Android telephony stack
•
23 likes•13,679 views
1. The document describes the architecture and communication flow for making requests to the radio interface layer (RIL) in Android. 2. It involves classes like GSMPhone, RIL, RILSender, RILReceiver, and the RILD native process which communicates with the proprietary radio interface library. 3. Requests are sent via asynchronous calls from the phone implementation to RIL, then from RIL to the RILD process which calls the proprietary radio library, and responses return through the same layers back to the original caller.
Report
Share
Report
Share
Download to read offline
Recommended
RIL and Android Telephony

Brief introduction of android telephony framework, detailed analyze of RIL (radio interface layer), and some examples for doing telephony thing in a low layer
Low Level View of Android System Architecture

This presentation covers the working model about Process, Thread, system call, Memory operations, Binder IPC, and interactions with Android frameworks.
Api flow mo ims_call_initiation from telephony _ android 

A brief overview on the API flow while making an MO Call through IMS in a VOLTE capable Phone.
The document is a walk through the code flow of a Call delegation from Framework to GII and to the vendor IMS applications from GII.
Android IPC Mechanism

This presentation covers the concepts hehind Android Binder, framework parts interacting with Binder, and the implementation details.
Binder: Android IPC

Binder is what differentiates Android from Linux, it is most important internal building block of Android, it is a subject every Android programmer should be familiar with
Recommended
RIL and Android Telephony

Brief introduction of android telephony framework, detailed analyze of RIL (radio interface layer), and some examples for doing telephony thing in a low layer
Low Level View of Android System Architecture

This presentation covers the working model about Process, Thread, system call, Memory operations, Binder IPC, and interactions with Android frameworks.
Api flow mo ims_call_initiation from telephony _ android 

A brief overview on the API flow while making an MO Call through IMS in a VOLTE capable Phone.
The document is a walk through the code flow of a Call delegation from Framework to GII and to the vendor IMS applications from GII.
Android IPC Mechanism

This presentation covers the concepts hehind Android Binder, framework parts interacting with Binder, and the implementation details.
Binder: Android IPC

Binder is what differentiates Android from Linux, it is most important internal building block of Android, it is a subject every Android programmer should be familiar with
Android Internals

Android Internals talk given ad Android Montreal on Nov. 3rd 2010 by Karim Yaghmour (author of O'Reilly's "Building Embedded Linux Systems.")
Outgoing Call Flow ~ Android ( < Nougat).

A brief overview on the API flow while making an MO Call.
The document is a walk through the code flow of a Call from the user interface (DIALER) to the Telecom Service , then to the Telephony Framework into the RIL(Java.)
Android Binder IPC for Linux

binder-for-linux is an experimental project to evaluate the feasibility of porting Android Binder IPC subsystem to Ubuntu Linux.
GitHub: https://github.com/hungys/binder-for-linux
Understanding binder in android

Binder, is the android-specific inter-process communication mechanism,
Android Binder: Deep Dive

Android is a Linux-based architecture. In addition to the original Linux driver, Android need other additional device driver, like Android Logger, Binder, Low Memory killer, Power Management for android(wakelock), ASHMEM, etc out of which ashmem ,logger and binder are all character device drivers.
Android Development: The Basics

Overview of the basics of Android software development. Presented to TechMaine's MaineJUG on June 21, 2011.
Understanding the Android System Server

Understanding the Android System Server talk given at AnDevCon by Karim Yaghmour in March 2011
Embedded Android : System Development - Part I

There is a surge in number of sensors / devices that are getting connected under the umbrella of Internet-Of-Things (IoT). These devices need to be integrated into the Android system and accessed via applications, which is covered in the course. Our Android system development course curriculum over weekends with practicals ensures you learn all critical components to get started.
Applied Computer Science Concepts in Android

In this presentation, the unaware or indirect applications of essential computer science concepts are dicussed as showcase. Jim Huang presented in Department of Computer Science and Engineering, National Taiwan University.
Broadcast Receiver

National Mobile Application Awareness Development & Capacity Building Program (Android Slides)
An Introduction to the Android Framework -- a core architecture view from app...

