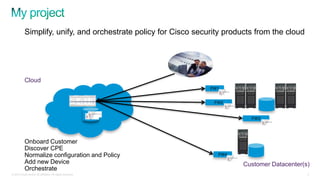
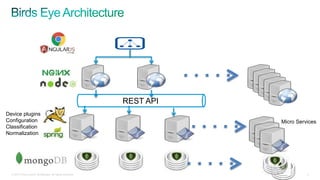
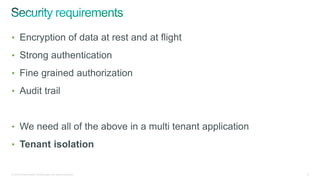
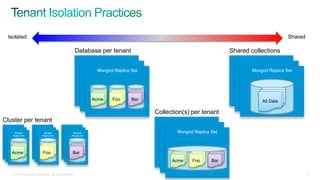
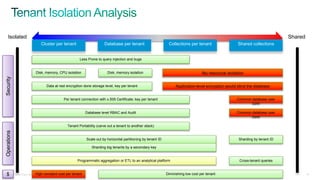
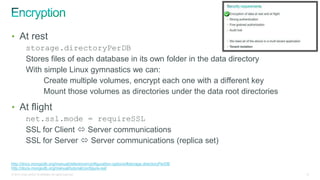
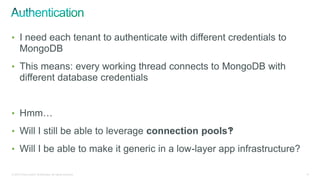
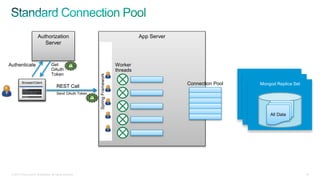
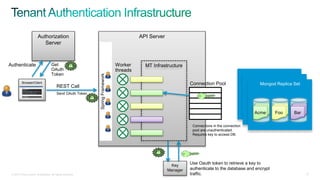
The document discusses implementing security for a multi-tenant SaaS application using MongoDB, focusing on aspects like encryption, strong authentication, and tenant isolation. It outlines the architecture and operational considerations necessary for securely managing data within a cloud environment. Key points include the use of role-based access control, connection pooling, and audit trails to enhance the application's security measures.







![© 2014 Cisco and/or its affiliates. All rights reserved. 19
• Ah with authenticated users – it’s easy!
• MongoDB employs Role-Based Access Control (RBAC)
• A user is granted one or more roles that determine the user’s
access to database resources and operations
http://docs.mongodb.org/manual/core/authorization/
db.createRole(
{
role: "accessSomeColls",
privileges: [
{ resource: { db: "acme", collection: "inventory" }, actions: [ "find", "update", "insert" ] },
{ resource: { db: "acme", collection: "orders" }, actions: [ "find" ] }
],
roles: []
}
)
db.grantRolesToUser( "acme", [ "accessSomeColls" ])](https://image.slidesharecdn.com/securedmultitenancy-v010-150604180030-lva1-app6891/85/Securing-MongoDB-to-Serve-an-AWS-Based-Multi-Tenant-Security-Fanatic-SaaS-Application-19-320.jpg)
![© 2014 Cisco and/or its affiliates. All rights reserved. 20
• Cool important feature in MongoDB Enterprise
• Can audit everything
schema (DDL)
replica set
authentication and authorization
general operations
• Audit Guarantee
Before adding an operation to the journal, MongoDB writes all audit events on the
connection that triggered the operation
• By default, the auditing system records all these operations
Filters are set up to restrict events captured
http://docs.mongodb.org/manual/core/auditing/
http://docs.mongodb.org/manual/reference/audit-message/
http://docs.mongodb.org/manual/reference/audit-message/#audit-event-actions-details-and-results
Audit Message Structure:
{
atype: <String>,
ts : { "$date": <timestamp> },
local: { ip: <String>, port: <int> },
remote: { ip: <String>, port: <int> },
users : [ { user: <String>, db: <String> }, ... ],
roles: [ { role: <String>, db: <String> }, ... ],
param: <document>,
result: <int>
}](https://image.slidesharecdn.com/securedmultitenancy-v010-150604180030-lva1-app6891/85/Securing-MongoDB-to-Serve-an-AWS-Based-Multi-Tenant-Security-Fanatic-SaaS-Application-20-320.jpg)
![© 2014 Cisco and/or its affiliates. All rights reserved. 21
• Sample config
• Additional atype examples:
authenticate, authCheck, createCollection, createDatabase, createIndex,
renameCollection, createUser, grantRolesToUser, createRole,
grantPrivilegesToRole, replSetReconfig, shardCollection, addShard, shutdown
http://docs.mongodb.org/manual/tutorial/configure-auditing/#audit-filter
security:
authorization: enabled
auditLog:
destination: file
format: JSON
path: data/db/auditLog.json
filter: '{ atype: "authCheck", "param.command": { $in: [ "insert", ”remove" ] } , “param.ns”: ”acme.devices” }'
setParameter: { auditAuthorizationSuccess: true }](https://image.slidesharecdn.com/securedmultitenancy-v010-150604180030-lva1-app6891/85/Securing-MongoDB-to-Serve-an-AWS-Based-Multi-Tenant-Security-Fanatic-SaaS-Application-21-320.jpg)

