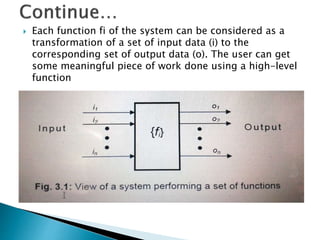
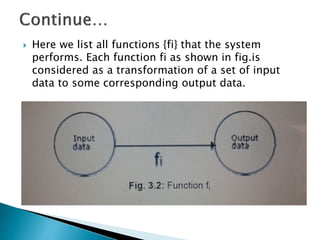
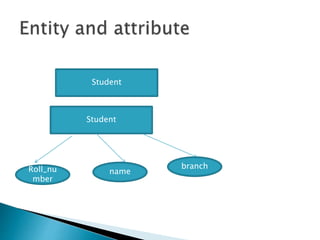
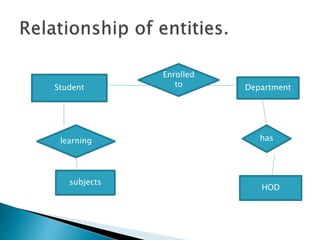
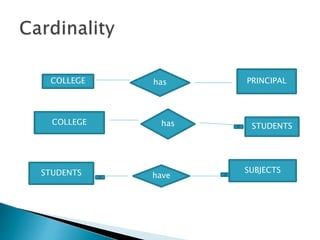
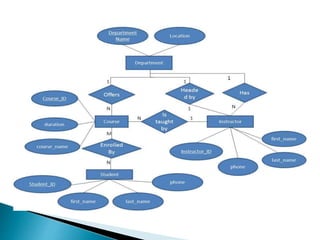
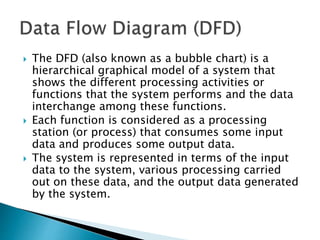
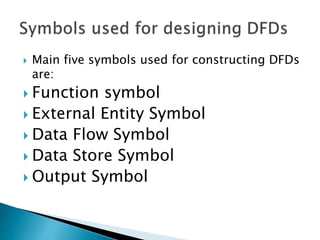
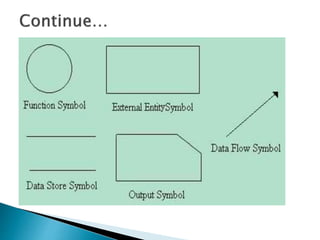
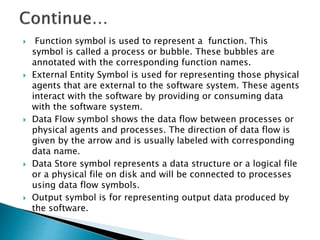
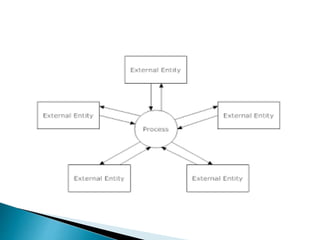
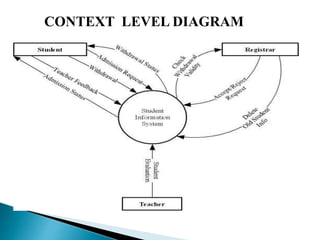
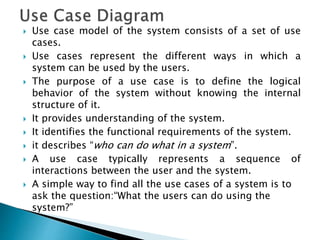
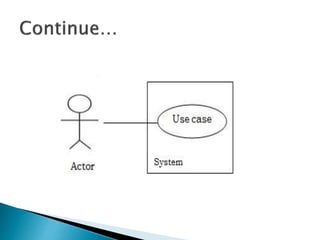
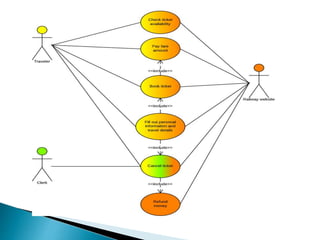
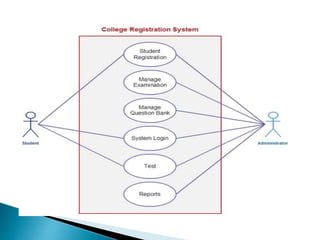
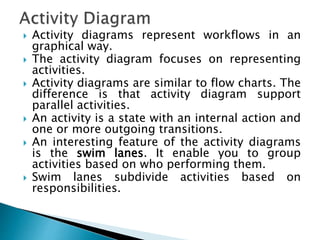
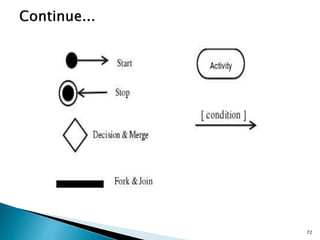
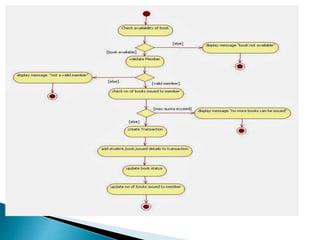
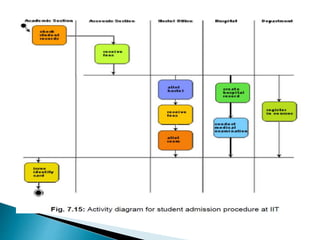
The document outlines the software requirements specifications (SRS) process, including requirement gathering, analysis, documentation, and the importance of structuring the SRS document effectively. It discusses both functional and non-functional requirements, emphasizes the role of a good software design that supports modularity and low coupling, and describes the methodologies for software design. Additionally, it highlights the significance of addressing common issues in SRS documentation to ensure project success.