This presentation, following the previous "An Introduction to the Linux Kernel and Device Drivers", is for another 3-hours lecture in the "Open Source System Software & Practice" class, organized and hosted by Prof. Shih-Hao Hung, in the Department of Computer Science and Information Engineering, National Taiwan University.
The slides cover the architecture of the Android Framework, including the Android architecture overview, system integration of the Android operating system, the Activity and Service framework components, life cycles, inter-component communication methods, how the framework works, the Android device control model, core system services, hardware abstraction layer, and related important issues, etc.
Booting Android: bootloaders, fastboot and boot images

Discover the internal workings of Android bootstrap. Find out how to reveal and modify a boot image.
Embedded Android : System Development - Part II (HAL)

Embedded Android System Development - Part II talks about Hardware Abstraction Layer (HAL). HAL is an interfacing layer through which Android service can place a request to device. Uses functions provided by Linux system to service the request from android framework. A C/C++ layer with purely vendor specific implementation. Packaged into modules (.so) file & loaded by Android system at appropriate time
Android internals 10 - Debugging/Profiling, Bluetooth/WiFI/RIL (rev_1.1)

Course: Android Internals
Lecture 10: Debugging/Profiling, Bluetooth/WiFI/RIL
More Related Content
What's hot
Android Internals

Android Internals talk given ad Android Montreal on Nov. 3rd 2010 by Karim Yaghmour (author of O'Reilly's "Building Embedded Linux Systems.")
Outgoing Call Flow ~ Android ( < Nougat).

A brief overview on the API flow while making an MO Call.
The document is a walk through the code flow of a Call from the user interface (DIALER) to the Telecom Service , then to the Telephony Framework into the RIL(Java.)
Android Binder IPC for Linux

binder-for-linux is an experimental project to evaluate the feasibility of porting Android Binder IPC subsystem to Ubuntu Linux.
GitHub: https://github.com/hungys/binder-for-linux
Understanding binder in android

Binder, is the android-specific inter-process communication mechanism,
Android Binder: Deep Dive

Android is a Linux-based architecture. In addition to the original Linux driver, Android need other additional device driver, like Android Logger, Binder, Low Memory killer, Power Management for android(wakelock), ASHMEM, etc out of which ashmem ,logger and binder are all character device drivers.
Android Development: The Basics

Overview of the basics of Android software development. Presented to TechMaine's MaineJUG on June 21, 2011.
Understanding the Android System Server

Understanding the Android System Server talk given at AnDevCon by Karim Yaghmour in March 2011
Embedded Android : System Development - Part I

There is a surge in number of sensors / devices that are getting connected under the umbrella of Internet-Of-Things (IoT). These devices need to be integrated into the Android system and accessed via applications, which is covered in the course. Our Android system development course curriculum over weekends with practicals ensures you learn all critical components to get started.
Applied Computer Science Concepts in Android

In this presentation, the unaware or indirect applications of essential computer science concepts are dicussed as showcase. Jim Huang presented in Department of Computer Science and Engineering, National Taiwan University.
Broadcast Receiver

National Mobile Application Awareness Development & Capacity Building Program (Android Slides)
An Introduction to the Android Framework -- a core architecture view from app...

This presentation, following the previous "An Introduction to the Linux Kernel and Device Drivers", is for another 3-hours lecture in the "Open Source System Software & Practice" class, organized and hosted by Prof. Shih-Hao Hung, in the Department of Computer Science and Information Engineering, National Taiwan University.
The slides cover the architecture of the Android Framework, including the Android architecture overview, system integration of the Android operating system, the Activity and Service framework components, life cycles, inter-component communication methods, how the framework works, the Android device control model, core system services, hardware abstraction layer, and related important issues, etc.
Booting Android: bootloaders, fastboot and boot images

Discover the internal workings of Android bootstrap. Find out how to reveal and modify a boot image.
Embedded Android : System Development - Part II (HAL)

Embedded Android System Development - Part II talks about Hardware Abstraction Layer (HAL). HAL is an interfacing layer through which Android service can place a request to device. Uses functions provided by Linux system to service the request from android framework. A C/C++ layer with purely vendor specific implementation. Packaged into modules (.so) file & loaded by Android system at appropriate time
What's hot (20)
An Introduction to the Android Framework -- a core architecture view from app...

An Introduction to the Android Framework -- a core architecture view from app...
Booting Android: bootloaders, fastboot and boot images

Booting Android: bootloaders, fastboot and boot images
Embedded Android : System Development - Part II (HAL)

Embedded Android : System Development - Part II (HAL)
Viewers also liked
Android internals 10 - Debugging/Profiling, Bluetooth/WiFI/RIL (rev_1.1)

Course: Android Internals
Lecture 10: Debugging/Profiling, Bluetooth/WiFI/RIL
Android Core Aula 5 - RIL (Radio Interface Layer)

Quinta Aula do curso "Android Core". Nesta aula veremos detalhes do RIL, o componente Android responsável por comunicação de voz.
Embedded Android Workshop at Embedded Linux Conference Europe 2011

"Embedded Android Workshop" presented by Karim Yaghmour at the Embedded Linux Conference Europe 2011.
Labmeeting - 20150211 - Novel End-to-End Voice Encryption Method in GSM System

Networking, Sensing and Control, 2008. ICNSC 2008.
IEEE International Conference
H.F. Qi, X.H. Yang, R. Jiang, B. Liang and S.J. Zhou
Encrypted Voice Communications

