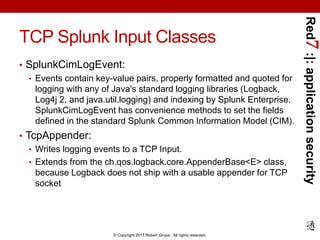
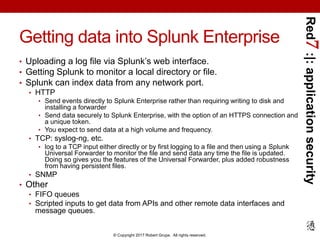
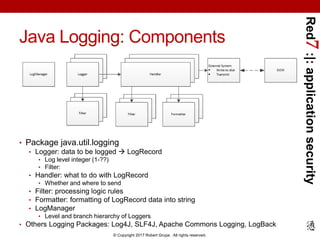
The document provides a comprehensive guide on application security logging with a focus on using Splunk SIEM and Java. It outlines the importance of logging for security and business purposes, details on configuring logging in Java, as well as best practices for integrating Splunk with Java applications. Additionally, it lists events to log and compliance requirements related to application security monitoring.














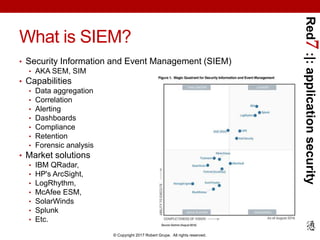
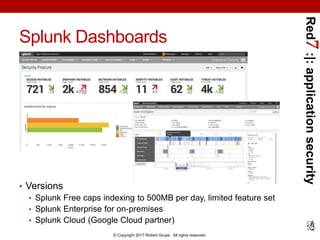










![Red7:|:applicationsecurity
© Copyright 2017 Robert Grupe. All rights reserved.
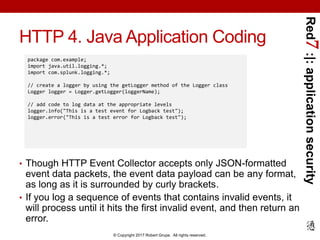
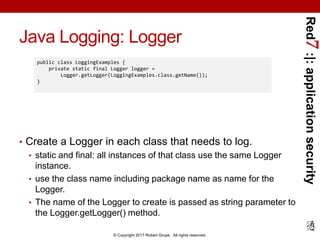
Java Logging Example
package com.example;
import java.util.logging.*;
public class Nose{
private static Logger logger = Logger.getLogger("com.wombat.nose"); // Obtain logger
public static void main(String argv[]) { // Log FINE tracing message
logger.fine("doing stuff");
try{
Wombat.sneeze();
} catch (Exception ex) { // Log the exception
logger.log(Level.WARNING, "trouble sneezing", ex);
}
logger.fine("done");
}
}](https://image.slidesharecdn.com/red7splunkapplicationsecurityloggingjava20170423-170424015249/85/Application-Security-Logging-with-Splunk-using-Java-31-320.jpg)






![Red7:|:applicationsecurity
© Copyright 2017 Robert Grupe. All rights reserved.
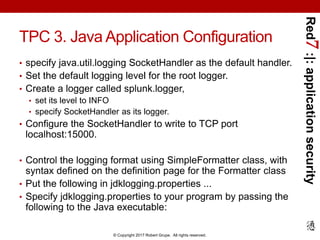
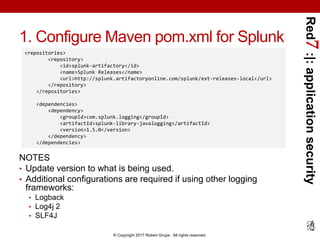
HTTP 3. Java Application Configuration
• Specify jdklogging.properties to your program by passing the
following to the Java executable
• Customize jdklogging.properties file
• Bare-minimum version below [refer to slide notes for more info]:
• Includes just the url, level, and token properties, plus the
disableCertificateValidation property.
• Doesn’t include optional source, sourcetype, batch_interval,
batch_size_bytes, batch_size_count, and index.
Need to customize XML configuration file for your setup.
- Djava.util.logging.config.file=/path/to/jdklogging.properties
%user_logger_name%.level = INFO
%user_logger_name%.handlers = com.splunk.logging.HttpEventCollectorLoggingHandler
com.splunk.logging.HttpEventCollectorLoggingHandler.url = %scheme%://%host%:%port%
com.splunk.logging.HttpEventCollectorLoggingHandler.level = INFO
com.splunk.logging.HttpEventCollectorLoggingHandler.token = %user_httpeventcollector_token%
com.splunk.logging.HttpEventCollectorLoggingHandler.disableCertificateValidation=true](https://image.slidesharecdn.com/red7splunkapplicationsecurityloggingjava20170423-170424015249/85/Application-Security-Logging-with-Splunk-using-Java-39-320.jpg)