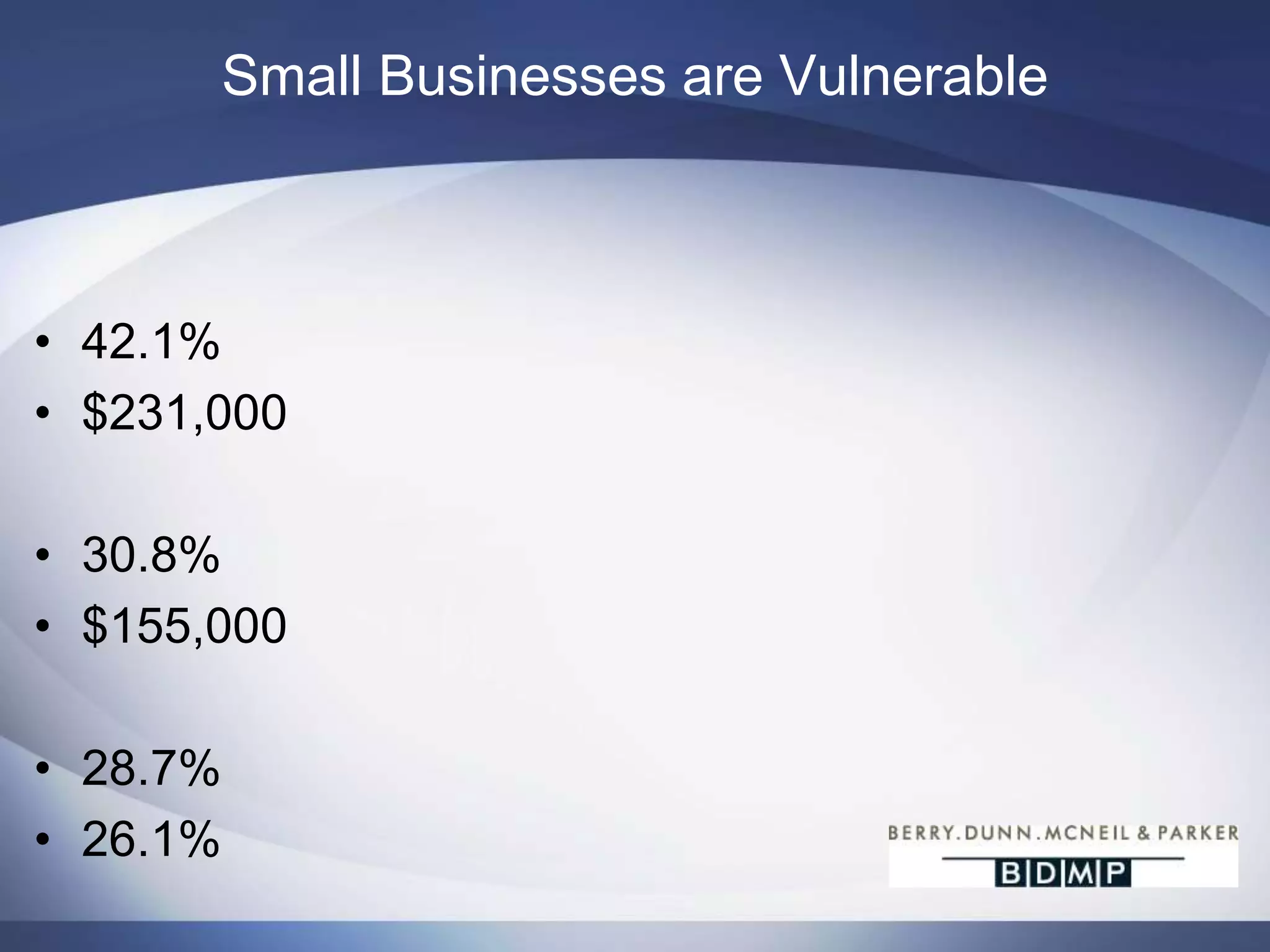
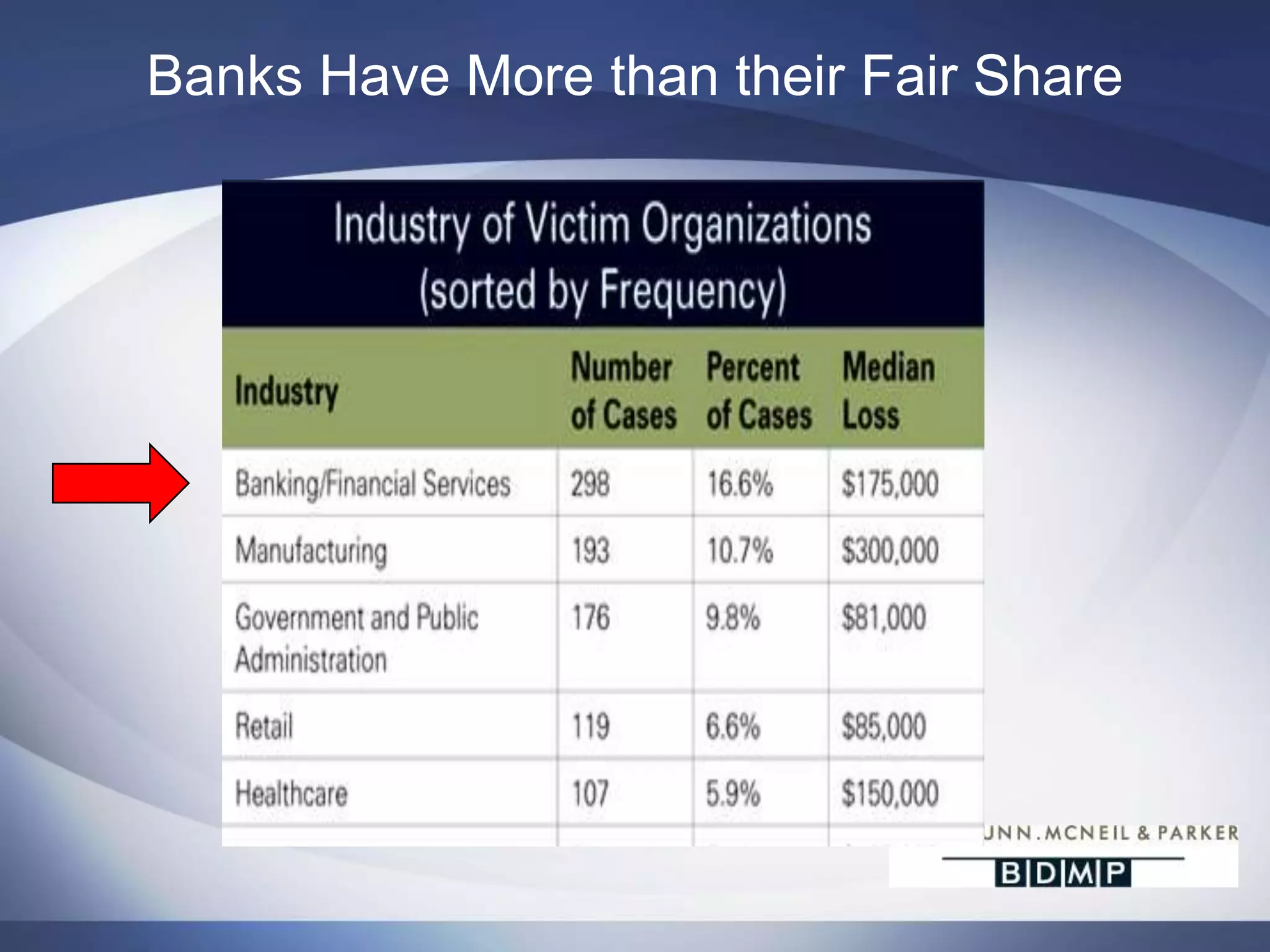
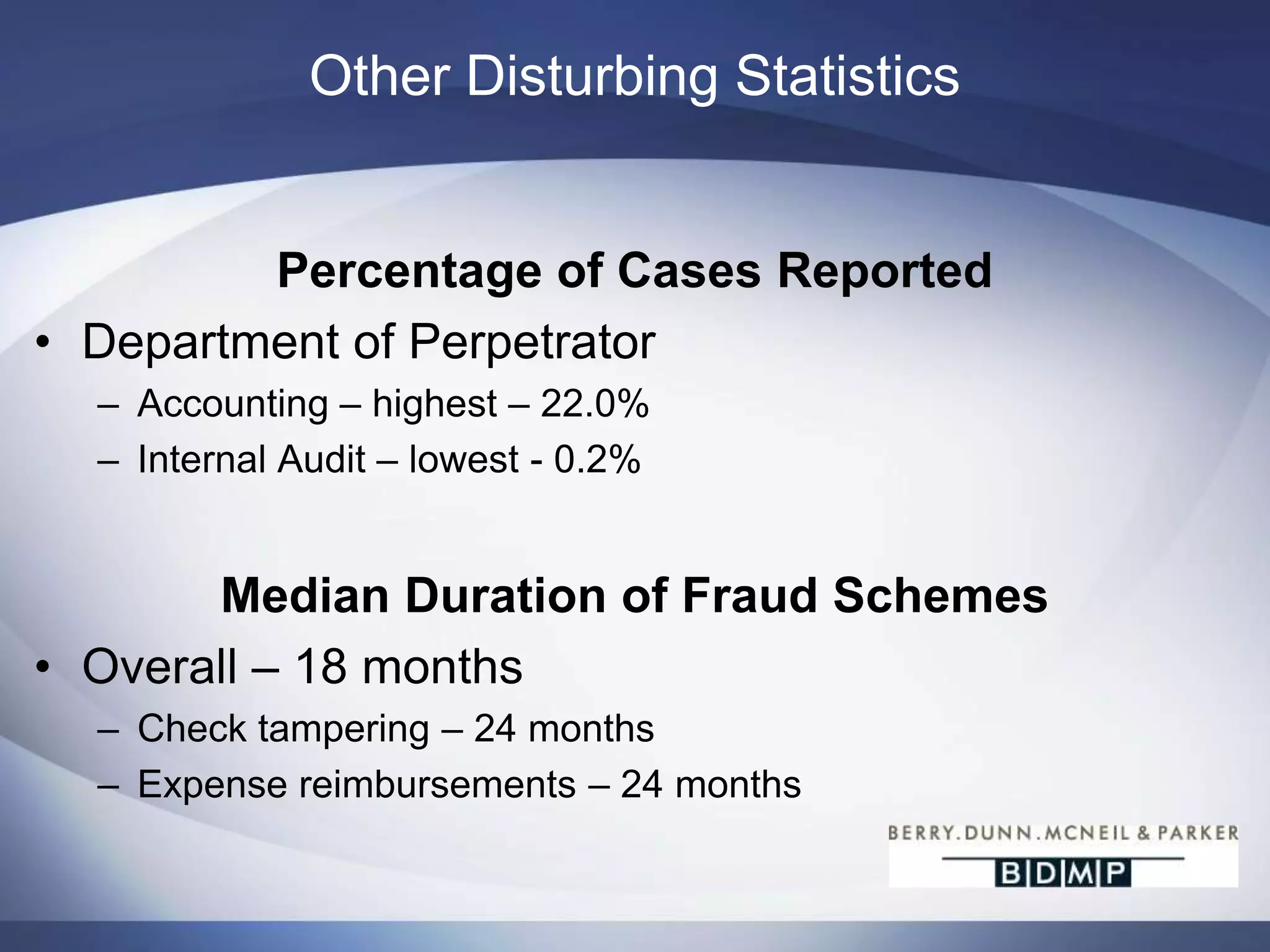
