Workshop on Cryptography - Frequency Analysis (basic)
•
1 like•236 views
1) Substitution ciphers encrypt messages by replacing each letter in the plaintext with another letter according to a fixed mapping or key. The same key is required to decrypt the ciphertext back to the original plaintext. 2) Caesar ciphers are one of the earliest and simplest substitution ciphers, where each letter is shifted a fixed number of positions down the alphabet. While they allow secret communication, the encryption is weak and vulnerable to frequency analysis attacks. 3) Frequency analysis works by comparing the letter frequencies in the ciphertext to the expected frequencies in the language the plaintext was written in, like English. This reveals the most common letter mappings used in the simple substitution cipher key.
Report
Share
Report
Share
Download to read offline
Recommended
Basic encryption

Cryptography is the study of encrypting information to make it unreadable without authorization. Encryption uses a cipher and key to encode data, hiding its original content. The encrypted data is transmitted and then decrypted at the destination using the same key and cipher to restore the original data. Early forms of encryption included simple substitution ciphers. Modern encryption encrypts data like ATM pins into binary and uses algorithms to encrypt it during transmission, ensuring privacy over insecure networks.
E-mail and Encryption

An old presentation describing one possible implementation of public key or asymmetric cryptography to secure e-mail traffic across public networks.
Cryptography And Secure Systems

The document discusses what it means for a system to be secure and how cryptography is used to build trust in systems. It defines security goals like confidentiality, integrity, authentication, and non-repudiation. It explains how cryptographic techniques like encryption, hashing, digital signatures, and certificates can provide these security properties. Finally, it stresses that the security of a system depends on the strength of the underlying cryptographic tools and protocols used.
Ccn

This document provides an overview of cryptography and security. It discusses symmetric and asymmetric cryptography, comparing their basic approaches. Symmetric cryptography uses the same key for encryption and decryption, while asymmetric cryptography uses different public and private keys. The document also defines basic cryptography terms like plain text, cipher text, and encryption/decryption. It describes traditional substitution and transposition ciphers as well as modern symmetric and asymmetric techniques. The goal is to maintain data security, confidentiality, authentication, and integrity through the appropriate use of encryption.
Symmetric & Asymmetric Cryptography

This document summarizes symmetric and asymmetric cryptography. Symmetric cryptography involves both parties agreeing on an encryption algorithm and key beforehand to encrypt and decrypt messages. Asymmetric cryptography uses public and private key pairs, where the public key encrypts messages and the private key decrypts them, allowing encryption without pre-sharing keys. It also discusses digital signatures, where messages are signed with a private key and verified with the corresponding public key. Common attacks on public-key cryptography like man-in-the-middle attacks are addressed. The document is intended for a computer science course on cryptography fundamentals and security mechanisms.
Symmetric and Asymmetric Encryption

Symmetric and asymmetric encryption are two methods used to secure information online. Symmetric encryption uses a shared private key between sender and receiver, while asymmetric encryption uses a public/private key pair. Symmetric encryption is simpler but asymmetric is more secure as private keys are not shared. Modern encryption often uses a combination of both methods, with symmetric encryption for bulk data and asymmetric to securely exchange the symmetric keys. Encryption techniques continue to evolve with new algorithms to outpace cyber criminals trying to access protected information.
Whatisdigitalsignature

Digital Signature within 3 Hours
www.signyourdoc.com
Kind Regards
kishan
BDM, signyourdoc
signyourdoc.com
9571333822
8385010532
Homework1

Encryption works by using keys to scramble data so it can only be read by the intended recipient. There are two main types of encryption: symmetric key encryption which uses the same key to encrypt and decrypt by both parties, and public key encryption which uses two different keys, a private key known only to the recipient and a public key to encrypt data. Examples of encryption in use include the ancient Spartans using wooden cylinders to encrypt messages and websites using SSL/TLS protocols that replace "http" with "https" and display a padlock icon to show an encrypted secure connection.
Recommended
Basic encryption

Cryptography is the study of encrypting information to make it unreadable without authorization. Encryption uses a cipher and key to encode data, hiding its original content. The encrypted data is transmitted and then decrypted at the destination using the same key and cipher to restore the original data. Early forms of encryption included simple substitution ciphers. Modern encryption encrypts data like ATM pins into binary and uses algorithms to encrypt it during transmission, ensuring privacy over insecure networks.
E-mail and Encryption

An old presentation describing one possible implementation of public key or asymmetric cryptography to secure e-mail traffic across public networks.
Cryptography And Secure Systems

