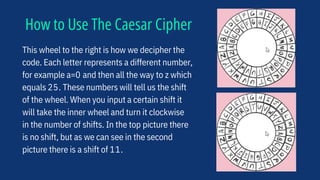
Cryptography is the process of encrypting information to hide its meaning and involves techniques like cipher systems that scramble letters and numbers. Different encryption methods have been used throughout history from simple substitution ciphers like the Caesar cipher used by Julius Caesar to modern techniques relying on complex mathematics. Alan Turing helped crack the German Enigma code during World War II by designing the bombe machine to determine the settings of the Enigma rotors and help decrypt messages.