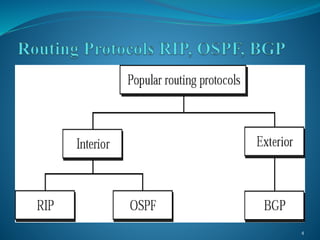
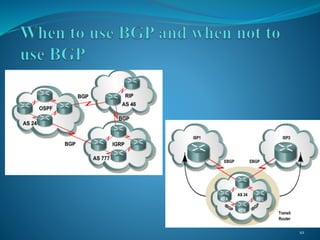
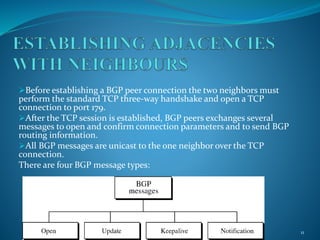
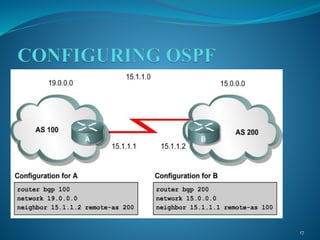
The document presents an overview of Border Gateway Protocol (BGP), detailing its significance in routing within large organizations and inter-domain connections. It covers the protocol's architecture, message types, path selection process, and configuration, alongside comparisons with other routing protocols like RIP and OSPF. The document also outlines the conditions under which BGP should and should not be used, emphasizing its role in managing multiple internet connections and routing policies.