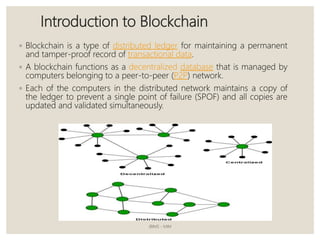
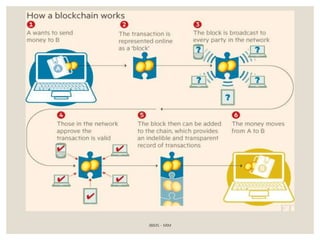
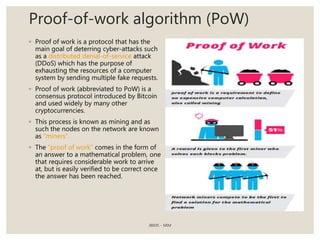
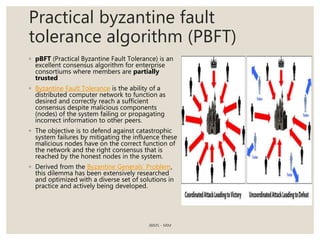
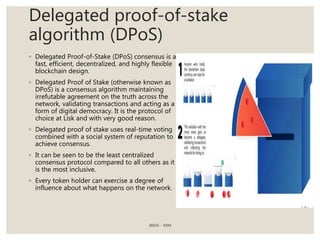
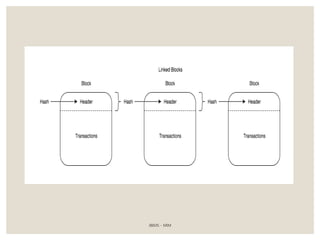
The document provides a comprehensive overview of blockchain technology, including its introduction, history, mechanisms, platforms, and consensus algorithms. It highlights how blockchain serves as a secure, decentralized digital ledger used across various industries beyond cryptocurrencies, such as finance, healthcare, and manufacturing. The document also contrasts different consensus mechanisms like proof-of-work and proof-of-stake, discussing their implications for energy consumption and transaction validation.