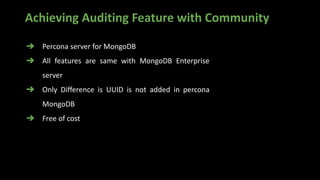
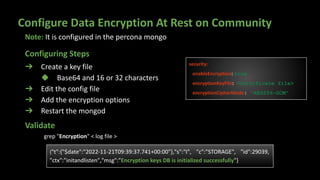
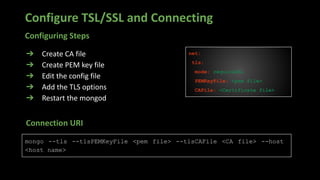
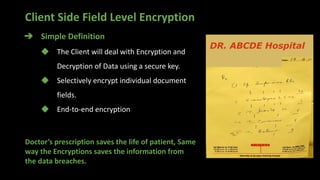
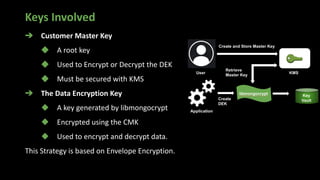
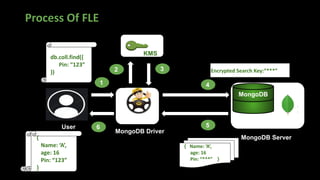
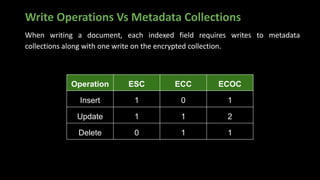
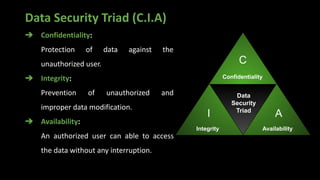
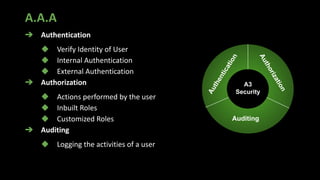
The document presents an in-depth overview of MongoDB security, detailing critical aspects such as data security triads, authentication mechanisms, role-based access control, and encryption methods for data at rest, in transit, and client-side. It also discusses auditing features, queryable encryption, and recommendations for maintaining database security. The content is designed for database engineers to implement necessary security measures for MongoDB effectively.









![Roles in MongoDB
Role: A detailed object consists of Actions with
privileges performed on resources.
Actions: Performable Activities.
Resources: The data on which the User going
to do activities.
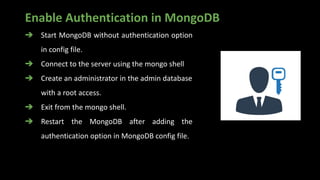
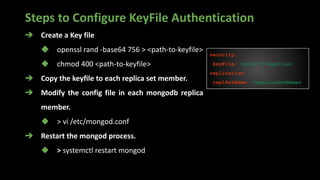
> use admin
> db.createRole(
{
role: "dropCollectionUser",
privileges: [
{
actions: [ "dropCollection" ],
resource: { db: "DB",
collection: "" }
}
],
roles: []
}
)](https://image.slidesharecdn.com/datasecutrityinmongodb-221127162204-f22b8c27/85/Achieving-compliance-With-MongoDB-Security-15-320.jpg)
![Built-In Roles in MongoDB
DataBase User
[ read, readWrite ]
DataBase Admin
[ dbAdmin, userAdmin, dbOwner ]
SuperUser
[ root ]
Cluster Admin
[ ClusterManager, ClusterMonitor,
hostManager, ClusterAdmin ]
BackUp/Restore
[ backup, restore ]
All Database
[ readAnyDatabase,
readWriteAnyDatabase ]](https://image.slidesharecdn.com/datasecutrityinmongodb-221127162204-f22b8c27/85/Achieving-compliance-With-MongoDB-Security-16-320.jpg)

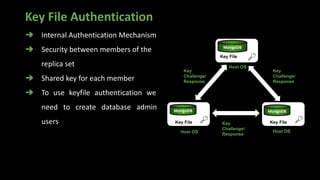


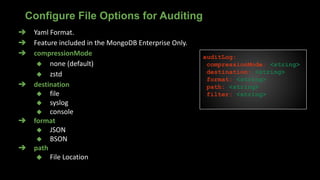
![➔ Filter limit the types of operations
➔ Use Query selectors
➔ Allows regular Expressions
➔ Syntax
filter: { <field>: <expression1> }
Filter Option In Auditing
filter:{
atype: "authCheck",
"param.command":{
$in: [ "find", "insert", "delete", "update",
"findandmodify"]}
},
auditAuthorizationSuccess: true
All
Operations
Filtered
Operations
Stored to
Destination
File
Example](https://image.slidesharecdn.com/datasecutrityinmongodb-221127162204-f22b8c27/85/Achieving-compliance-With-MongoDB-Security-23-320.jpg)
![Audit Message Structure
{
atype: <string>, # Action type
ts : { $date: <timestamp> },
uuid : { $binary: <string>, $type: <string> },
local: { ip: <string>, port: <int> || isSystemUser: <boolean> || unix:
<string> },
remote: { ip: <string>, port: <int> || isSystemUser: <boolean> || unix:
<string> },
users : [ { user: <string>, db: <string> }, ... ],
roles: [ { role: <string>, db: <string> }, ... ],
param: <document>,
result: <int>
}](https://image.slidesharecdn.com/datasecutrityinmongodb-221127162204-f22b8c27/85/Achieving-compliance-With-MongoDB-Security-24-320.jpg)