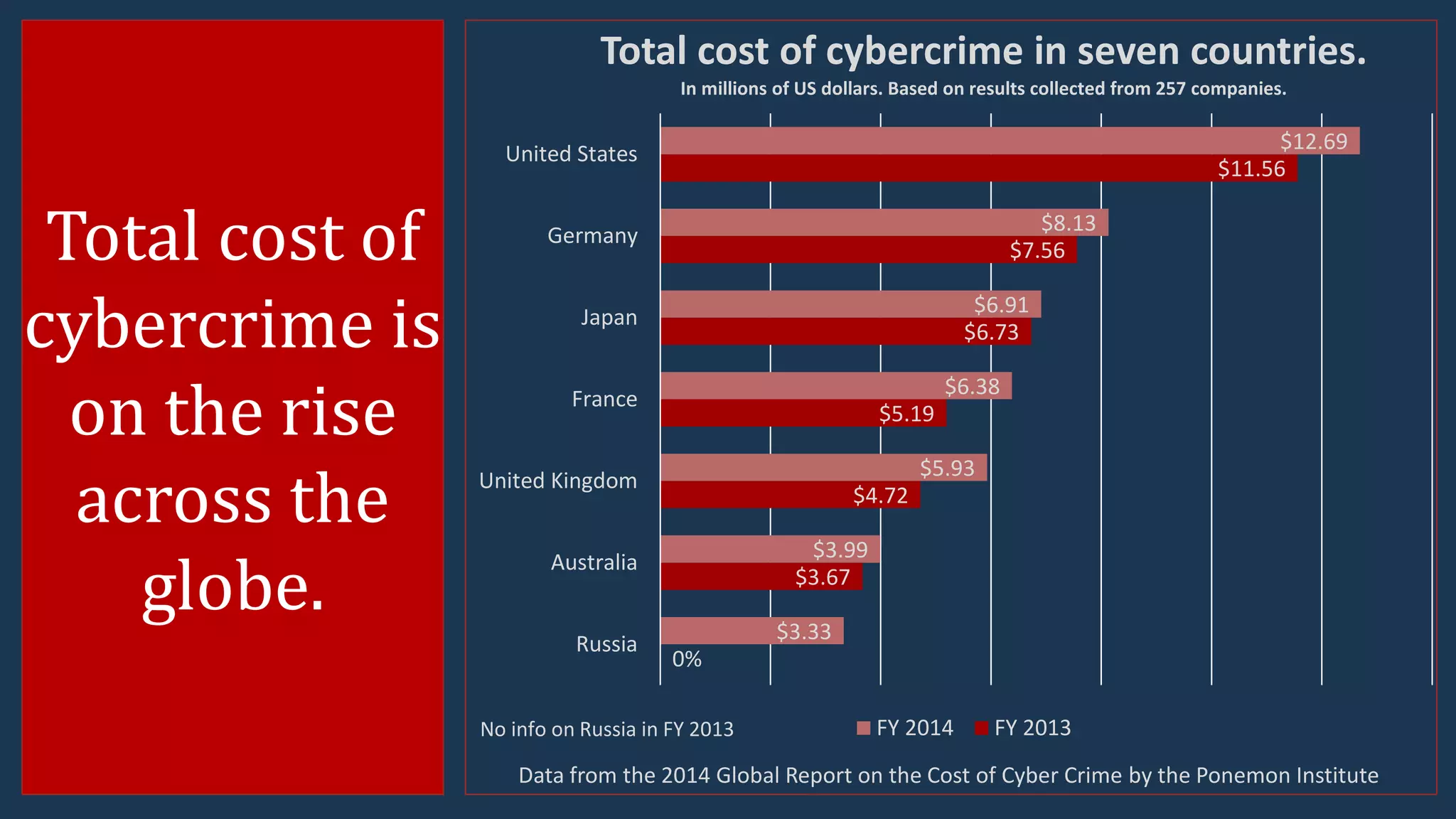
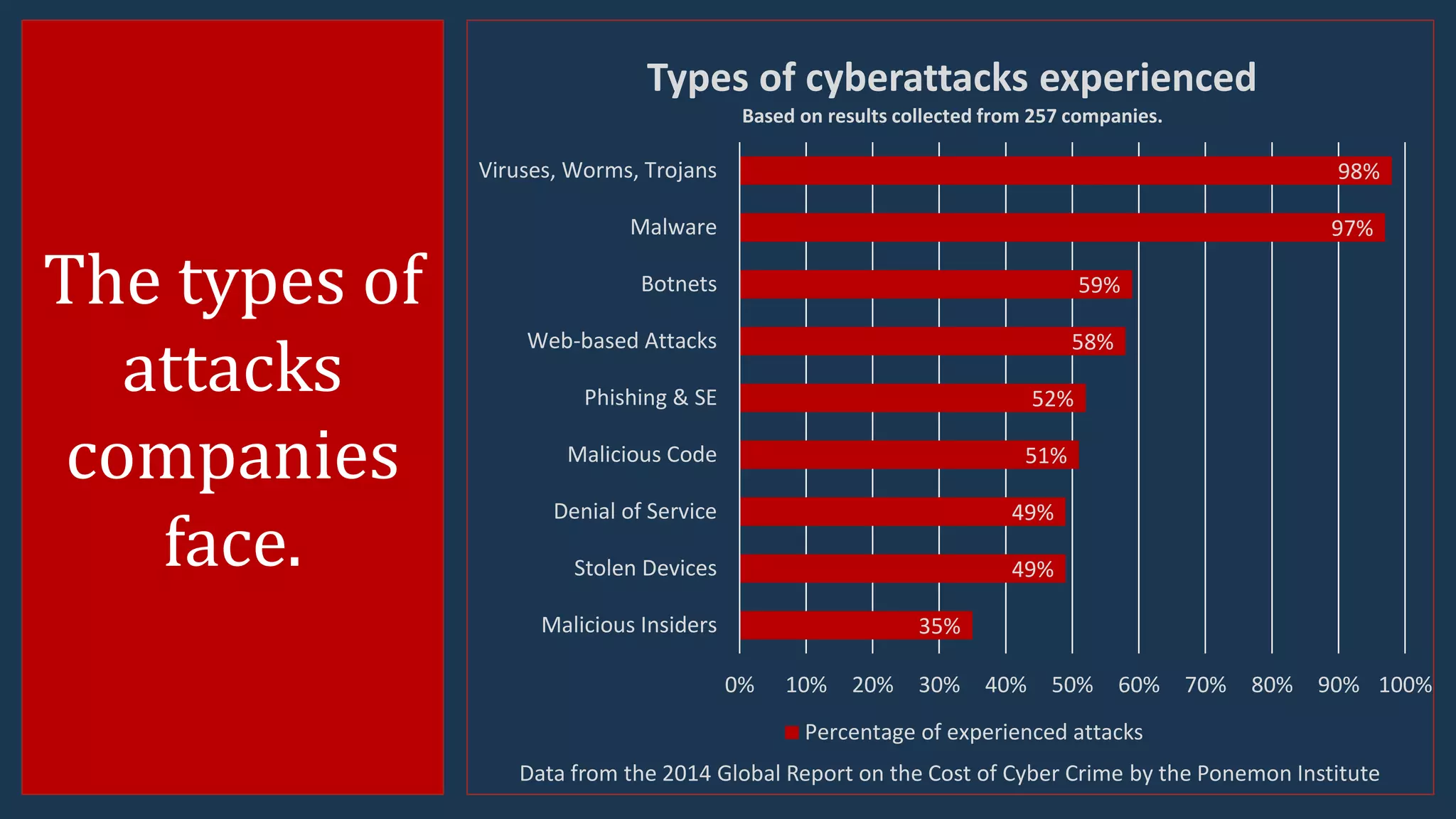
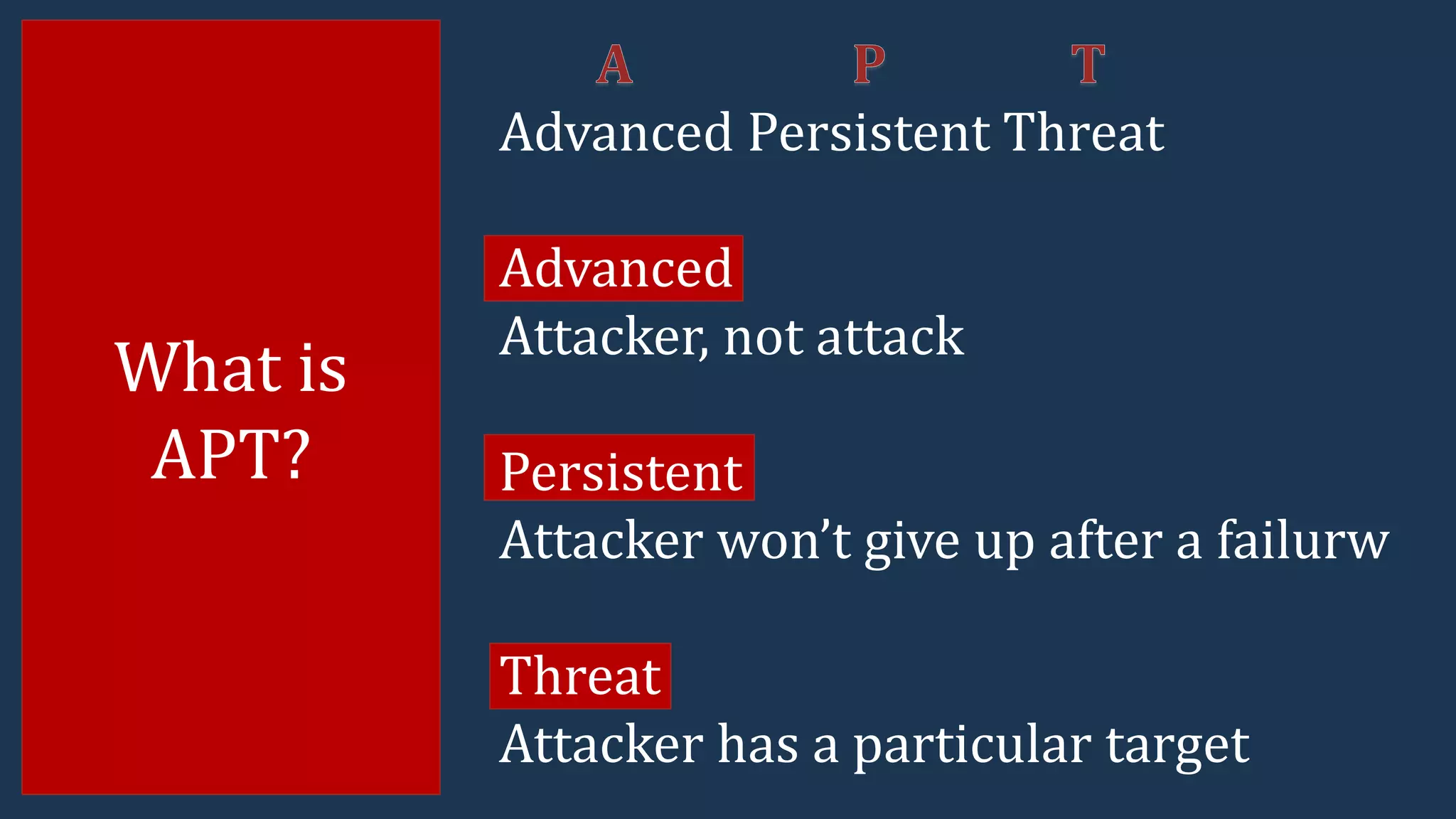
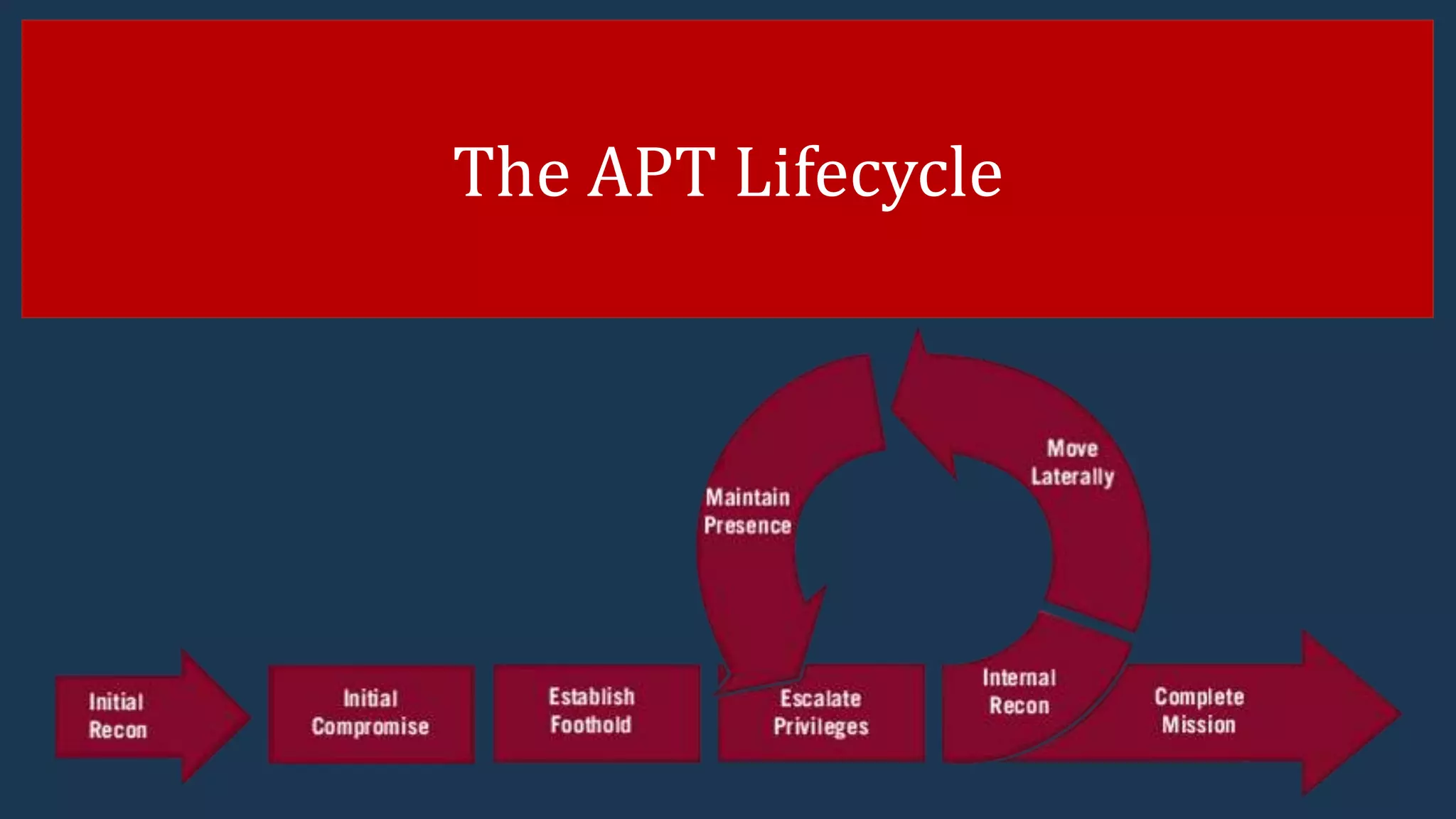
The document presents insights into the current advanced persistent threat (APT) landscape in cybersecurity, emphasizing the increasing costs and risks associated with cybercrime. It outlines various types of cyberattacks, methods of attack, and the defense strategies organizations can adopt to protect against APTs, including understanding the nature of threats and implementing layered security measures. Key statistics from reports highlight the prevalence and serious implications of these cyber threats across different countries and industries.