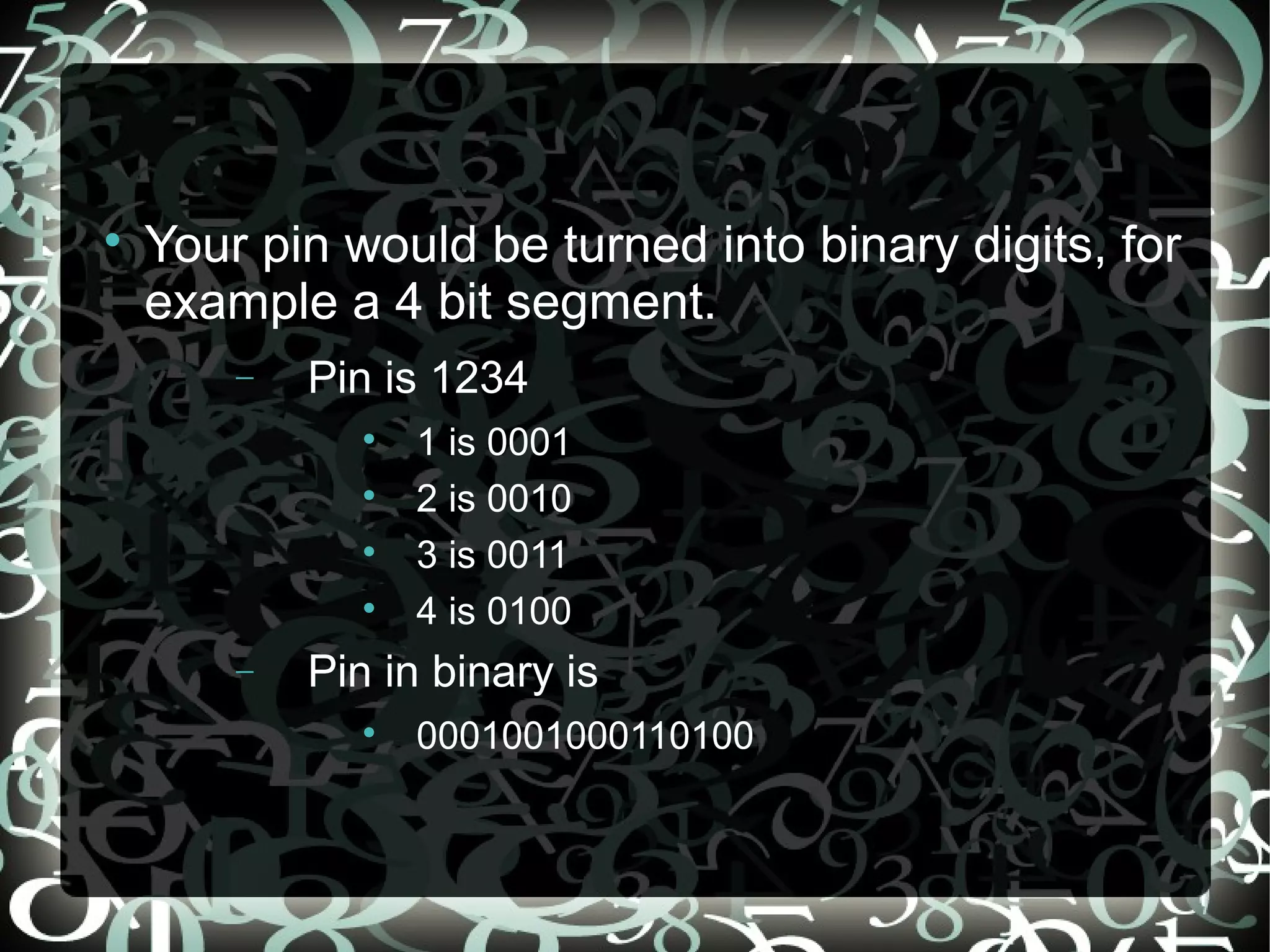
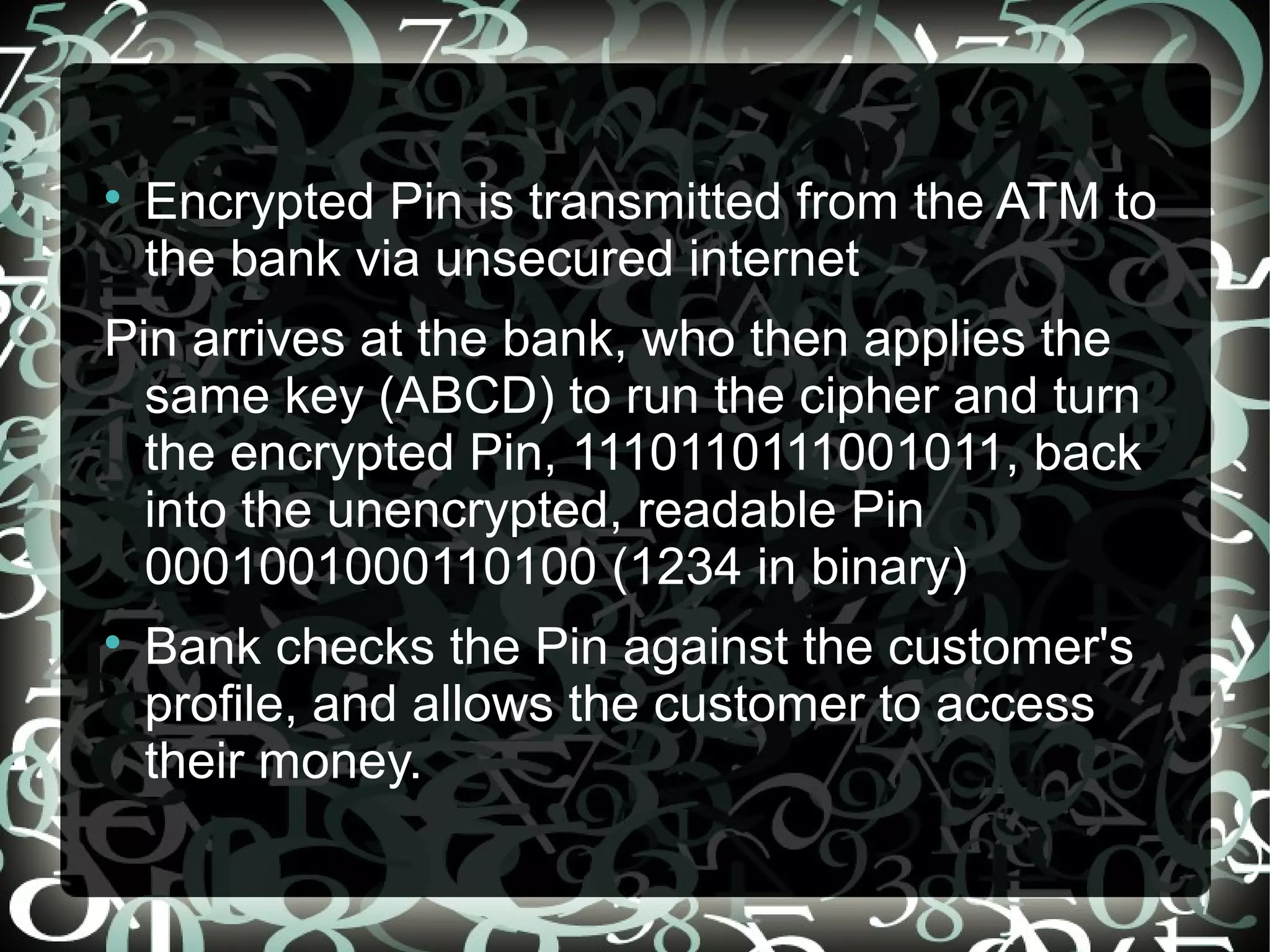
Cryptography is the study of encrypting information to make it unreadable without authorization. Encryption uses a cipher and key to encode data, hiding its original content. The encrypted data is transmitted and then decrypted at the destination using the same key and cipher to restore the original data. Early forms of encryption included simple substitution ciphers. Modern encryption encrypts data like ATM pins into binary and uses algorithms to encrypt it during transmission, ensuring privacy over insecure networks.