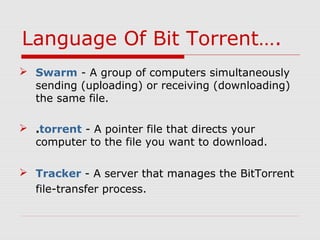
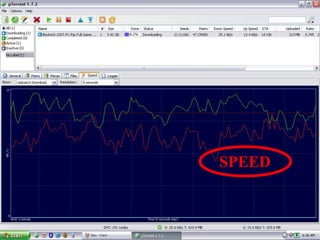
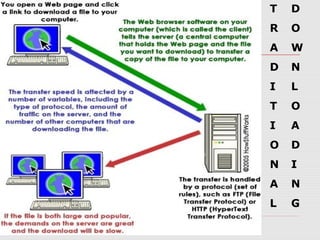
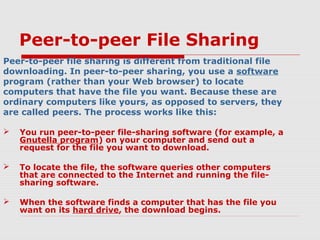
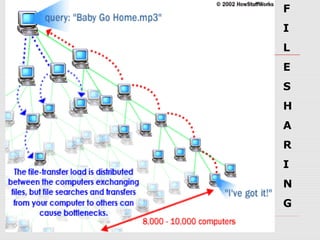
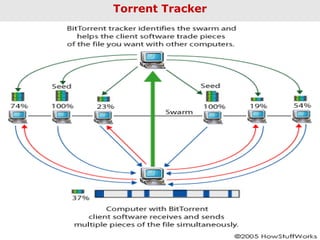
BitTorrent is a file-sharing protocol that allows for fast downloading of large files by utilizing a peer-to-peer network, thereby maximizing transfer speeds. It operates by having users download file pieces simultaneously from multiple sources, reducing dependency on central servers, and includes terms like 'seeder' and 'leecher' within its ecosystem. While BitTorrent is free and open-source, it has become associated with piracy due to the ease of accessing unlicensed content.