The document discusses what it means for a system to be secure and how cryptography is used to build trust in systems. It defines security goals like confidentiality, integrity, authentication, and non-repudiation. It explains how cryptographic techniques like encryption, hashing, digital signatures, and certificates can provide these security properties. Finally, it stresses that the security of a system depends on the strength of the underlying cryptographic tools and protocols used.
Ccn

This document provides an overview of cryptography and security. It discusses symmetric and asymmetric cryptography, comparing their basic approaches. Symmetric cryptography uses the same key for encryption and decryption, while asymmetric cryptography uses different public and private keys. The document also defines basic cryptography terms like plain text, cipher text, and encryption/decryption. It describes traditional substitution and transposition ciphers as well as modern symmetric and asymmetric techniques. The goal is to maintain data security, confidentiality, authentication, and integrity through the appropriate use of encryption.
Symmetric & Asymmetric Cryptography

This document summarizes symmetric and asymmetric cryptography. Symmetric cryptography involves both parties agreeing on an encryption algorithm and key beforehand to encrypt and decrypt messages. Asymmetric cryptography uses public and private key pairs, where the public key encrypts messages and the private key decrypts them, allowing encryption without pre-sharing keys. It also discusses digital signatures, where messages are signed with a private key and verified with the corresponding public key. Common attacks on public-key cryptography like man-in-the-middle attacks are addressed. The document is intended for a computer science course on cryptography fundamentals and security mechanisms.
Symmetric and Asymmetric Encryption

Symmetric and asymmetric encryption are two methods used to secure information online. Symmetric encryption uses a shared private key between sender and receiver, while asymmetric encryption uses a public/private key pair. Symmetric encryption is simpler but asymmetric is more secure as private keys are not shared. Modern encryption often uses a combination of both methods, with symmetric encryption for bulk data and asymmetric to securely exchange the symmetric keys. Encryption techniques continue to evolve with new algorithms to outpace cyber criminals trying to access protected information.
Whatisdigitalsignature

Digital Signature within 3 Hours
www.signyourdoc.com
Kind Regards
kishan
BDM, signyourdoc
signyourdoc.com
9571333822
8385010532
Homework1

Encryption works by using keys to scramble data so it can only be read by the intended recipient. There are two main types of encryption: symmetric key encryption which uses the same key to encrypt and decrypt by both parties, and public key encryption which uses two different keys, a private key known only to the recipient and a public key to encrypt data. Examples of encryption in use include the ancient Spartans using wooden cylinders to encrypt messages and websites using SSL/TLS protocols that replace "http" with "https" and display a padlock icon to show an encrypted secure connection.
Crypt

The document discusses cryptography and the RSA encryption algorithm. It begins with an introduction to cryptography and its uses. It then covers the history of cryptography, common security issues, and different cryptographic techniques like symmetric and asymmetric encryption. The document focuses on explaining the RSA algorithm, how it works using public and private keys, and why factoring large numbers makes RSA secure. It provides an overview of the key aspects of cryptography and the RSA algorithm.
Ss

Encryption works by encoding information before it is transmitted to protect sensitive data like passwords and personal information. There are two main types of encryption: symmetric-key encryption where both computers use the same secret key, and public-key encryption which uses different keys for encryption and decryption. Encryption along with authentication, which verifies the source and integrity of information, provide security for data transmitted over the internet and between computers.
Criptography

This document provides an overview of cryptography. It discusses traditional cryptography techniques like the Caesar cipher and shift ciphers. It also explains symmetric and asymmetric key cryptography, giving examples like DES, RSA, and their uses. Cryptographic services like authentication, data integrity, non-repudiation, and confidentiality are mentioned. The document notes how cryptography is widely used today in network security, banking transactions, and military communications.
Crypto

• What is cryptography?
• Why it’s helpful in a network and how hackers broke security?
• Different methods of encryption and decryption?
Network Security

This document provides an overview of computer security concepts, including risks, authentication, encryption, public key cryptography, wireless network security, and hacking tools and techniques. It discusses how attackers can sniff network traffic, crack wireless encryption, scan for vulnerabilities, and use social engineering to compromise systems. The document recommends maintaining up-to-date software, using strong passwords, limiting network access, and backing up data to help secure systems from potential threats.
Cryptography intro

Cryptography involves encrypting plaintext data into ciphertext using encryption algorithms and keys. Conventional cryptography uses a single secret key for both encryption and decryption, while public key cryptography uses separate public and private keys. The combination of these methods in hybrid cryptosystems like PGP provides both the speed of conventional encryption and the key distribution benefits of public key cryptography.
Information Security

