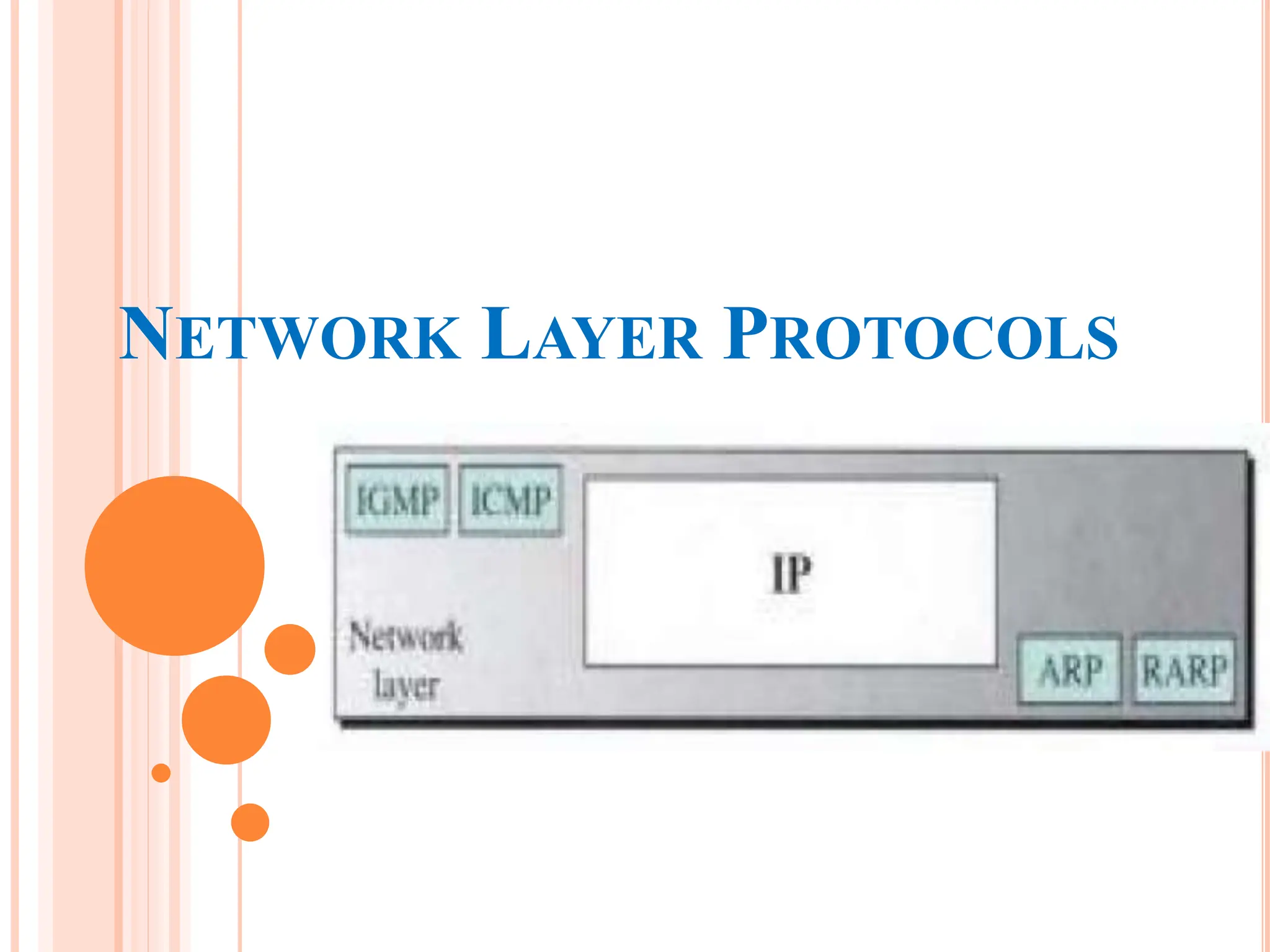
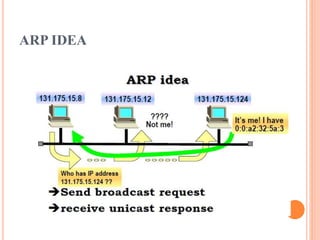
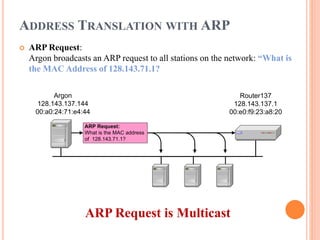
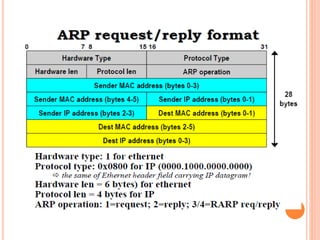
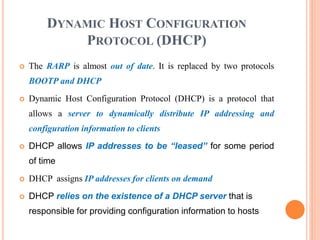
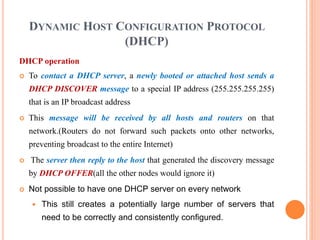
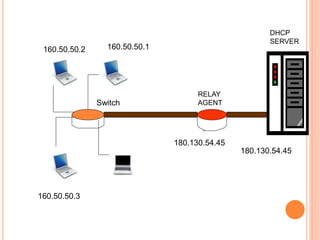
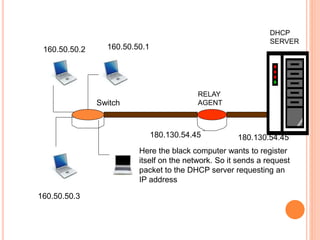
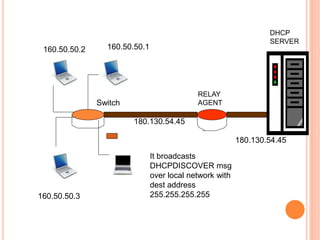
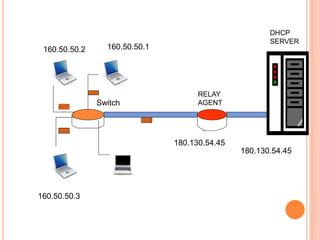
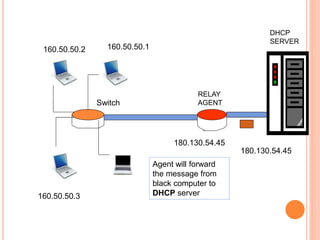
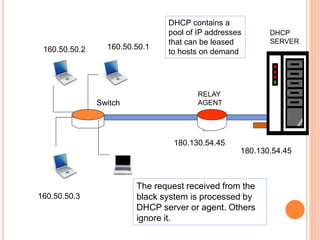
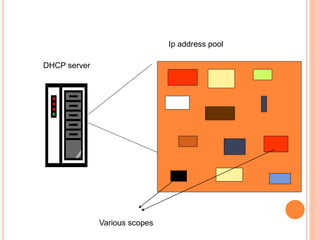
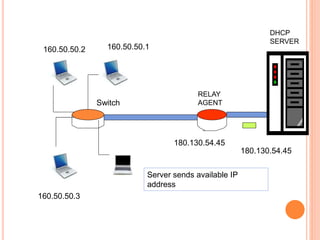
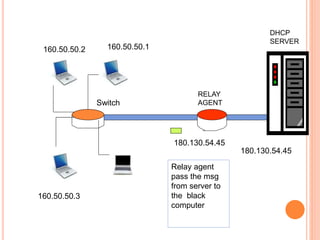
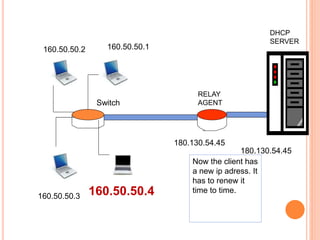
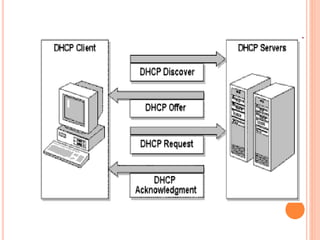
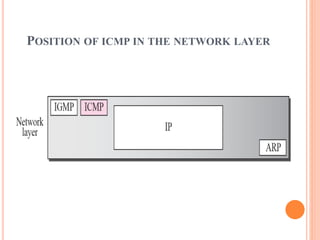
