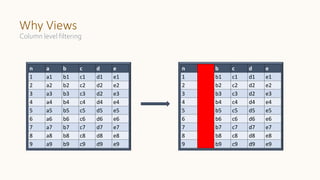
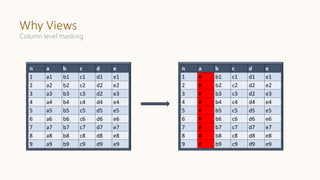
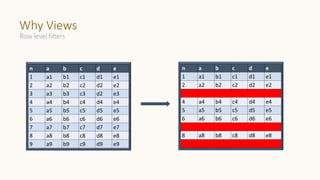
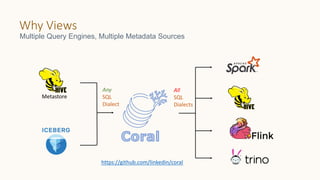
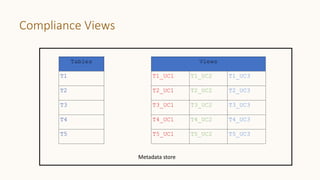
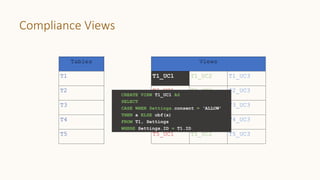
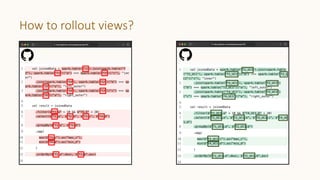
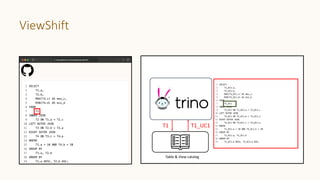
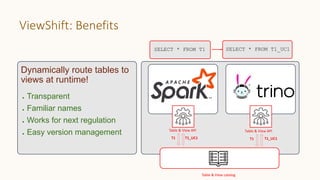
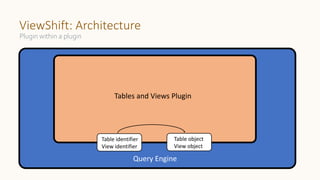
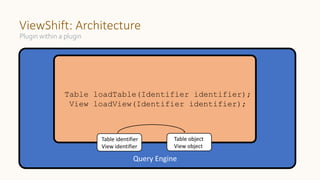
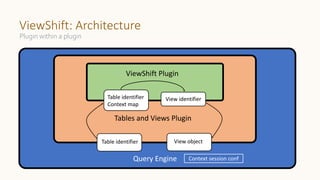
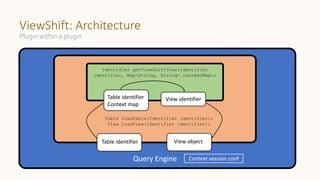
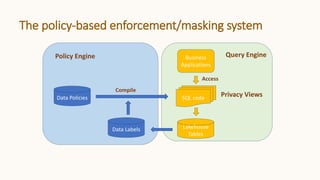
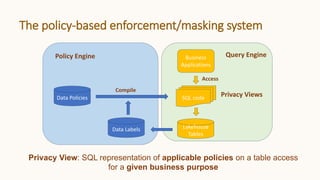
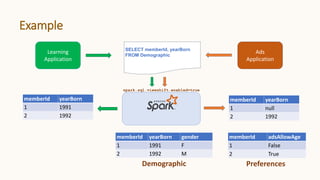
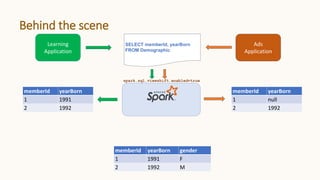
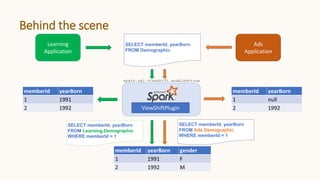
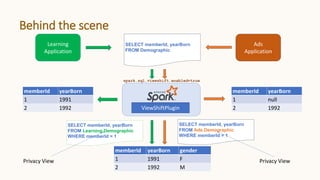
The document introduces 'Viewshift', a system designed for dynamic policy enforcement in data lakes, addressing the complexities of data compliance such as GDPR and CCPA. It emphasizes the use of expressive SQL views that enable column-level filtering, masking, and compliance management, while allowing for easy rollout and versioning of policies. The architecture facilitates seamless integration with various SQL engines, enhancing the agility of data governance in a decentralized data environment.