Self Contained Encrypted Voice solution for business and government. Central server + iphone and android app, high level of encrypted voice and text message capability that resides completely onsite, works anywhere from one enabled comms device to another on the same network
Linux kernel modules

This is the presentation I gave on Linux kernel modules at the Linux Meetup in Austin, TX, on 2/5/2015.
http://www.meetup.com/linux-85/events/185946802/
Code referred to in the presentation: https://github.com/ereyes01/kernel-mod-prez
Voice securityprotocol review

This talk is a intense overview of major voice security and encryption protocols existing out there for different scope.
Communication Service Providers (CSP) and the Telecom API Ecosystem

Free White Paper on Communications Enabling Apps and Telecom API Ecosystem from Mind Commerce
Viewers also liked (20)
Android internals 10 - Debugging/Profiling, Bluetooth/WiFI/RIL (rev_1.1)

Android internals 10 - Debugging/Profiling, Bluetooth/WiFI/RIL (rev_1.1)
Embedded Android Workshop at Embedded Linux Conference Europe 2011

Embedded Android Workshop at Embedded Linux Conference Europe 2011
Labmeeting - 20150211 - Novel End-to-End Voice Encryption Method in GSM System

Labmeeting - 20150211 - Novel End-to-End Voice Encryption Method in GSM System
Android Application Component: BroadcastReceiver Tutorial

Android Application Component: BroadcastReceiver Tutorial
Communication Service Providers (CSP) and the Telecom API Ecosystem

Communication Service Providers (CSP) and the Telecom API Ecosystem
Similar to Android telephony stack
Remote Method Innovation (RMI) In JAVA

Brief introduction about the Remote Method Innovation (RMI) In JAVA.
Presentation 4 rifidi emulator lab

Sharing RFID training materials which i developed for assignment in my MSc for software systems , in Heriott Watt University
Remote Method Invocation (RMI)

Overview of Java RMI remoting.
RMI is a lightweight Java technology that provides access to remote methods, similar to RPC, but object-oriented. RMI basically provides remote object access for a client and object registration for servers.
RMI is both a Java API (java.rmi.* package) as well as a transport protocol definition for transporting RMI calls through a network.
RMI is a Java technology since it requires that client and server objects run in a JVM (Java Virtual Machine). By using IIOP as transport protocol, however, it is possible to connect RMI-clients to non-Java server objects (e.g. CORBA).
RMI defines the elements client, server, RMI registry where servers register their services and possibly a plain vanilla web server that can be used by clients to dynamically load object classes to access servers.
Rfc high res 3 july 2012

RF Code provides you with a high resolution image of the environmental variables of your datacenter while understanding what assets you have and where they are.
We provide the answer to the question
“Where is it, what is it and how is it doing?”.
Similar to Android telephony stack (8)
Recently uploaded
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

Dr. Sean Tan, Head of Data Science, Changi Airport Group
Discover how Changi Airport Group (CAG) leverages graph technologies and generative AI to revolutionize their search capabilities. This session delves into the unique search needs of CAG’s diverse passengers and customers, showcasing how graph data structures enhance the accuracy and relevance of AI-generated search results, mitigating the risk of “hallucinations” and improving the overall customer journey.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

ここ3000字までしか入らないけどタイトルの方がたくさん文字入ると思います。
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI

Enchancing adoption of Open Source Libraries. A case study on Albumentations.AIVladimir Iglovikov, Ph.D.
Presented by Vladimir Iglovikov:
- https://www.linkedin.com/in/iglovikov/
- https://x.com/viglovikov
- https://www.instagram.com/ternaus/
This presentation delves into the journey of Albumentations.ai, a highly successful open-source library for data augmentation.
Created out of a necessity for superior performance in Kaggle competitions, Albumentations has grown to become a widely used tool among data scientists and machine learning practitioners.
This case study covers various aspects, including:
People: The contributors and community that have supported Albumentations.
Metrics: The success indicators such as downloads, daily active users, GitHub stars, and financial contributions.
Challenges: The hurdles in monetizing open-source projects and measuring user engagement.
Development Practices: Best practices for creating, maintaining, and scaling open-source libraries, including code hygiene, CI/CD, and fast iteration.
Community Building: Strategies for making adoption easy, iterating quickly, and fostering a vibrant, engaged community.
Marketing: Both online and offline marketing tactics, focusing on real, impactful interactions and collaborations.
Mental Health: Maintaining balance and not feeling pressured by user demands.
Key insights include the importance of automation, making the adoption process seamless, and leveraging offline interactions for marketing. The presentation also emphasizes the need for continuous small improvements and building a friendly, inclusive community that contributes to the project's growth.
Vladimir Iglovikov brings his extensive experience as a Kaggle Grandmaster, ex-Staff ML Engineer at Lyft, sharing valuable lessons and practical advice for anyone looking to enhance the adoption of their open-source projects.
Explore more about Albumentations and join the community at:
GitHub: https://github.com/albumentations-team/albumentations
Website: https://albumentations.ai/
LinkedIn: https://www.linkedin.com/company/100504475
Twitter: https://x.com/albumentationsLarge Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications.
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Essentials of Automations: The Art of Triggers and Actions in FME