The key to information security is protecting information and information systems from unauthorized access through various means. Some common methods of securing information include encryption, authentication, passwords, digital signatures, and controlling access. Public key encryption uses a private and public key system where the private key is known only to the user and the public key can be shared more widely. Encryption scrambles data using an algorithm and key to make it unreadable without the proper key.
enkripsi and authentication

1) Symmetric-key cryptography uses the same key to encrypt and decrypt data but requires a secure way to share the secret key between parties.
2) Public-key cryptography addresses this issue by using different but mathematically linked public and private keys, allowing secure communication without pre-shared keys.
3) Digital signatures use public-key cryptography to authenticate senders, working by encrypting a digest of the message with the sender's private key that can be decrypted and verified using their public key.
Secret-Key-Cryptography-ppt-by-alljobs.co_.in_.pptx

This document discusses secret key cryptography. Secret key cryptography uses the same key to encrypt and decrypt messages. It provides examples of simple substitution ciphers and discusses algorithms like AES, 3DES, and RC4. The document outlines the uses of secret key cryptography for secure communication when both parties have the shared key. It also discusses the advantages of speed and disadvantages of needing to keep the shared key secret.
Caesar cipher

Our team worked on a Cryptography project. Our project was designed to convert a normal message or text to private and secure cipher text to maintain confidentiality and security in both corporate and national security. Here the plain text is converted into cipher text through a web platform where the user submits the confidential plain text and get the cipher text for the corresponding plain text.
cryptography presentation this about how cryptography works

Cryptography is the process of encrypting information to hide its meaning and involves techniques like cipher systems that scramble letters and numbers. Different encryption methods have been used throughout history from simple substitution ciphers like the Caesar cipher used by Julius Caesar to modern techniques relying on complex mathematics. Alan Turing helped crack the German Enigma code during World War II by designing the bombe machine to determine the settings of the Enigma rotors and help decrypt messages.
Cryptography

The document provides information about the members of a group - Abdullah Rashid Baig, Adnan Haider, Muhammad Zakria, and Muhammad Zeeshan Khan. It then provides definitions and explanations of cryptography, cryptographic algorithms, encryption, decryption, plaintext, ciphertext, keys, secret key cryptography, public key cryptography, hashing, digital signatures, and security goals like confidentiality, authentication, integrity, availability, non-repudiation, and access control. It also discusses potential attacks on cryptography like viruses, traffic analysis, electromagnetic detection, and dictionary attacks.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and that the data hasn't been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and that the data hasn't been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and that the data hasn't been altered. Together, encryption and authentication create a secure online environment for sharing information.
encryption

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Encryption

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Our Journey: from Waterfall to Agile to DevOps

An overview of the recent changes in the IT industry from the point of view of Software Development. How modern companies are transitioning from old methodologies to newer ones to adapt to the new business models.
Development & GDPR (v2)

The document discusses the challenges of implementing the General Data Protection Regulation (GDPR) for an agile/DevOps organization. It provides an overview of key GDPR concepts like personal data, processing, controllers, processors, and territorial scope. It analyzes how these concepts impact software engineers and their work, for example requiring them to identify where data subjects are located and ensure purposes for data collection are specified. The document aims to explain GDPR in a practical way for technical teams to understand how it affects their work.
More Related Content
Similar to Workshop on Cryptography - Frequency Analysis (basic)
Crypt

The document discusses cryptography and the RSA encryption algorithm. It begins with an introduction to cryptography and its uses. It then covers the history of cryptography, common security issues, and different cryptographic techniques like symmetric and asymmetric encryption. The document focuses on explaining the RSA algorithm, how it works using public and private keys, and why factoring large numbers makes RSA secure. It provides an overview of the key aspects of cryptography and the RSA algorithm.
Ss

Encryption works by encoding information before it is transmitted to protect sensitive data like passwords and personal information. There are two main types of encryption: symmetric-key encryption where both computers use the same secret key, and public-key encryption which uses different keys for encryption and decryption. Encryption along with authentication, which verifies the source and integrity of information, provide security for data transmitted over the internet and between computers.
Criptography

This document provides an overview of cryptography. It discusses traditional cryptography techniques like the Caesar cipher and shift ciphers. It also explains symmetric and asymmetric key cryptography, giving examples like DES, RSA, and their uses. Cryptographic services like authentication, data integrity, non-repudiation, and confidentiality are mentioned. The document notes how cryptography is widely used today in network security, banking transactions, and military communications.
Crypto

• What is cryptography?
• Why it’s helpful in a network and how hackers broke security?
• Different methods of encryption and decryption?
Network Security

