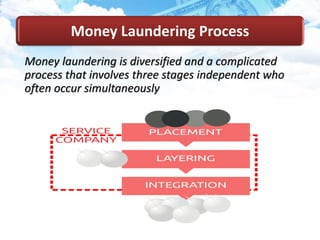
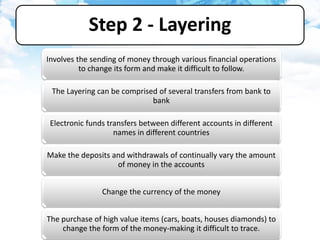
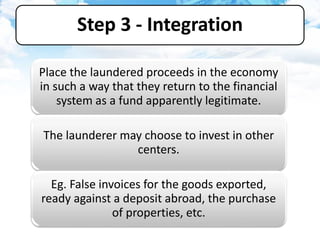
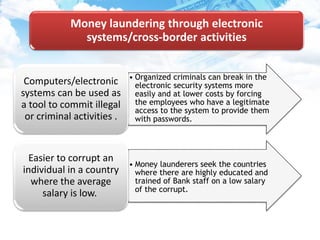
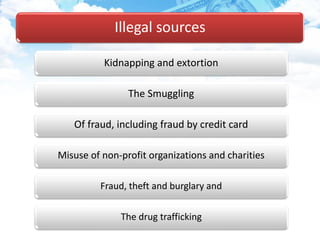
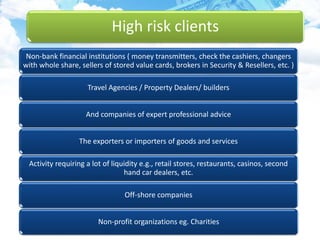
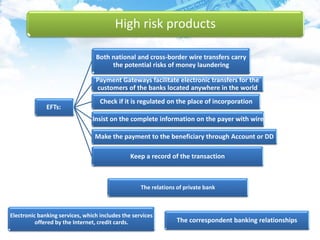
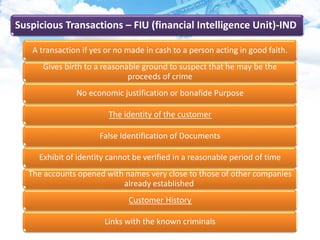
The document discusses money laundering, including defining it, describing the process, and providing case studies. Money laundering is defined as disguising illegally obtained money to make it appear legitimate. The process typically involves three stages: placement, layering, and integration. Placement involves putting dirty money into the financial system. Layering involves separating the money from its source through transactions. Integration makes the money appear clean. Case studies show how professionals like lawyers and accountants can be used to launder money through techniques like shell companies and structured transactions. Estimates suggest $600 billion to $2 trillion may be laundered annually, impacting economies and banking systems.