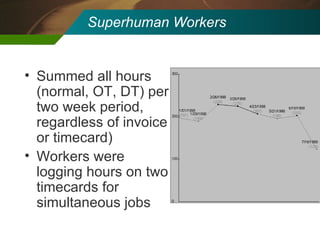
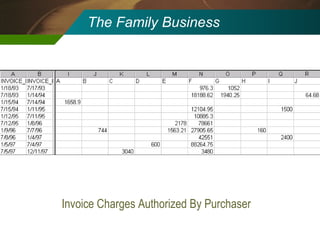
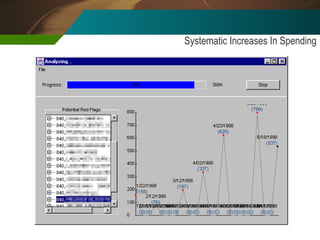
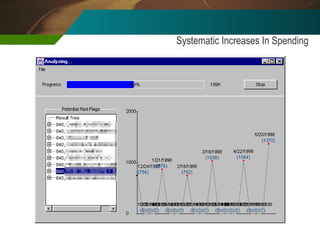
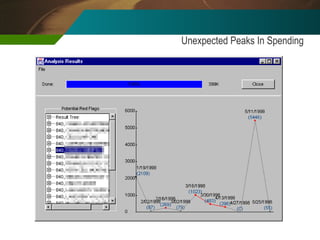
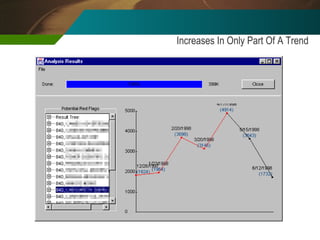
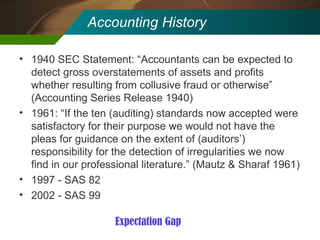
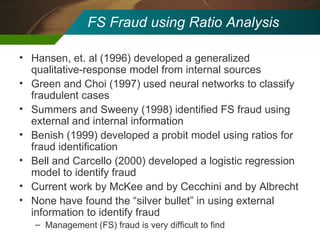
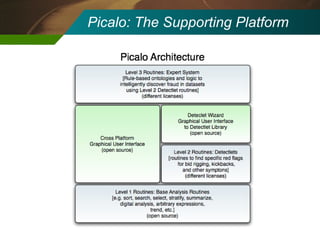
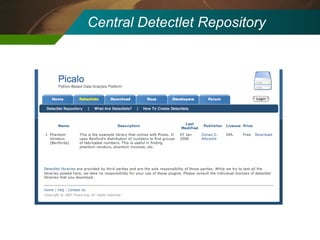
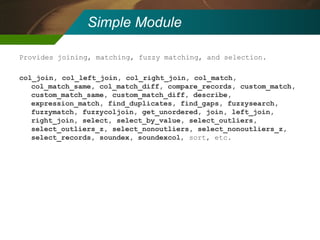
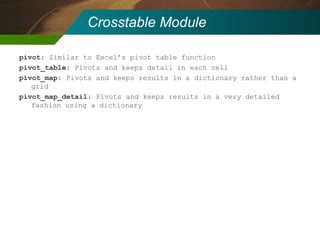
The document discusses the development and application of 'detectlets' as tools for enhancing fraud detection, highlighting the significant financial impact of fraud on organizations, with annual losses estimated at over $400 billion in the U.S. It details the architecture of the Picalo platform, which enables auditors to use these detectlets efficiently and cost-effectively, addressing common challenges in fraud detection. Future research directions include expanding the repository of detectlets and improving their capabilities for both internal and external audits.