This document provides an overview of computer security concepts, including risks, authentication, encryption, public key cryptography, wireless network security, and hacking tools and techniques. It discusses how attackers can sniff network traffic, crack wireless encryption, scan for vulnerabilities, and use social engineering to compromise systems. The document recommends maintaining up-to-date software, using strong passwords, limiting network access, and backing up data to help secure systems from potential threats.
Cryptography intro

Cryptography involves encrypting plaintext data into ciphertext using encryption algorithms and keys. Conventional cryptography uses a single secret key for both encryption and decryption, while public key cryptography uses separate public and private keys. The combination of these methods in hybrid cryptosystems like PGP provides both the speed of conventional encryption and the key distribution benefits of public key cryptography.
Information Security

The key to information security is protecting information and information systems from unauthorized access through various means. Some common methods of securing information include encryption, authentication, passwords, digital signatures, and controlling access. Public key encryption uses a private and public key system where the private key is known only to the user and the public key can be shared more widely. Encryption scrambles data using an algorithm and key to make it unreadable without the proper key.
enkripsi and authentication

1) Symmetric-key cryptography uses the same key to encrypt and decrypt data but requires a secure way to share the secret key between parties.
2) Public-key cryptography addresses this issue by using different but mathematically linked public and private keys, allowing secure communication without pre-shared keys.
3) Digital signatures use public-key cryptography to authenticate senders, working by encrypting a digest of the message with the sender's private key that can be decrypted and verified using their public key.
Secret-Key-Cryptography-ppt-by-alljobs.co_.in_.pptx

This document discusses secret key cryptography. Secret key cryptography uses the same key to encrypt and decrypt messages. It provides examples of simple substitution ciphers and discusses algorithms like AES, 3DES, and RC4. The document outlines the uses of secret key cryptography for secure communication when both parties have the shared key. It also discusses the advantages of speed and disadvantages of needing to keep the shared key secret.
Caesar cipher

Our team worked on a Cryptography project. Our project was designed to convert a normal message or text to private and secure cipher text to maintain confidentiality and security in both corporate and national security. Here the plain text is converted into cipher text through a web platform where the user submits the confidential plain text and get the cipher text for the corresponding plain text.
cryptography presentation this about how cryptography works

Cryptography is the process of encrypting information to hide its meaning and involves techniques like cipher systems that scramble letters and numbers. Different encryption methods have been used throughout history from simple substitution ciphers like the Caesar cipher used by Julius Caesar to modern techniques relying on complex mathematics. Alan Turing helped crack the German Enigma code during World War II by designing the bombe machine to determine the settings of the Enigma rotors and help decrypt messages.
Cryptography

The document provides information about the members of a group - Abdullah Rashid Baig, Adnan Haider, Muhammad Zakria, and Muhammad Zeeshan Khan. It then provides definitions and explanations of cryptography, cryptographic algorithms, encryption, decryption, plaintext, ciphertext, keys, secret key cryptography, public key cryptography, hashing, digital signatures, and security goals like confidentiality, authentication, integrity, availability, non-repudiation, and access control. It also discusses potential attacks on cryptography like viruses, traffic analysis, electromagnetic detection, and dictionary attacks.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and that the data hasn't been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and that the data hasn't been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Amazon

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and that the data hasn't been altered. Together, encryption and authentication create a secure online environment for sharing information.
encryption

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Encryption

Computer encryption uses cryptography to secure online transactions. There are two main types of encryption: symmetric-key encryption where both computers share the same key, and public-key encryption which uses different keys for encryption and decryption. Encryption encodes data during transmission while authentication verifies the identity of the sender and confirms the data has not been altered. Together, encryption and authentication create a secure online environment for sharing information.
Similar to Workshop on Cryptography - Frequency Analysis (basic) (20)
Secret-Key-Cryptography-ppt-by-alljobs.co_.in_.pptx

Secret-Key-Cryptography-ppt-by-alljobs.co_.in_.pptx
cryptography presentation this about how cryptography works

cryptography presentation this about how cryptography works
More from Andrea Tino
Our Journey: from Waterfall to Agile to DevOps

An overview of the recent changes in the IT industry from the point of view of Software Development. How modern companies are transitioning from old methodologies to newer ones to adapt to the new business models.
Development & GDPR (v2)

The document discusses the challenges of implementing the General Data Protection Regulation (GDPR) for an agile/DevOps organization. It provides an overview of key GDPR concepts like personal data, processing, controllers, processors, and territorial scope. It analyzes how these concepts impact software engineers and their work, for example requiring them to identify where data subjects are located and ensure purposes for data collection are specified. The document aims to explain GDPR in a practical way for technical teams to understand how it affects their work.
Development & GDPR