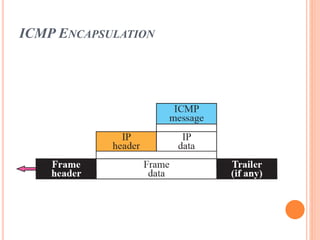
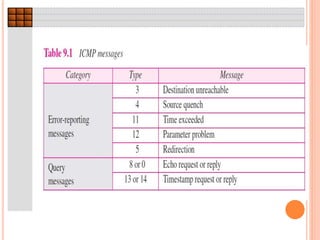
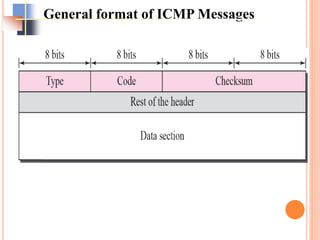
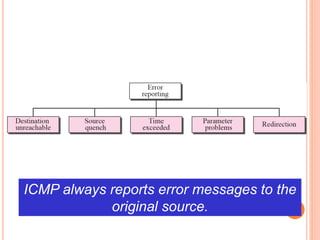
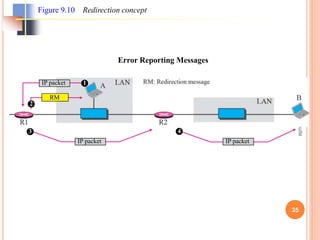
The document discusses network layer protocols, focusing on the Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP) which are responsible for mapping IP addresses to MAC addresses and vice versa. It also covers the Dynamic Host Configuration Protocol (DHCP), which dynamically assigns IP addresses to clients, and the Internet Control Message Protocol (ICMP), which handles error reporting for the IP protocol. Overall, it highlights the importance of these protocols in ensuring effective communication across networks.