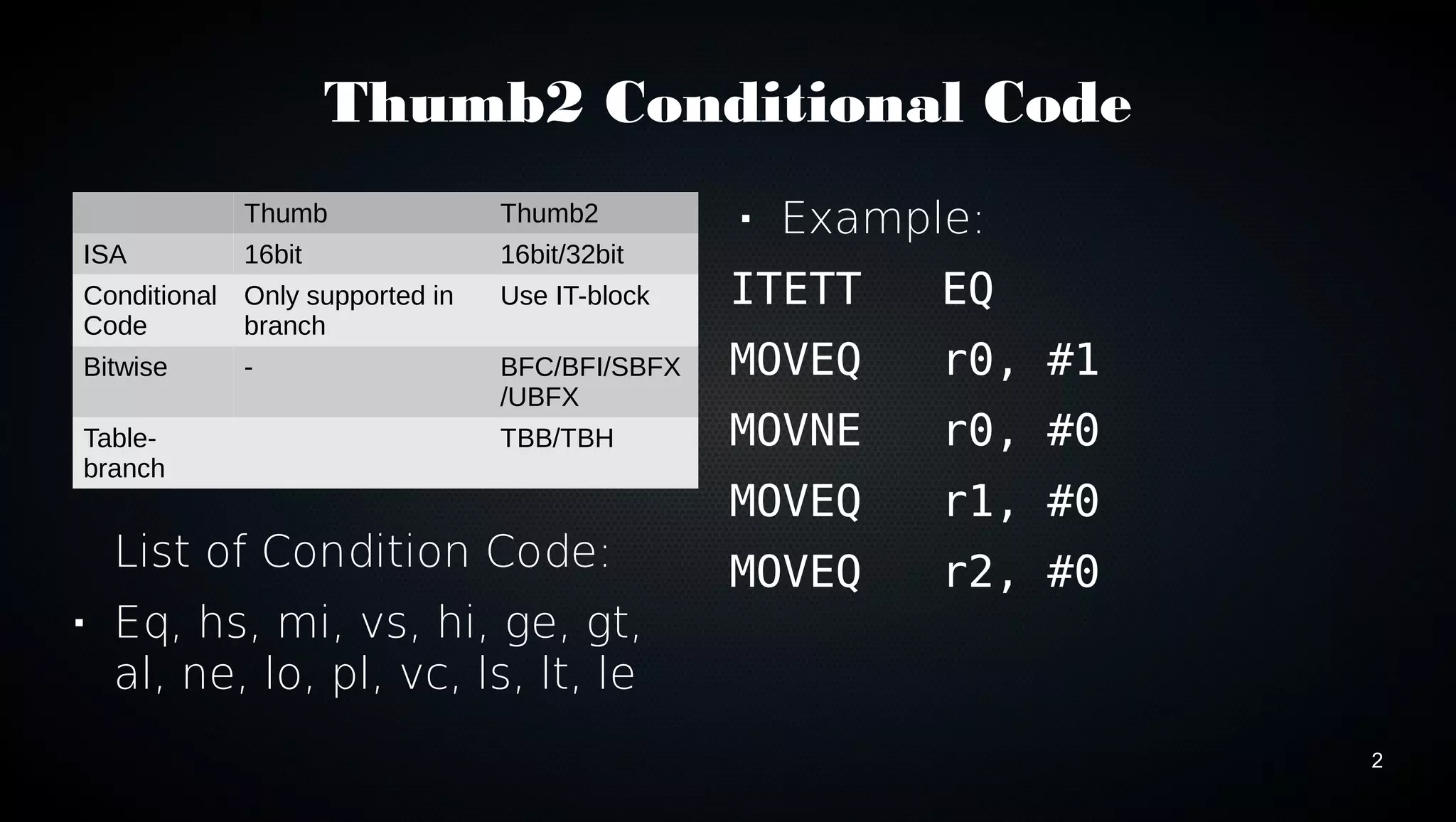
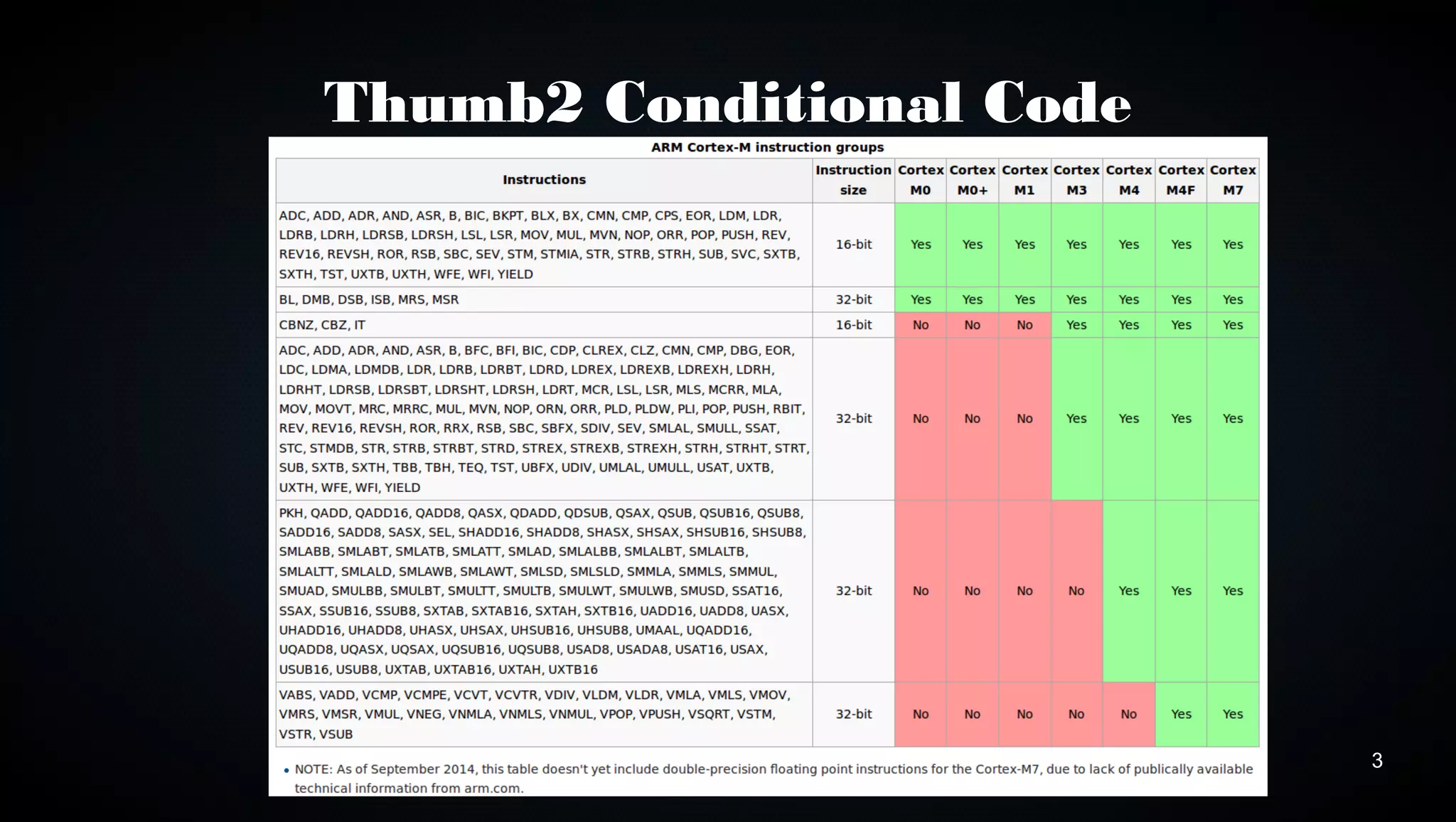
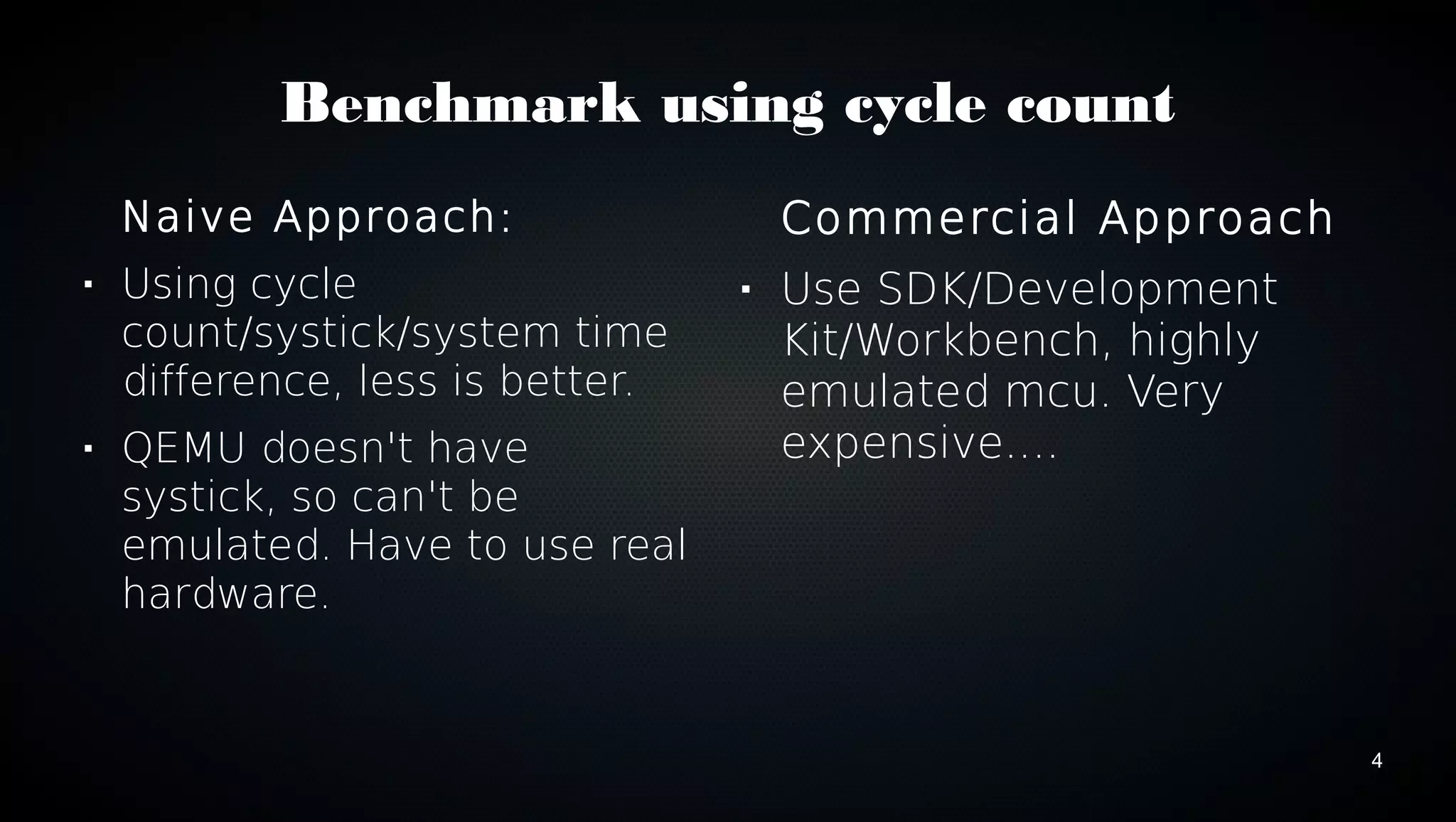