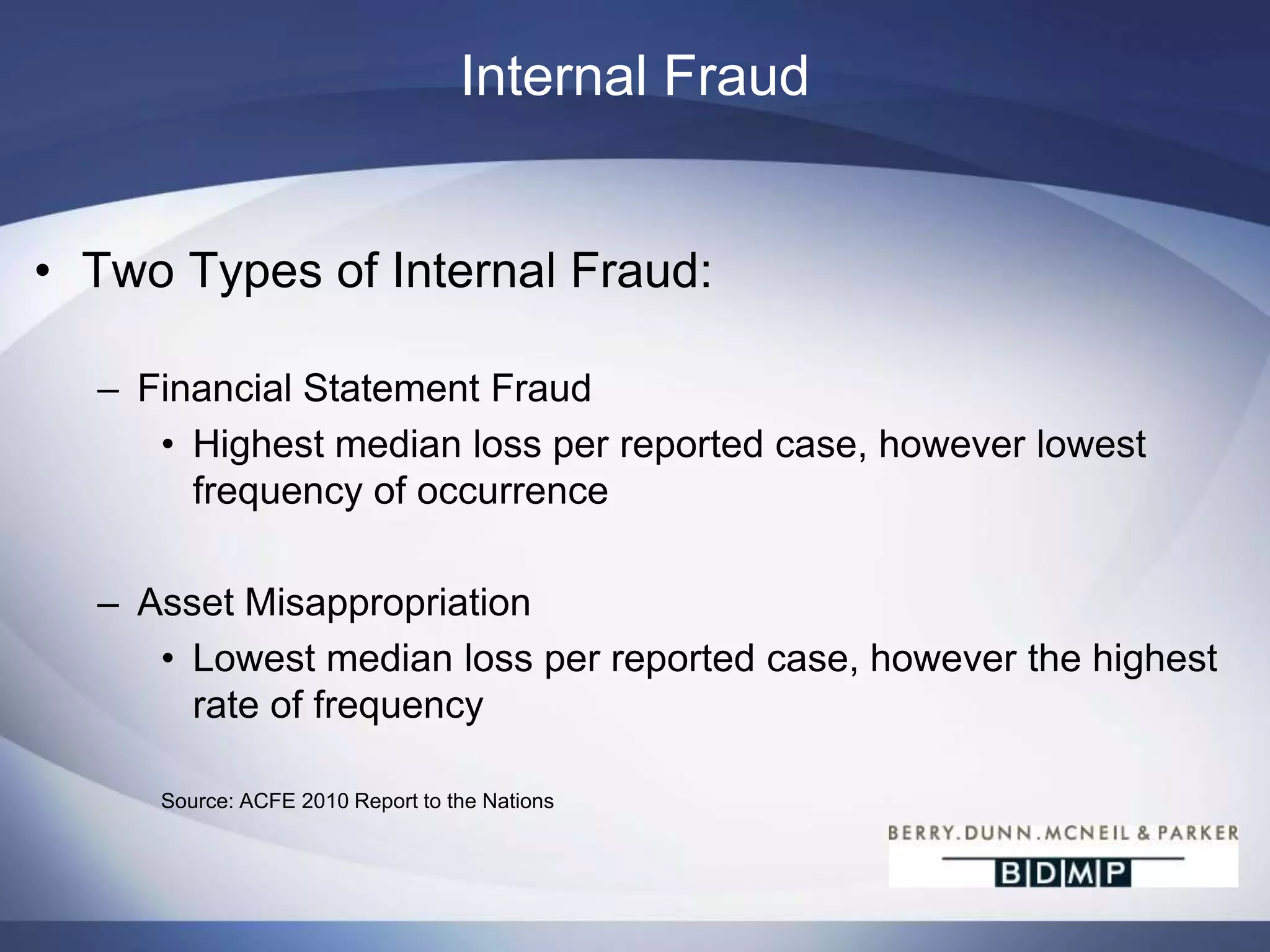
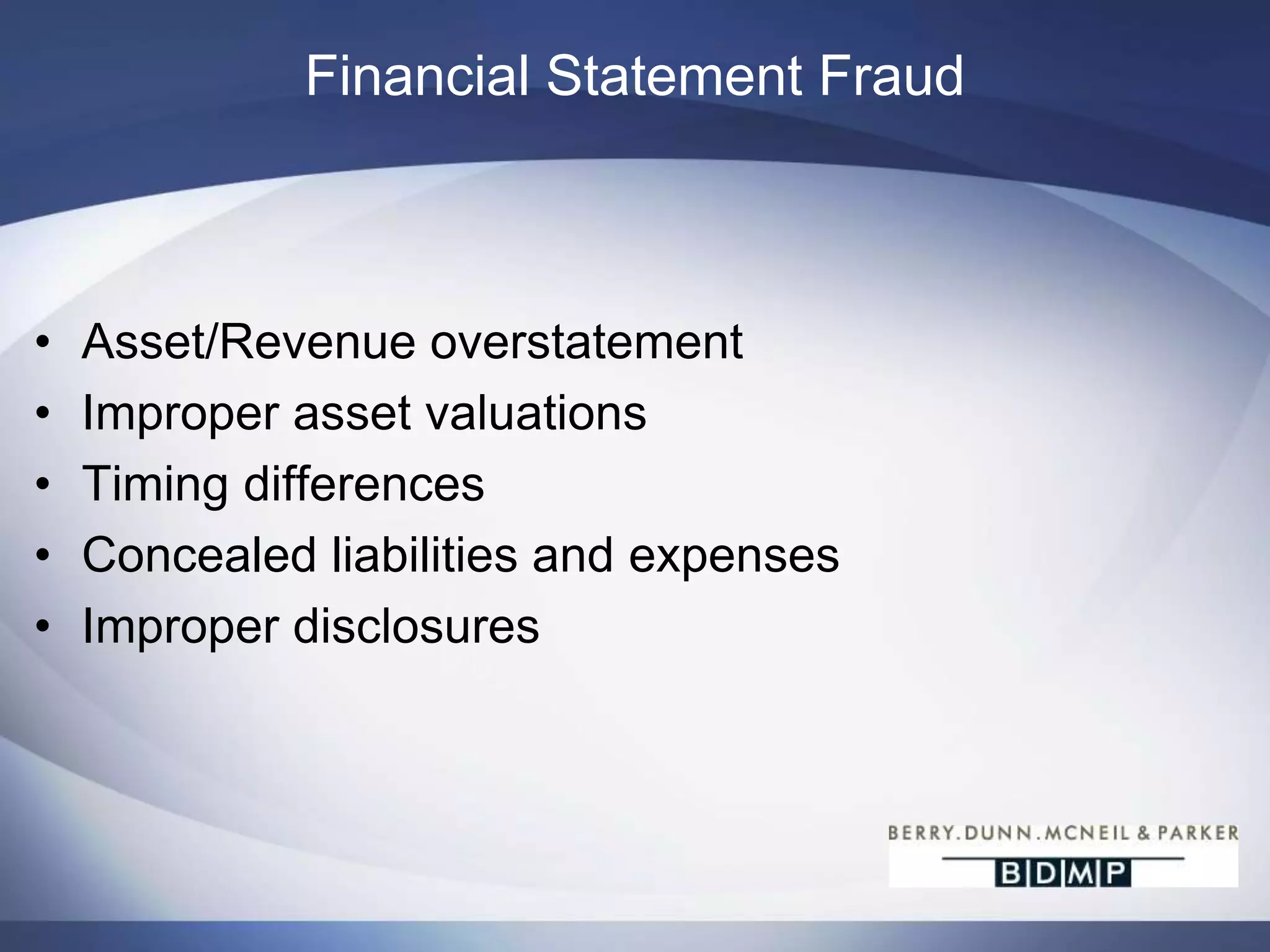
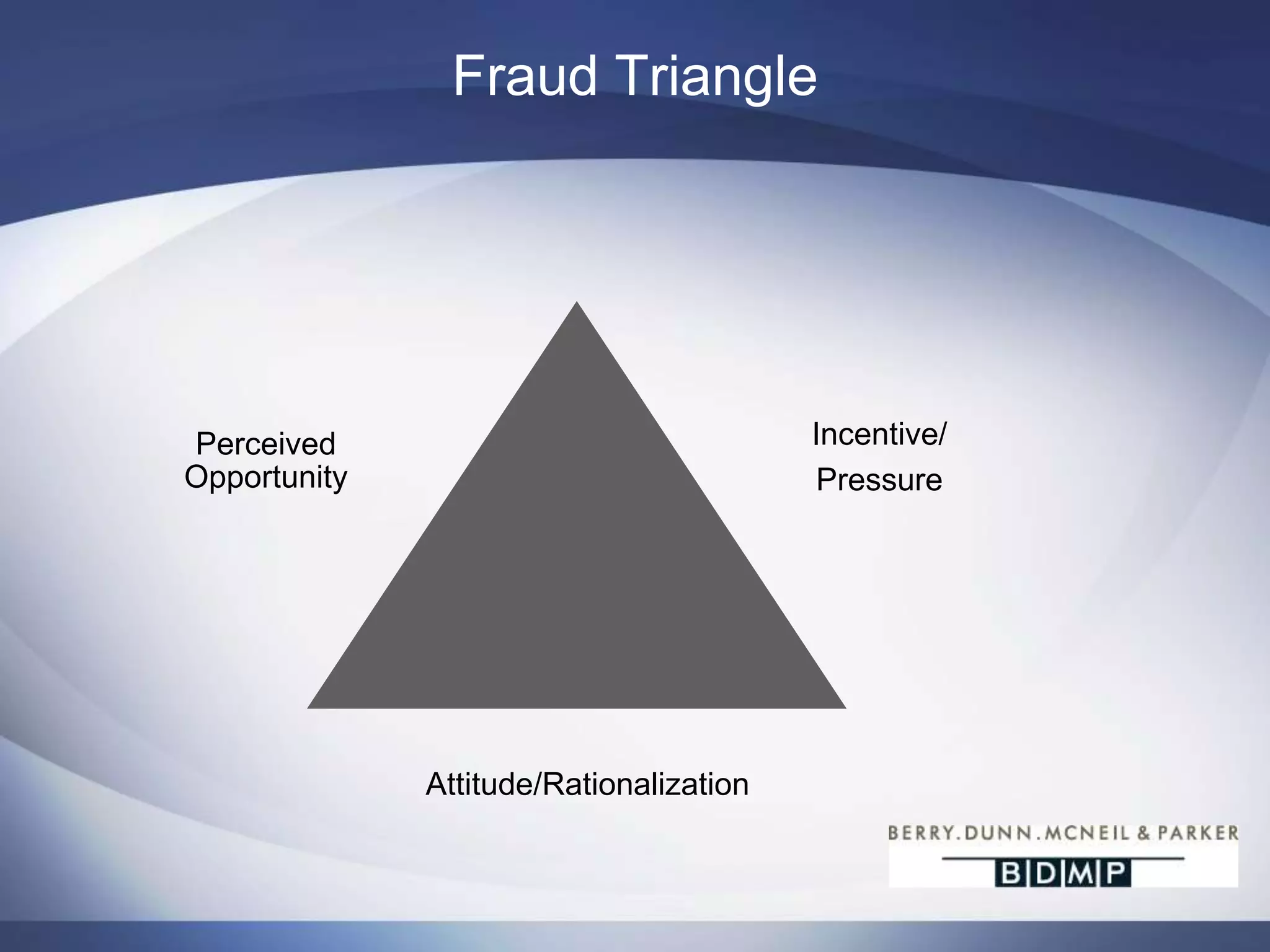