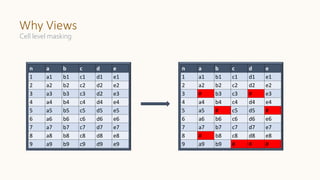




![Label: AGE
Rule:
if adsAllowAge:
KEEP
else:
ERASE
Label: AGE
Rule:
if adsAllowAge:
KEEP
else:
ERASE
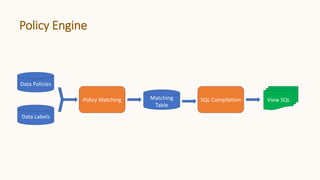
Policy Engine Example – Policy Matching
Purpose: Ads
Label: AGE
Rule:
if adsAllowAge:
KEEP
else:
ERASE
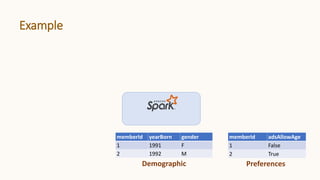
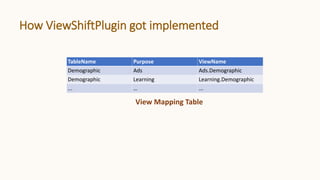
TableName Field Label
Demographic memberId KEY
Demographic yearBorn AGE
Demographic gender GENDER
Data Labels
TableName Purpose ApplicablePolicies
Demographic Ads [{"Field":"yearBorn",
"Policy":"AdsPolicyForAge"}]
Demographic Learning []
AdsPolicyForAge
Matching Table](https://image.slidesharecdn.com/viewshift-slides-240608185613-a8e9de75/85/ViewShift-Hassle-free-Dynamic-Policy-Enforcement-for-Every-Data-Lake-39-320.jpg)
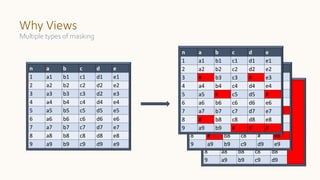
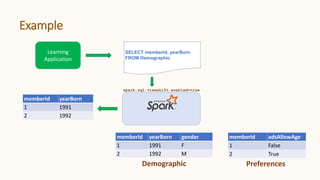
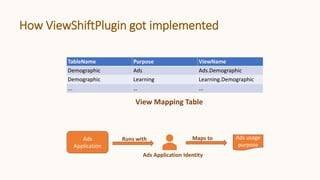
![Policy Engine Example – SQL compilation
TableName Purpose ApplicablePolicies
Demographic Ads [{"Field":"yearBorn",
"Policy":"AdsPolicyForAge"}]
Demographic Learning []
Matching Table
SELECT
memberId,
CASE
WHEN HAS_CONSENT(memberId, "adsAllowAge") THEN yearBorn
ELSE NULL
END as yearBorn,
gender
FROM Demographic
Ads.Demographic
SELECT *
FROM Demographic
Learning.Demographic
Purpose: Ads
Label: AGE
Rule:
if adsAllowAge:
KEEP
else:
ERASE](https://image.slidesharecdn.com/viewshift-slides-240608185613-a8e9de75/85/ViewShift-Hassle-free-Dynamic-Policy-Enforcement-for-Every-Data-Lake-40-320.jpg)
![Policy Engine Example – SQL compilation
TableName Purpose ApplicablePolicies
Demographic Ads [{"Field":"yearBorn",
"Policy":"AdsPolicyForAge"}]
Demographic Learning []
Matching Table
SELECT
memberId,
CASE
WHEN HAS_CONSENT(memberId, "adsAllowAge") THEN yearBorn
ELSE NULL
END as yearBorn,
gender
FROM Demographic
Ads.Demographic
SELECT *
FROM Demographic
Learning.Demographic
Purpose: Ads
Label: AGE
Rule:
if adsAllowAge:
KEEP
else:
ERASE
HAS_CONSENT(memberId: BIGIN,
consentName: VARCHAR):
Returns true iff memberId has consent
on consentName](https://image.slidesharecdn.com/viewshift-slides-240608185613-a8e9de75/85/ViewShift-Hassle-free-Dynamic-Policy-Enforcement-for-Every-Data-Lake-41-320.jpg)


