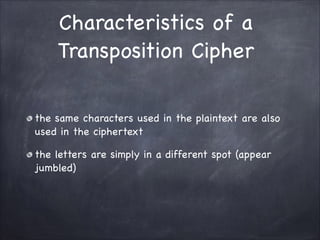
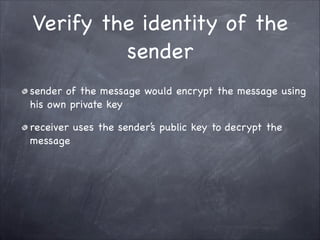
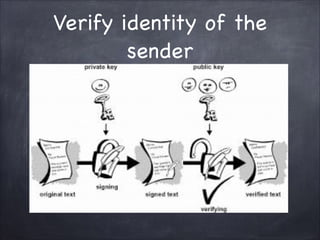
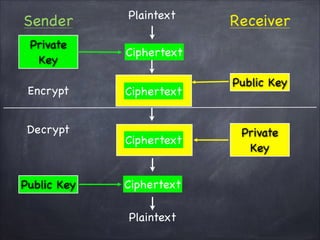
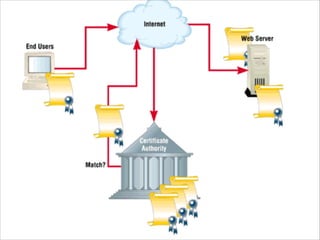
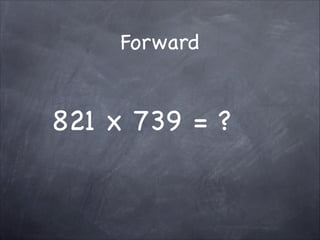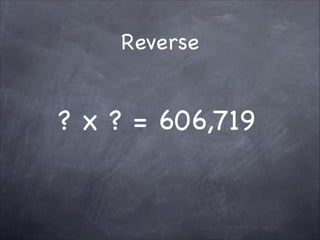The document provides an overview of cryptography, detailing classical ciphers like transposition and substitution methods, and highlighting modern techniques such as asymmetric cryptography and hybrid systems. It explains the intricacies of mechanisms like the Vigenère cipher and RSA encryption, emphasizing the mathematical underpinnings of key exchanges and encryption methods. Additionally, it discusses the roles of digital signatures and certificate authorities in ensuring authenticity and integrity in digital communications.