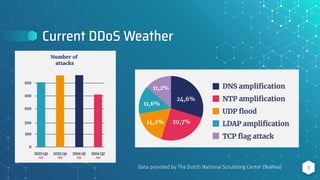
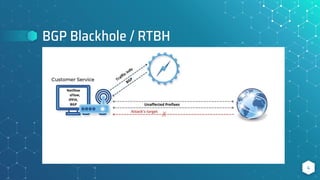
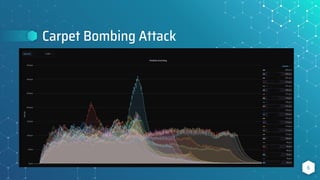
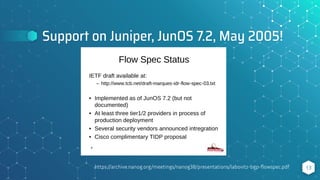
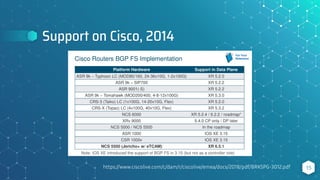
The document discusses BGP flow specification as a method for DDoS mitigation, detailing its features, filtering capabilities, and limitations across various platforms such as Juniper, Cisco, and Huawei. It highlights the challenges faced in implementing flow specification rules and provides resources for further reading and community engagement. The author, Pavel Odintsov, invites questions and discussions related to the topic.