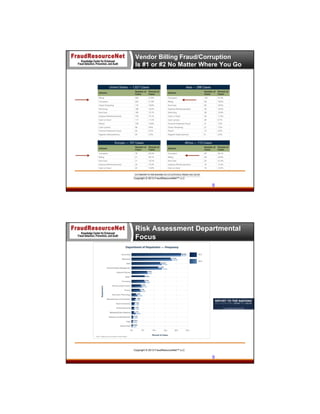
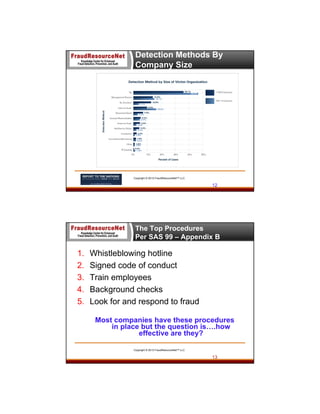
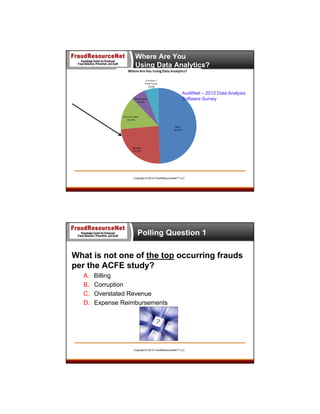
The document discusses utilizing data analytics to detect and prevent procure-to-pay (P2P) fraud, highlighting the roles of experts in the field. It covers the types of fraud that commonly occur, identifying red flags, and methodologies to effectively implement data analysis for fraud prevention. The presentation emphasizes the importance of anti-fraud controls and outlines a comprehensive framework for organizations to better manage risks associated with fraud.