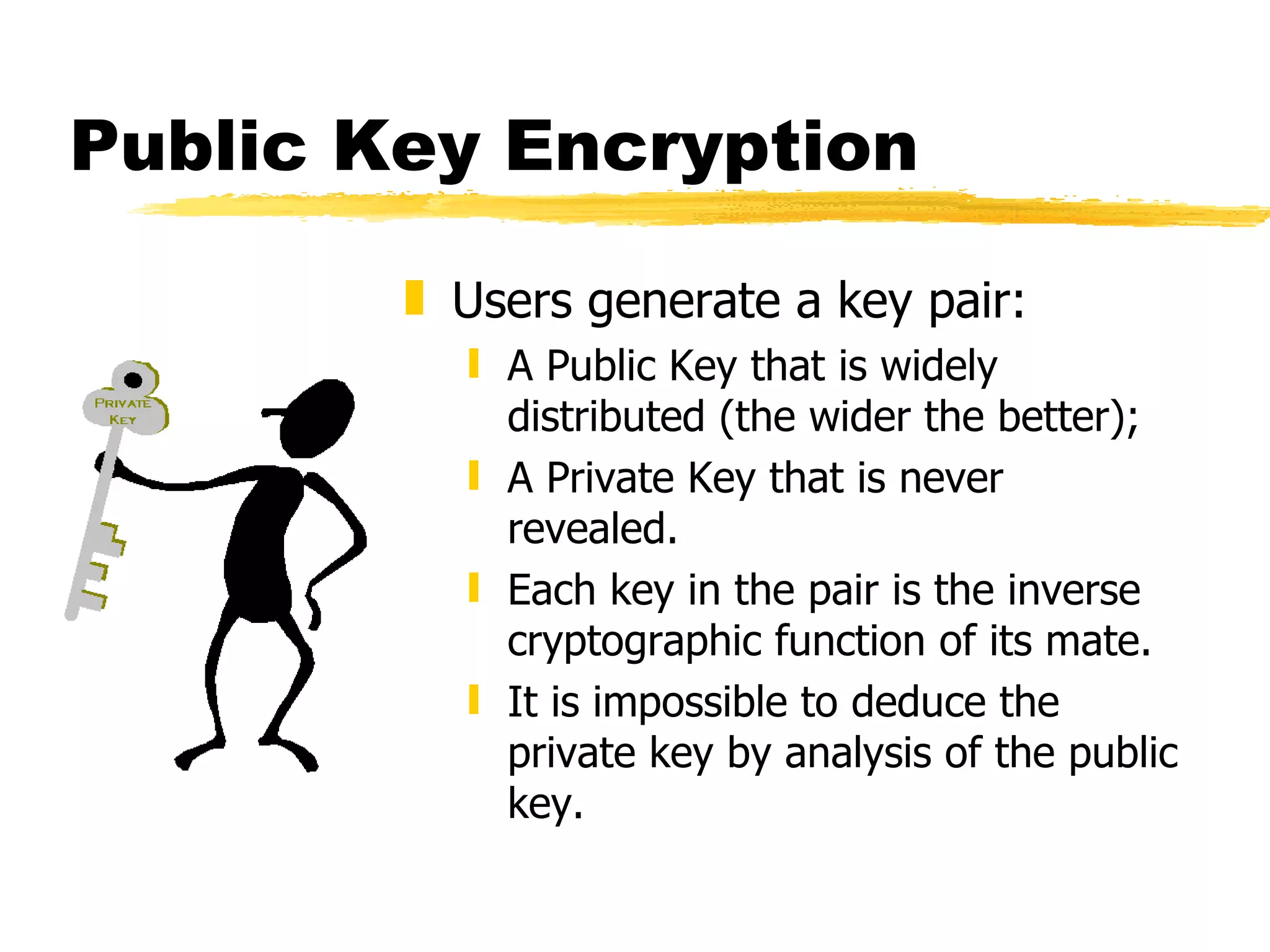
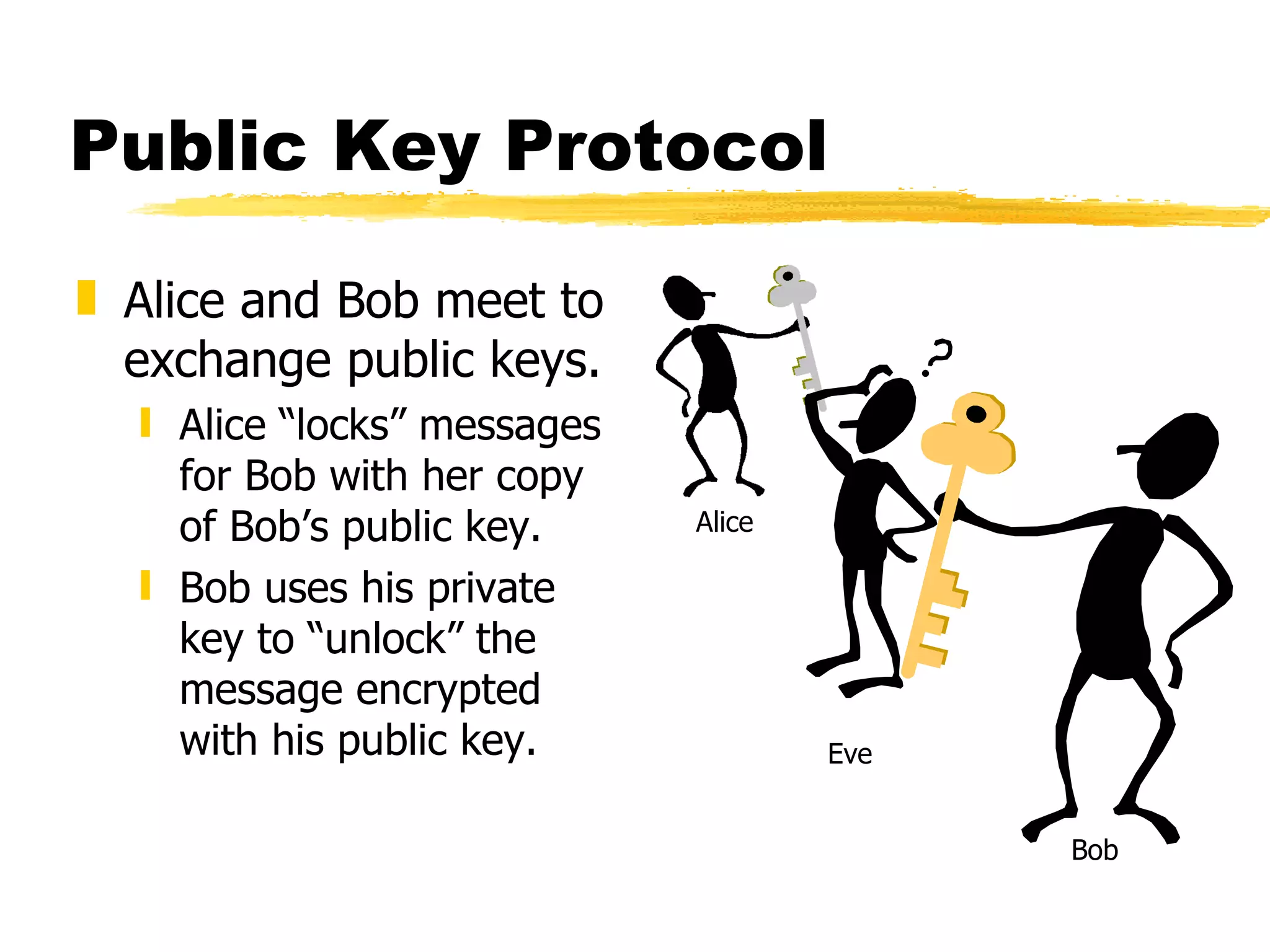
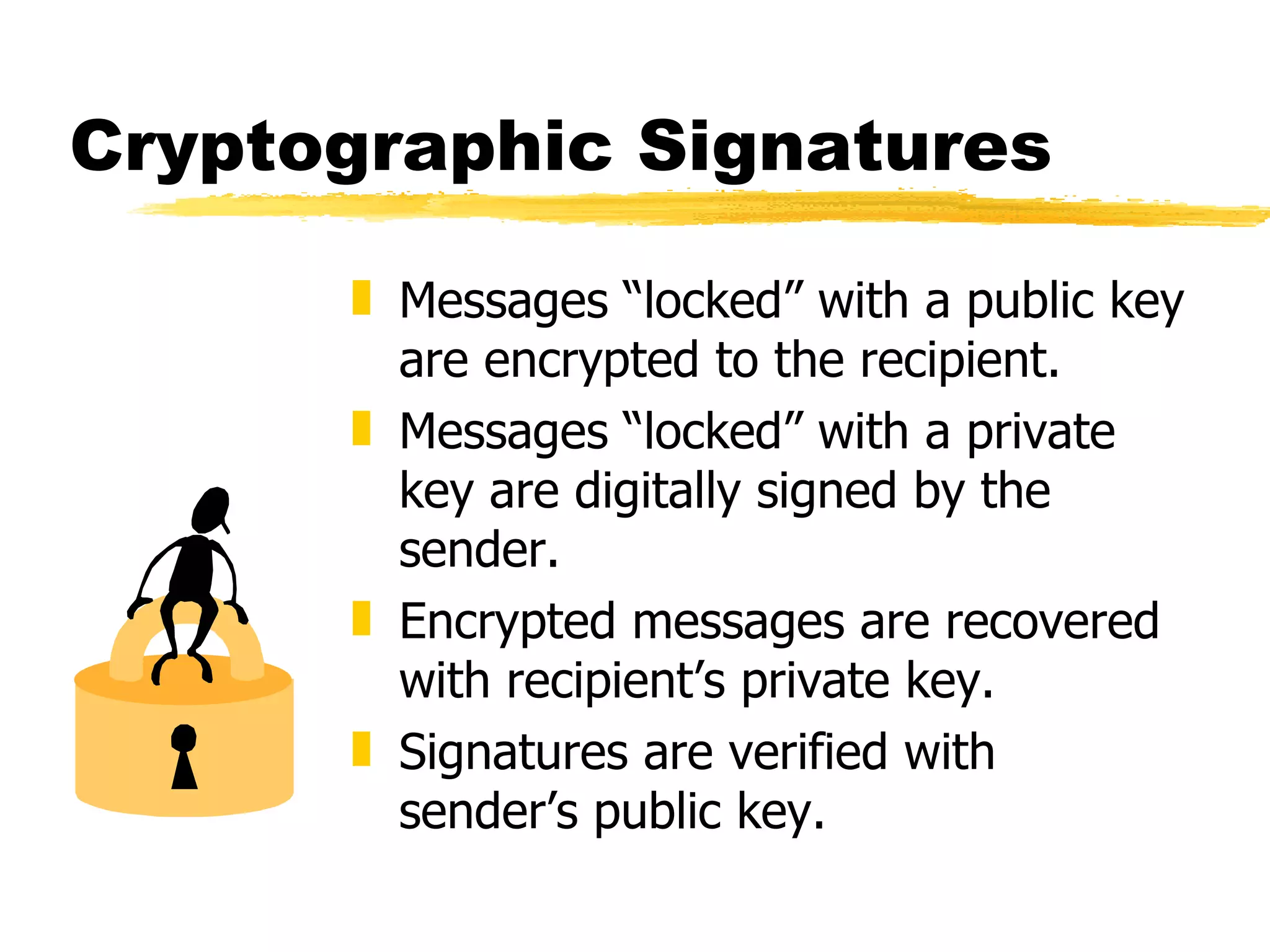
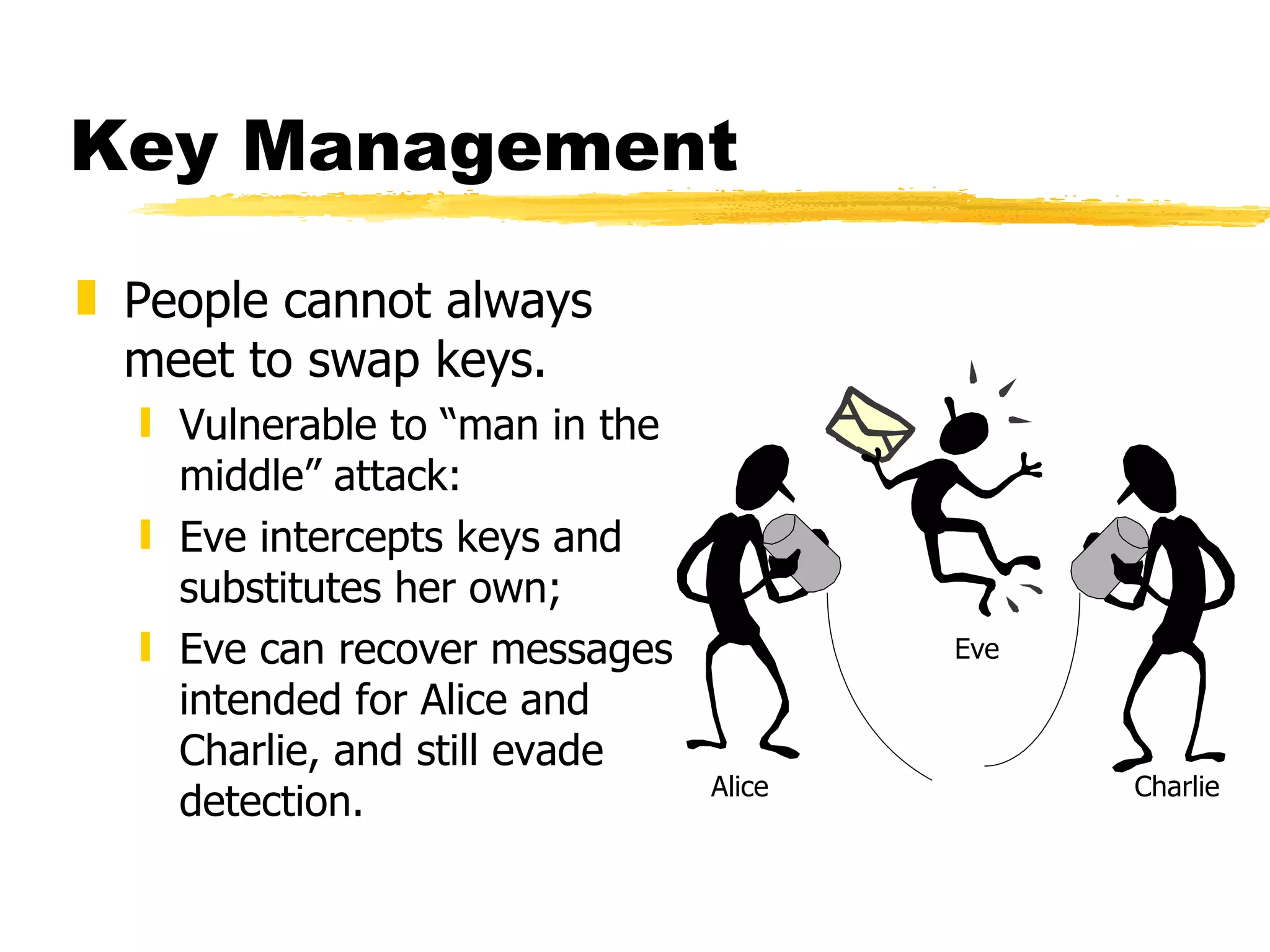
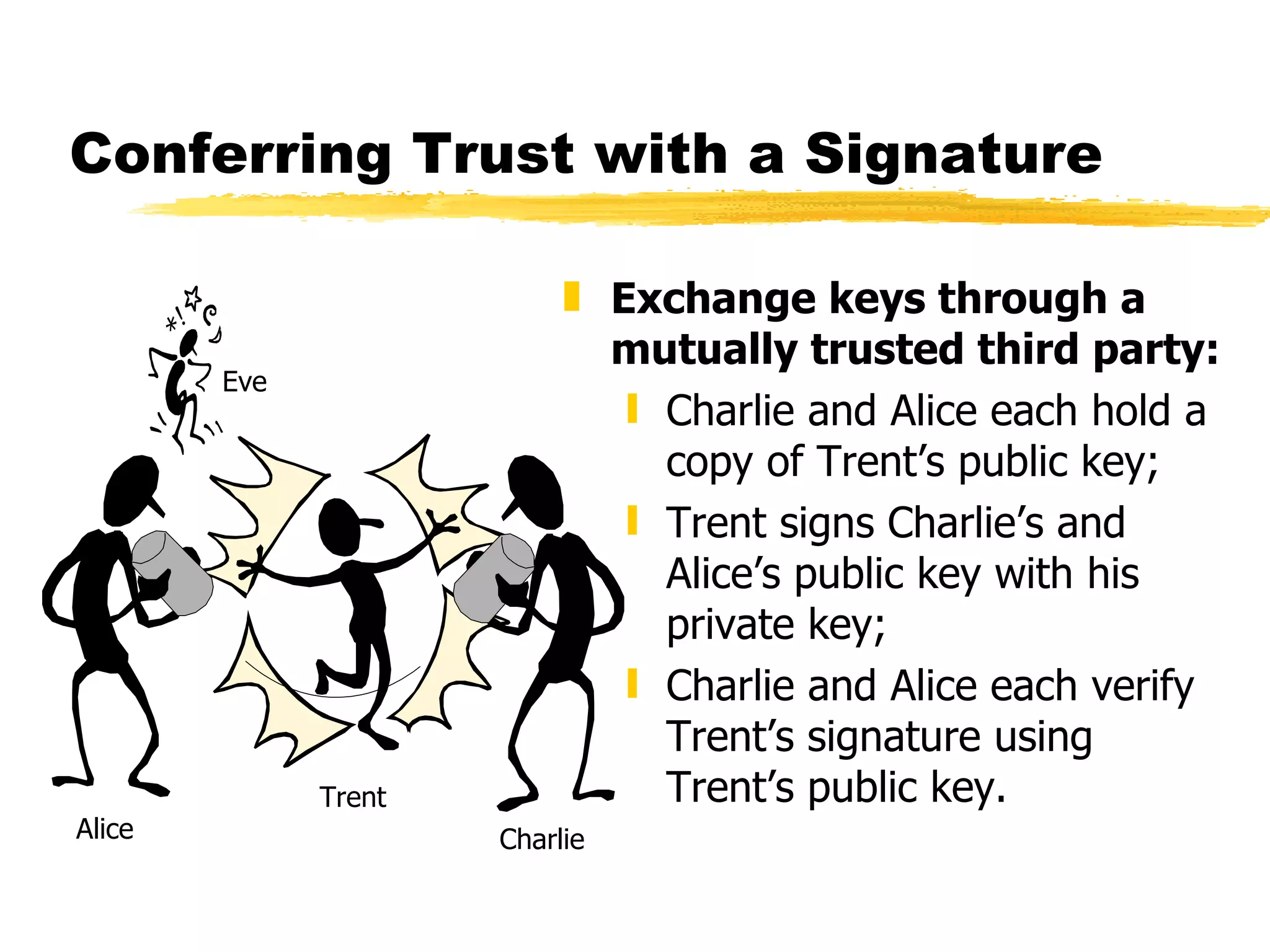
The document discusses the challenges of securing email communications in a distributed corporate network, highlighting vulnerabilities such as data theft and impersonation. It explains the use of public key encryption to ensure secure messaging and authenticate senders, while also addressing key management issues and the risks associated with poor practices. The document concludes by mentioning the evolution of encryption standards and provides a brief overview of the mathematical principles behind key generation and message encryption.







![If you really want to know ... Find two very large primes, p and q. Find n=pq (the public modulus). Choose e, such that e < n and relatively prime to (p-1)(q-1). Compute d such that ed=1[mod (p-1)(q-1)]. e is the public exponent and d is the private one. The public key is (n,e), and the private key is (n,d). To encrypt, divide the target message into blocks smaller than n and perform modular exponentiation: c=m^e mod n Decryption is the inverse operation: m=c^d mod n … et Voila!](https://image.slidesharecdn.com/encryptionandemail-12676494584059-phpapp01/75/E-mail-and-Encryption-14-2048.jpg)