The document discusses the challenges that organizations face in implementing the General Data Protection Regulation (GDPR) from the perspective of developers. It provides an overview of key GDPR concepts like personal data and processing. It analyzes how GDPR impacts processes and software architecture in organizations pursuing agile and DevOps practices. The document aims to explain GDPR in a practical way for engineers and development managers by highlighting relevant articles and their implications for technical challenges in building compliant systems.
Cutting Edge on Development Methodologies in IT

The document provides an overview of the evolution of software development methodologies from Waterfall to Agile and DevOps. It discusses how software development moved from a sequential Waterfall model to iterative Agile methodologies as business needs changed and requirements became more dynamic. It then explains how DevOps further merged development and operations teams to enable continuous delivery in highly connected, microservices-based architectures needed to support modern digital businesses. Key practices like continuous integration, delivery, infrastructure as code, and monitoring are also summarized.
An introduction to DevOps

DevOps is a practice that aims to break down barriers between development and operations teams. It originated as teams adopted Agile methodologies and moved toward continuous delivery of software. DevOps aims to speed up delivery through practices like continuous integration, infrastructure as code, and breaking down silos between teams. The document outlines the history and benefits of DevOps, including increased speed, reliability, collaboration and security. It also defines key DevOps practices and provides examples of how they work.
Continuous Everything

The document discusses methodologies for implementing DevOps in an organization, focusing on Continuous Integration (CI), Continuous Delivery (CD), and Continuous Deployment (CDP). It defines each practice and describes the typical architecture and workflows. CI automates building and testing code changes. CD further automates deploying to pre-production environments. CDP fully automates deploying to production. The document warns that CDP is risky and an organization must be prepared with capabilities like fast deployment rollbacks and monitoring before implementing it.
Modern Trends in UI Decoupling Design

UI designers and developers have evolved over time to better separate user interfaces from code and business logic. Early approaches mixed interfaces and code together (Mesozoic era), while later approaches separated code and interfaces but not fully (Paleolithic era). Modern approaches use frameworks to fully decouple and isolate interfaces, styles, and code (Modern era) through techniques like CSS Modules, which allow encapsulation of styles and protection from interference between components. This achieves the full benefits of decoupling for both designers and developers.
Javascript cheatsheet

This document introduces some basic concepts in JavaScript including variables, data types, flow control, and functions. Variables are used to store and retrieve values and are fundamental building blocks. JavaScript supports basic types like strings and numbers. Flow control allows executing code conditionally using if/else statements and loops. Functions help modularize and reuse code by defining pieces of code that can be called multiple times.
Master Thesis - A Distributed Algorithm for Stateless Load Balancing

The algorithm object of this thesis deals with the problem of balancing data units
across different stations in the context of storing large amounts of information in
data stores or data centres. The approaches being used today are mainly based on
employing a central balancing node which often requires information from the different
stations about their load state.
The algorithm being proposed here follows the opposite strategy for which data is
balanced without the use of any centralized balancing unit, thus fulfilling the distributed
property, and without gathering any information from stations about their
current load state, thus the stateless property.
This document will go through the details of the algorithm by describing the idea
and the mathematical principles behind it. By means of an analytical proof, the equation
of balancing will be devised and introduced. Later on, tests and simulations,
carried on by means of different environments and technologies, will illustrate the
effectiveness of the approach. Results will be introduced and discussed in the second
part of this document together with final notes about current state of art, challenges
and deployment considerations in real scenarios.
Modern web applications

Web applications are software based on web technologies like HTML, JavaScript, and CSS that offer functionality similar to native applications. Languages that compile to JavaScript and CSS can help make codebases more maintainable by adding features like types, object-oriented programming, and variables. Web applications can be distributed both as websites running in browsers and as mobile/desktop apps by using technologies like Node.js and Cordova. Testing and automation of web applications is also possible using frameworks like Jasmine, Selenium, and Appium.
Visual Studio Tools for Cordova

An overview of the new features in Visual Studio 2015 for developing cross platform apps with Cordova.
Microsoft + Agile (light)

Understanding how modern software is developed and how agile
methodologies are applied in Microsoft to deliver great products.
This version present topics in a lighter form and the presentation takes less time.
Microsoft + Agile

Understanding how modern software is developed and how agile
methodologies are applied in Microsoft to deliver great products.
The World of Stylesheet Languages

SASS is a CSS preprocessor that provides a more structured language for stylesheet development. It features include variables, nested rules, mixins, and functions that allow developers to write cleaner CSS code. SASS files can be compiled into normal CSS files. Using SASS improves code quality by reducing repetition and making stylesheets easier to maintain as projects increase in complexity. SASS also encourages separating CSS into multiple files based on components, media queries, or other logical structures to better organize the code.
How to Develop Cross-Platform Apps

