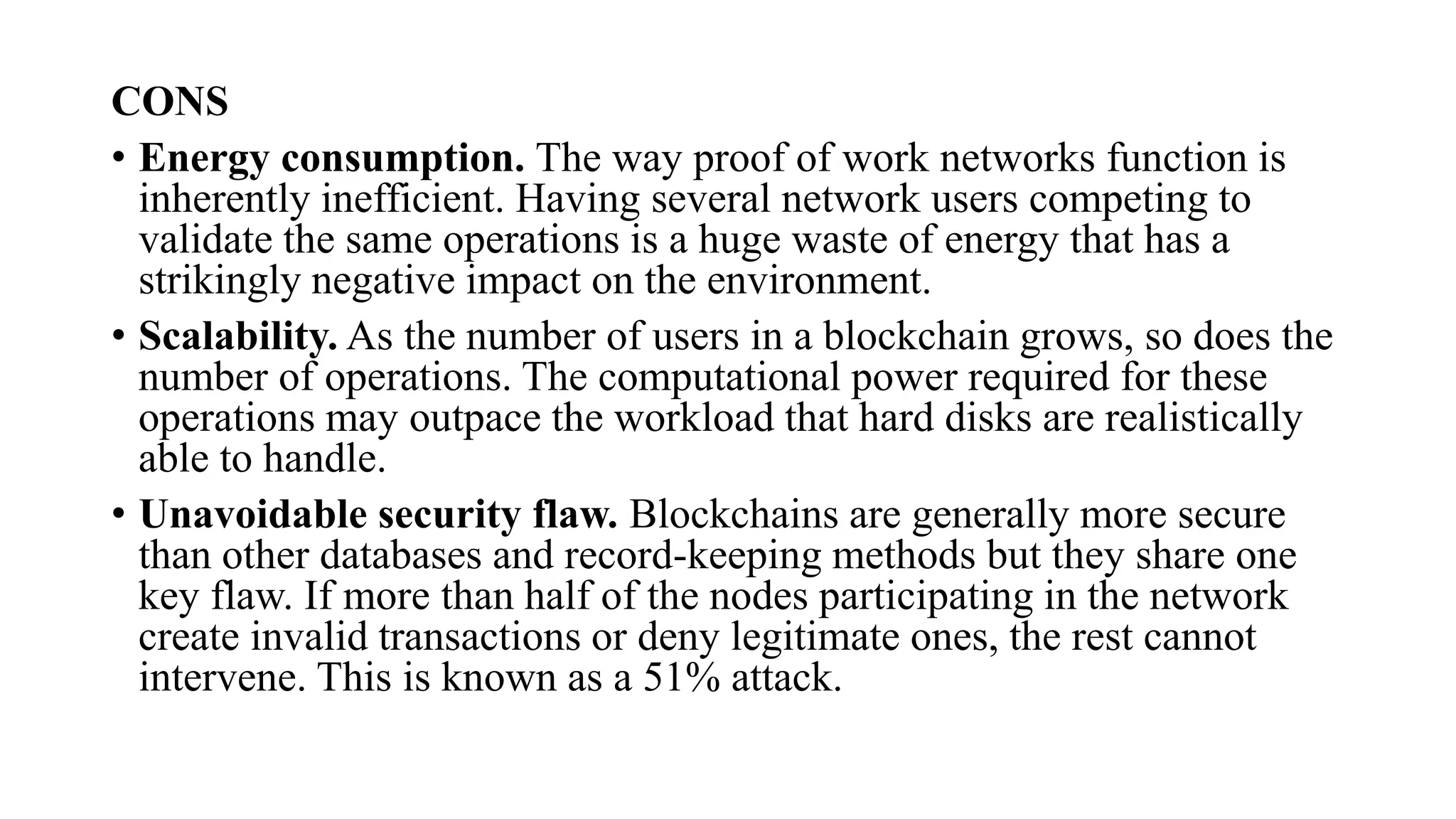
Blockchain is a decentralized and distributed ledger system that allows multiple parties to securely record and store information in a transparent and tamper-resistant manner. It works by creating a chain of blocks, with each block containing a set of transactions. This chain is then distributed across a network of computers, making it nearly impossible to alter. Key features of blockchain include decentralization, transparency, immutability, and security. While applications include cryptocurrency, NFTs, and supply chain management, challenges remain around scalability, energy consumption, and potential security flaws from 51% attacks.