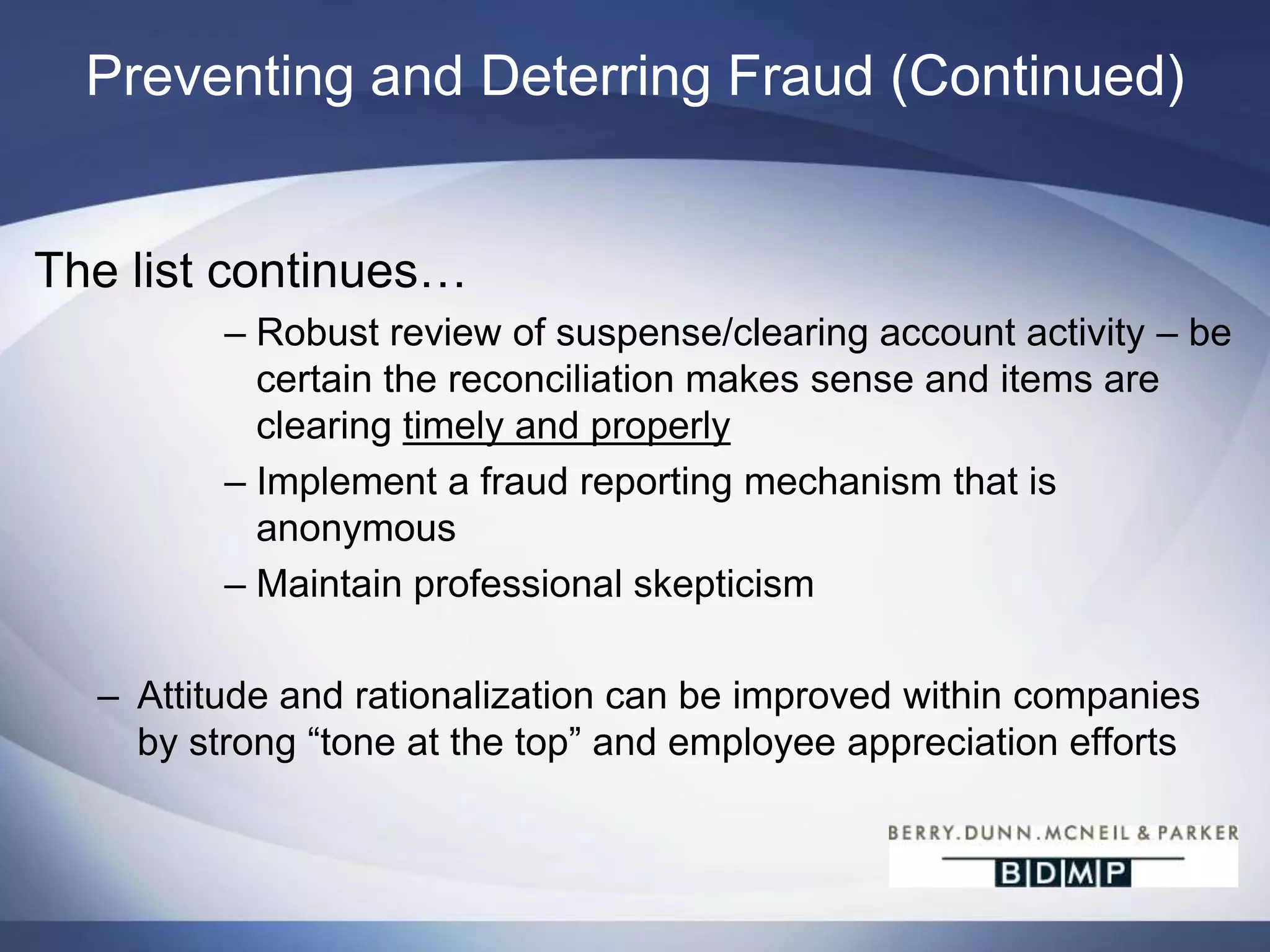
This document summarizes a presentation on bank fraud and data forensics. It discusses common types of internal and external bank fraud such as wire fraud, check fraud, and asset misappropriation. It outlines the fraud triangle of opportunity, pressure, and rationalization. It emphasizes the importance of strong internal controls and segregation of duties to prevent fraud. The presentation also discusses how digital forensics can be used to investigate inappropriate network activity, email, internet usage, and recover deleted files during fraud investigations. Contact information is provided for the three presenters.