A presentation about modern trends for developing cross-platform apps using Visual Studio and Cordova. The presentation targets beginners and covers topics not in detail. The objective is providing a generic overview.
The Asynchronous Pattern (for beginners)

The document discusses asynchronous programming patterns in JavaScript. Asynchronous programming was introduced to address the problem of synchronous functions blocking other code from executing while waiting for a long-running function to complete. Asynchronously calling a function allows the caller to continue execution immediately rather than waiting idly for the called function to finish. This improves performance over synchronous functions that require the caller to wait actively. The asynchronous model uses callbacks to retrieve the return value from an asynchronous function after it completes rather than blocking the caller thread.
Designing an effective hybrid apps automation framework

Best practices to design an hybrid-app automation framework with today’s de-facto standards: WebDriver, Selenium and Appium.
7 tips for more effective morning SCRUM

1) Morning scrum meetings can drag on if not properly managed. Changing the speaking order each day and having members voluntarily lead discussions can make meetings more dynamic.
2) When reporting status, team members should follow a consistent pattern of discussing work completed yesterday, work planned for today, and only bring up problems if help is needed from others.
3) If remote, send a pre-meeting email with your status. In meetings, keep reports brief and under 5 minutes, avoiding deep technical explanations unless necessary. Signaling "take it offline" prevents side conversations from dominating.
Powerful tools for building web solutions

A 360-degree overview of the most popular technologies in web development to boost your productivity.
Working with Agile technologies and SCRUM

The document provides an overview of Scrum and Agile methodologies for software development. It discusses key Scrum concepts like roles, events, artifacts, and tools used in the Scrum process. The roles in Scrum include the Product Owner, Development Team, and Scrum Master. Events include the Sprint, Sprint Planning meeting, Daily Scrum meeting, and Sprint Review meeting. Artifacts include Product and Sprint Backlogs, as well as Deliverables and Bugs. Tools discussed include Kanban boards, code review tools, changesets, and Microsoft's unit testing framework.
More from Andrea Tino (20)
Master Thesis - A Distributed Algorithm for Stateless Load Balancing

Master Thesis - A Distributed Algorithm for Stateless Load Balancing
Designing an effective hybrid apps automation framework

Designing an effective hybrid apps automation framework
Recently uploaded
KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions

K8sGPT is a tool that analyzes and diagnoses Kubernetes clusters. This presentation was used to share the requirements and dependencies to deploy K8sGPT in a local environment.
CHINA’S GEO-ECONOMIC OUTREACH IN CENTRAL ASIAN COUNTRIES AND FUTURE PROSPECT

The rivalry between prominent international actors for dominance over Central Asia's hydrocarbon
reserves and the ancient silk trade route, along with China's diplomatic endeavours in the area, has been
referred to as the "New Great Game." This research centres on the power struggle, considering
geopolitical, geostrategic, and geoeconomic variables. Topics including trade, political hegemony, oil
politics, and conventional and nontraditional security are all explored and explained by the researcher.
Using Mackinder's Heartland, Spykman Rimland, and Hegemonic Stability theories, examines China's role
in Central Asia. This study adheres to the empirical epistemological method and has taken care of
objectivity. This study analyze primary and secondary research documents critically to elaborate role of
china’s geo economic outreach in central Asian countries and its future prospect. China is thriving in trade,
pipeline politics, and winning states, according to this study, thanks to important instruments like the
Shanghai Cooperation Organisation and the Belt and Road Economic Initiative. According to this study,
China is seeing significant success in commerce, pipeline politics, and gaining influence on other
governments. This success may be attributed to the effective utilisation of key tools such as the Shanghai
Cooperation Organisation and the Belt and Road Economic Initiative.
ISPM 15 Heat Treated Wood Stamps and why your shipping must have one

For International shipping and maritime laws all wood must contain the ISPM 15 Stamp. Here is how and why.
哪里办理(csu毕业证书)查尔斯特大学毕业证硕士学历原版一模一样

原版一模一样【微信:741003700 】【(csu毕业证书)查尔斯特大学毕业证硕士学历】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
NATURAL DEEP EUTECTIC SOLVENTS AS ANTI-FREEZING AGENT

NATURAL DEEP EUTECTIC SOLVENTS AS ANTI-FREEZING AGENT
Computational Engineering IITH Presentation

This Presentation will give you a brief idea about what Computational Engineering at IIT Hyderabad has to offer.
Comparative analysis between traditional aquaponics and reconstructed aquapon...

