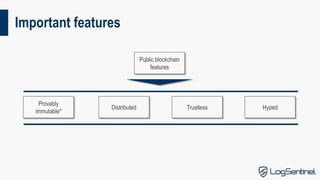
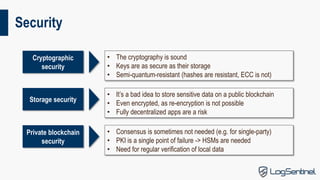
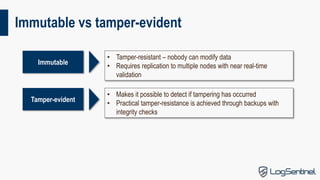
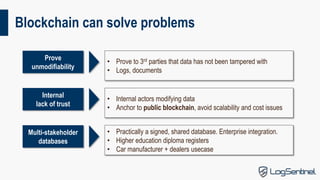
This document provides an overview of blockchain technology, including its types, use cases, security, and usability. It discusses the key components of blockchain like hash chains, Merkle trees, and consensus models. It outlines the main types of blockchain solutions and some important features like immutability and decentralization. The main drawbacks of public blockchains are that they are expensive, volatile, and not scalable. The document also discusses security considerations and challenges with usability. It analyzes some proposed use cases for blockchain technology and their issues. In conclusion, it states that cryptography enables data integrity, and the right tool should be chosen for each job.