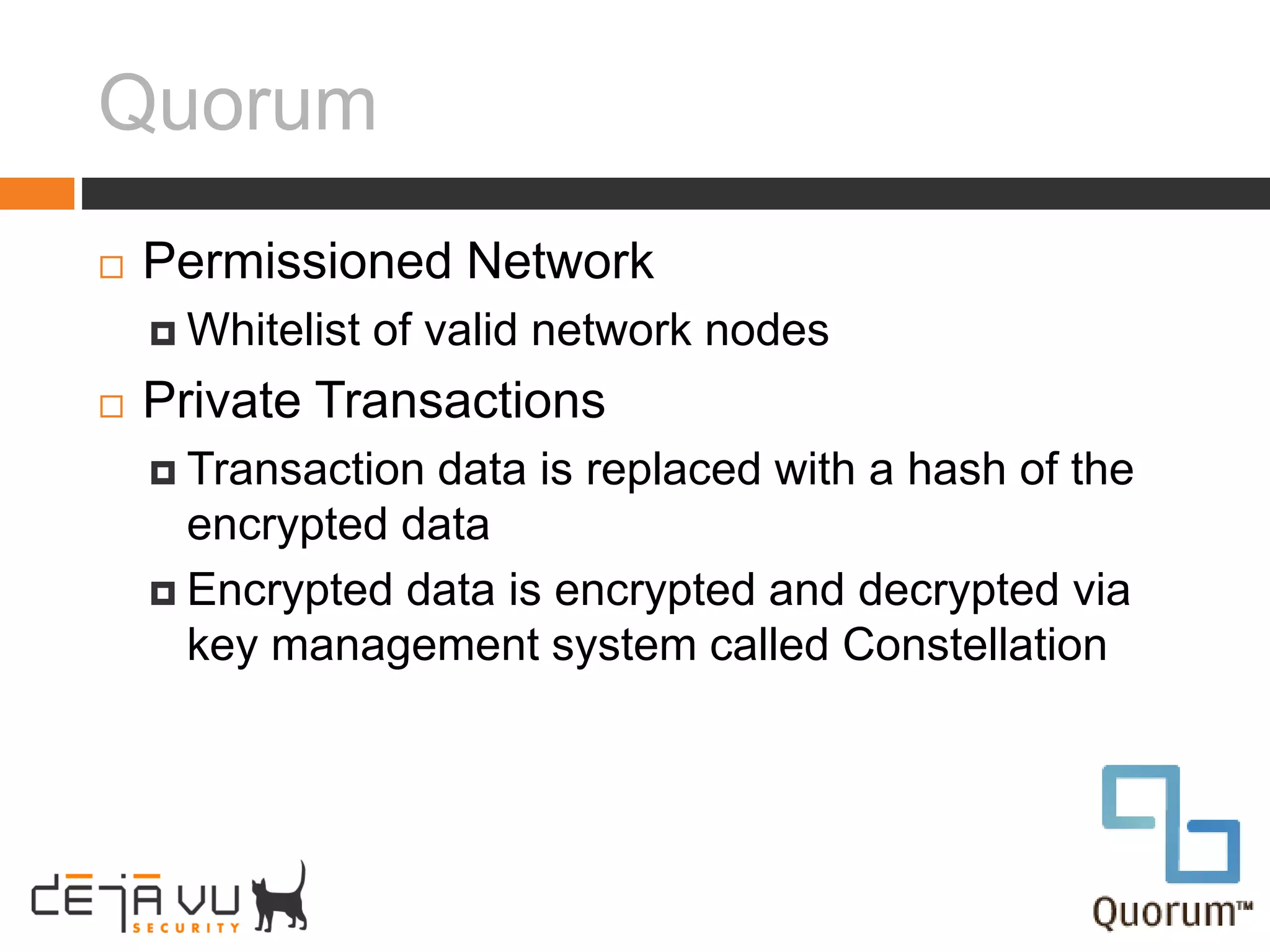
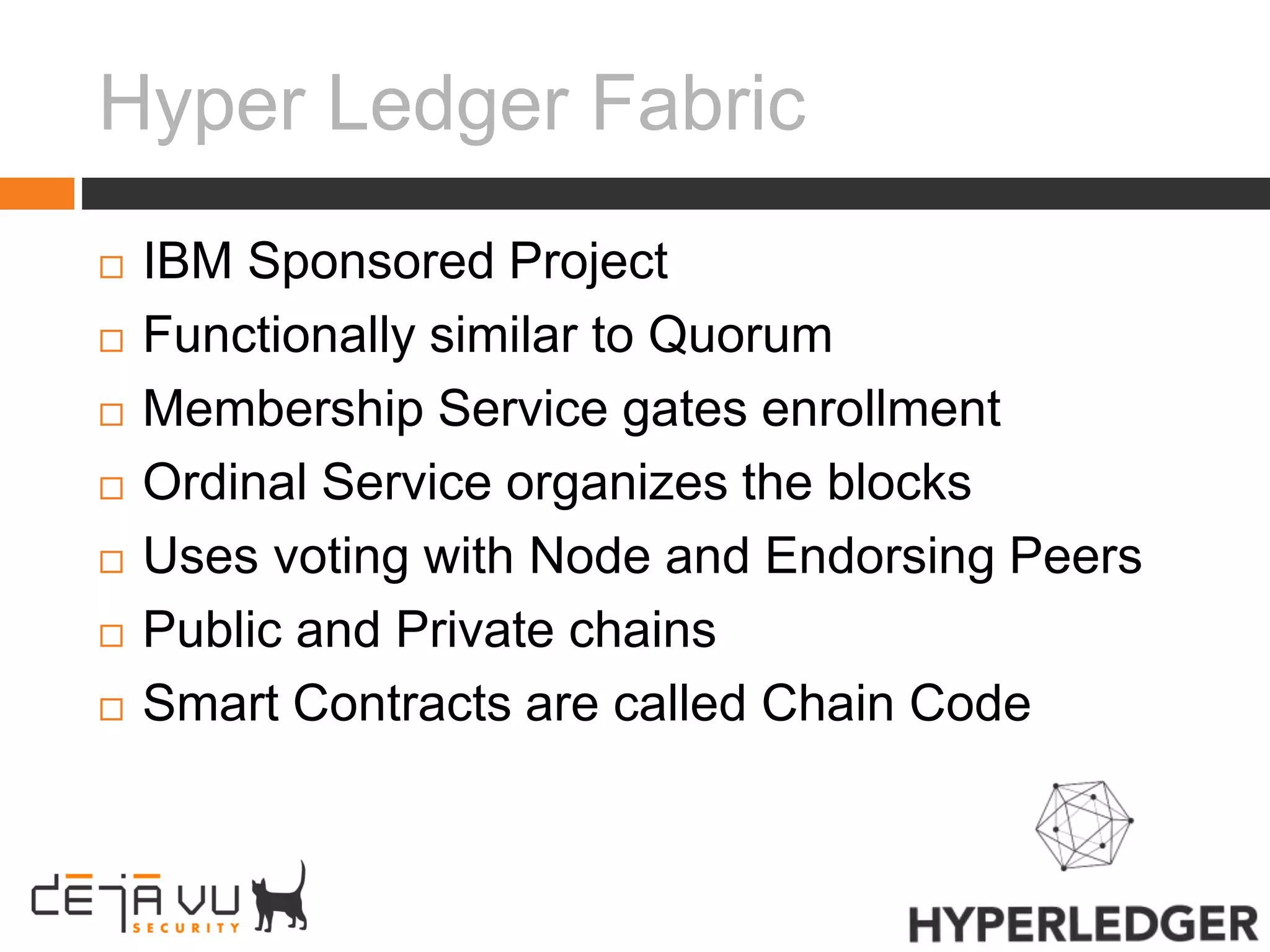
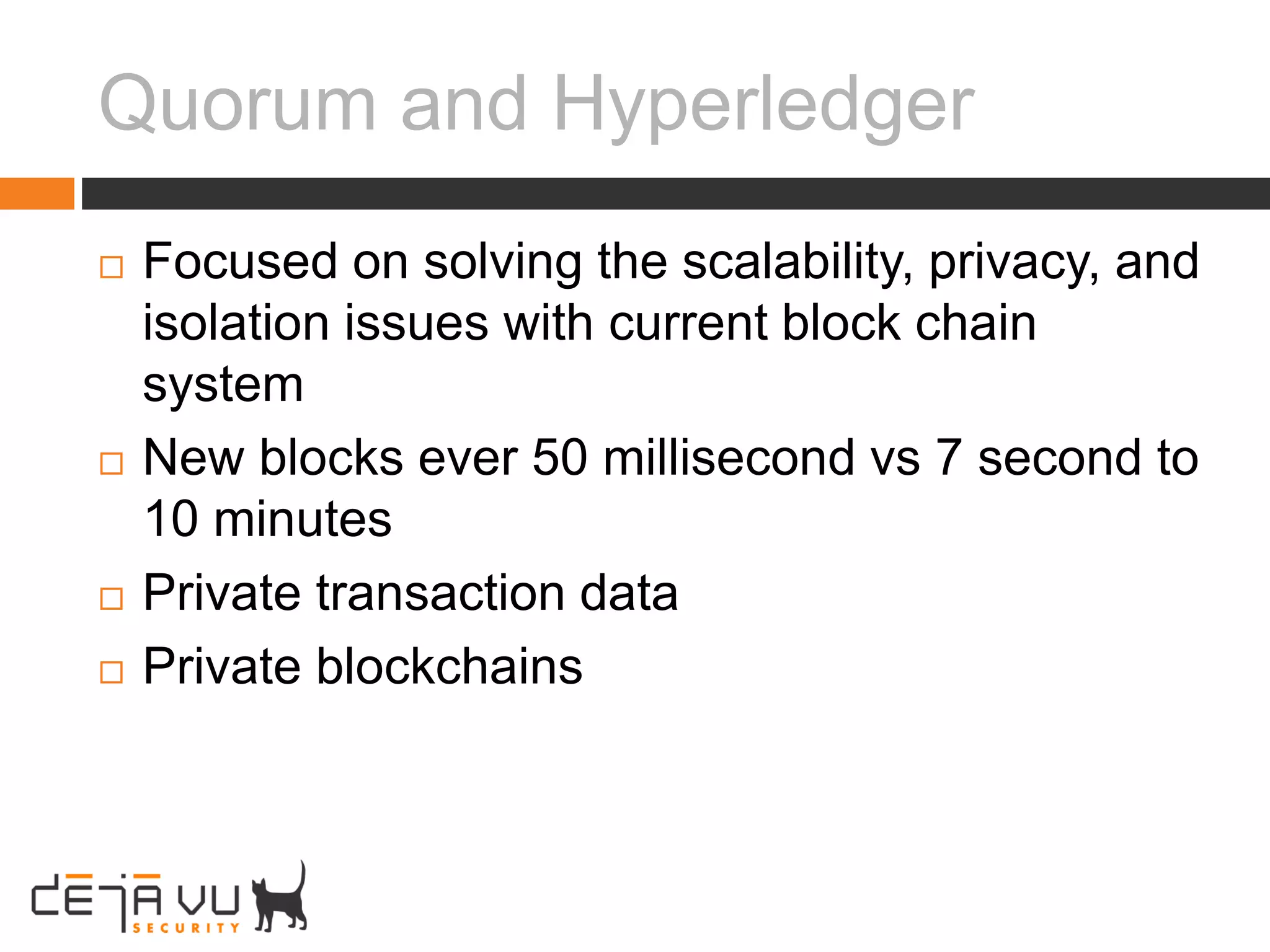
Adam Cecchetti, CEO of Deja vu Security, discusses building security into blockchain technologies. Early ledger technologies from 5000 years ago provide context for modern blockchains. Blockchains face challenges with privacy, forging records, and scalability similar to early computers. Enterprise blockchains like Quorum and Hyperledger aim to solve these issues by making transactions private and permissioned through consensus algorithms instead of mining. Building security into decentralized applications and smart contracts is important as blockchains are still new computing platforms facing classic security problems.


![Early Ledger Tech : Not Privacy
Preserving!
“A stockpile of 12,000 trade accounts left by Assyrian
merchants in the 19th century BCE has been used to find
half a dozen locations. The researchers used
mathematical models based on the prices of goods and
the frequency of trips between trade hubs to pinpoint
where the cities once stood.”[0]](https://image.slidesharecdn.com/blockchainsummit-3-adam-171214010220/75/Deja-vu-Security-Blockchain-Security-Summit-Adam-Cecchetti-5-2048.jpg)