The aquaponic system of planting is a method that does not require soil usage. It is a method that only needs water, fish, lava rocks (a substitute for soil), and plants. Aquaponic systems are sustainable and environmentally friendly. Its use not only helps to plant in small spaces but also helps reduce artificial chemical use and minimizes excess water use, as aquaponics consumes 90% less water than soil-based gardening. The study applied a descriptive and experimental design to assess and compare conventional and reconstructed aquaponic methods for reproducing tomatoes. The researchers created an observation checklist to determine the significant factors of the study. The study aims to determine the significant difference between traditional aquaponics and reconstructed aquaponics systems propagating tomatoes in terms of height, weight, girth, and number of fruits. The reconstructed aquaponics system’s higher growth yield results in a much more nourished crop than the traditional aquaponics system. It is superior in its number of fruits, height, weight, and girth measurement. Moreover, the reconstructed aquaponics system is proven to eliminate all the hindrances present in the traditional aquaponics system, which are overcrowding of fish, algae growth, pest problems, contaminated water, and dead fish.
Optimizing Gradle Builds - Gradle DPE Tour Berlin 2024

Sinan from the Delivery Hero mobile infrastructure engineering team shares a deep dive into performance acceleration with Gradle build cache optimizations. Sinan shares their journey into solving complex build-cache problems that affect Gradle builds. By understanding the challenges and solutions found in our journey, we aim to demonstrate the possibilities for faster builds. The case study reveals how overlapping outputs and cache misconfigurations led to significant increases in build times, especially as the project scaled up with numerous modules using Paparazzi tests. The journey from diagnosing to defeating cache issues offers invaluable lessons on maintaining cache integrity without sacrificing functionality.
LLM Fine Tuning with QLoRA Cassandra Lunch 4, presented by Anant

Slides for the 4th Presentation on LLM Fine-Tuning with QLoRA Presented by Anant, featuring DataStax Astra
Hematology Analyzer Machine - Complete Blood Count

The CBC machine is a common diagnostic tool used by doctors to measure a patient's red blood cell count, white blood cell count and platelet count. The machine uses a small sample of the patient's blood, which is then placed into special tubes and analyzed. The results of the analysis are then displayed on a screen for the doctor to review. The CBC machine is an important tool for diagnosing various conditions, such as anemia, infection and leukemia. It can also help to monitor a patient's response to treatment.
Unit-III-ELECTROCHEMICAL STORAGE DEVICES.ppt

Batteries -Introduction – Types of Batteries – discharging and charging of battery - characteristics of battery –battery rating- various tests on battery- – Primary battery: silver button cell- Secondary battery :Ni-Cd battery-modern battery: lithium ion battery-maintenance of batteries-choices of batteries for electric vehicle applications.
Fuel Cells: Introduction- importance and classification of fuel cells - description, principle, components, applications of fuel cells: H2-O2 fuel cell, alkaline fuel cell, molten carbonate fuel cell and direct methanol fuel cells.
Literature Review Basics and Understanding Reference Management.pptx

Three-day training on academic research focuses on analytical tools at United Technical College, supported by the University Grant Commission, Nepal. 24-26 May 2024
Casting-Defect-inSlab continuous casting.pdf

Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting. Casting-Defect-inSlab continuous casting
IEEE Aerospace and Electronic Systems Society as a Graduate Student Member

IEEE Aerospace and Electronic Systems Society as a Graduate Student Member
BRAIN TUMOR DETECTION for seminar ppt.pdf

BRAIN TUMOR DETECTION
AND CLASSIFICATION USING
ARTIFICIAL INTELLIGENCE
Recently uploaded (20)
KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions

KuberTENes Birthday Bash Guadalajara - K8sGPT first impressions
CHINA’S GEO-ECONOMIC OUTREACH IN CENTRAL ASIAN COUNTRIES AND FUTURE PROSPECT

CHINA’S GEO-ECONOMIC OUTREACH IN CENTRAL ASIAN COUNTRIES AND FUTURE PROSPECT
ISPM 15 Heat Treated Wood Stamps and why your shipping must have one

ISPM 15 Heat Treated Wood Stamps and why your shipping must have one
NATURAL DEEP EUTECTIC SOLVENTS AS ANTI-FREEZING AGENT

NATURAL DEEP EUTECTIC SOLVENTS AS ANTI-FREEZING AGENT
Comparative analysis between traditional aquaponics and reconstructed aquapon...