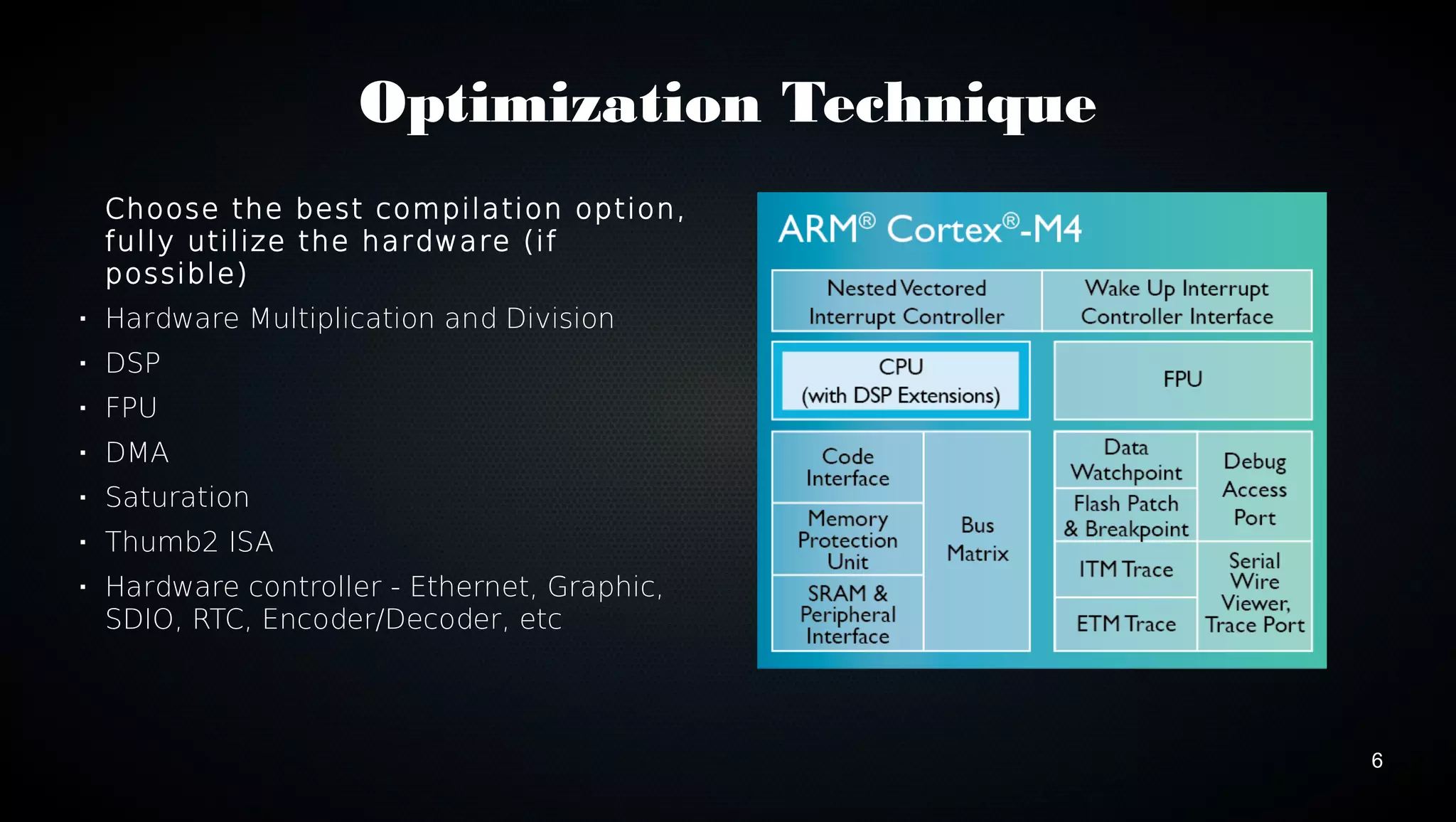
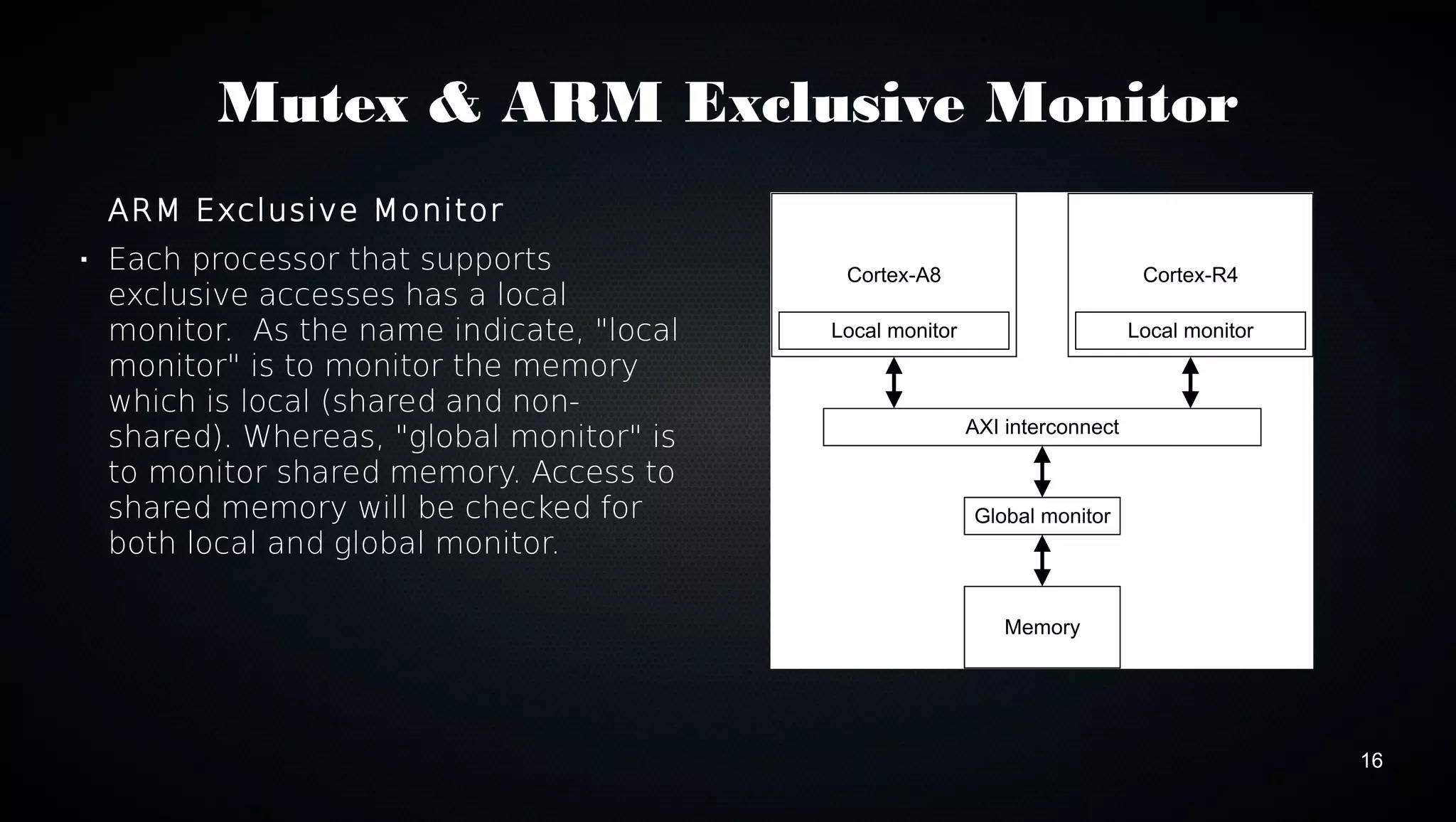
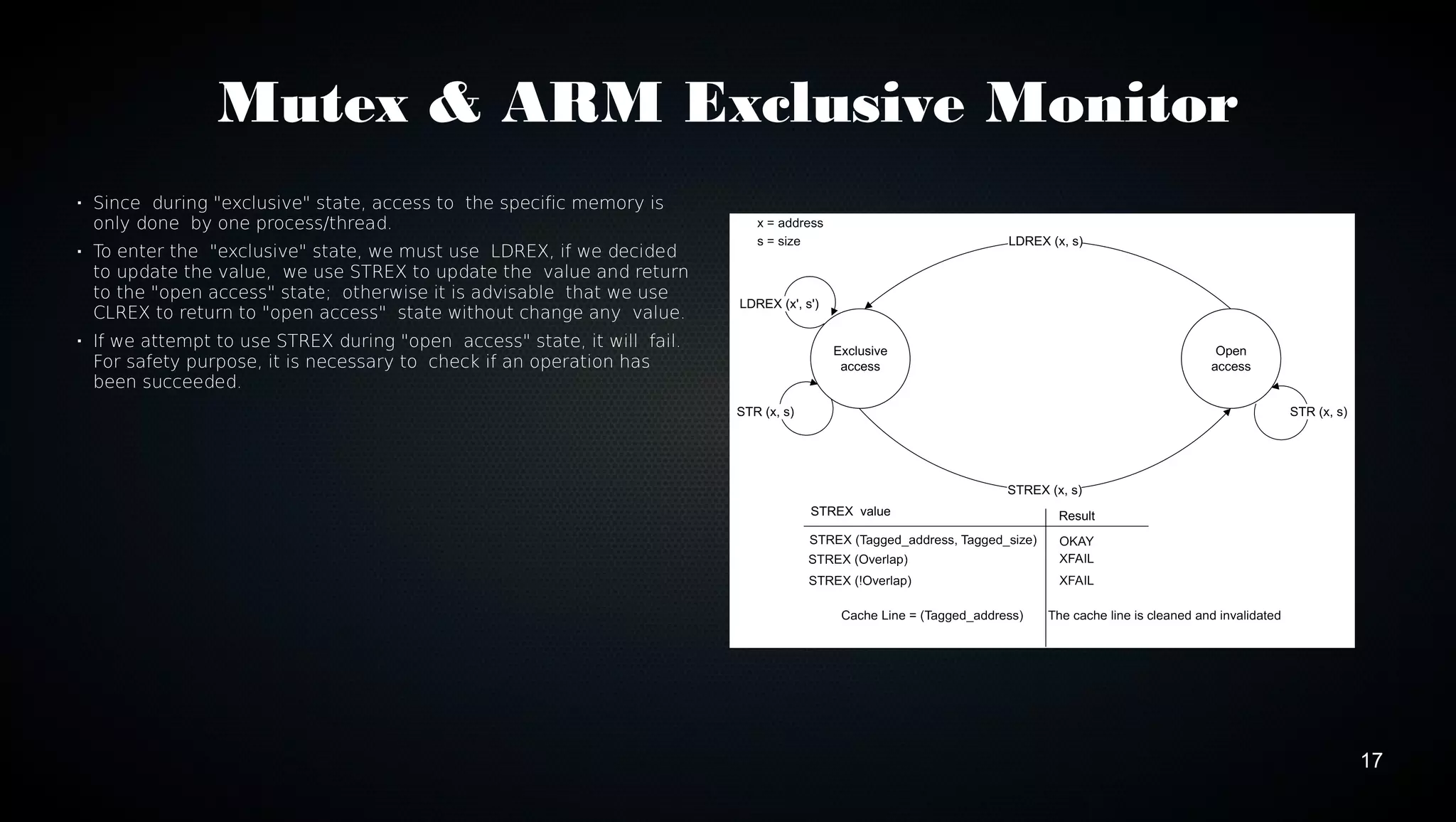
This document discusses various techniques for optimizing code on ARM processors, including using conditional instructions, benchmarking with cycle counts, utilizing hardware features like multiplication and DMA, choosing optimal data structures and algorithms, and using mutexes and exclusive monitors for thread synchronization. Some key points covered are using bitwise operations instead of shifts/masks when possible, structs for packing data efficiently in memory, and preferring to reuse existing libraries over reimplementing functionality.