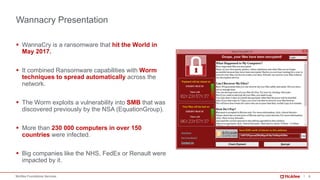
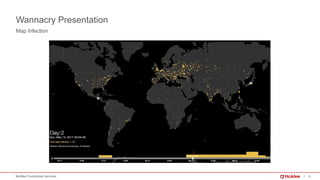
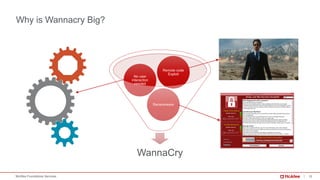
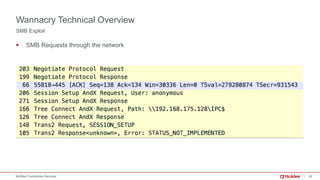
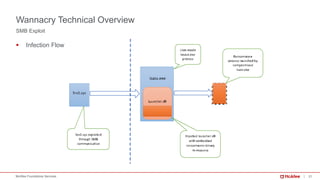
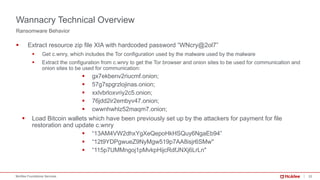
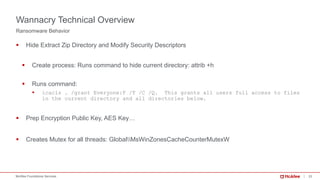
The document provides a comprehensive analysis of the WannaCry ransomware attack that occurred in May 2017, detailing its spread via the EternalBlue exploit and the impact on over 230,000 computers across 150 countries. Key lessons include the importance of patch management, security awareness, and preparedness against evolving malware threats. It emphasizes that despite its simplicity, WannaCry’s worm capabilities facilitated rapid dissemination, which continues to influence new ransomware variants.













![18McAfee Foundstone Services
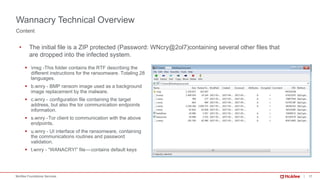
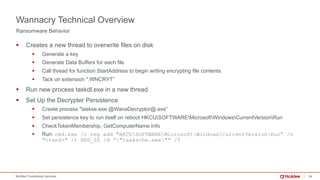
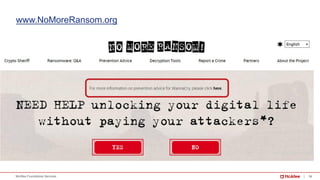
§ Wannacry has a kill switch function to stop the spreading.
§ hxxp://www[dot]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[dot]com
§ hxxp://www[dot]ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[dot]com
Kill Switch Function
Wannacry Technical Overview](https://image.slidesharecdn.com/wannacryanalysis-171118213037/85/Wannacry-Technical-Insight-and-Lessons-Learned-18-320.jpg)











![McAfee, the McAfee logo and [insert <other relevant McAfee Names>] are trademarks or registered trademarks of McAfee LLC or its subsidiaries in the U.S. and/or other countries.
Other names and brands may be claimed as the property of others.
Copyright © 2017 McAfee LLC.](https://image.slidesharecdn.com/wannacryanalysis-171118213037/85/Wannacry-Technical-Insight-and-Lessons-Learned-39-320.jpg)