Comparative analysis between traditional aquaponics and reconstructed aquapon...
Optimizing Gradle Builds - Gradle DPE Tour Berlin 2024

Optimizing Gradle Builds - Gradle DPE Tour Berlin 2024
LLM Fine Tuning with QLoRA Cassandra Lunch 4, presented by Anant

LLM Fine Tuning with QLoRA Cassandra Lunch 4, presented by Anant
Hematology Analyzer Machine - Complete Blood Count

Hematology Analyzer Machine - Complete Blood Count
Literature Review Basics and Understanding Reference Management.pptx

Literature Review Basics and Understanding Reference Management.pptx
IEEE Aerospace and Electronic Systems Society as a Graduate Student Member

IEEE Aerospace and Electronic Systems Society as a Graduate Student Member
Introduction to AI Safety (public presentation).pptx

Introduction to AI Safety (public presentation).pptx
Workshop on Cryptography - Frequency Analysis (basic)
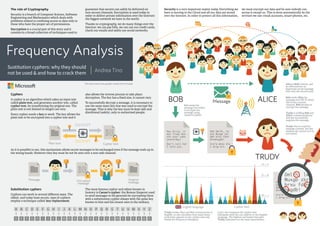
- 1. Sustitution cyphers: why they should not be used & and how to crack them Frequency Analysis Andrea Tino This document uses graphic assets from Freepik Cyphers A cypher is an algorithm which takes an input text called plain text, and generates another text, called cypher text, by transforming the priginal one. The plain text is not limited its length can vary. Every cypher needs a key to work. The key allows the plain text to be encrypted into a cypher text and it The role of Cryptography Security is a branch of Computer Science, So ware Engineering and Mathematics which deals with problems related to confining access to data only to those who have the proper set of permissions. Encryption is a crucial part of this story and it consists in a broad collection of techniques used to guarantee that secrets can safely be delivered on non-secure channels. Encryption is used today in order to deliver private information over the Internet: the biggest network we have in the world. Thanks to cryptography, we do many things over the Internet: we can pay bills, we can use our credit cards, check our emails and safely use social networks. Security is a very important ma er today. Everything we have is moving to the Cloud and all our data are stored over the Internet. In order to protect all this information, Substitution cyphers Cyphers can work in several different ways. The oldest, and today least secure, type of cyphers employ a technique called: key-replacement. also allows the reverse process to take place: decryption. The key has a fixed size, it cannot vary. To successfully decrypt a message, it is necessary to use the same exact key that was used to encrypt the message. That is why the key must be kept safe and distributed (safely), only to authorized people. The most famous cypher and oldest known in hostory is Caesar’s cypher: the Roman Emperor used to send messages to his generals by encrypting them with a substitution cypher always with the same key known to him and his closest men in the military. As it is possible to see, this mechanism allows secret messages to be exchanged even if the message ends up in the wrong hands. However they key must be not be sent over a non-safe channel. we must encrypt our data and be sure nobody can access it except us. This is done automatically by the services we use: email accounts, smart-phones, etc. A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A B CD E F G H I J K L M N O P Q R S T U V W X Y Z Plain text #$%!?+0^!@ ?+0^!!?+0^ !@?+0^!?+0 ^!@?+0^!!@ #$%!!?+0^! Cypher text ENCRYPT DECRYPT ALICEBOB Message Message #$%!?+0^!@ ?+0^!!?+0^ !@?+0^!?+0 ^!@?+0^!!@ #$%!!?+0^! Encrypted message Original message TRUDY Hey Alice, it was Trudy who ate your cake yesterday! Don’t tell her I told you. Khb Dmlfh, lw zdv Wuxgb zkr dwh brxu fdnh bhvwhugdb! Grq’w whoo khu L wrog brx. Bob sends the message but before it encrypts the message using Caesar’s Cypher. Khb Dmlfh, lw zdv Wuxgb zkr dwh brxu fdnh bhvwhugdb! Grq’w whoo khu L wrog brx. Khb Dmlfh, lw zdv Wuxgb zkr dwh brxu fdnh bhvwhugdb! Grq’w whoo khu L wrog brx. Bob sends Alice the message over Wi-Fi. Since this is not a secure channel, Bob decides to encrypt the message. Trudy is sniffing Bob and Alice’s communications and she successfully acquires the message. Alice is Bob’s friend, and he will send her an important secret message that only she should read. Trudy tries to read the message content, but she realizes she cannot as it is encrypted. E F G H J MA B C DE F G I J OA B C D English language Cypher text D = A H = E M = J Trudy knows Alice and Bob communicate in English, so she calculates how many times each le er appears in the cypher-text and builds the frequency histogram. Later, she compares the cypher-text histogram with the one relative to the English language. The highest and lowest bars give Trudy indication on the main associations.
