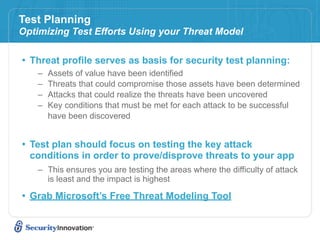
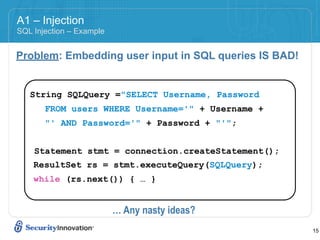
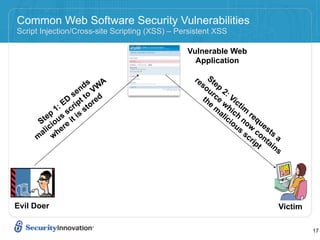
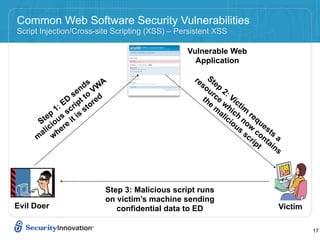
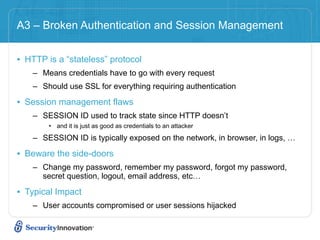
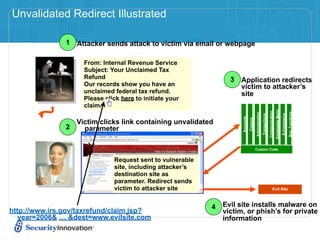
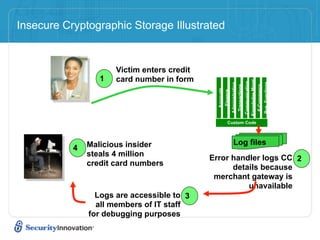
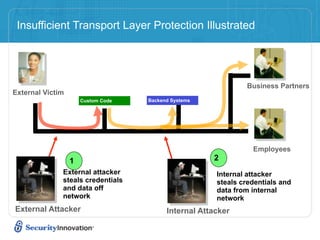
Here are 3 ways to prevent SQL injection:
1. Use prepared statements with parameter binding instead of concatenating strings.
2. Validate all input and sanitize special characters.
3. White-list allowed characters instead of blacklisting dangerous ones.
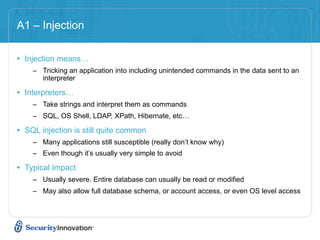
The root cause is putting untrusted data directly into a SQL query. Always separate data and code to prevent injection attacks.