In this second installment of our Essentials of Automations webinar series, we’ll explore the landscape of triggers and actions, guiding you through the nuances of authoring and adapting workspaces for seamless automations. Gain an understanding of the full spectrum of triggers and actions available in FME, empowering you to enhance your workspaces for efficient automation.
We’ll kick things off by showcasing the most commonly used event-based triggers, introducing you to various automation workflows like manual triggers, schedules, directory watchers, and more. Plus, see how these elements play out in real scenarios.
Whether you’re tweaking your current setup or building from the ground up, this session will arm you with the tools and insights needed to transform your FME usage into a powerhouse of productivity. Join us to discover effective strategies that simplify complex processes, enhancing your productivity and transforming your data management practices with FME. Let’s turn complexity into clarity and make your workspaces work wonders!
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
Recently uploaded (20)
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...

みなさんこんにちはこれ何文字まで入るの?40文字以下不可とか本当に意味わからないけどこれ限界文字数書いてないからマジでやばい文字数いけるんじゃないの?えこ...
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI

Enchancing adoption of Open Source Libraries. A case study on Albumentations.AI
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Essentials of Automations: The Art of Triggers and Actions in FME

Essentials of Automations: The Art of Triggers and Actions in FME
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
Android telephony stack
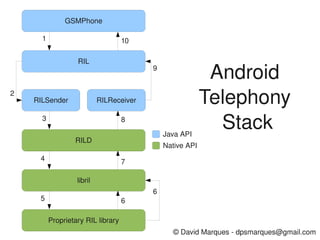
- 1. GSMPhone 1 10 RIL 9 Android 2 RILSender RILReceiver Telephony 3 8 Java API Stack RILD Native API 4 7 libril 6 5 6 Proprietary RIL library © David Marques dpsmarques@gmail.com
- 2. GSMPhone 1 10 RIL The com.android.internal.telephony.gsm.GSMPhone class implements a GSM phone and exposes all phone capabilities to the other components inside the android framework. This class interfaces with the radio interface layer in order to communicate to the baseband radio modem though the com.android.internal.telephony.RIL class. The topdown communication between these layers is done by asynchronous function calls passing an android.os.Message instance to be used in order to send the response back to the function caller with the function result within the message itself.
- 3. RIL 9 2 RILSender RILReceiver The com.android.internal.telephony.RIL class has two internal classes responsible for sending the requests and receiving the responses to and from the RIL daemon respectively. Both RILSender and RILReceiver classes run on its own threads interacting with the RIL daemon through a linux socket to send and receive messages to the baseband radio.
- 4. RILSender RILReceiver 3 8 RILD The RIL daemon (RILD) is a native linux process that communicates with the Java telephony API through a linux socket exposing a radio implementation agnostic protocol.
- 5. RILD 4 7 libril 6 5 6 Proprietary RIL library The RIL daemon (RILD) loads the proprietary RIL library and registers its radio specific functions implementation into the telephony stack. The RILD receives requests through a linux socket and processes the request calling the proprietary library's radio function implementation passing the appropriate parameters. The proprietary library returns a response to the telephony stack through a callback function which marshals the response and sends it back to the Java API though the same socket used to receive the request. The Java layers processes the request on the RILReceiver class and forwards the response to the original request owner.
- 6. Solicited command flow: android RIL -> proprietary RIL R RILD I libril L proprietary ril 1. Phone implementation calls RIL class to communicate with the baseband radio; 2. RIL class creates a Parcel and fills its content with the specified parameters; 3. RIL marshals the parcel into raw data and sends through the RILD socket; 4. RILD unmarshals the raw data into a Parcel and extracts the request parameters from the Parcel; 5. RILD calls through libril the proprietary RIL library request handler function passing the extracted parameters;
- 7. Solicited command flow: proprietary RIL -> android RIL R RILD I libril L proprietary ril 1. Proprietary RIL library calls the response function on the android libril passing the result; 2. Android libril creates a Parcel, puts the result within it and marshals the Parcel into raw data to be sent through the RILD socket back to the Java layer; 3. At the Java layer the raw data that came from the socket is unmarshaled into a Parcel and the result is extracted and sent to the original request owner; 4. The request owner receives the response on a Message instance passed to the RIL class method called to make the request;
- 8. Note: All the information in this document comes from the Android 2.2 release (aka Froyo) of the Android opensource project. Any future updates may invalidate the information contained on this document.